In order for the WireGuard solution to work properly, it is necessary to create, among others: interface for Wireguard and configure other settings
##### **WireGuard's** configuration is available in the menu item **VPN servers->WireGuard**
[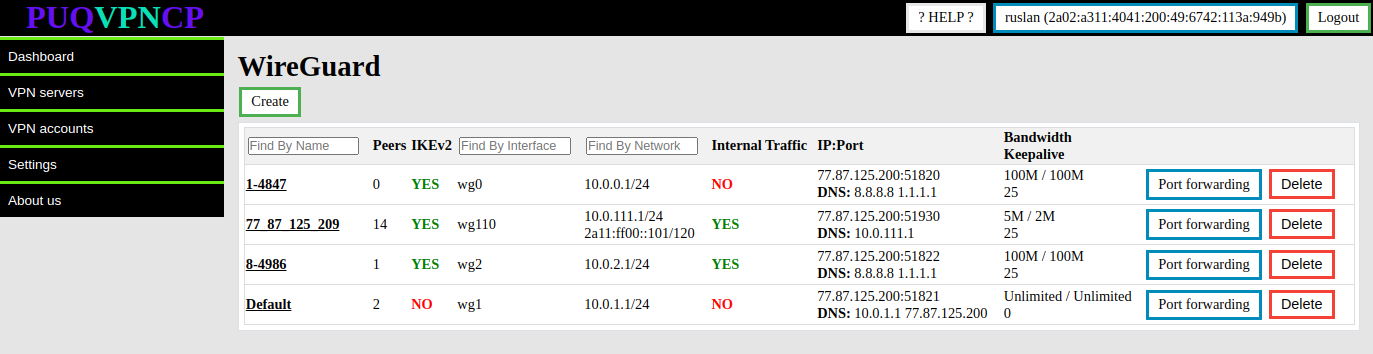](https://doc.puq.info/uploads/images/gallery/2023-07/image-1690791351780.png)
To create a new **WireGuard** server, click the Create button.
[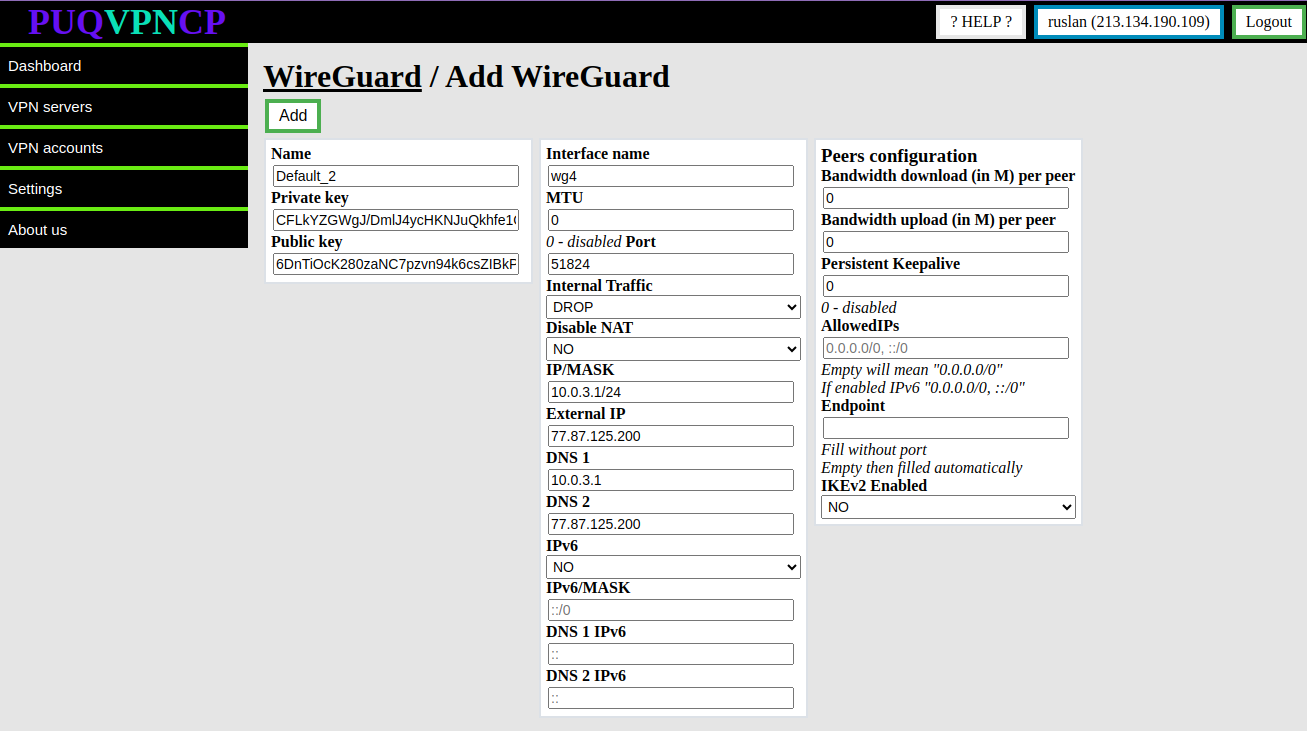](https://doc.puq.info/uploads/images/gallery/2023-10/image-1697374139408.png)
The system will automatically fill in the form for creating a new server with unique data.
You can change the data if necessary.
- **Name** - This is a unique configuration name, this name appears in the system as the main configuration model of the **WireGuard** interface, this parameter cannot be changed later
- **Private key/Public key -** Keys for encrypting the traffic of the WireGuard interface, the system generated new keys, but you can set them yourself when creating the **WireGuard** interface
- **Interface name -** Name of the **WireGuard** network interface in the system, this parameter cannot be changed
- **IP/MASK -**The parameters of the internal network of clients of this **WireGuard** interface, the address that is specified will be assigned to the interface and for all clients of this interface it will be the default gateway.
- **Internal Traffic -** Allow or deny traffic exchange between the client of this interface
- **Disable NAT-** If set to YES, then NAT rules will not be added to the firewall, which is necessary for public IP for the client or restricting access to the Internet.
- **Port -** Port on which the interface will listen for incoming connections
- **External IP -** The public IP address that will be used in the interface configuration, NAT will be organized through this address for all clients of this interface. **The address must be public and configured on the server**.
- **DNS 1/DNS 2 -** DNS servers that will be issued to the client of this interface
- **Bandwidth download/Bandwidth upload -** conditional value for the throughput of each peer connected to this **WireGuard** interface. This data will be automatically applied when creating a VPN client for this WireGuard interface.
- **Persistent Keepalive -** A sensible interval that works with a wide variety of firewalls is 25 seconds. Setting it to 0 turns the feature off, which is the default, since most users will not need this, and it makes **WireGuard** slightly more chatty
- **MTU** - Ability to set **MTU** on the **WireGuard** interface. This parameter is involved in generating the client settings configuration.
- **AllowedIPs -** This parameter is involved in generating the client settings configuration.
- **IKEv2 Enabled -** Enables **IKEv2** protocol support for this interface. If set to **YES** then users of this interface will connect to the server using the **IKEv2** protocol
- **IPv6 -** Enable or disable IPV6
- **IPv6/MASK -** IPv6 subnet to be distributed among peers
- **DNS 1 IPv6/DNS 2 IPv6 -** IPv6 DNS servers
You must understand that changing any interface parameters will completely remove all old configuration and create an interface with new parameters.
In case of changing critical parameters, each client must reconfigure the connection taking into account the new configuration.
[](https://doc.puq.info/uploads/images/gallery/2023-07/image-1690793942519.png)
[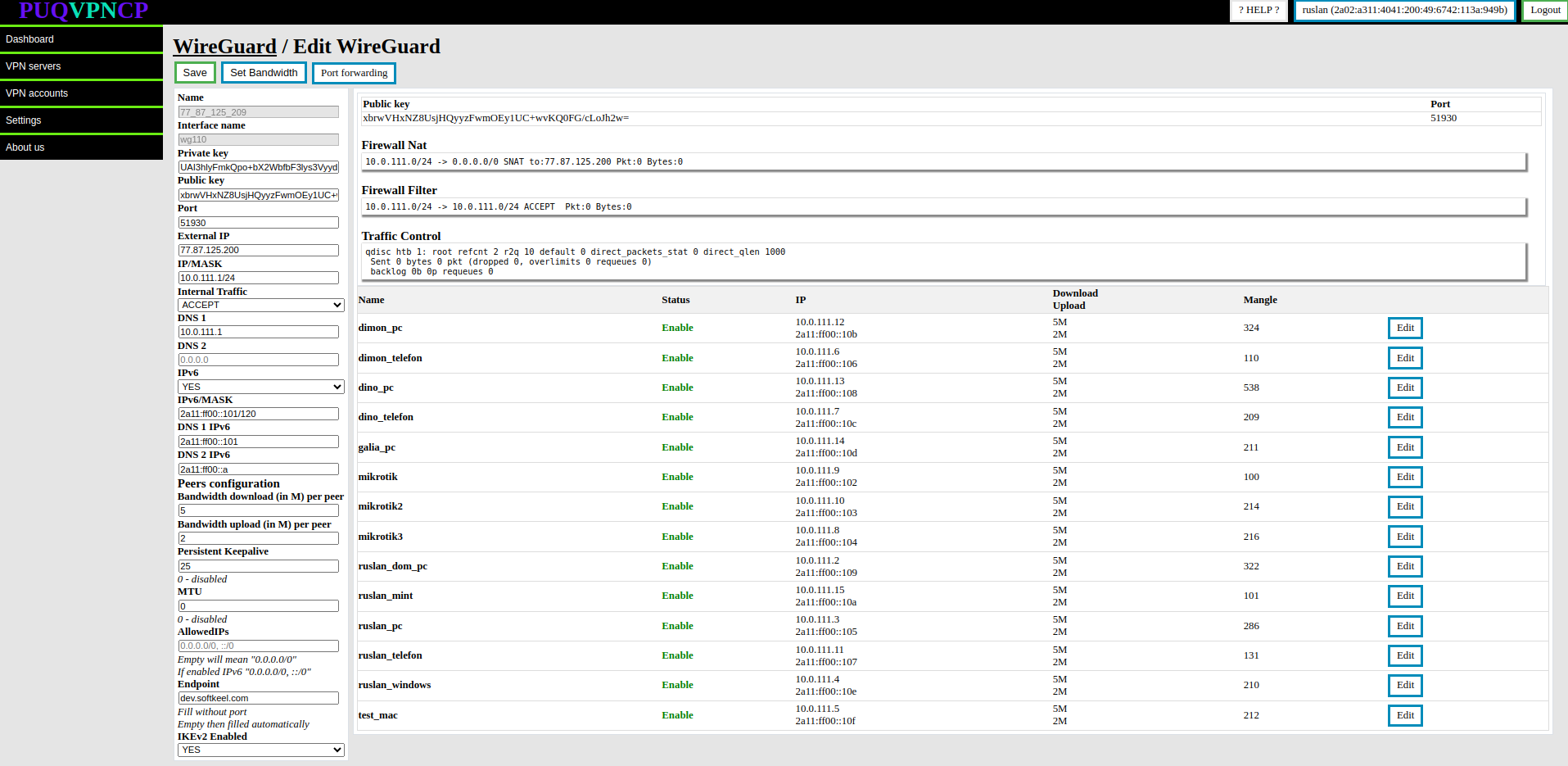](https://doc.puq.info/uploads/images/gallery/2023-07/image-1690793950704.png)
**You can change the following parameters of the WireGuard interface**
- **Private key/Public key -** Keys for encrypting the traffic of the WireGuard interface, the system generated new keys, but you can set them yourself when creating the **WireGuard** interface
- **IP/MASK -**The parameters of the internal network of clients of this **WireGuard** interface, the address that is specified will be assigned to the interface and for all clients of this interface it will be the default gateway.
- **Internal Traffic -** Allow or deny traffic exchange between the client of this interface
- **Port -** Port on which the interface will listen for incoming connections
- **External IP -** The public IP address that will be used in the interface configuration, NAT will be organized through this address for all clients of this interface. **The address must be public and configured on the server**.
- **DNS 1/DNS 2 -** DNS servers that will be issued to the client of this interface
- **Bandwidth download/Bandwidth upload -** conditional value for the throughput of each peer connected to this **WireGuard** interface. This data will be automatically applied when creating a VPN client for this WireGuard interface.
- **Persistent Keepalive -** A sensible interval that works with a wide variety of firewalls is 25 seconds. Setting it to 0 turns the feature off, which is the default, since most users will not need this, and it makes **WireGuard** slightly more chatty
- **MTU** - Ability to set **MTU** on the **WireGuard** interface. This parameter is involved in generating the client settings configuration.
- **AllowedIPs -** This parameter is involved in generating the client settings configuration.
- **IKEv2 Enabled -** Enables **IKEv2** protocol support for this interface. If set to **YES** then users of this interface will connect to the server using the **IKEv2** protocol
- **IPv6 -** Enable or disable IPV6
- **IPv6/MASK -** IPv6 subnet to be distributed among peers
- **DNS 1 IPv6/DNS 2 IPv6 -** IPv6 DNS servers
"**Set Bandwidth**" button, which automatically sets the bandwidth of all clients of the external interface/server Set Bandwidth for the parameters that are entered in the section Peer configuration
# Diagnostic Information
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
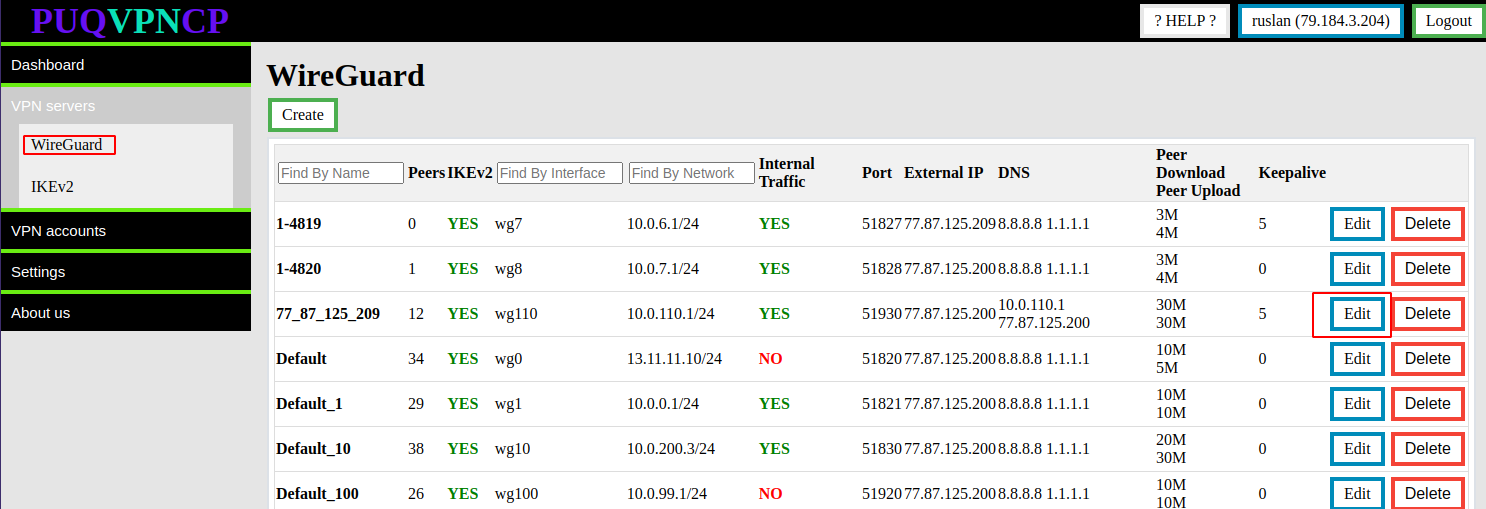
##### **WireGuard** diagnostic Information is available in the menu item **VPN servers->WireGuard**
Select the **WireGuard** interface for which you want to display diagnostic information and click the button "Edit" in the corresponding row.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671007016158.png)
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671007061670.png)
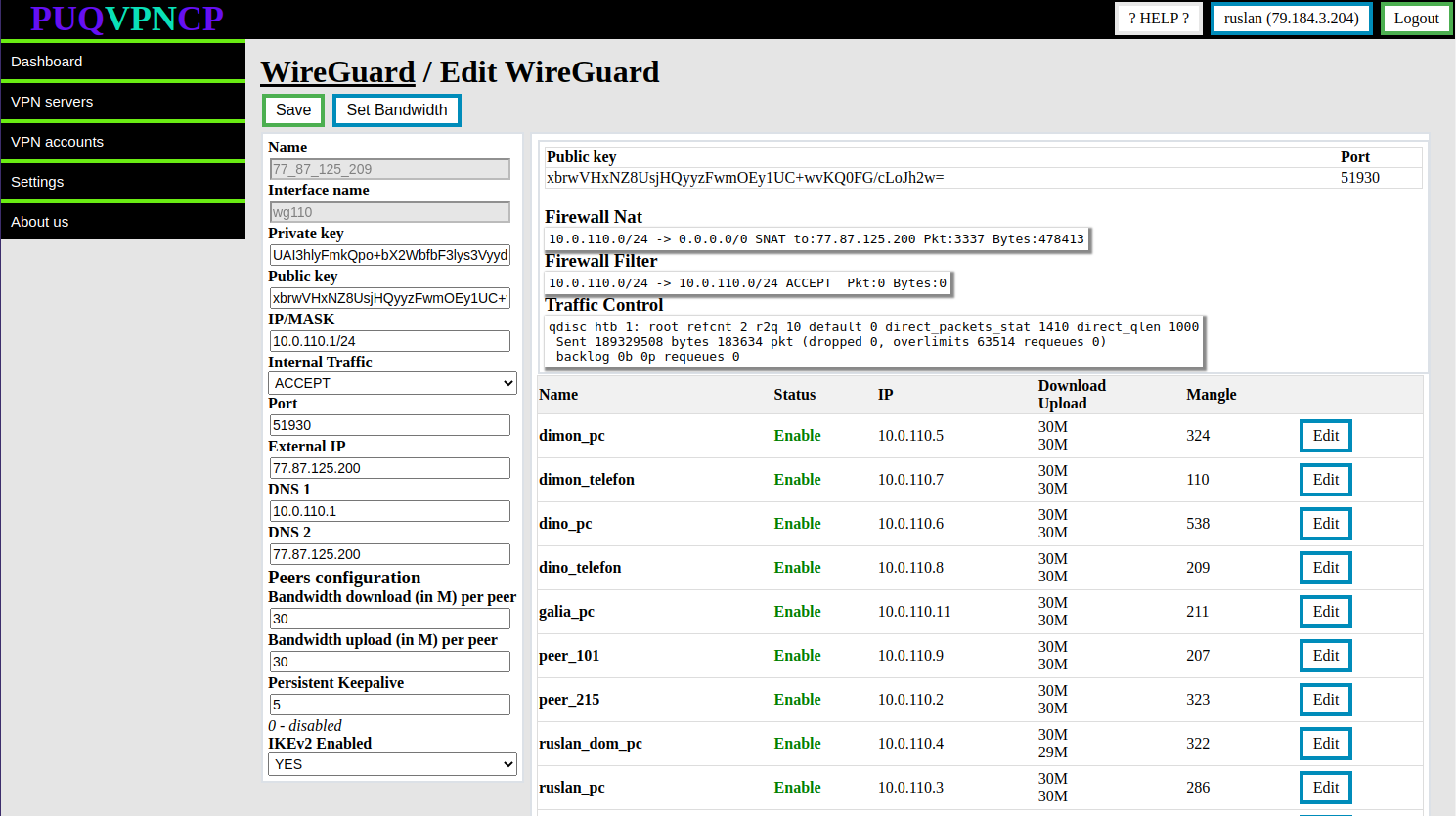
- **Public key/Port -** The actual data that is installed in the system on this interface
- **Firewall Nat -** The actual data is taken from the system firewall, this is a rule that implements nat, with statistics on packet counters and traffic passing through this rule.
- **Firewall Filter -** The actual data is taken from the system firewall, these are rules allowing internal traffic of interface clients, with statistics on packet counters and traffic passing through this rules.
- **Traffic Control -** The actual data is taken from the system with the **Traffic control** configuration, it shows that the interface is involved in filtering traffic in order to limit the speed to the clients of this interface.
Further, there is a table in which the list of all clients which are assigned to this interface.
# Port Forwarding
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
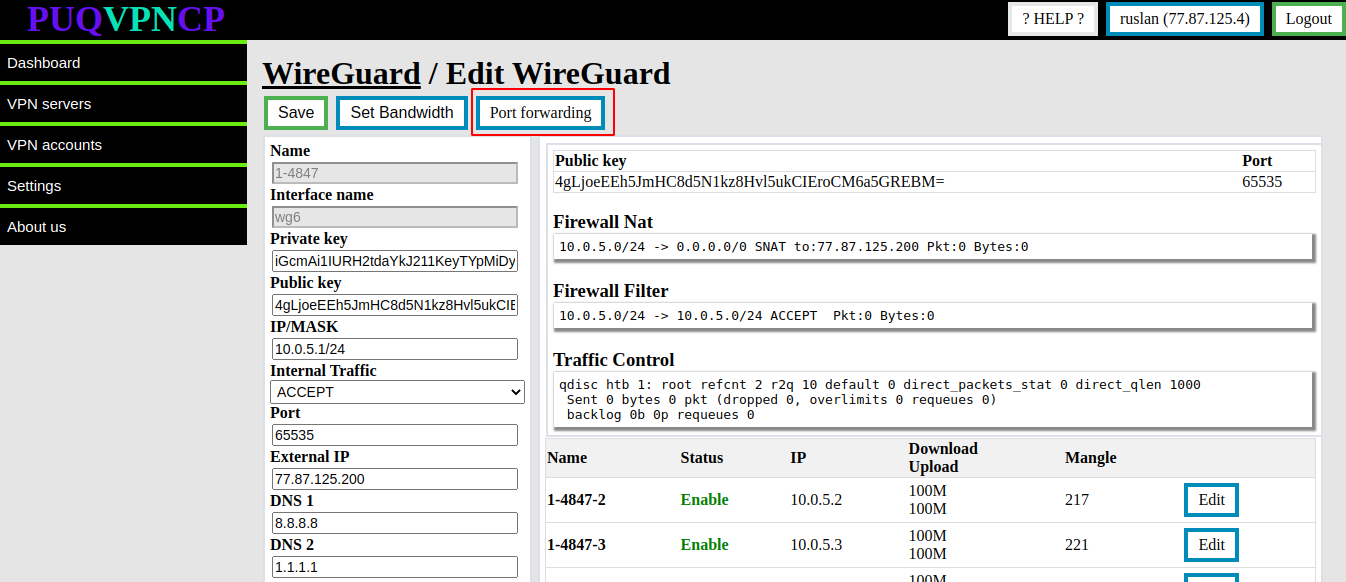
**Port forwarding** is a networking technique used to allow external devices to access services running on a local network. Essentially, it involves redirecting incoming network traffic from a specific port on a router or firewall to a specific device or port on the internal network. This allows devices outside the local network to access resources such as web servers, FTP servers, or game servers hosted on a local network. Port forwarding is often used for remote access to devices, for example, accessing a security camera or a home automation system from a remote location.
To access port forwarding settings, select the Wireguard server for which you wish to configure port forwarding and click on the **port forwarding** button.
[](https://doc.puq.info/uploads/images/gallery/2023-02/image-1677505786729.png)
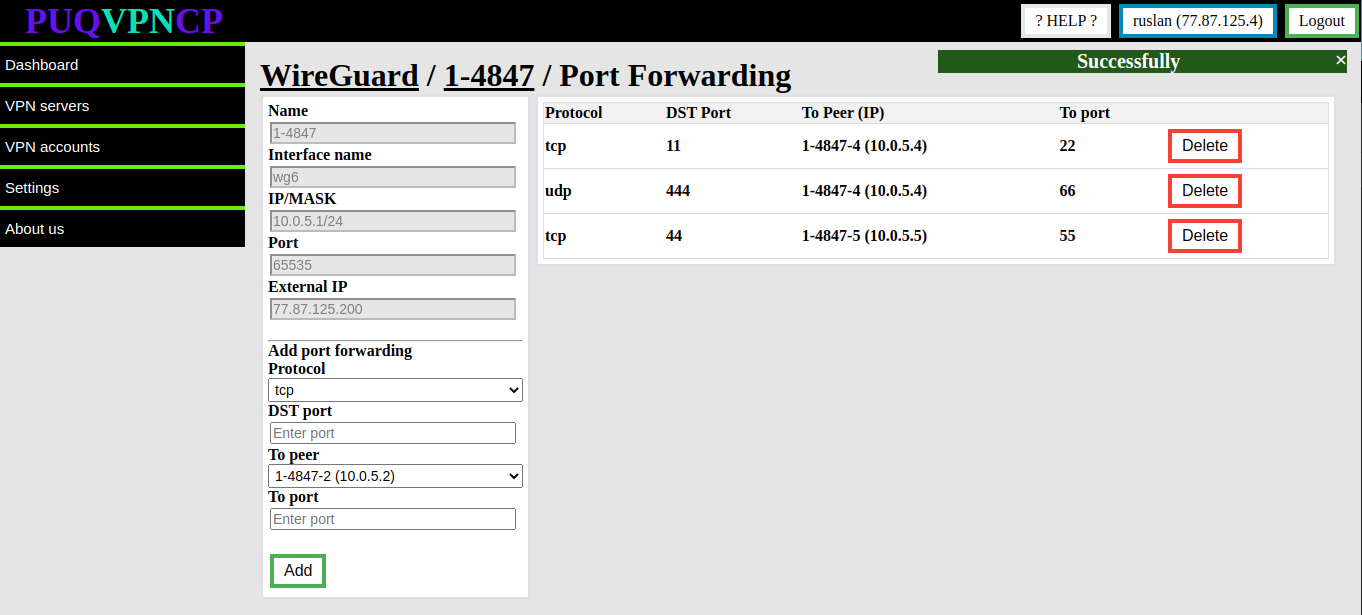
When you access the port forwarding settings, a list of all currently forwarded ports from the external IP address to the internal account will be displayed. If you wish to add a new port forwarding rule, simply fill out the necessary information and click on the "**ADD**" button. Conversely, if you need to remove an existing port forwarding rule, click on the "**DELETE**" button associated with the relevant entry. These options provide a great deal of flexibility in managing your port forwarding settings to ensure that external devices can access the resources on your VPN network that you want to make available.
[](https://doc.puq.info/uploads/images/gallery/2023-02/image-1677505845931.png)
# IKEv2
# Basic concepts IKEv2 EAP
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
Since version 1.2 **PUQVPNCP** supports VPN protocol **IKEv2** implemented with [strongSwan](https://www.strongswan.org/)
**IKEv2** is a protocol that allows you to create direct IPSec tunnels between a server and a client. **IPSec** provides encryption of network traffic in IKEv2 virtual private networks. **IKEv2** is natively supported on a number of platforms (OS X 10.11+, iOS 9.1+, Windows 10) without additional applications and easily resolves client connectivity issues.
For the protocol to work correctly, it is necessary to configure certificates for encryption; using the panel, this process is easy and comes down to pressing literally two buttons.
It is worth remembering that the main VPN protocol in the panel is WireGuard, and the **IKEv2** protocol is an additional protocol. This means that before using **IKEv2**, you must configure the WireGuard protocol, and then enable **IKEv2** support on each **WireGuard** interface on which you want to use **IKEv2**.
## **IKEv2** protocol available to clients
- **Android** (Official application from strongSwan)
- **iOS** (integrated client)
- **macOS** (integrated client)
- **Linux** (network-manager-strongswan)
- **Windows** (integrated client)
Due to the specifics of Microsoft's implementation of the client in Windows, there is a technical nuance that requires you to enter the password twice each time you connect.
## Usage features IKEv2 EAP
- To use the **IKEv2 EAP** protocol, the client must have the domain name of the VPN server, username and password for authorization, and there is a need to import the root certificate to authenticate the server certificate.
- The **IKEv2 EAP** protocol uses **IPSec** encryption to encrypt traffic between the client and the server, this imposes a certain load on the server and we recommend taking this into account when choosing server parameters.
- The data transfer rate in the case of rate limiting is lower than declared, due to the fact that all data packets are consistent with the headers that are required for IPsec encryption to work. *This is especially noticeable at low limits of 1-10 megabits.*
- Due to the technical aspects of VPN client rate limiting, the data rate limit will be taken from the outgoing traffic parameter, this parameter in **IKEv2** connections will be for incoming and outgoing traffic
# Technical requirements and installation
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## Technical requirements
- Operating systems: Debian 9+ (amd64), Ubuntu 18+ (amd64)
- Real ip address on server interface
- Domain name for the server
- **PUQVPNCP v1.2**
- Installed packages **strongswan strongswan-pki libstrongswan-extra-plugins**
## **Installation**
We issue all comments after logging into the SSH terminal window as the root user.
```shell
apt-get update
apt-get upgrade
reboot
```
```shell
apt-get install strongswan strongswan-pki libstrongswan-extra-plugins -y
```
## Checking installed packages
##### Checking the strongSwan
```shell
dpkg -s strongswan-starter
```
Output should looks similar to this:
```shell
Package: strongswan-starter
Status: install ok installed
Priority: optional
Section: net
Installed-Size: 610
Maintainer: strongSwan Maintainers
Architecture: amd64
Source: strongswan
Version: 5.9.1-1+deb11u3
Depends: adduser, libstrongswan (= 5.9.1-1+deb11u3), lsb-base (>= 3.0-6), debconf (>= 0.5) | debconf-2.0, libc6 (>= 2.27)
Pre-Depends: init-system-helpers (>= 1.54~)
Recommends: strongswan-charon
Conflicts: openswan
Conffiles:
/etc/apparmor.d/usr.lib.ipsec.stroke 3ddc2d056db9435ba0d421678308bee3
/etc/init.d/ipsec a7b2d9de5749ee0bebcd6ac3f9fee732
/etc/ipsec.conf 01485a8658db82dd781f9229f4151661
/etc/ipsec.secrets d8e074734da10d2ec7bcd9913263d717
/etc/strongswan.d/charon/stroke.conf effb1b5bc46a7c849754fada75bae0d2
/etc/strongswan.d/starter.conf 2ba2784c18e268e34cec179d90e38437
Description: strongSwan daemon starter and configuration file parser
The strongSwan VPN suite uses the native IPsec stack in the standard
Linux kernel. It supports both the IKEv1 and IKEv2 protocols.
.
The starter and the associated "ipsec" script control the charon daemon from
the command line. It parses ipsec.conf and loads the configurations to the
daemon.
Homepage: http://www.strongswan.org
```
- - - - - -
##### Checking the IPSec Version
```shell
ipsec version
```
Output should looks similar to this:
```shell
Linux strongSwan U5.9.1/K5.10.0-10-amd64
University of Applied Sciences Rapperswil, Switzerland
See 'ipsec --copyright' for copyright information.
```
- - - - - -
##### Checking the pki
```shell
pki
```
Output should looks similar to this:
```shell
strongSwan 5.9.1 PKI tool
loaded plugins: test-vectors pkcs11 tpm aes rc2 sha2 sha1 md5 mgf1 random x509 revocation pubkey pkcs1 pkcs7 pkcs8 pkcs12 dnskey sshkey pem openssl gcrypt af-alg gmp curve25519 hmac drbg curl
usage:
pki --acert (-z) issue an attribute certificate
pki --dn (-d) extract the subject DN of an X.509 certificate
pki --gen (-g) generate a new private key
pki --issue (-i) issue a certificate using a CA certificate and key
pki --keyid (-k) calculate key identifiers of a key/certificate
pki --pkcs12 (-u) PKCS#12 functions
pki --pkcs7 (-7) PKCS#7 wrap/unwrap functions
pki --print (-a) print a credential in a human readable form
pki --pub (-p) extract the public key from a private key/certificate
pki --req (-r) create a PKCS#10 certificate request
pki --self (-s) create a self signed certificate
pki --signcrl (-c) issue a CRL using a CA certificate and key
pki --verify (-v) verify a certificate using the CA certificate
pki --help (-h) show usage information
```
- - - - - -
# Create a root certificate
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
If you already have a root certificate ready, use certificate import. More in the certificate[ import instructions](https://doc.puq.info/books/puqvpncp/page/import-the-root-certificate "Import the root certificate") section.
Go to menu item **VPN servers -> IKEv2**
[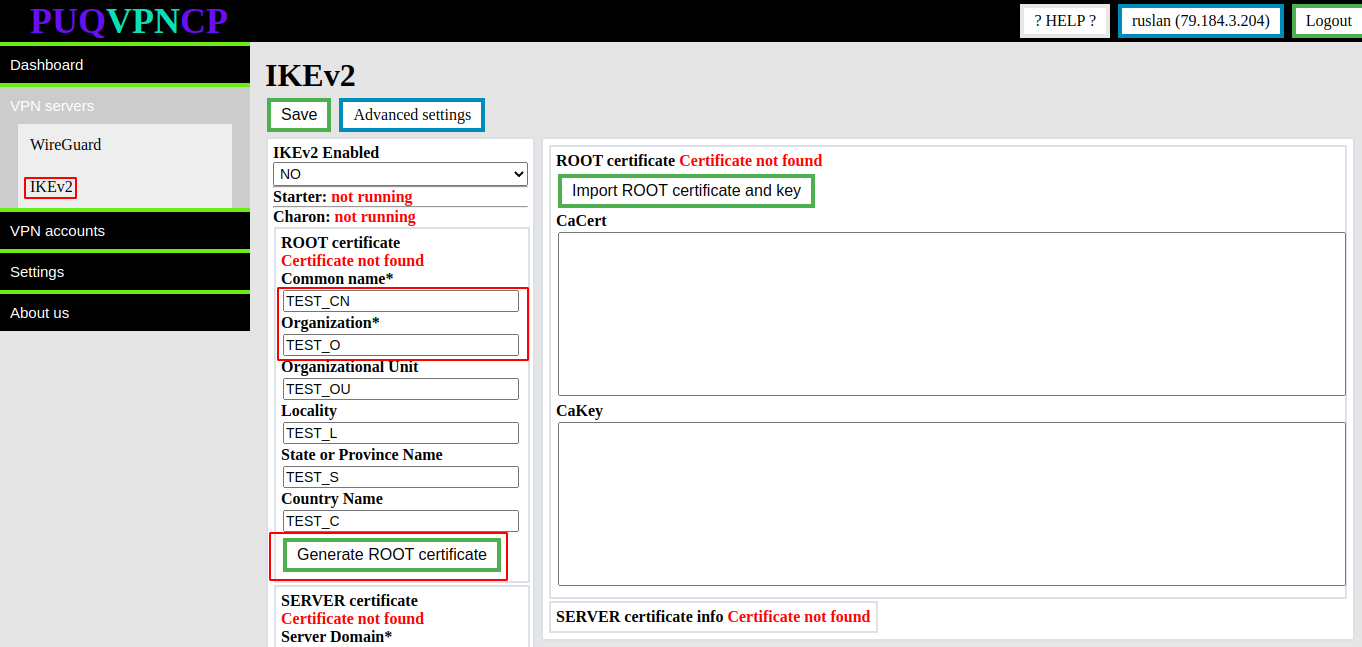](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670922619439.png)
You need to fill in the required fields such as:
- Common name
- Organization
Then click the button **Generate ROOT certificate**
After these steps, the **root certificate and private key** will be generated.
Information about the certificate will be available in the same place.
[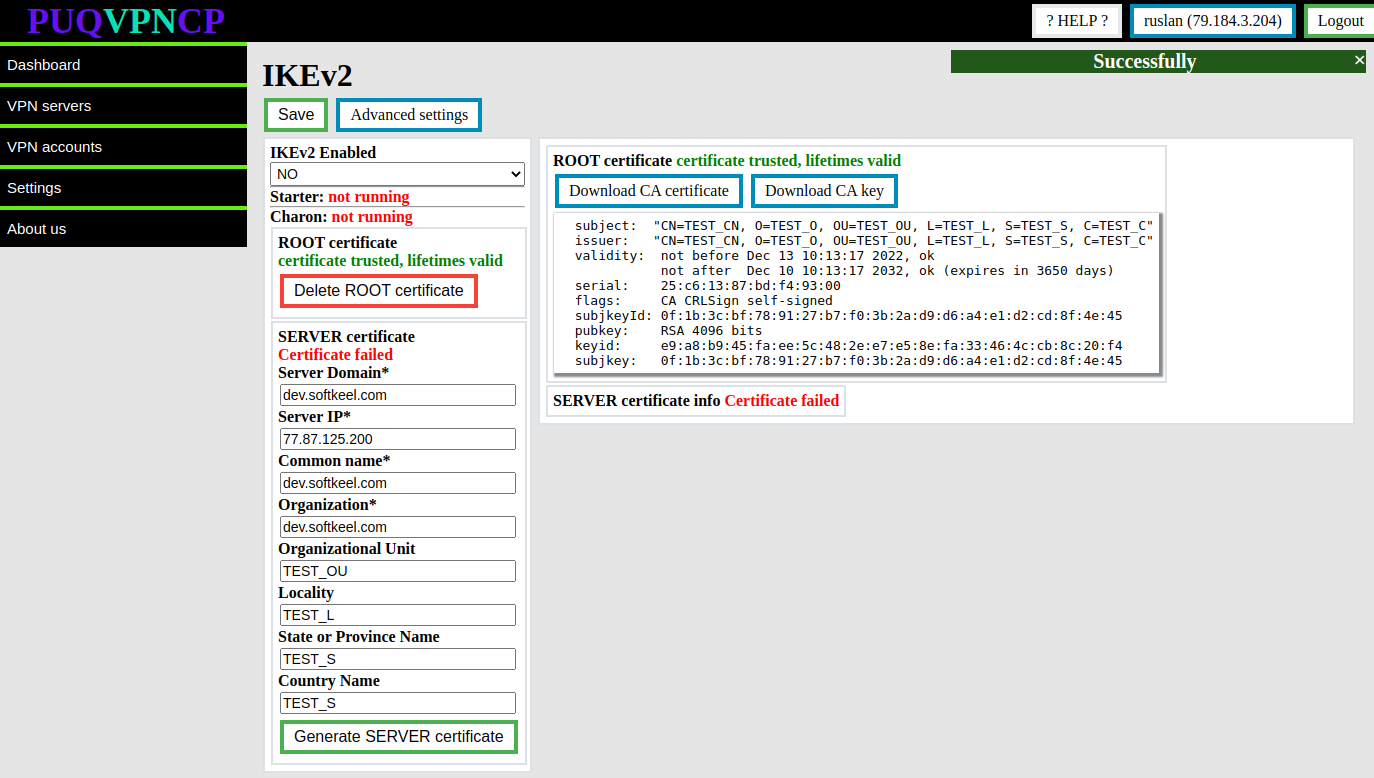](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670922926394.png)
To download the root certificate and private key, you can use the buttons **Download CA certificate** and **Download CA key**
To remove the root certificate, use the **Delete ROOT certificate** button
# Import the root certificate
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
If you don't have a root certificate ready, use the certificate generation option. More in the certificate generation instruction section.
Go to menu item **VPN servers -> IKEv2**
[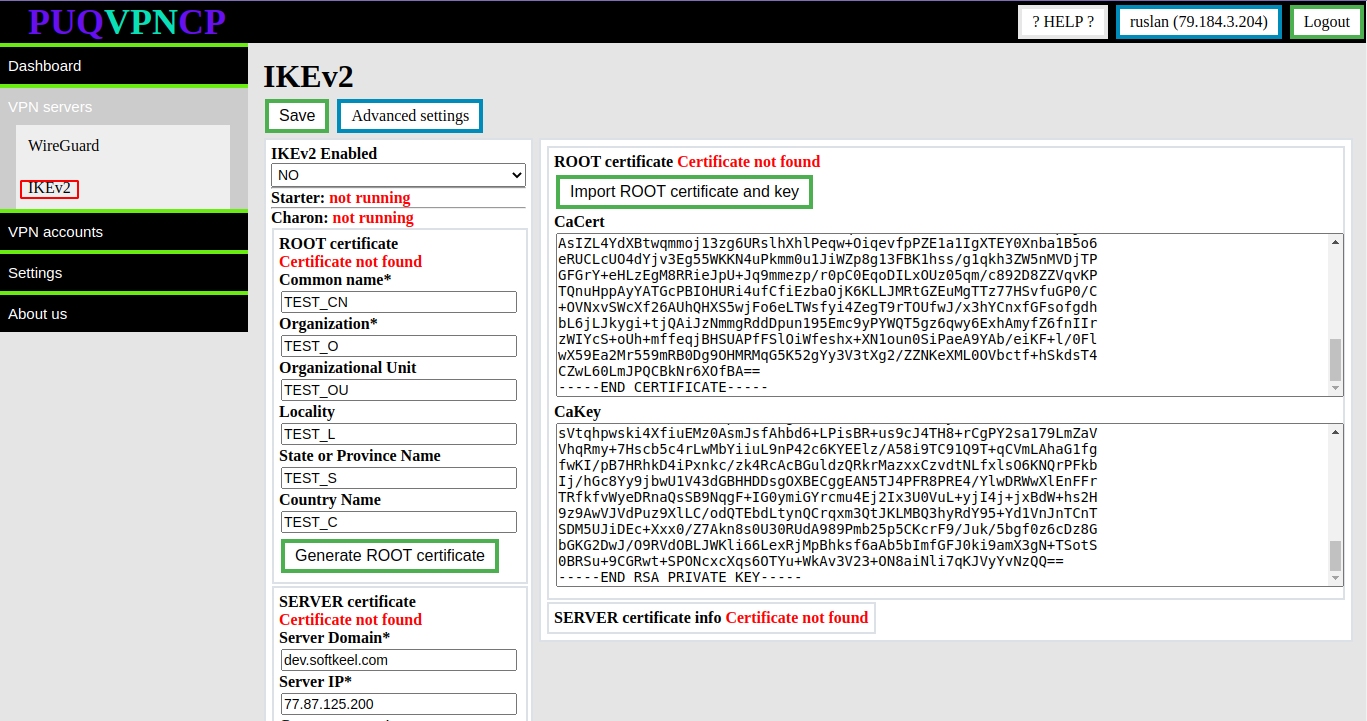](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670923354418.png)
You need to fill in the fields intended for the root certificate and for the private key
- **CaCert**
- **CaKey**
To import the root certificate and private key, click the **Import ROOT certificate and key** button
After these steps, the **root certificate and private key** will be imported.
Information about the certificate will be available there.
[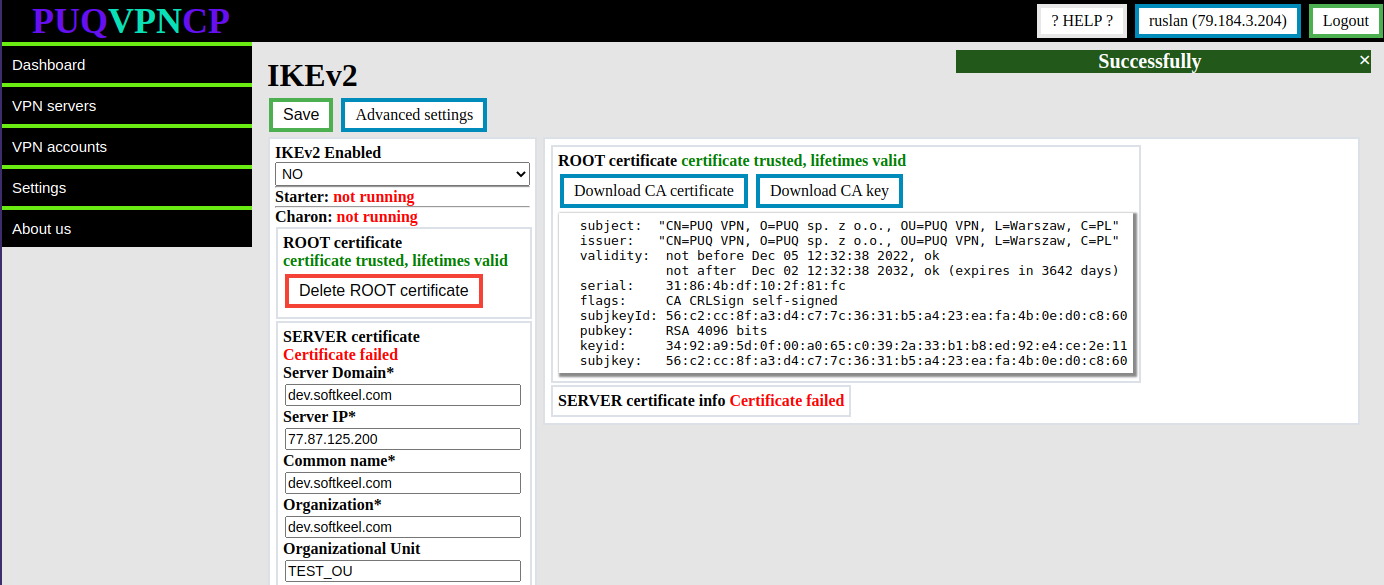](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670923545662.png)
To download the root certificate and private key, you can use the buttons **Download CA certificate** and **Download CA key**
To remove the root certificate, use the **Delete ROOT certificate** button
# Create a server certificate
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
Before creating a server certificate, you must create or import a root certificate.
Go to menu item **VPN servers -> IKEv2**
[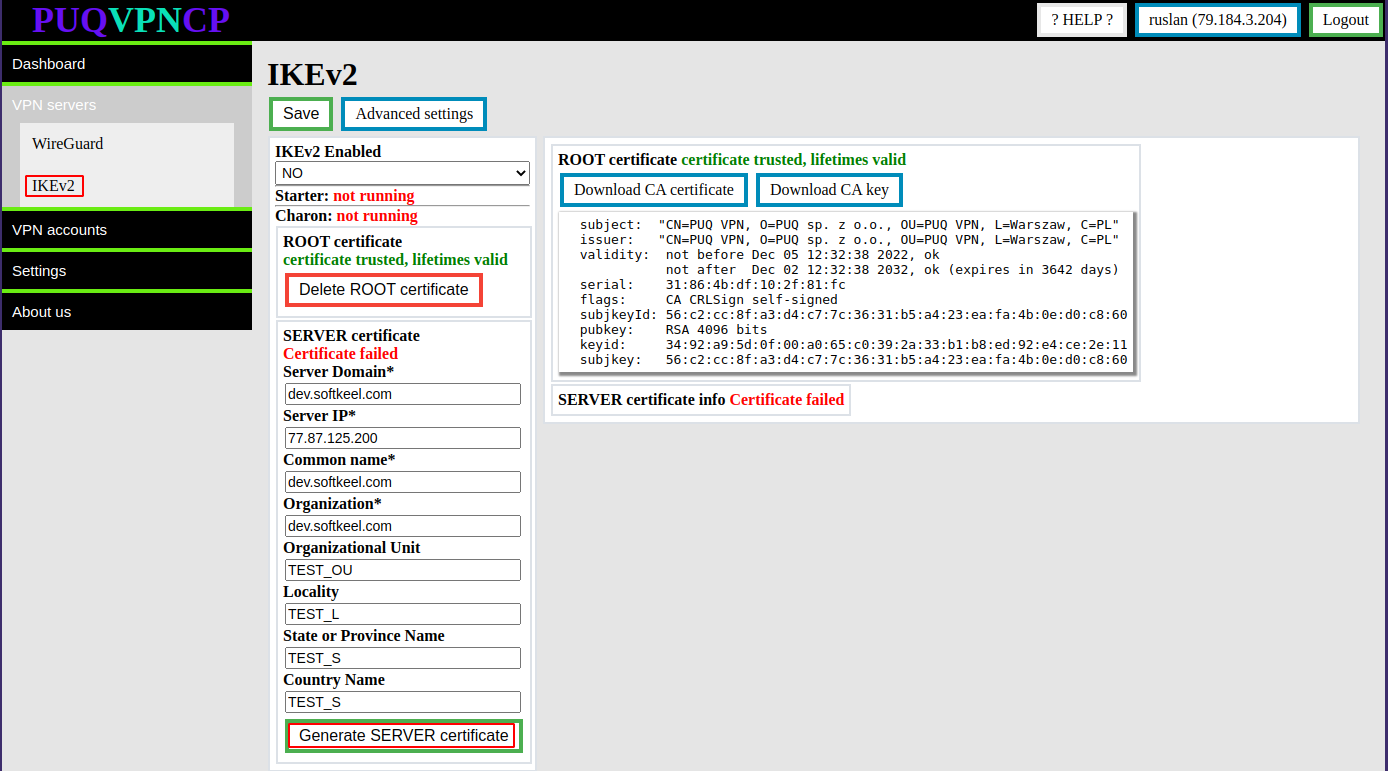](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670924167899.png)
You need to fill in the required fields such as:
- **Server Domain**
- **Server IP**
- **Common name**
- **Organization**
Then click the button **Generate SERVER certificate**
After these steps, the **Server certificate and private key** will be generated.
Information about the certificate will be available in the same place.
[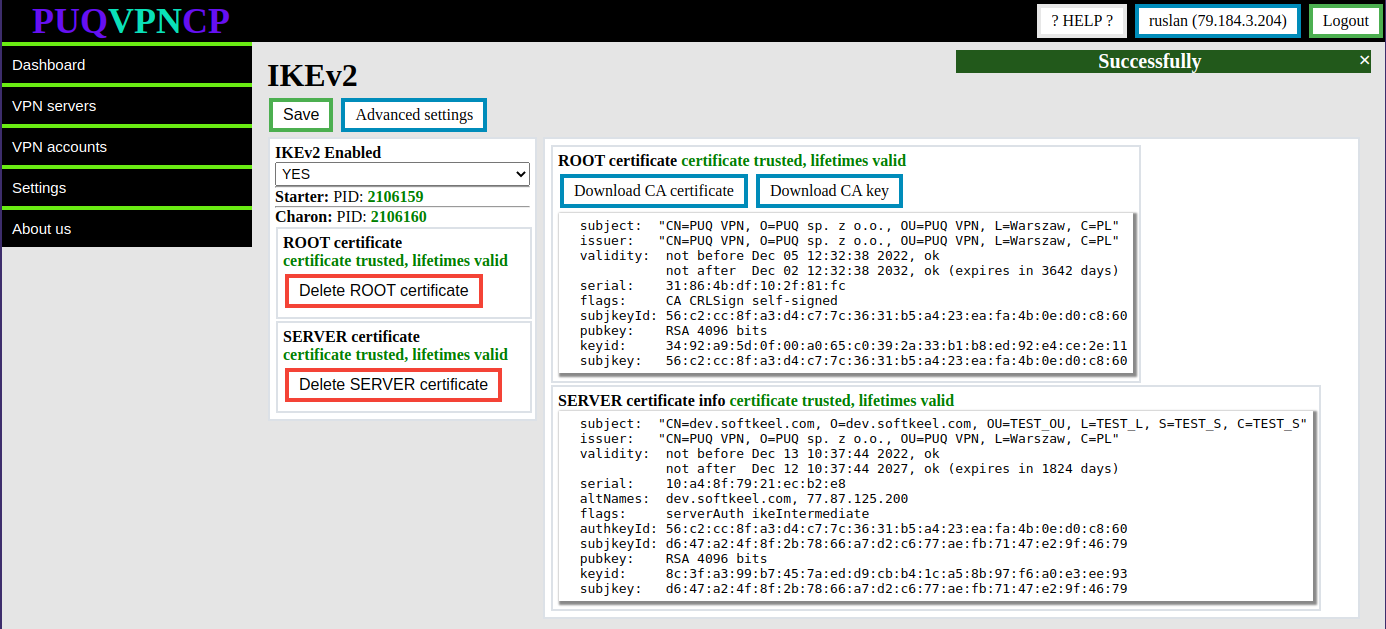](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670924293587.png)
To remove the server certificate, use the **Delete SERVER certificate** button
After a successful server certificate generation process, the IKEv2 server transitions to the enabled state.
[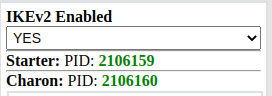](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670924457963.png)
# Advanced settings
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
For more precise server settings, you can use Advanced settings
On this page you can customize the server to suit your needs.
Use the official strongSwan documentation for parameter information
[https://wiki.strongswan.org/projects/strongswan/wiki/IpsecConf](https://wiki.strongswan.org/projects/strongswan/wiki/IpsecConf)
Go to menu item **VPN servers -> IKEv2** Click on the **Advanced settings** button
[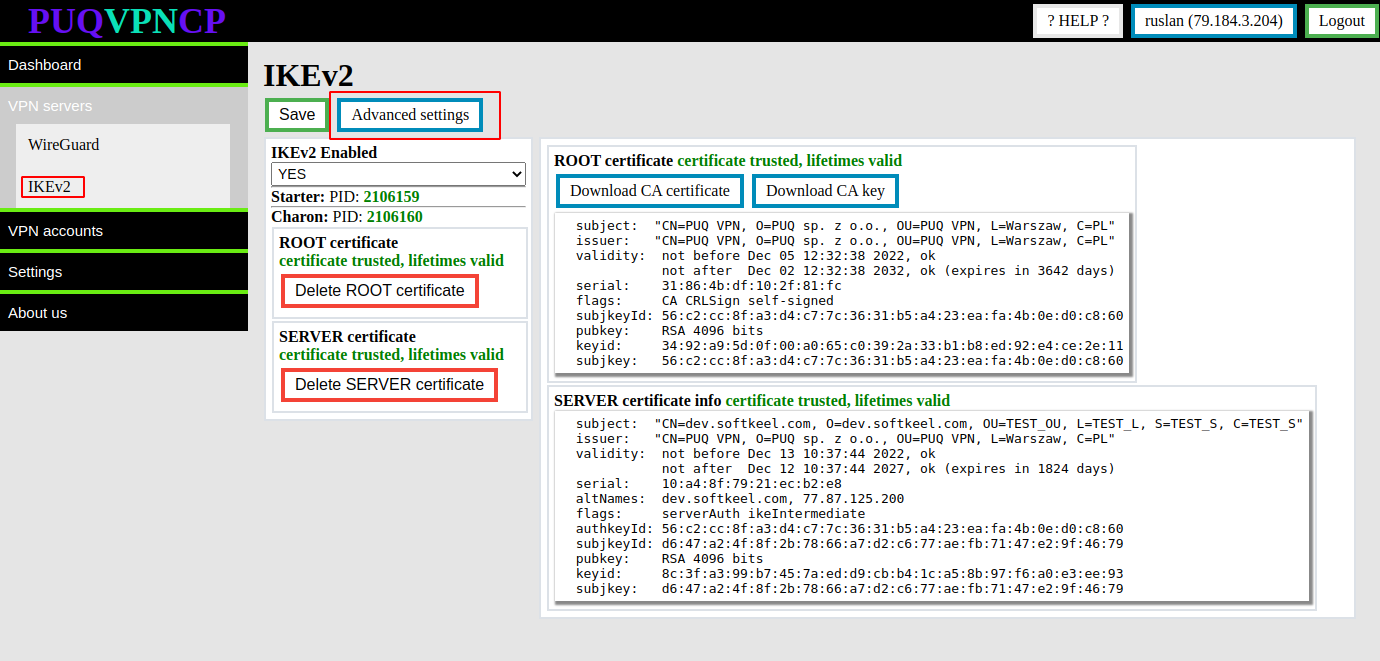](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670924658462.png)
Go to the IKEv2 Advanced settings page
[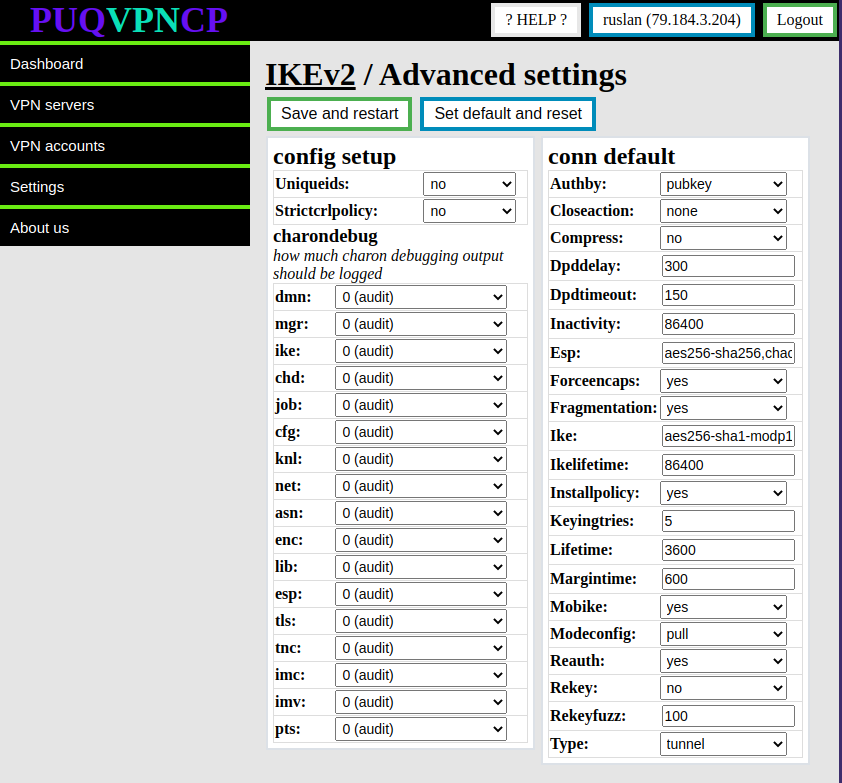](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670924724136.png)
In order to restore the default settings, click the **Set default and reset** button
# Enable IKEv2
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
It is worth remembering that the main VPN protocol in the panel is **WireGuard**, and the **IKEv2** protocol is an additional protocol. This means that before using **IKEv2**, you must configure the **WireGuard** protocol, and then enable **IKEv2** support on each **WireGuard** interface on which you want to use **IKEv2**.
##### For the inclusion of the **IKEv2** protocol, switch to the configuration of the **WireGuard** user interface
To enable the **IKEv2** protocol, switch to the desired **WireGuard** interface.
[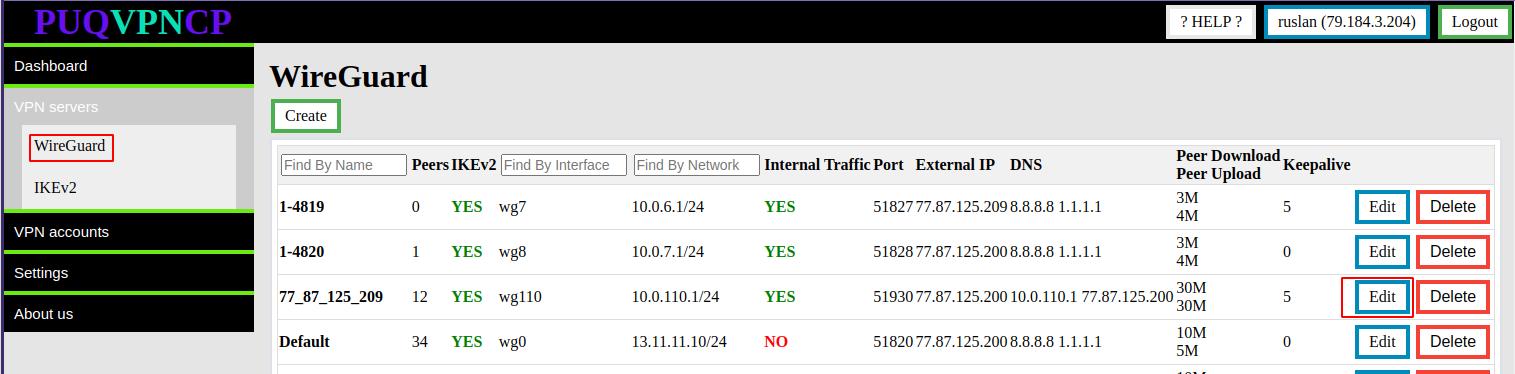](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670936314051.png)
[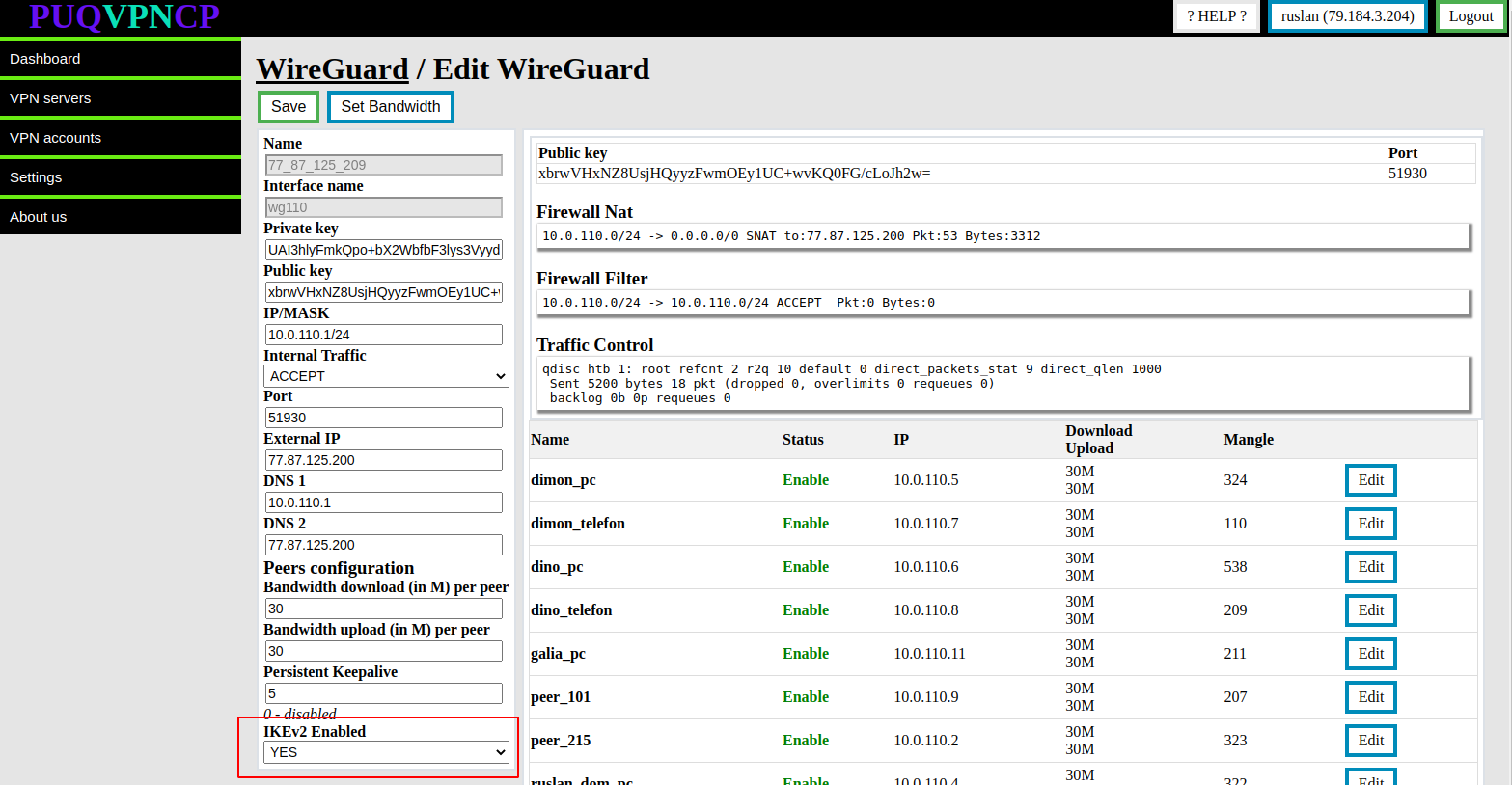](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670925351457.png)
Set the **IKEv2 Enabled** option to **YES** to keep the value of the **Save** button
# VPN accounts
# Create VPN account
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In this panel tab you can create new VPN accounts.
This activity can be simplified by using additional modules for WHMCS that automate the whole process. [More information here.](https://puqcloud.com/whmcs-modules-vpn/)
#### Create VPN account
To create a VPN account go to **VPN accounts -> Add VPN account**
[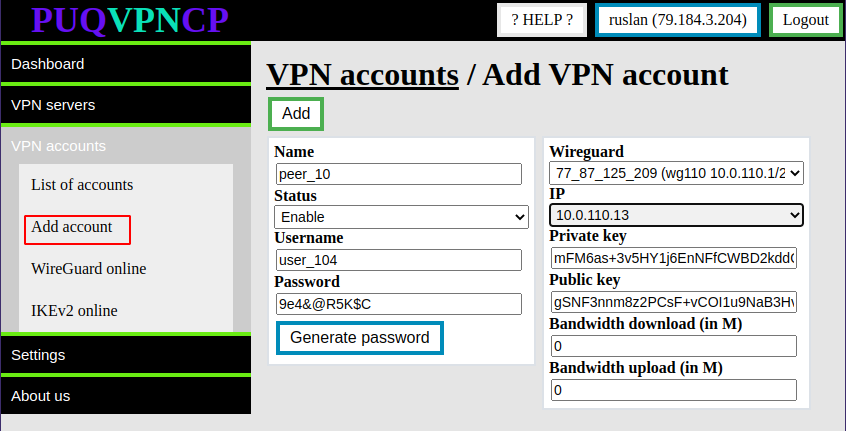](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671012867877.png)
The system will automatically fill the form with unique data. It is necessary to change them if there is a need for it.
- **Name -** Account name, required to link the account with the WireGuard and IKEv2 servers
- **Status -** Account status can be enabled or disabled
- **Username/Password -** Authorization data for protocols that require login and password authorization (IKEv2)
- **Wireguard -** The Wireguard interface to which the new account will be assigned
- **IP -** The IP address that will be allocated to the account and will be assigned when connecting by any protocol.
- **Private key/Public key -**Traffic encryption keys in the WireGuard protocol
- **Bandwidth download /Bandwidth upload -** If necessary, reassign the bandwidth of the account. Otherwise, a similar parameter of the WireGuard interface will be taken into account
After filling in all the fields, click the **Add** button
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671013555840.png)
# Editing VPN account
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In this panel tab you can manage VPN accounts.
This activity can be simplified by using additional modules for WHMCS that automate the whole process. [More information here.](https://puqcloud.com/whmcs-modules-vpn/)
##### Edit an VPN account
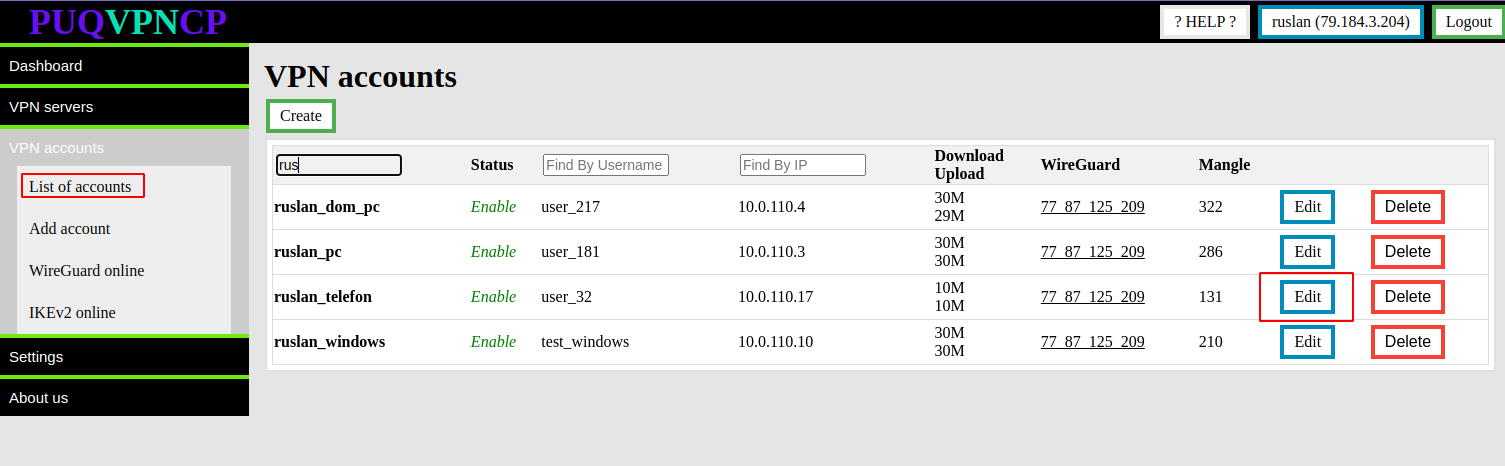
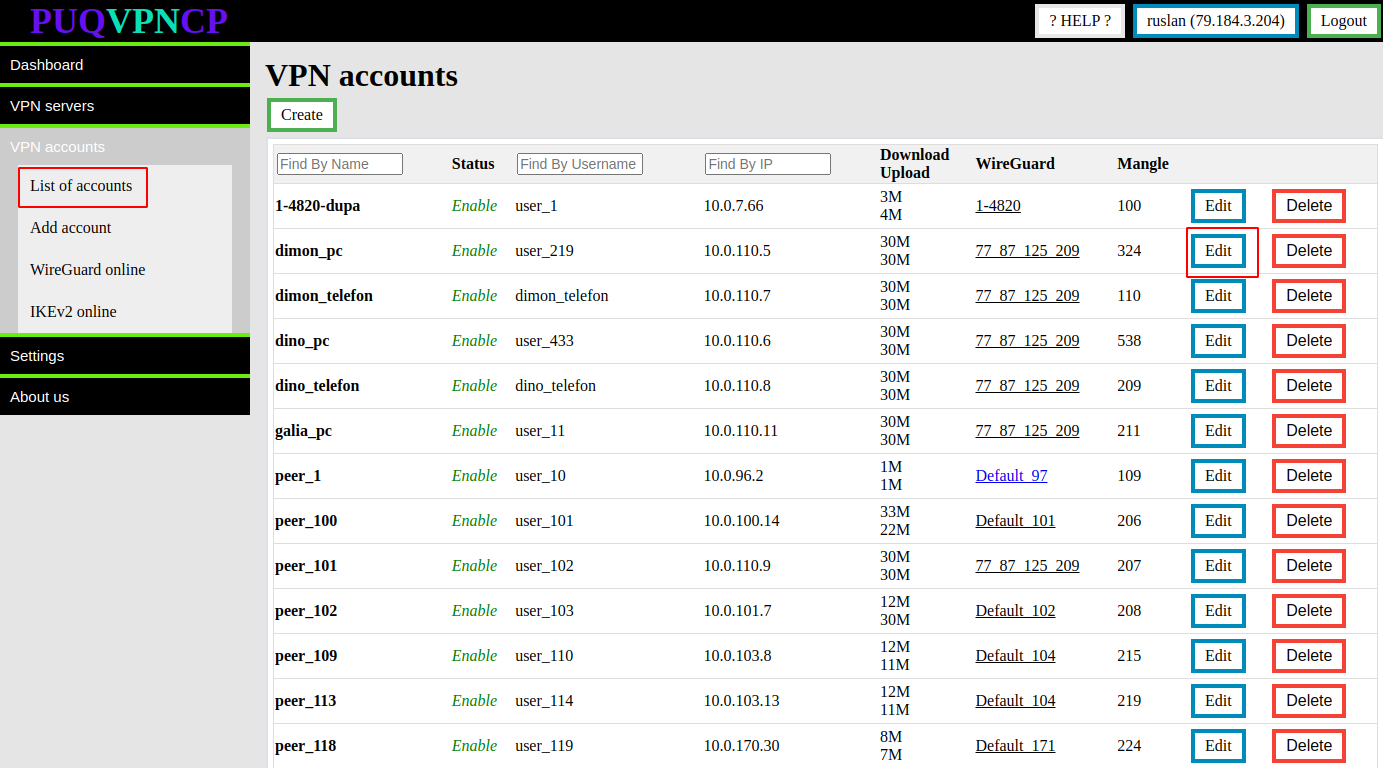
To edit an account, go to **VPN accounts -> List accounts** and select the account you want to edit by pressing the **EDIT** button
[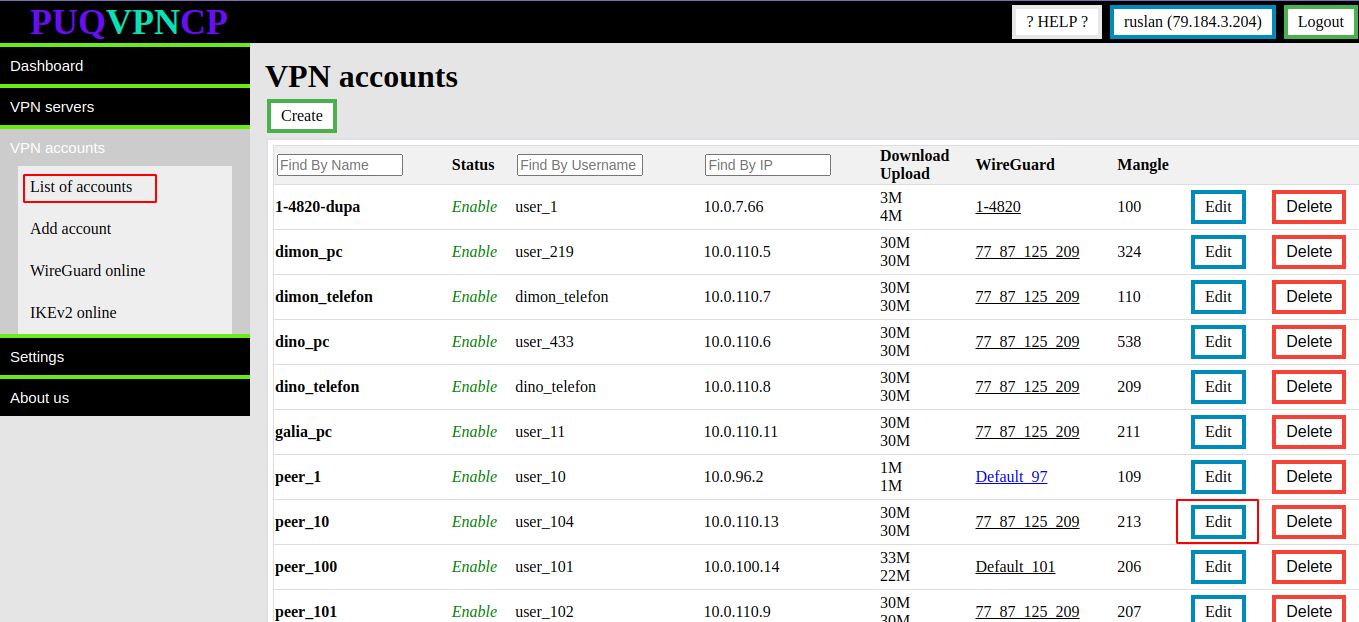](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671013859819.png)
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671013884416.png)
##### It is possible to edit the following parameters
- **Password -** User password for connecting through protocols that require login and password authorization
- **Status -** To enable or disable an account
- **IP -** The IP address that will be allocated to the account and will be assigned when connecting by any protocol (If you change this setting, you must reconfigure the client with the new configuration in the WireGuard protocol)
- **Bandwidth download/Bandwidth upload -** Account bandwidth
After all the data has been entered, click the **Save** button.
Each time the **Save** button is pressed, the client settings will be reconfigured and the connection to the client will be terminated.
# Diagnostic Information
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
##### Information about VPN account diagnostics is available in the menu item **VPN accounts -> List accounts.** Select the VPN account for which you want to display diagnostic information by clicking the **EDIT** button
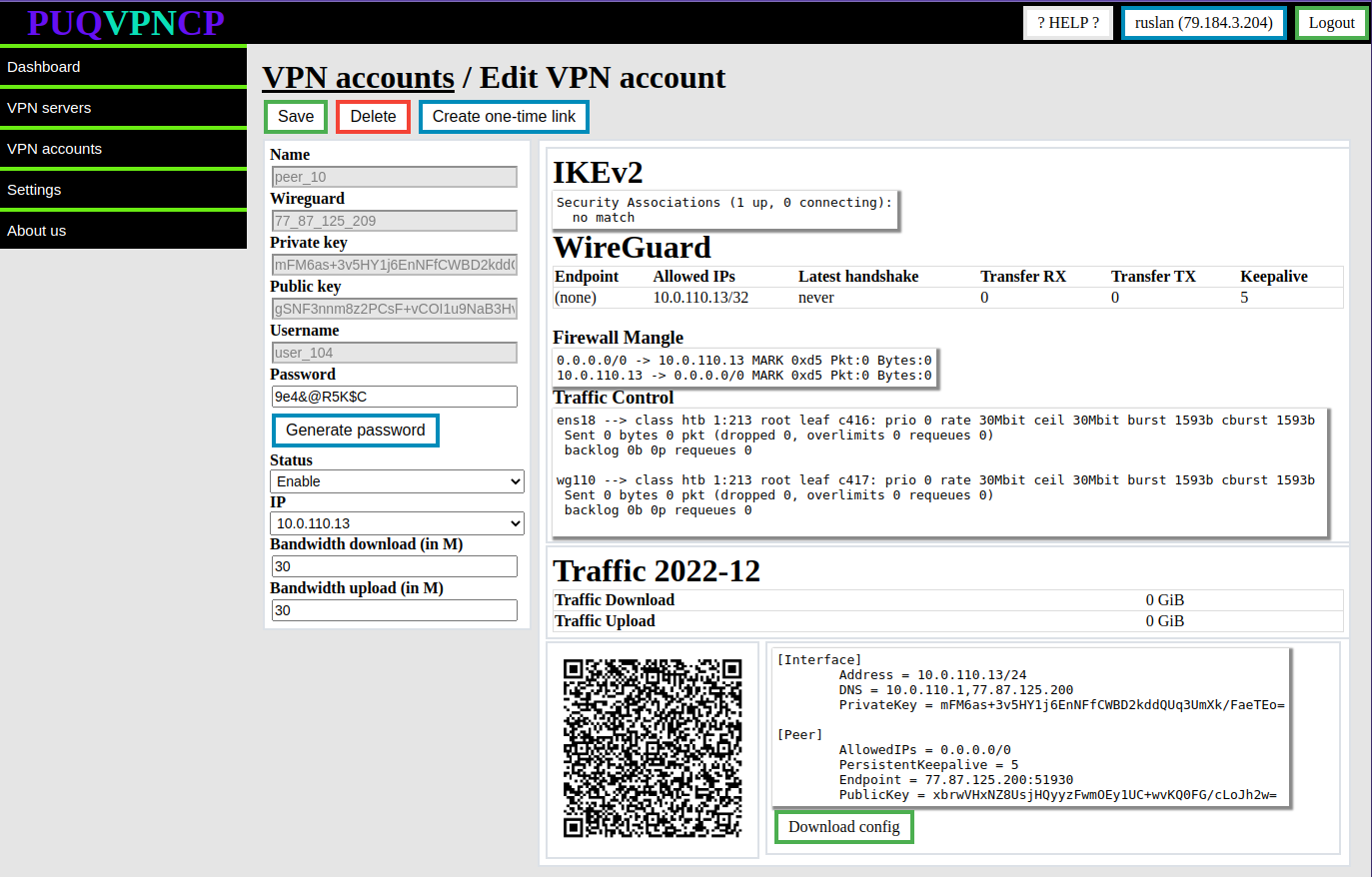
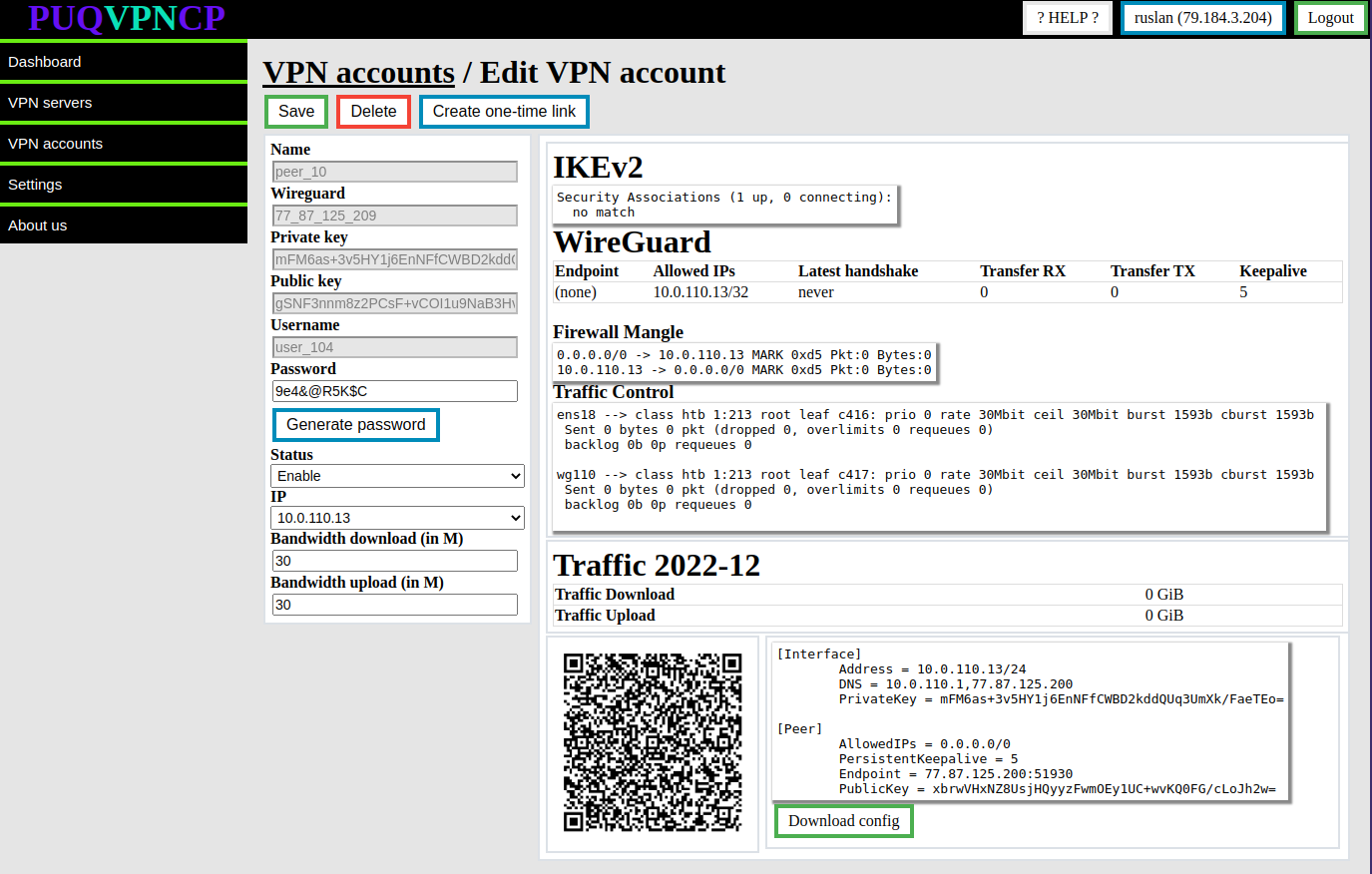
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671016077083.png)
[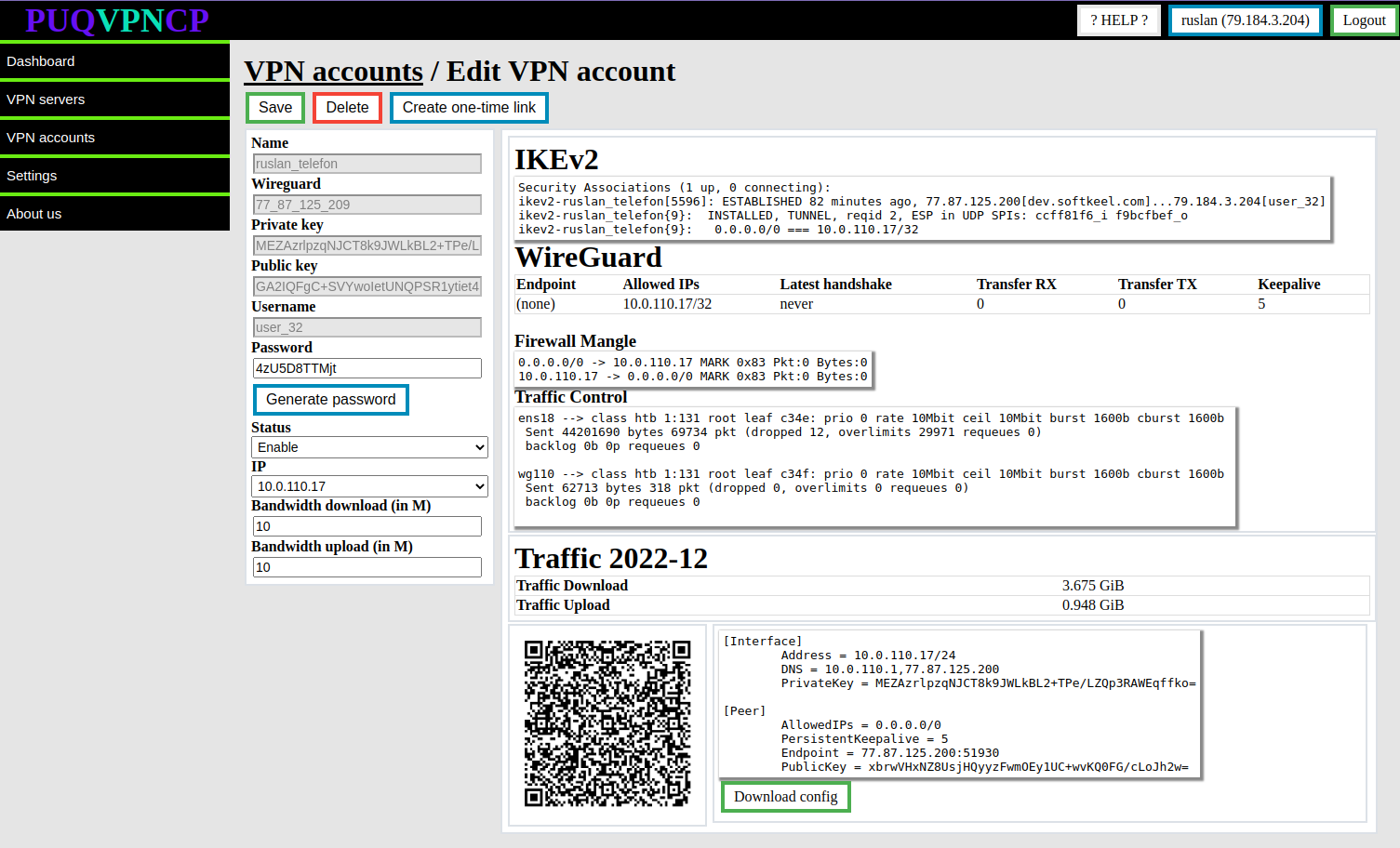](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671016081489.png)
##### IKEv2 section
Actual data from the system about the connection in the **IKEv2** protocol
##### WireGuard
Actual data from the system about the connection in the **WireGuard** protocol
##### Firewall Mangle
The actual data is taken from the system firewall, these are rules that mark traffic from the client and to the client for bandwidth limitation purposes and to collect traffic statistics, with statistics on packet counters and traffic passing through these rules.
While the system is reading the brush value, the counter is reset to zero.
##### Traffic control
The actual data is taken from the system with the Traffic Control configuration, it shows that the interfaces are involved in traffic filtering in order to limit the rate for clients of this interface.
##### Traffic
Actual traffic usage in the current month
There is also a section with the configuration of the **WireGuard** client in the form of a QR code and in text form
# WireGuard online users list
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
##### In order to see which VPN accounts are online in the **WireGuard** protocol, you need to go to the menu item **VPN accounts->WireGuard online**
[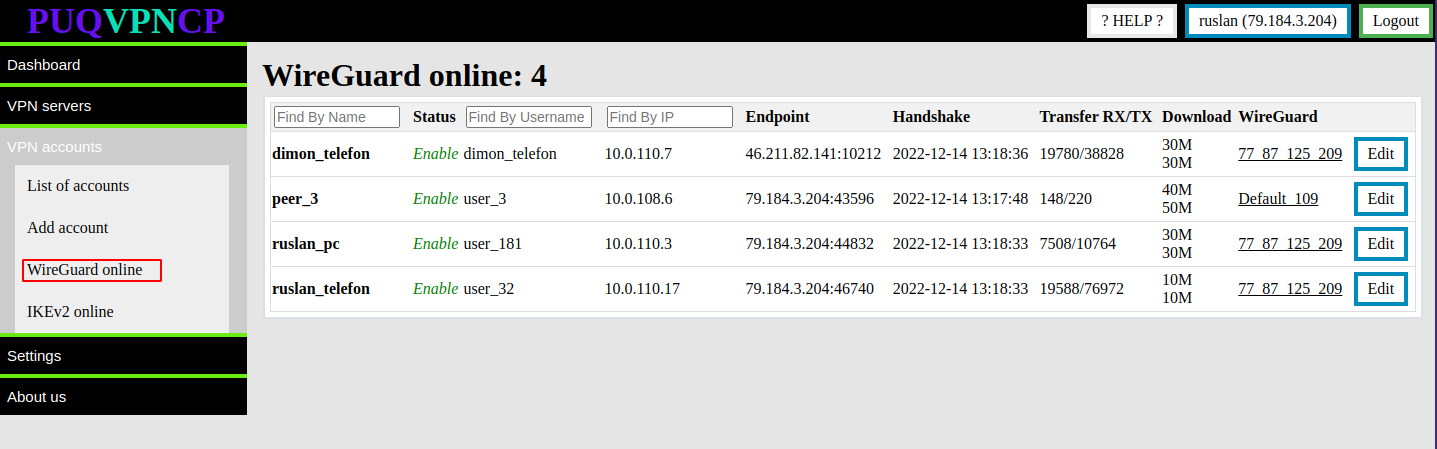](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671020348870.png)
# IKEv2 online users list
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
##### In order to see which VPN accounts are online in the **IKEv2** protocol, you need to go to the menu item **VPN accounts->IKE\_v2 online**
[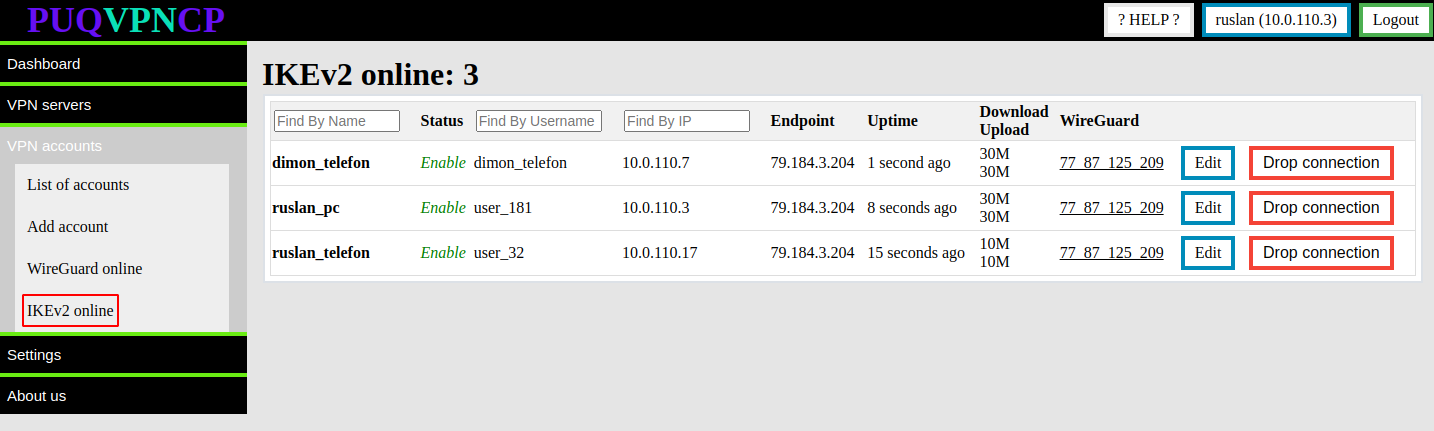](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671020442522.png)
# One-time link
# Basic concepts One-time link
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
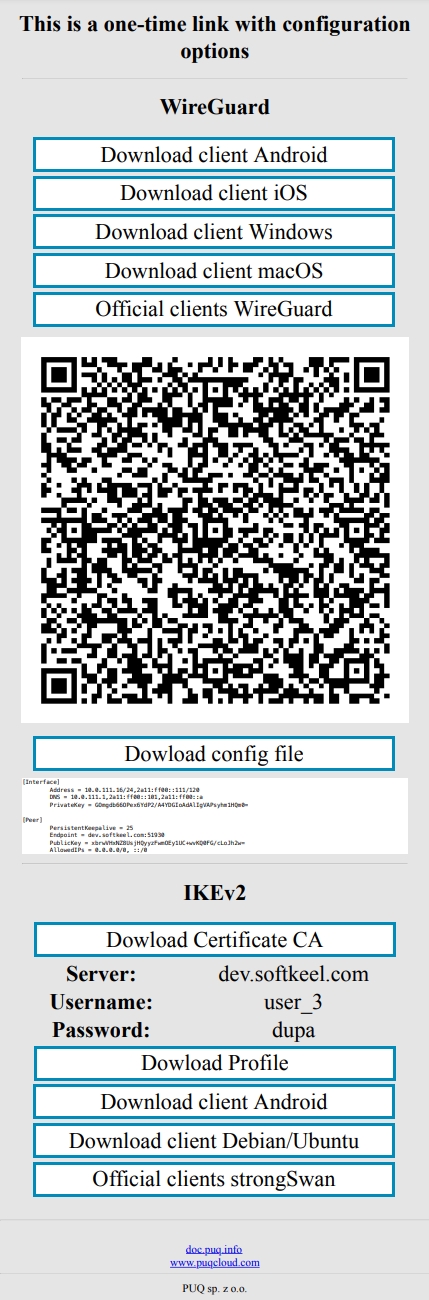
One-time link helps to transfer the VPN connection configuration to the client in a secure way and allows you to greatly simplify the setup of a new connection.
In order for one-time links to work, you need to have an SSL certificate installed on the PUQVPNCP panel.
Otherwise, the connection will not be encrypted, which means that the transmitted data about the VPN connection is at risk of being intercepted.
It is possible to automatically generate links via API. If you have a panel license, you can use it. There is also a [ready-made solution for the WHMCS panel](https://doc.puq.info/books/wireguard-business-vpn-whmcs-module "WireGuard Business-VPN WHMCS module") that allows you to automate this process.
Attention, it is strongly recommended not to send one-time links through public messengers or mail systems. Such systems tend to enter this link for analysis, and naturally, after such an action, this link will not work for the end user.
One-time link is fully customizable, you can insert your logo, text, links to instructions, links to VPN clients, etc.
What does a one-time link look like?
SO: [https://dev.softkeel.com/otl/6d0ab61682230552427c45ba50f5c925439ac7c6334f6477cdd4a1e745c57425d9b9f8cc4379dda8](https://dev.softkeel.com/otl/6d0ab61682230552427c45ba50f5c925439ac7c6334f6477cdd4a1e745c57425d9b9f8cc4379dda8)
| [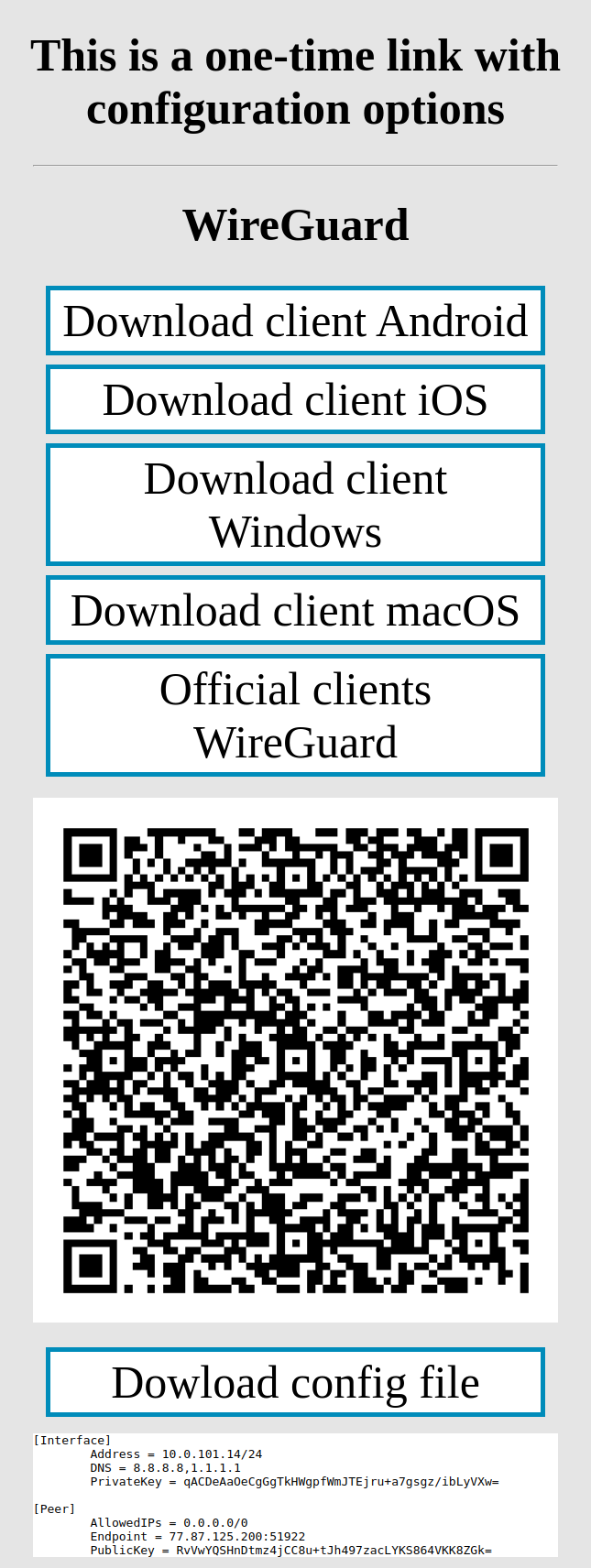](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928183751.png)
| [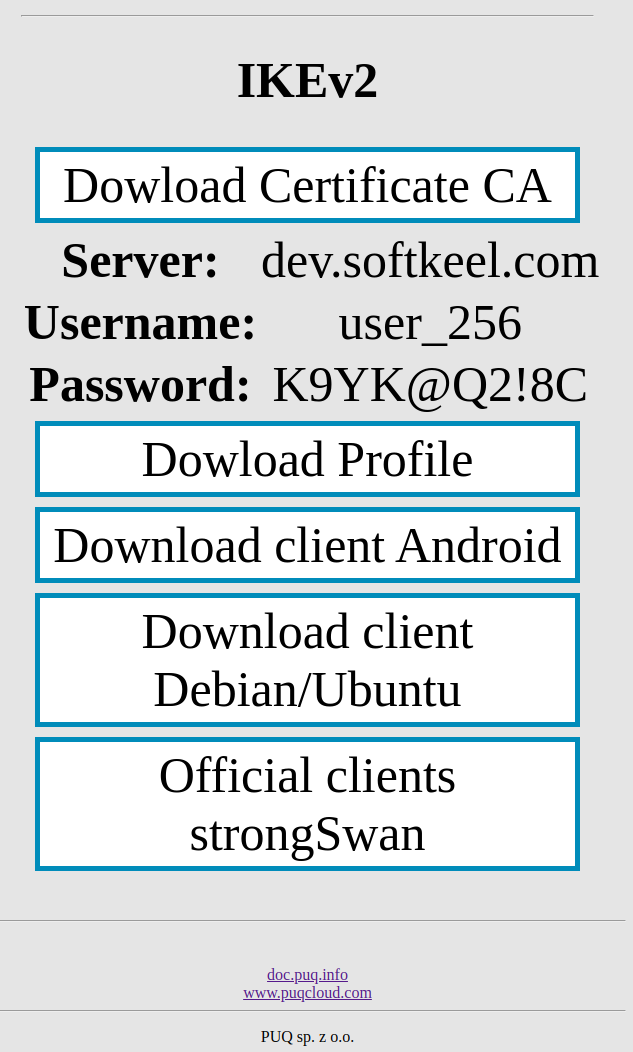](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928187032.png) |
#####
##### To get One-time link, you need to generate it per client manually (if you do not use the automation mechanisms mentioned earlier). Go to VPN Accounts and add/edit an account.
[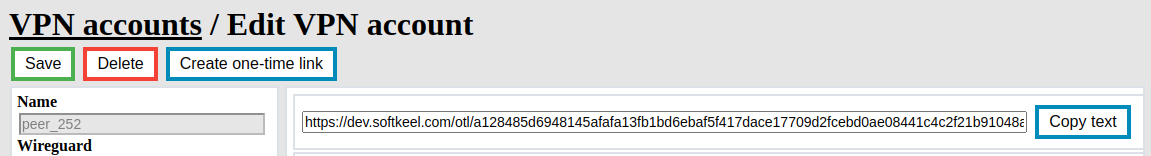](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928409880.png)
# Basic settings and customization
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
**One-time link is needed in order to transfer the VPN connection configuration to the client in a secure way.**
##### One-time link configuration is available in the menu item **Settings->One-time link**
[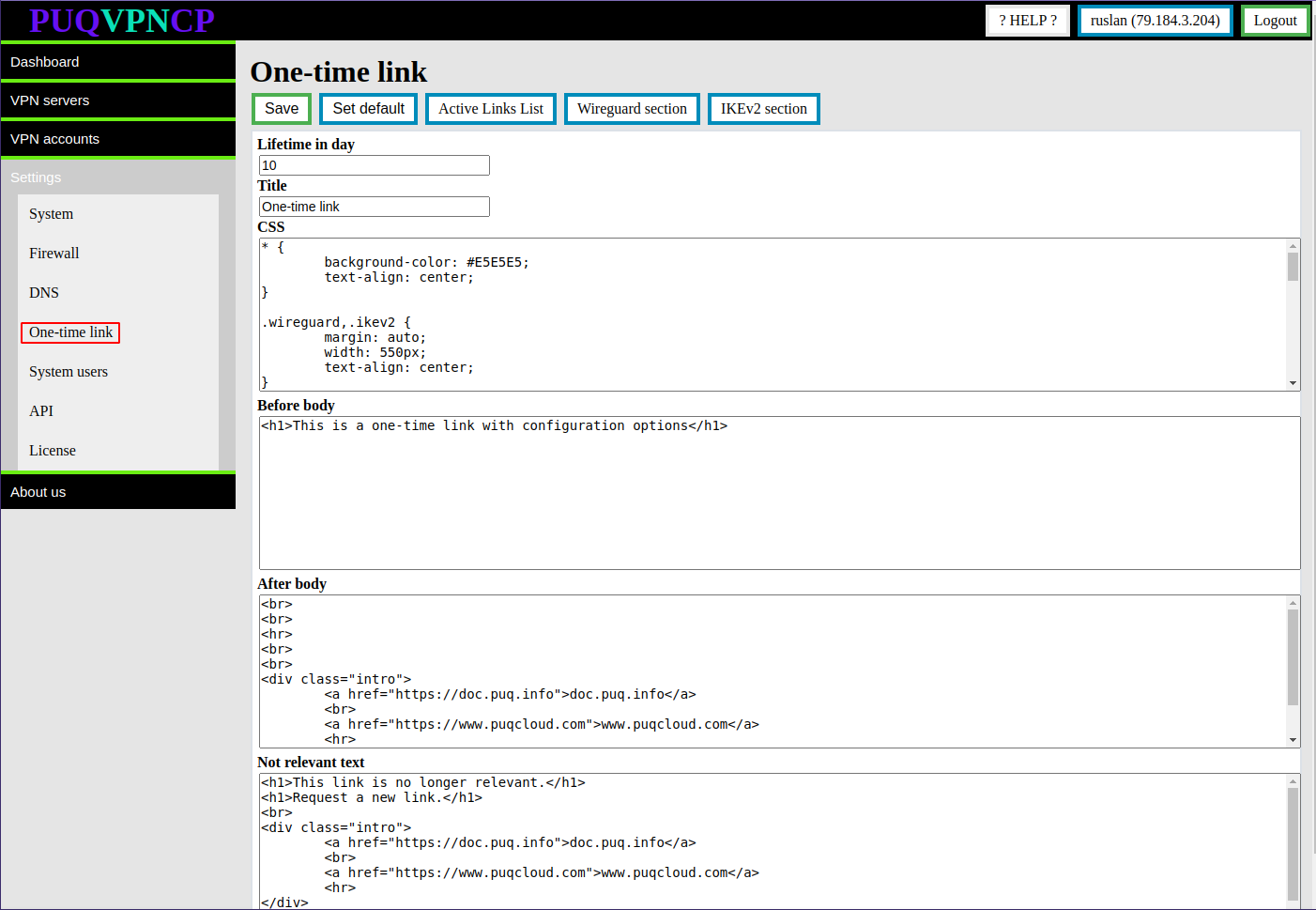](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670934358043.png)
**Lifetime in day -** Time in days during which a one-time link will be available
**Title -** The title of the one-time link page
The **CSS** field contains the CSS style that will be used on the one-time link page.
In the **Before body** field, the text that will be inserted on top of the entire page of the one-time link
In the **After body** field, the text that will be inserted at the bottom of the entire page of the one-time link
**Not relevant text -** The text that will be shown if the one-time link is not available or there is no link.
To reset the default settings, click the **Set default** button
# Active Links List
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
##### To view the list of active one-time links, click the **Active Links List** button.
Option is available in menu> Settings>One-Time link.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670934894137.png)
[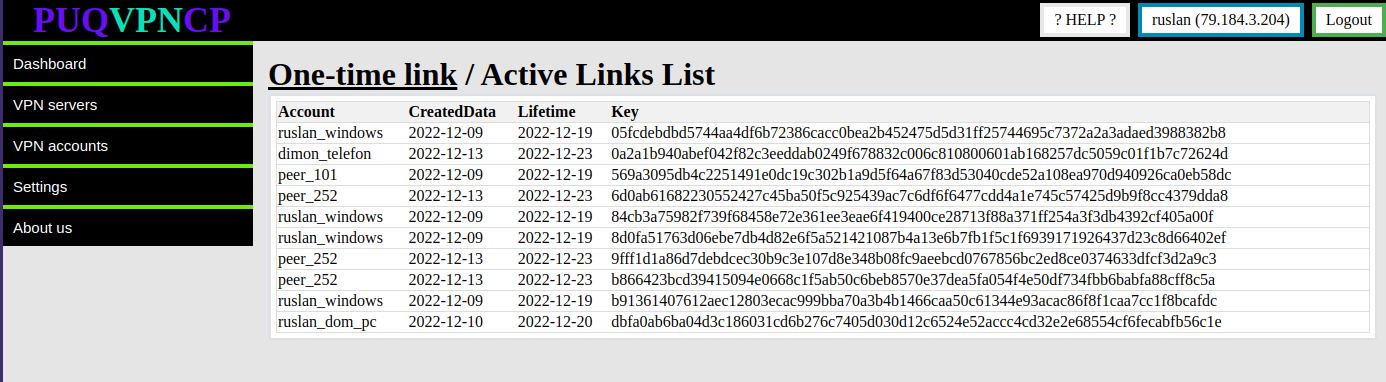](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670934898567.png)
The information that is available is: The account to which this link is intended, date of creation, date of expiration and key.
# Config WireGuard section
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
To go to the WireGuard sections, click on the **Wireguard section** button
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670935123225.png)
[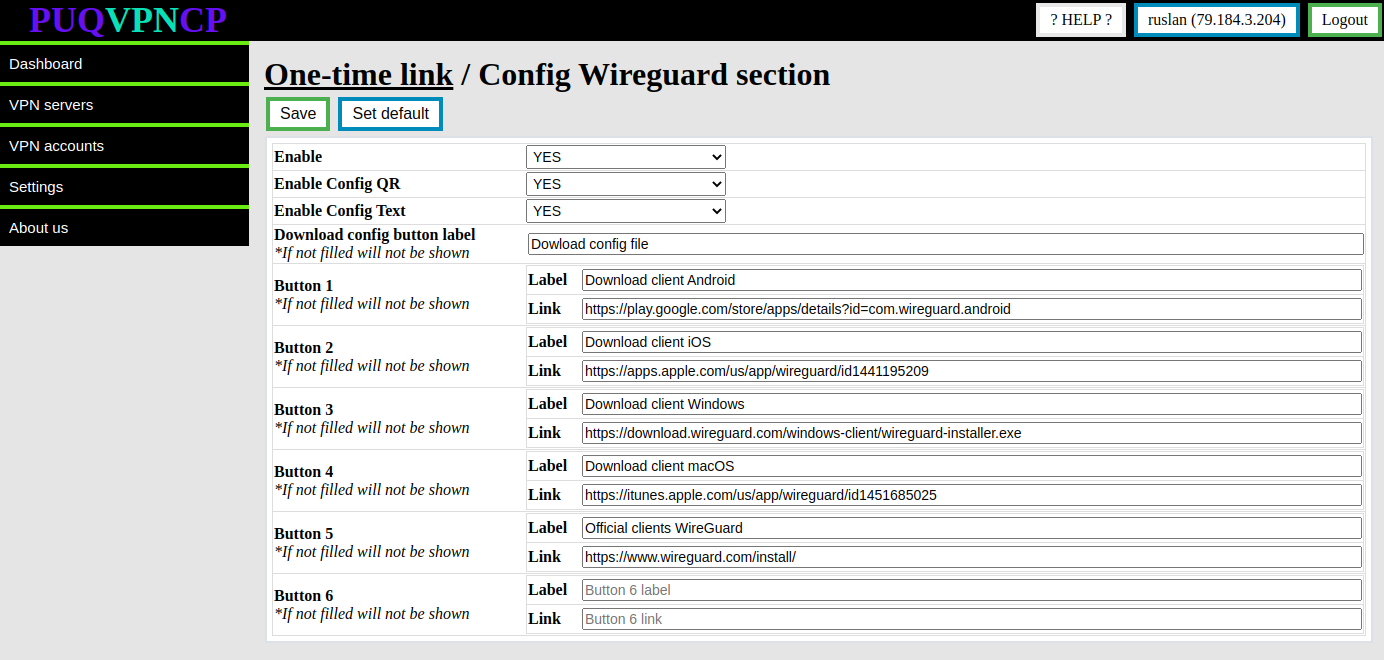](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670935127706.png)
**Enable** - Whether or not to show the **WireGuard** section in a one-time link
**Enable Config QR -** Whether or not to show the **WireGuard** configuration QR code section in a one-time link
**Enable Config Text -** Whether or not to show the **WireGuard** configuration text section in a one-time link
**Download config button label -** The name of the button that allows you to download the WireGuard configuration (if not filled, the button will not be shown)
**Button 1-6 -** Custom buttons in the **WireGuard** section (if not filled, the button will not be shown)
# Config IKEv2 section
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
To go to the WireGuard sections, click on the **IKEv2 section** button
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670935479266.png)
[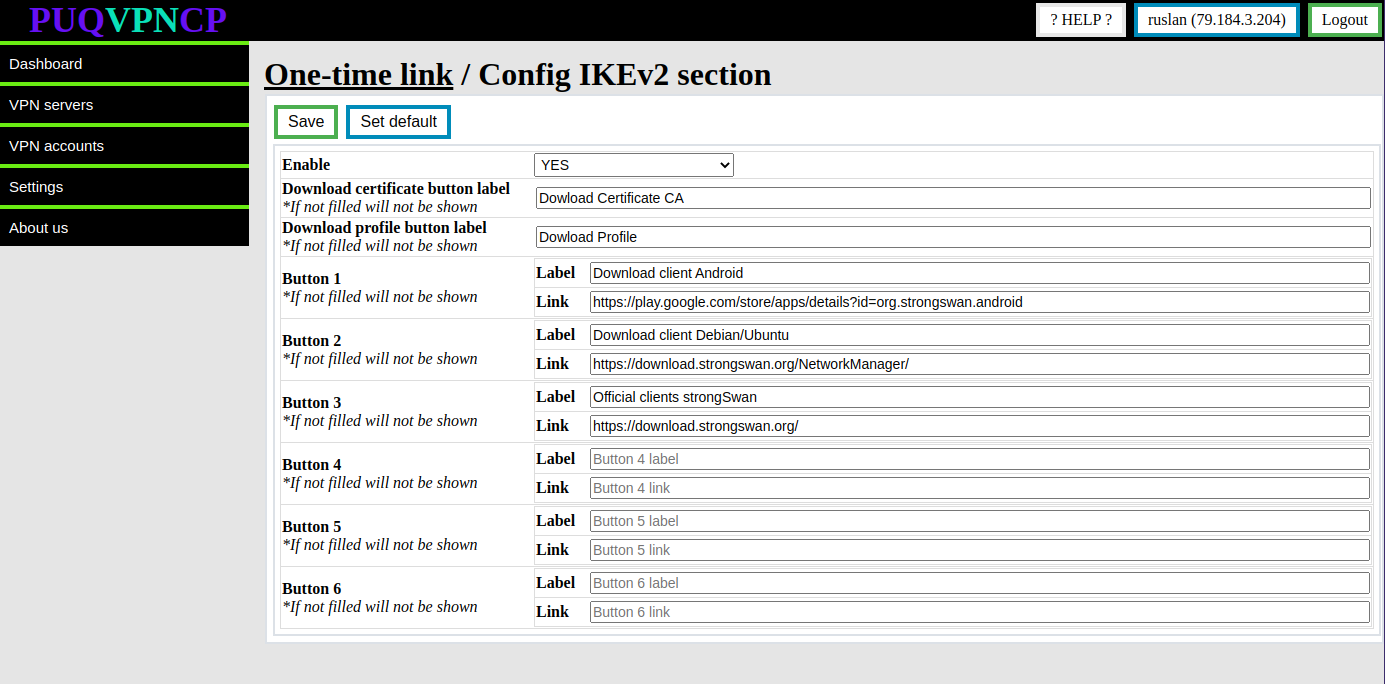](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670935498148.png)
**Enable** - Whether or not to show the **IKEv2** section in a one-time link
**Download certificate button label -** The name of the button that allows you to download the **CA ertificate** (if not filled, the button will not be shown)
**Download profile button label -** The name of the button that allows you to download the **configuration profile** (if not filled, the button will not be shown)
**Button 1-6 -** Custom buttons in the **IKEv2** section (if not filled, the button will not be shown)
# Get One-time link
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to get a one-time link, select the required account and click the **Create one-time link** button
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671011974508.png)
[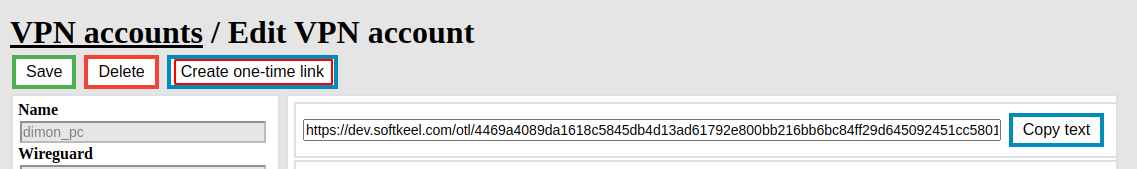](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671012006882.png)
Copy the link and pass it on safely.
# WireGuard clients configuring
# WireGuard Official clients
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
Our solution works great with official client programs. We strongly invite you to use them.
| [](https://panel.puqcloud.com/index.php?rp=/store/puqvpn "https://panel.puqcloud.com/index.php?rp=/store/puqvpn") | [](https://www.wireguard.com/ "https://www.wireguard.com/") |
#### You can download from the [https://www.wireguard.com/install/](https://www.wireguard.com/install/)
Please always download latest versions. The following list is intended as a general direction only.
- - - - - -
#### Windows \[7, 8.1, 10, 11, 2008R2, 2012R2, 2016, 2019, 2022 – v0.5.3\]
[Download Windows Installer](https://download.wireguard.com/windows-client/wireguard-installer.exe)
[Browse MSIs](https://download.wireguard.com/windows-client/)
- - - - - -
#### macOS \[[app store](https://itunes.apple.com/us/app/wireguard/id1451685025?ls=1&mt=12) – v1.0.15\]
[Download from App Store](https://itunes.apple.com/us/app/wireguard/id1451685025?ls=1&mt=12)
- - - - - -
#### Android \[[play store](https://play.google.com/store/apps/details?id=com.wireguard.android) – vunknown – out of date & [f-droid](https://f-droid.org/en/packages/com.wireguard.android/) – v1.0.20220516\]
[Download from Play Store](https://play.google.com/store/apps/details?id=com.wireguard.android)
[Download from F-Droid](https://f-droid.org/en/packages/com.wireguard.android/)
- - - - - -
#### iOS \[[app store](https://itunes.apple.com/us/app/wireguard/id1441195209?ls=1&mt=8) – v1.0.15\]
[Download from App Store](https://itunes.apple.com/us/app/wireguard/id1441195209?ls=1&mt=8)
- - - - - -
#### Debian/Ubuntu
```
$ sudo apt install wireguard
```
- - - - - -
# Android WireGuard client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to connect to a VPN, follow these steps:
1. Open the link you received in a browser to get instructions and configuration for your new VPN connection. And you will see the following page in the browser window
[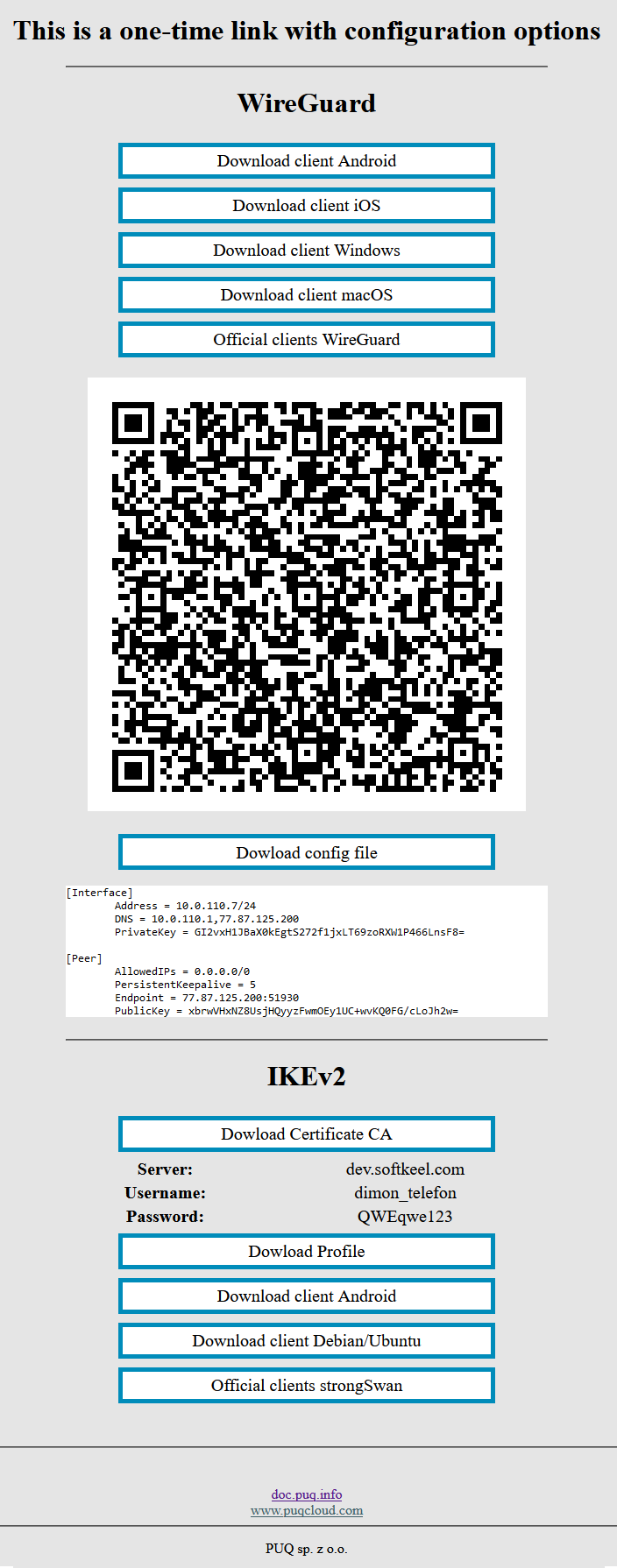](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928539397.png)
2. Since we are setting up a connection for an android device, we need the WireGuard client for android. To download the client on your phone, open the link on your mobile device and click "Download client Android".
[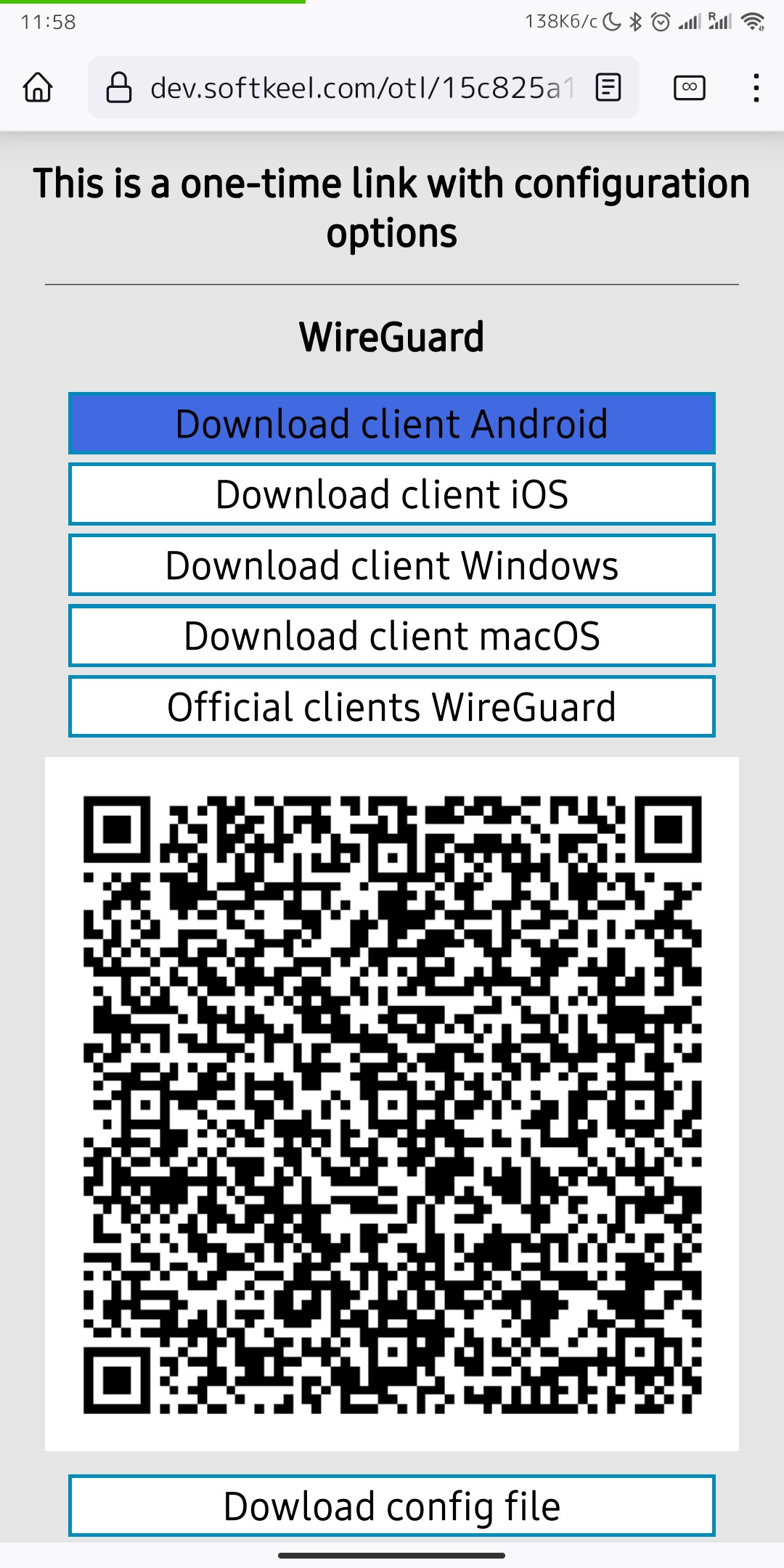](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670931428322-mozilla-firefox.jpg)
3. After you click on the "Download client Android" button, your application store will open, where you need to install your client for Android. Click "Install" to install the application on your mobile device.
[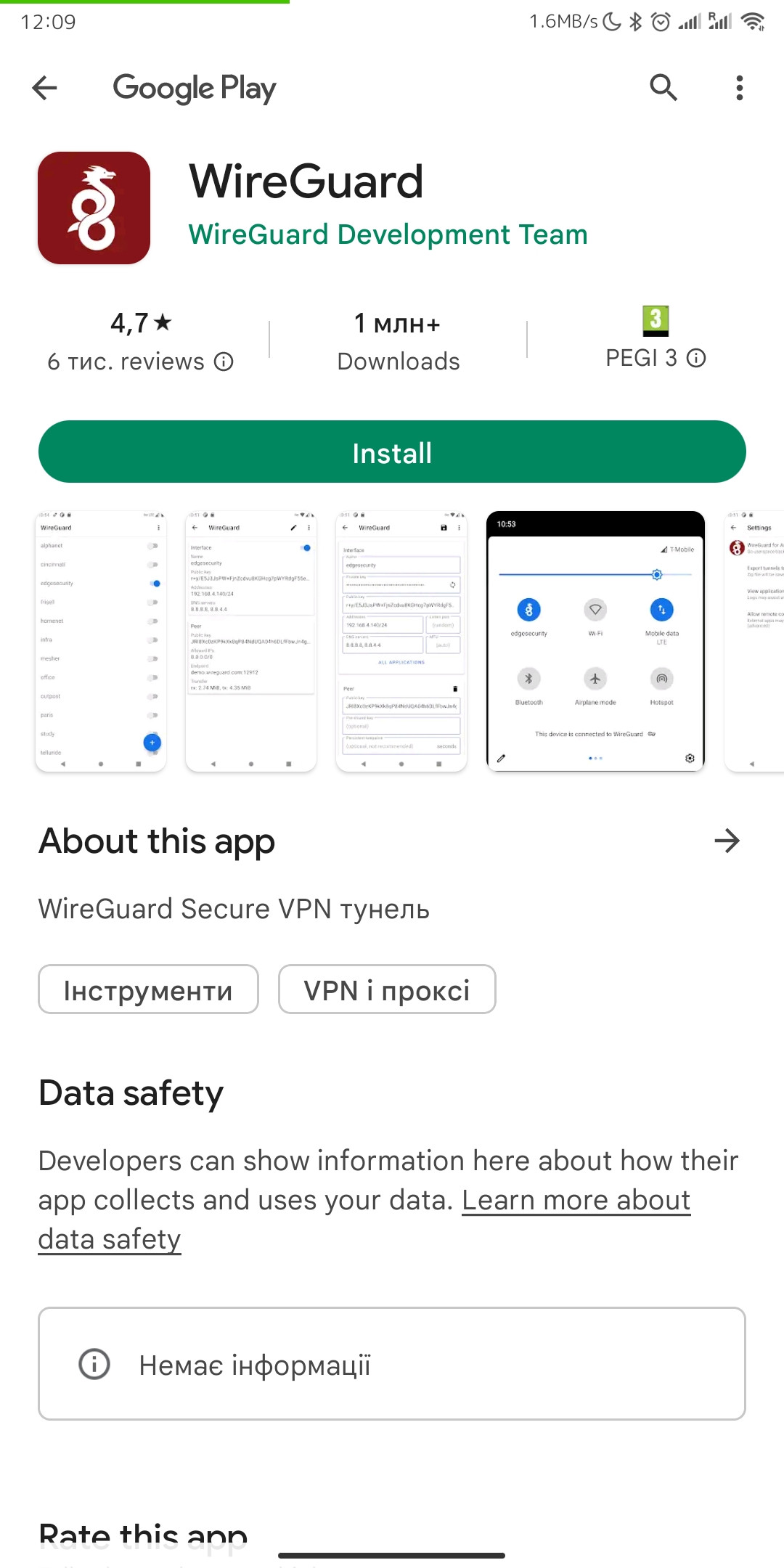](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670931747373-android-vending.jpg)
4. After completing the app installation, open the app to configure your VPN connection.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670931979459-android-vending.jpg)
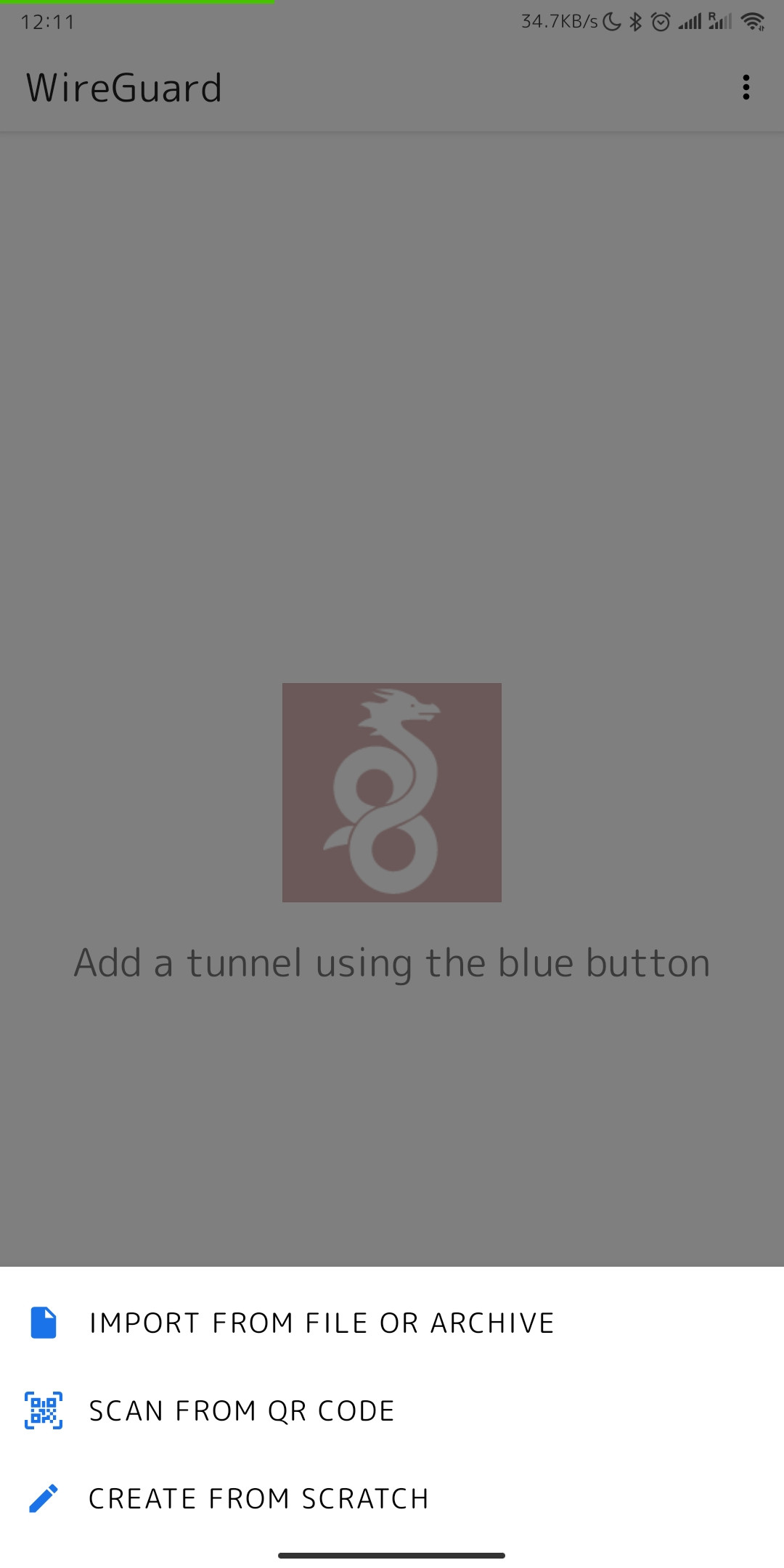
5. This is how the main window of the application looks like, which has no configured connections. To set up a new VPN connection, you must press the plus button.
[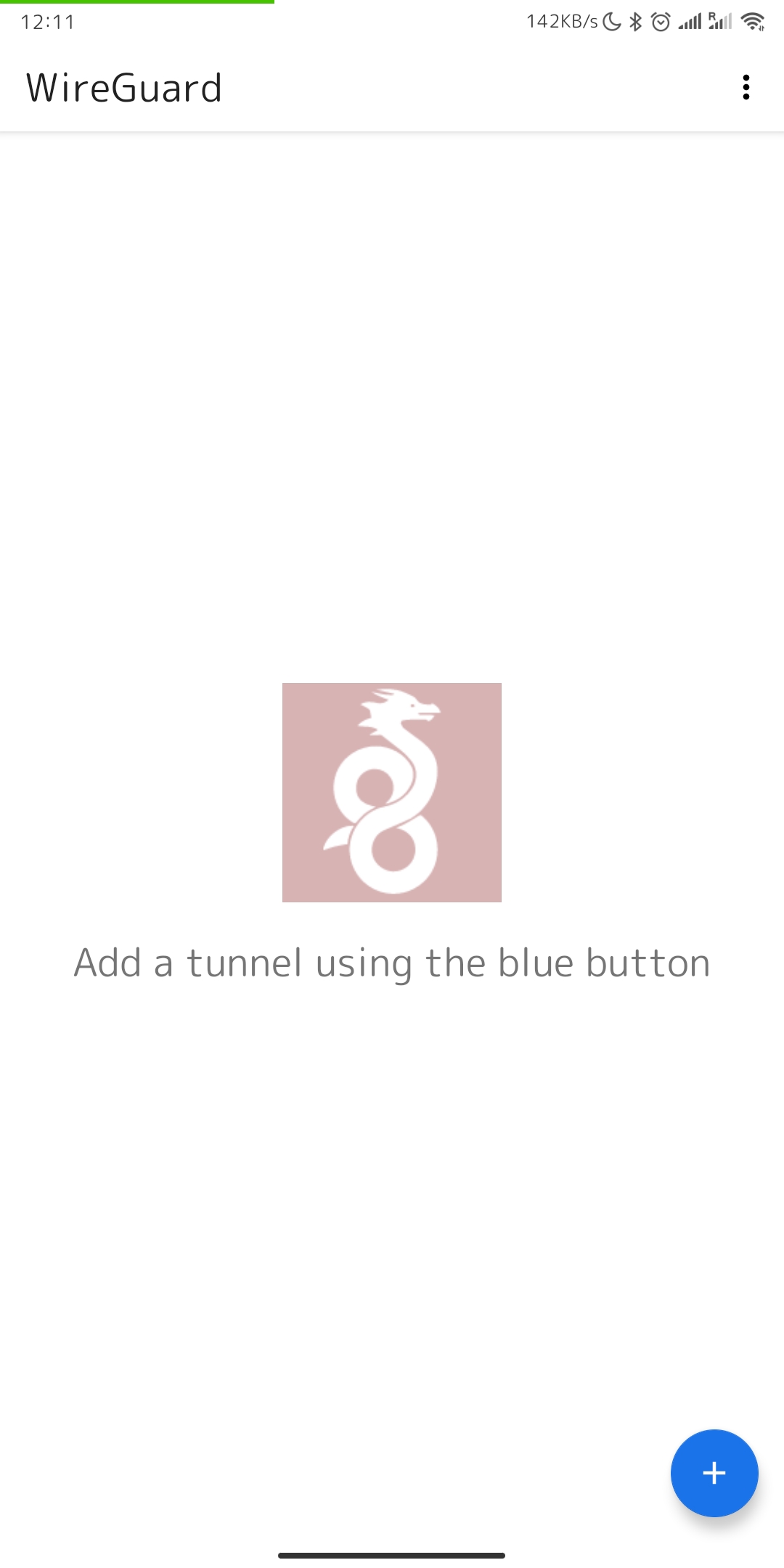](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670932117112-wireguard-android.jpg)
6. After you click on the button that allows you to create a new connection, you will be presented with several options. Now we will use the QR code scanning method. Click on the "SCAN FROM QR CODE" button to start scanning.
Later in this manual, **in point number 13**, we will look at creating a connection using a configuration file.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670932306868-wireguard-android.jpg)
7. It is worth noting that if you are using the application for the first time, your device will ask you if you can allow access to the camera. You need to allow access to the camera, otherwise scanning will not be possible.
[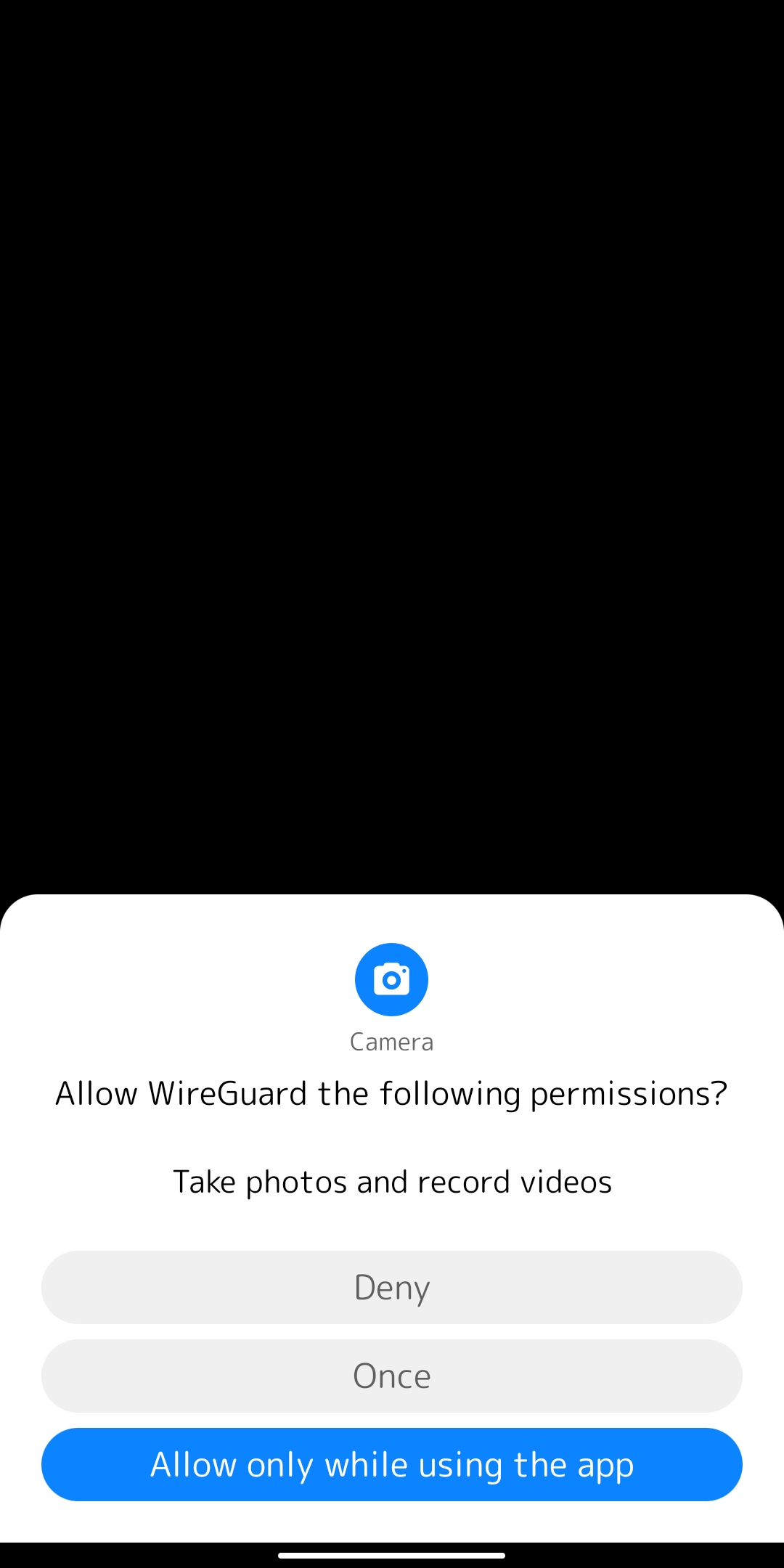](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670932444235-lbe-security-miui.jpg)
8. After you can already start scanning and see that your device is ready, point your camera at the QR code you received.
[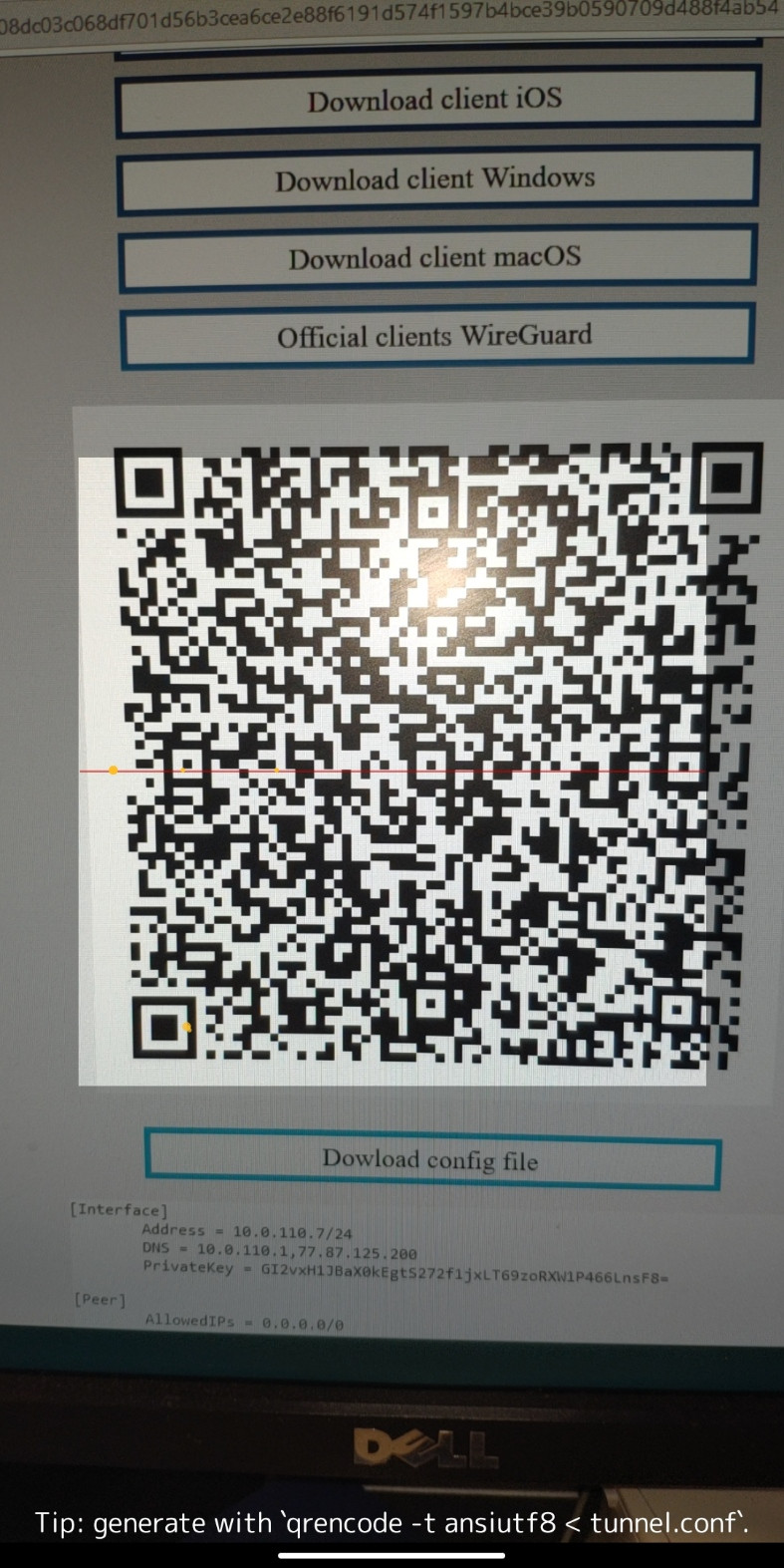](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670932633969-wireguard-android.jpg)
9. After scanning the code, when the scan was successful, the application will prompt you to enter a name for the new connection. Enter a name and save the new configuration by clicking on the "CREATE TUNEL" button.
[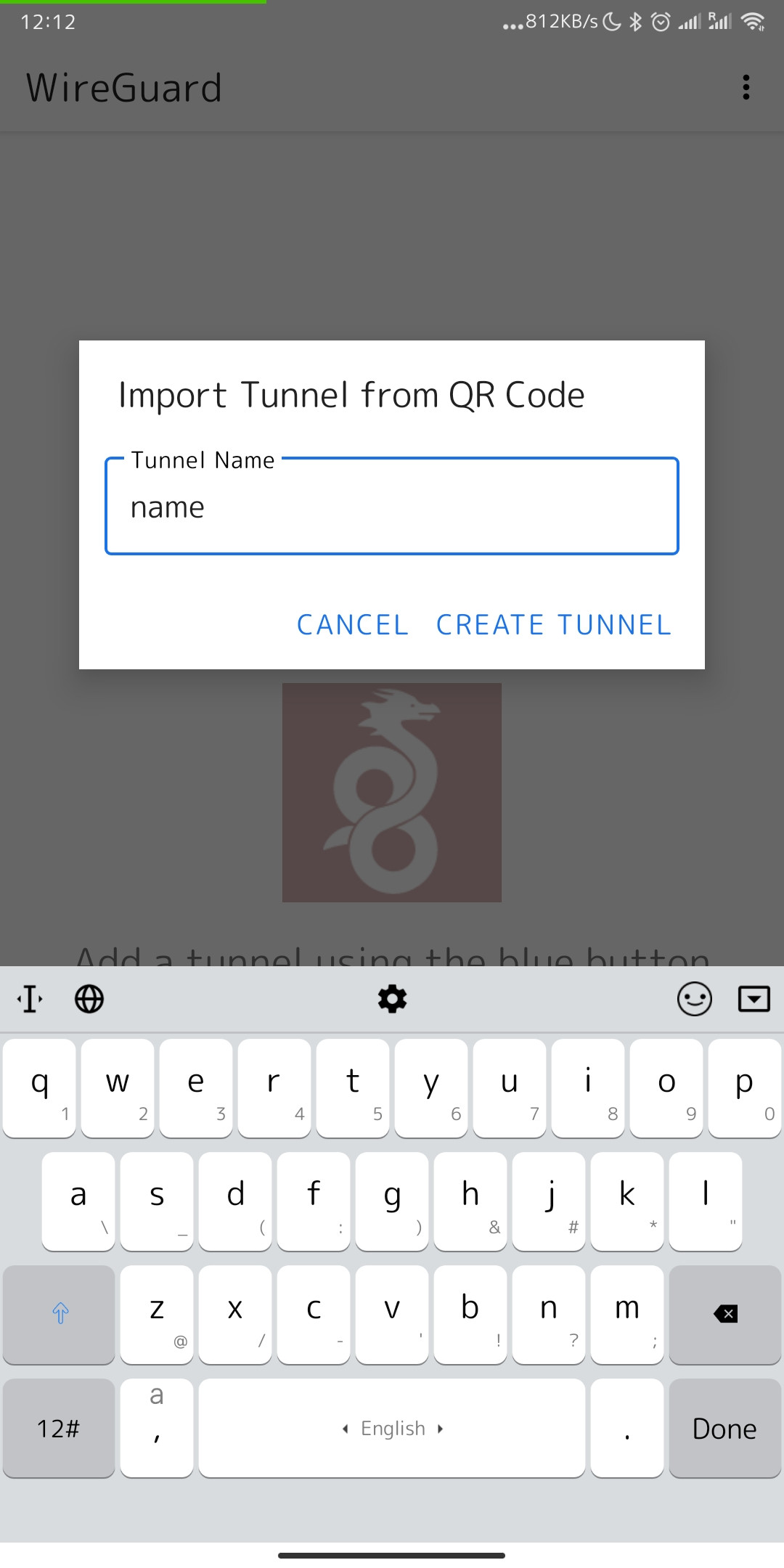](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670932948416-wireguard-android.jpg)
10. After you save your new connection, you will see a list of your VPN connections. Find the required connection to activate it and switch the slider to activation mode.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670933284570-wireguard-android.jpg)
11. It is worth noting that if you have activated your connection for the first time, the system will ask you if it is possible to add such a connection, you must agree that a new connection will be established in order to establish a new connection.
[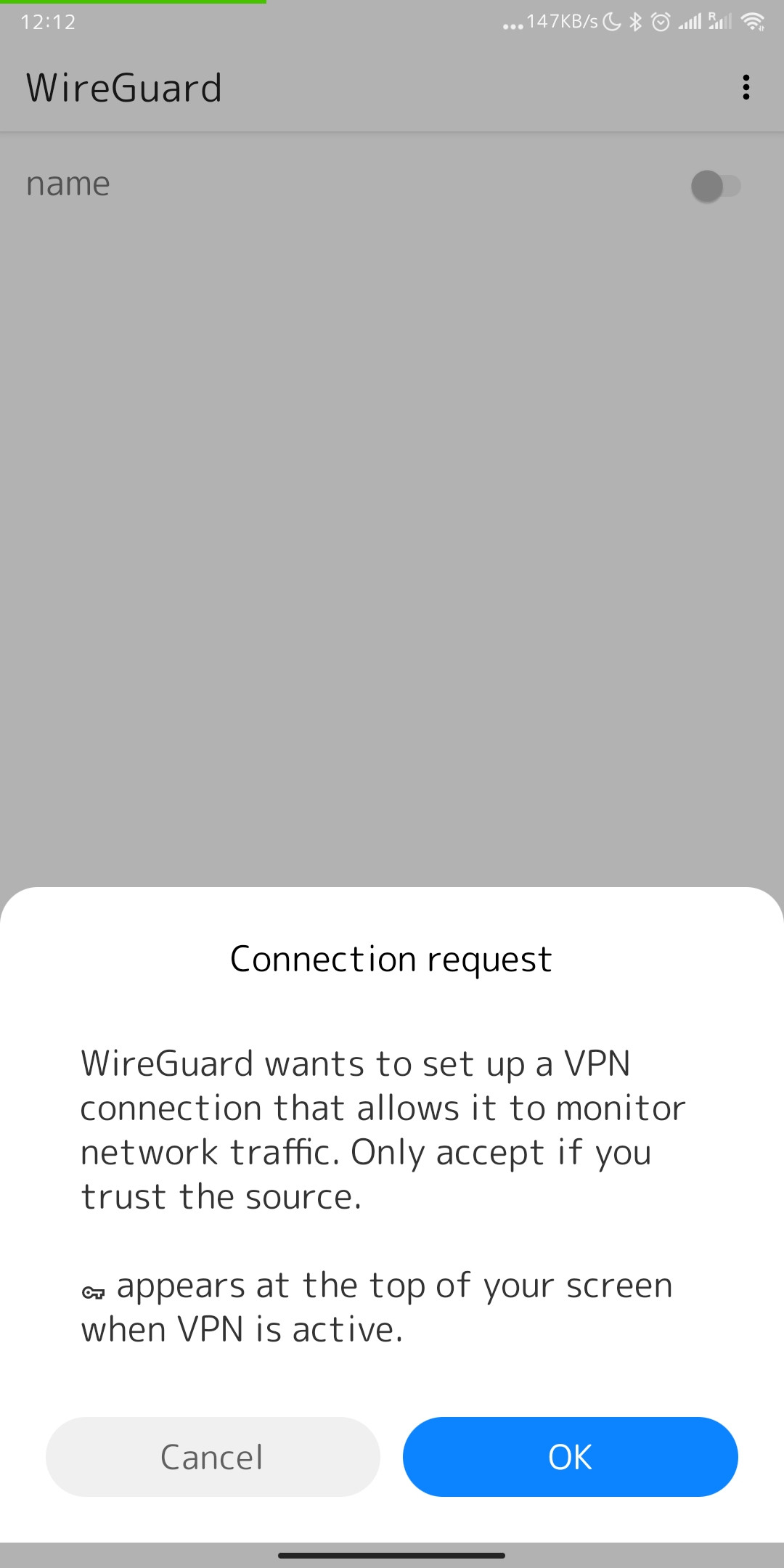](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670933447131-android-vpndialogs.jpg)
12. And so, now your connection is established, you can notice that the slider is in activation mode and you can see a special system icon in the notification bar, which indicates that the VPN connection is activated.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670933929090-wireguard-android.jpg)
13. To create a connection using a configuration file: You need to download the configuration file to your mobile device. To download this file, click on the "Dowload config file" button.
[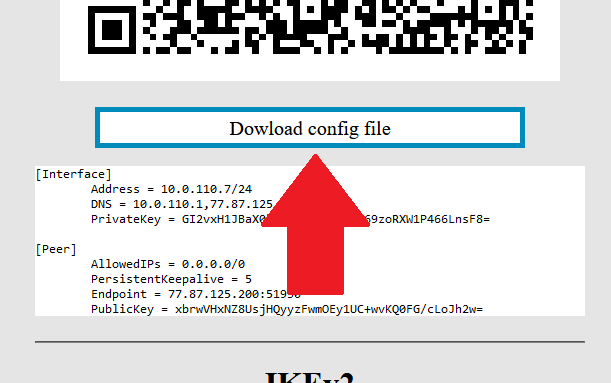](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670935270396.png)[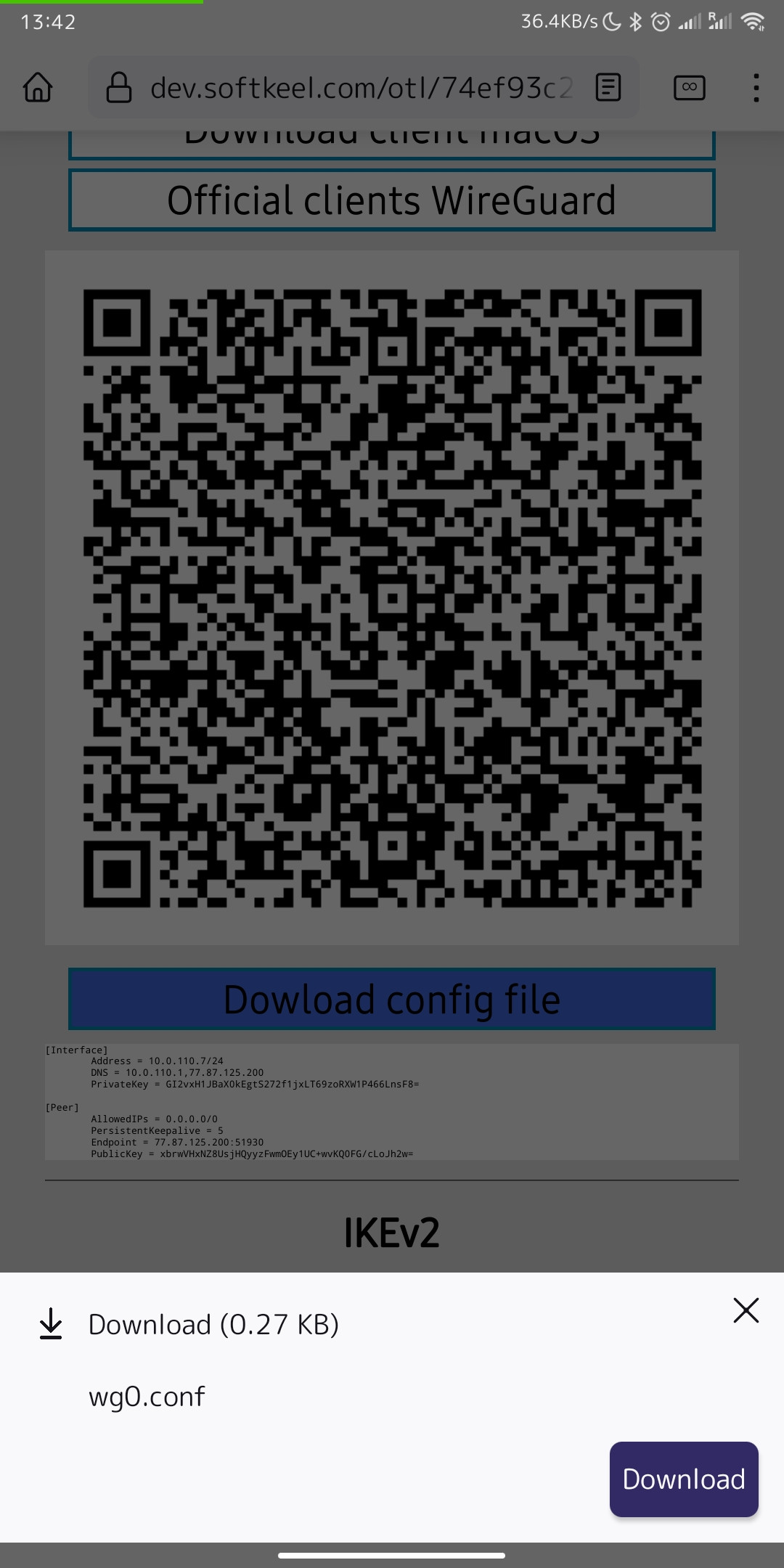](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670935726727-mozilla-firefox.jpg)
14. Once your configuration file has been downloaded to your device, you need to proceed. You need to return to the "WireGuard" application to import your configuration file. Click "IMPORT FROM FILE OR ARCHIVE" to start importing the configuration file.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670936080006-wireguard-android.jpg)
15. Next, you will be prompted to find your configuration file. You need to find the configuration file and select it.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671108793041.png)
16. After you select your configuration file, the connection will be created.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670936447601-wireguard-android.jpg)
17. To connect to a new VPN connection, you need to activate the slider opposite to the activate position.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670936682420.png)
# macOS WireGuard client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
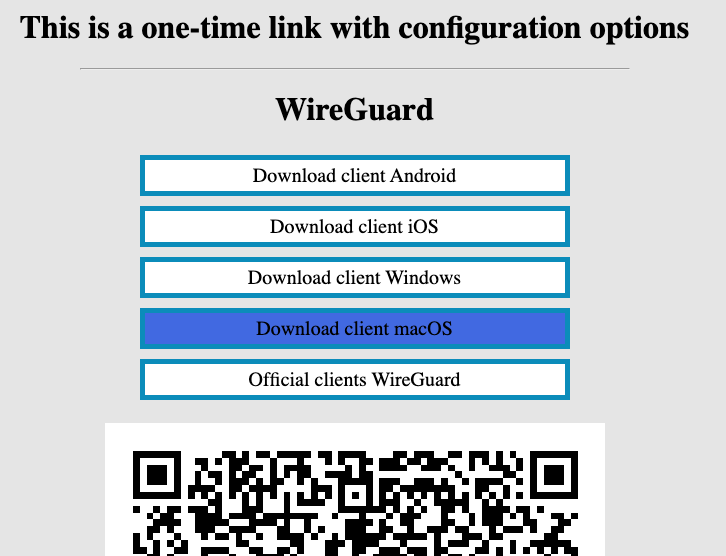
In order to connect to a VPN, follow these steps:
1. Open the link you received in a browser to get instructions and configuration for your new VPN connection. And you will see the following page in the browser window
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928539397.png)
2. In order to start the configuration you need to download the configuration file. To download the configuration file, click the "Dowload config file" button.
[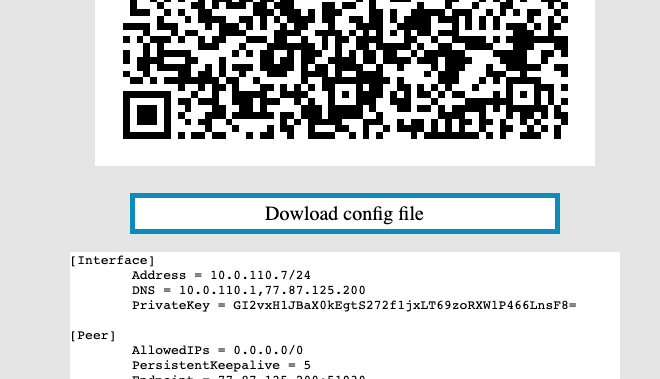](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940579264-46-38.png)
3. Save the file to downloads or any other place to import later.
4. Since we are setting up a connection for an android device, we need the WireGuard client for macOS. To download the client on your device, open the link on your device and click "Download client macOS".
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940104810-39-21.png)
5. After you click on the "Download client macOS" button, your application store will open, where you need to install your client for macOS. Click "Get" and after "Install" to install the application on your device.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940223739.png)
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940268384.png)
6. After completing the app installation, open the app to configure your VPN connection.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940318349.png)
7. This is how the main window of the application looks like, which has no configured connections. To set up a new VPN connection, you must press the "Import tunel(s) from file" button.
[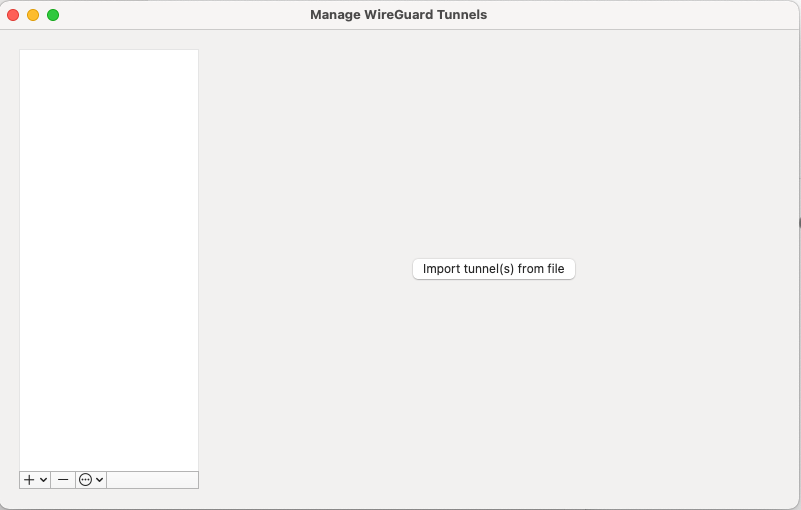](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940440973-46-12.png)
8. Next, you will be prompted to find your configuration file. You need to find the configuration file and select it.
[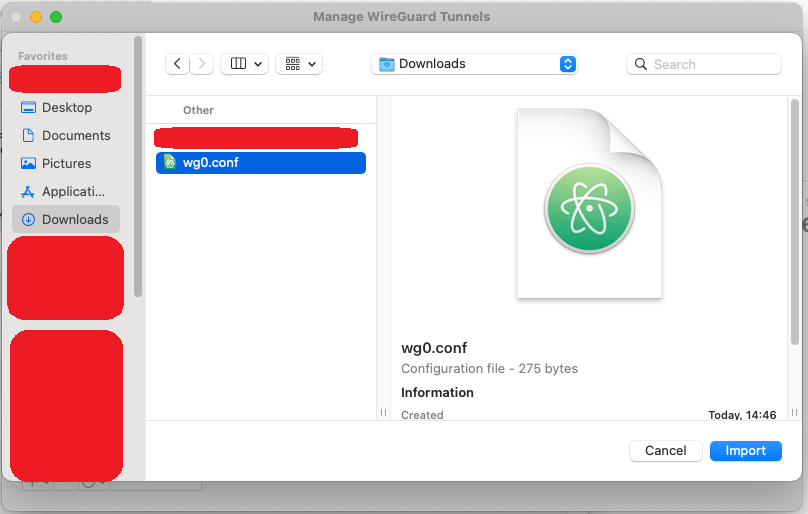](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940871659.png)
9. After you select your configuration file, the connection will be created.
[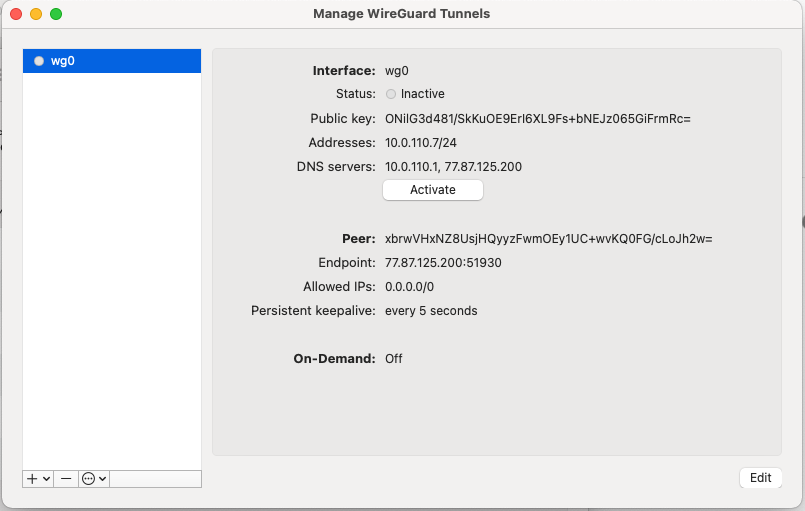](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940911751-48-49.png)
10. Click the "Activate" button. To activate your VPN connection.
[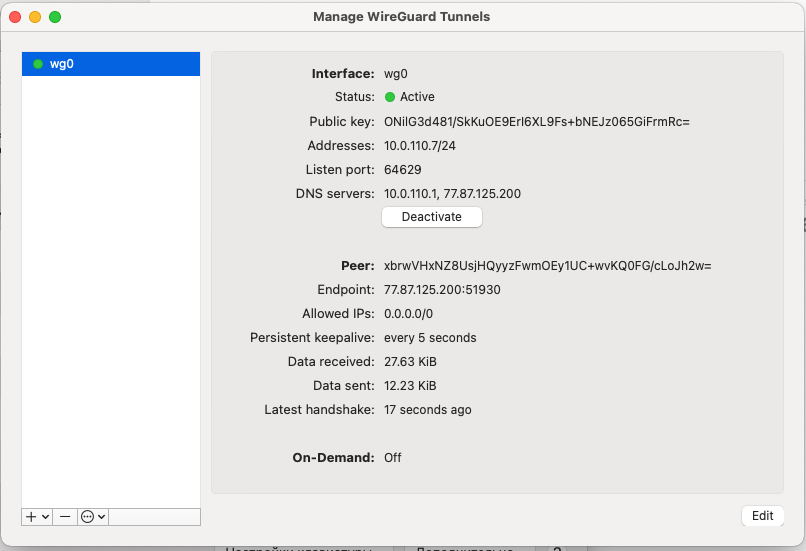](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940991508-49-39.png)
11. Congratulations. Your VPN connection is active. We can see this by looking at the system icon bar.
[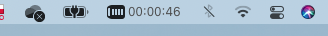](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670941094231-50-08.png)
# Windows WireGuard client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to connect to a VPN, follow these steps:
1. Open the link you received in a browser to get instructions and configuration for your new VPN connection. And you will see the following page in the browser window
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928539397.png)
2. In order to start the configuration you need to download the configuration file. To download the configuration file, click the "Dowload config file" button.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670940579264-46-38.png)
3. Save the file to downloads or any other place to import later.
4. Since we are setting up a connection for an android device, we need the WireGuard client for Windows. To download the client on your device, open the link on your device and click "Download client Windows".
[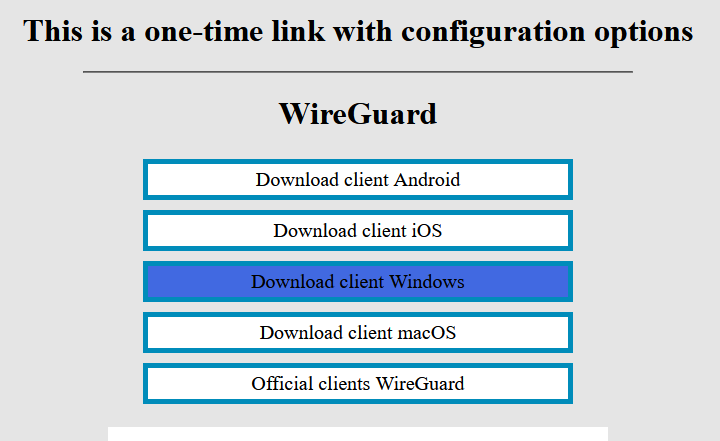](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670942403983.png)
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670942450081.png)
5. Install the app on your device.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670942686661.png)
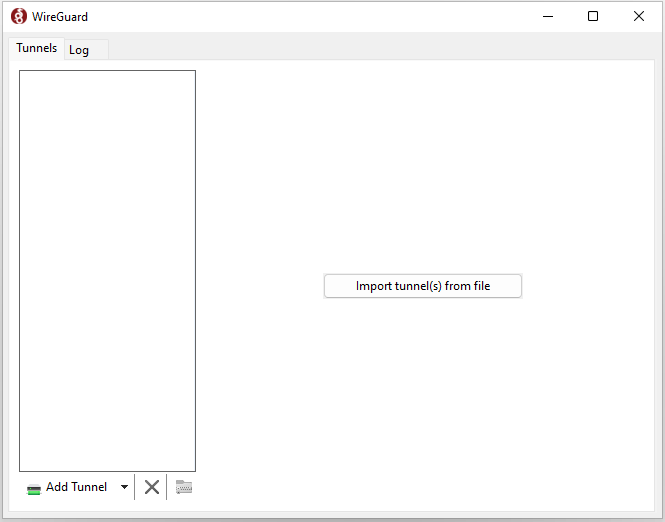
6. This is how the main window of the application looks like, which has no configured connections. To set up a new VPN connection, you must press the "Import tunel(s) from file" button.
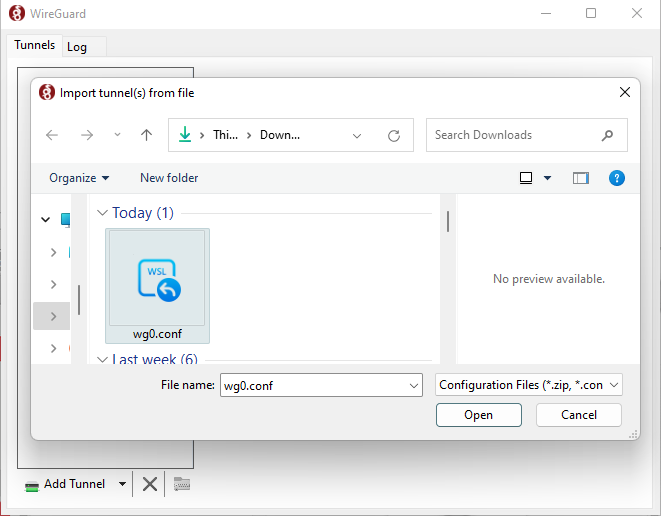
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670942755221.png)
7. Next, you will be prompted to find your configuration file. You need to find the configuration file and select it.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670942837134.png)
8. After you select your configuration file, the connection will be created.
[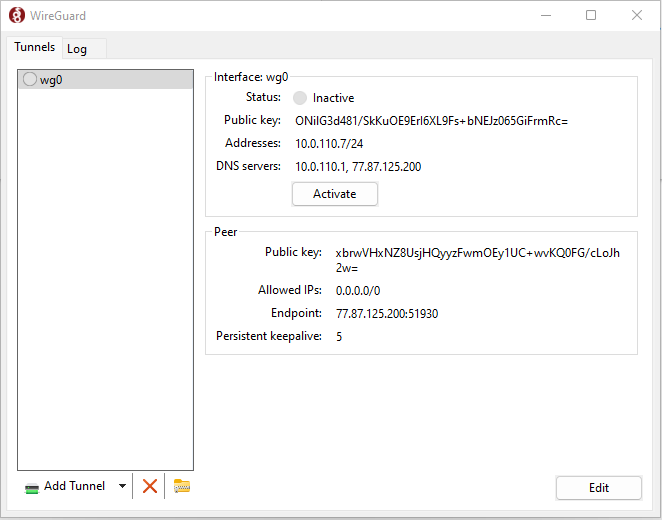](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670942895225.png)
9. Click the "Activate" button. To activate your VPN connection.
[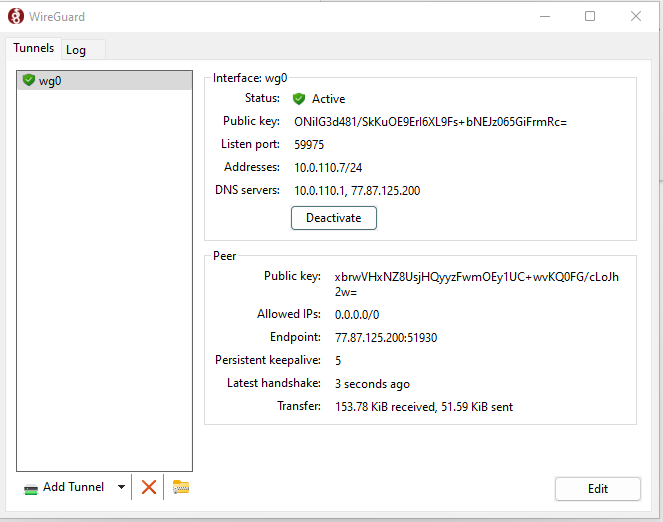](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670942931918.png)
10. Congratulations. Your VPN connection is active.
# Linux WireGuard client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to connect to a VPN, follow these steps:
1. Open the link you received in a browser to get instructions and configuration for your new VPN connection. And you will see the following page in the browser window
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928539397.png)
2. In order to start the configuration you need to download the configuration file. To download the configuration file, click the "Dowload config file" button.
[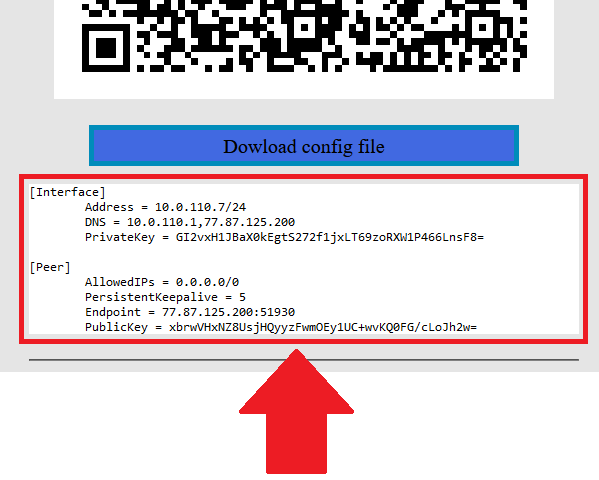](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671007982861.png)
3. Save the file to downloads or any other place to import later. You can download the configuration file and move it to your server, or you can create a new file and copy the configuration text into it. We will copy the configuration text into a new file in this WireGuard client setup guide.
4. Since we are setting up a connection for an Linux device, we need the WireGuard client for Linux. To download and install the client on your device, by command `sudo apt install wireguard`
5. After installing the client, navigate to the folder `cd /etc/wireguard/` and create a configuration file. With the help of the command `nano wg0.conf`
6. Copy the configuration text into your terminal window.
[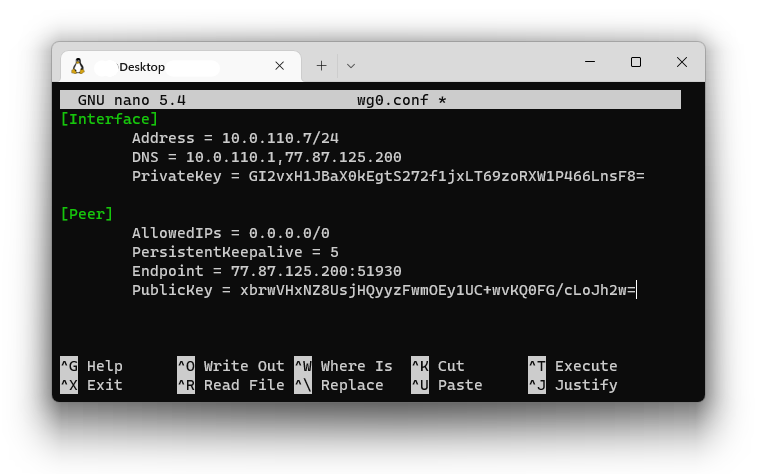](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671008968309.png)
7. Save the file, after saving the file you need to complete the connection.
Connect using the command: `sudo wg-quick up wg0`
# Mikrotik WireGuard client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## Configuring Mikrotik as an WireGuard Client.
##### Make sure you have an up to date **routerOS** system.
Version must be at least: 7.6
```
[admin@VPN-CLIENT] > system package print
Columns: NAME, VERSION
# NAME VERSION
0 routeros 7.6
```
##### Open a single-use shipment on the **WireGuard** section for the client's configuration request
[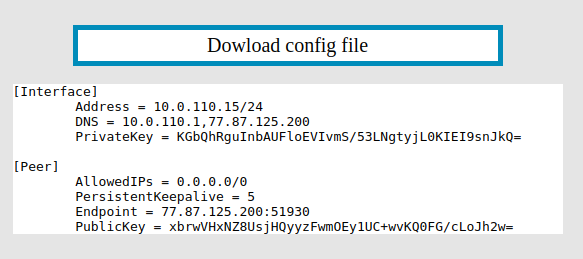](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671100595697.png)
##### Login to **Mikrotik** via Winbox
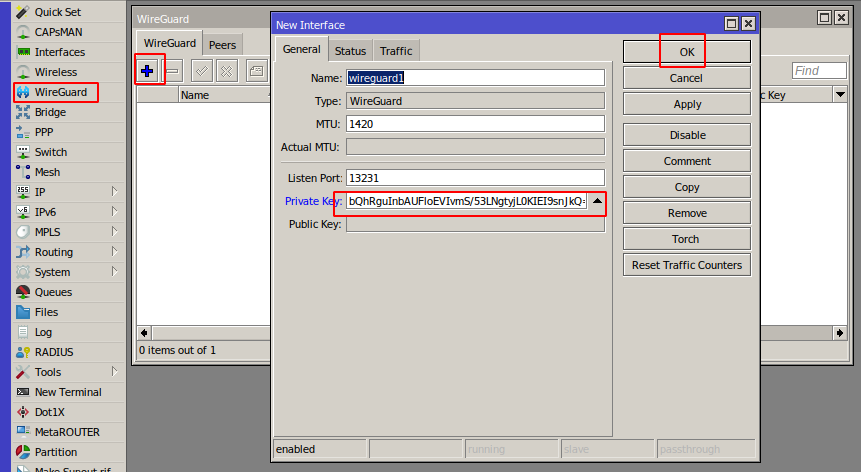
Click on the menu item **WireGuard** In the window that opens, in the **WireGuard** tab, click the plus to add a new **WireGuard** interface
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671100789370.png)
Copy the private key from the text configuration from the **\[Interface\]** section to the **PrivateKey** field in the **WireGuard** interface settings in **Mikrotik**
Click **OK** to create the interface
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671101049703.png)
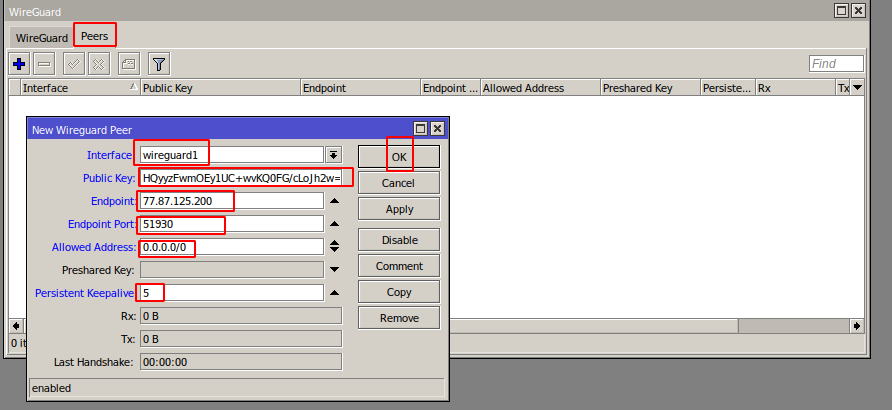
Go to the peers tab.
Click plus to add a new peer
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671101223879.png)
**Interface** - Select the previously created **WireGuard** interface
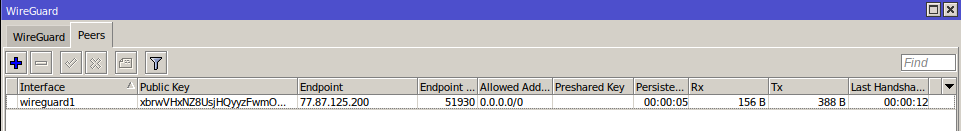
**Public key** - Copy the public key from the text configuration from the **\[Peer\]** section to the Public key field
**Endpoint** - Copy the server **address** from the text configuration from the **\[Peer\]** section to the endpoint field
**Endpoint Port -** Copy the server **port** from the text configuration from the **\[Peer\]** section to the Endpoint Port field
**Allowed Address -** Copy **AllowedIPs** from the text configuration from the **\[Peer\]** section to the Allowed Address field
**Persistent Keepalive -** Copy the **PersistentKeepalive** from the text configuration from the **\[Peer\]** section to the Persistent Keepalive field
Click **OK** to create a peer
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671101662963.png)
##### In order to have communication with the server, you need to set the address on the **WireGuard** interface
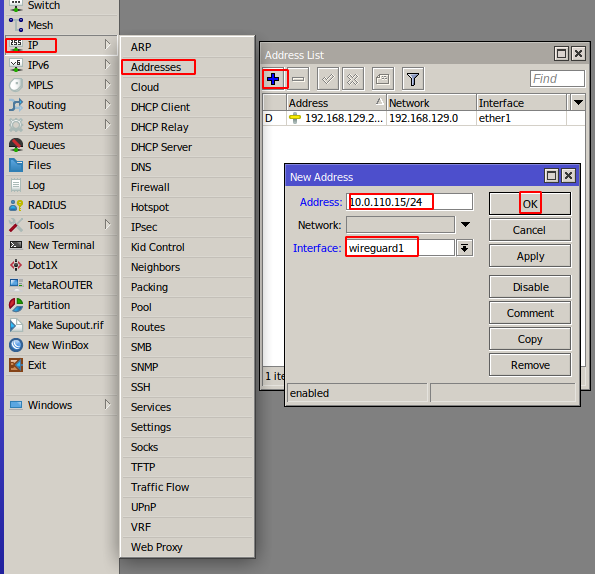
Go to the menu item **IP->Addresses** In the window that opens, click the plus to assign an IP address to the WireGuard interface
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671101826333.png)
**Addresse -** Copy the Address from the text configuration from the **\[Interface\]** section to the Address field
**Interface** - Select the previously created **WireGuard** interface
Press the OK button to confirm
[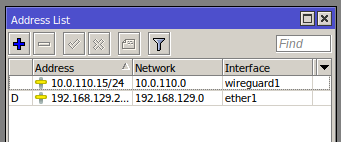](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671102046038.png)
You also need to configure the traffic routes you need at your discretion.
# iOS WireGuard client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to connect to a VPN, follow these steps:
1. Open the link you received in a browser to get instructions and configuration for your new VPN connection. And you will see the following page in the browser window
[](https://doc.puq.info/uploads/images/gallery/2023-07/1.png)
2. Since we are setting up a connection for an iOS device, we need the WireGuard client for iOS. To download the client on your phone, open the link on your mobile device and click "Download client iOS".
[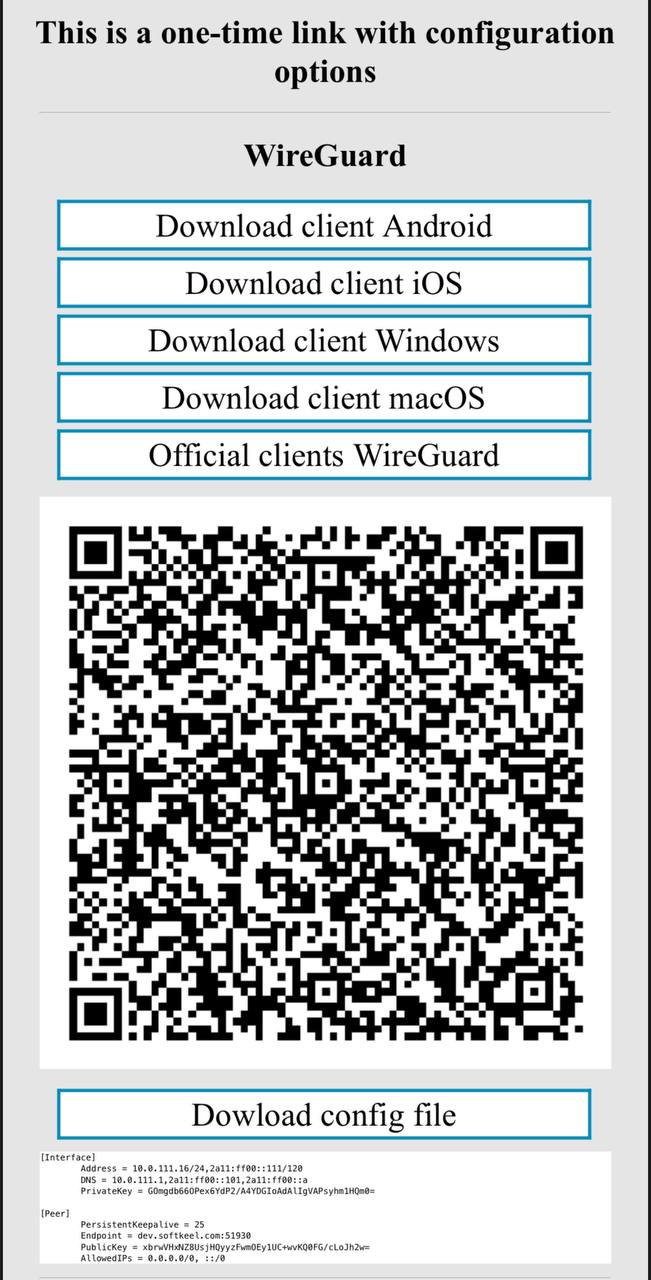](https://doc.puq.info/uploads/images/gallery/2023-07/2.jpg)
3. After you click on the "Download client iOS" button, your application store will open, where you need to install your client for iOS. Click "Install" to install the application on your mobile device.
[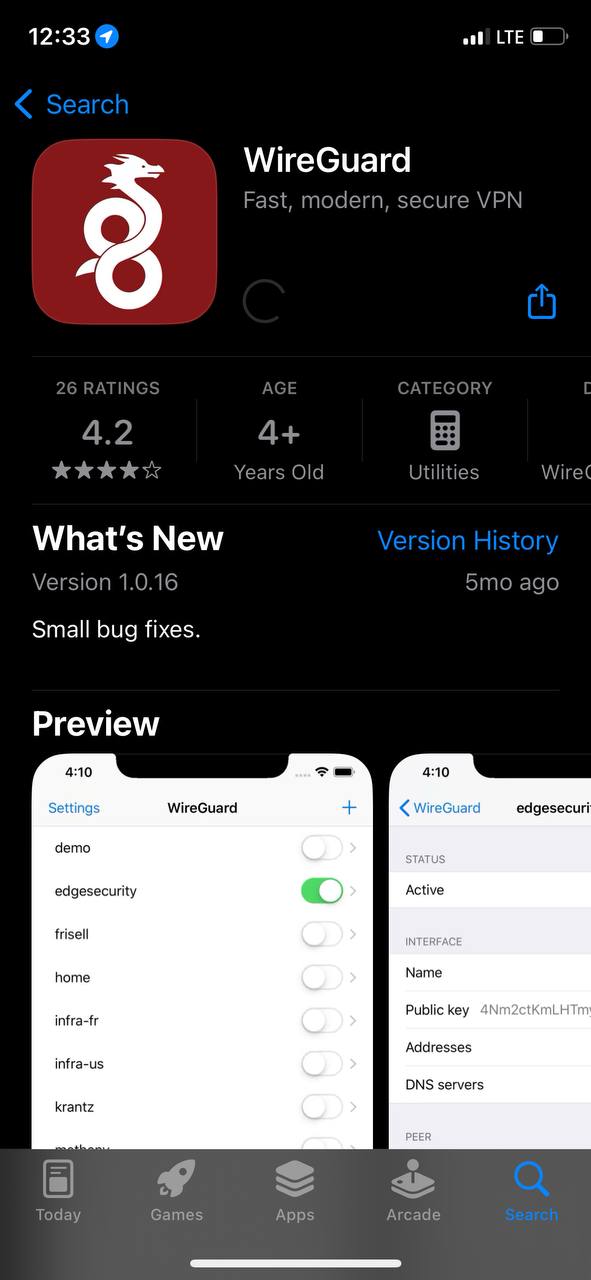](https://doc.puq.info/uploads/images/gallery/2023-07/4.jpg)
4. After completing the app installation, open the app to configure your VPN connection.
[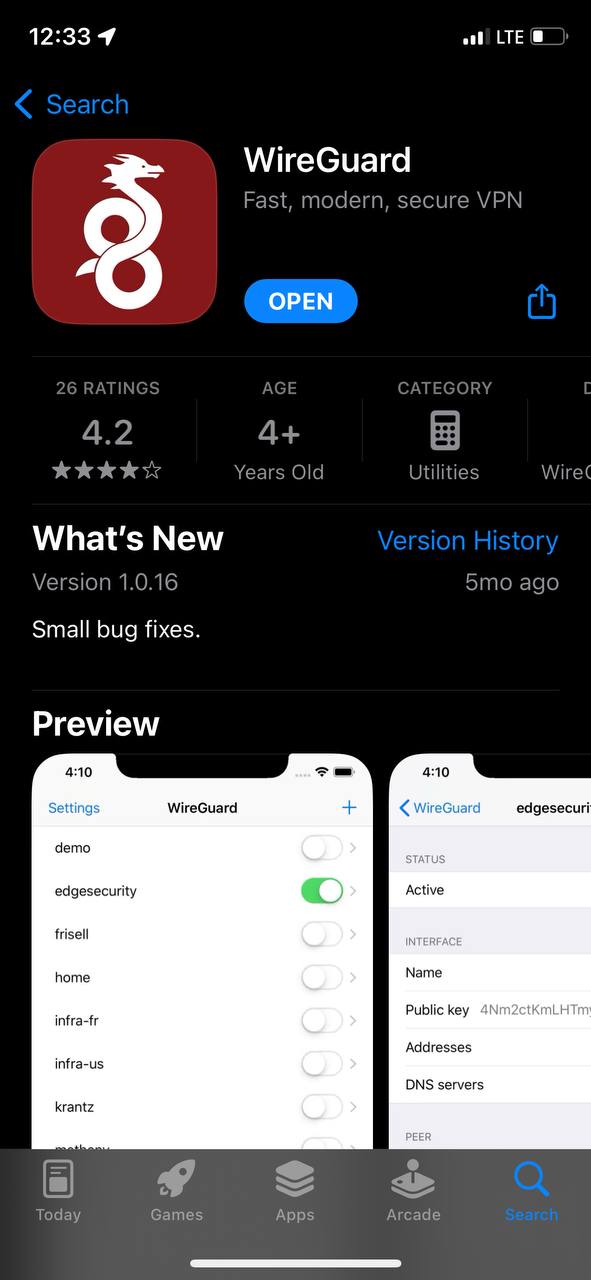](https://doc.puq.info/uploads/images/gallery/2023-07/3.jpg)
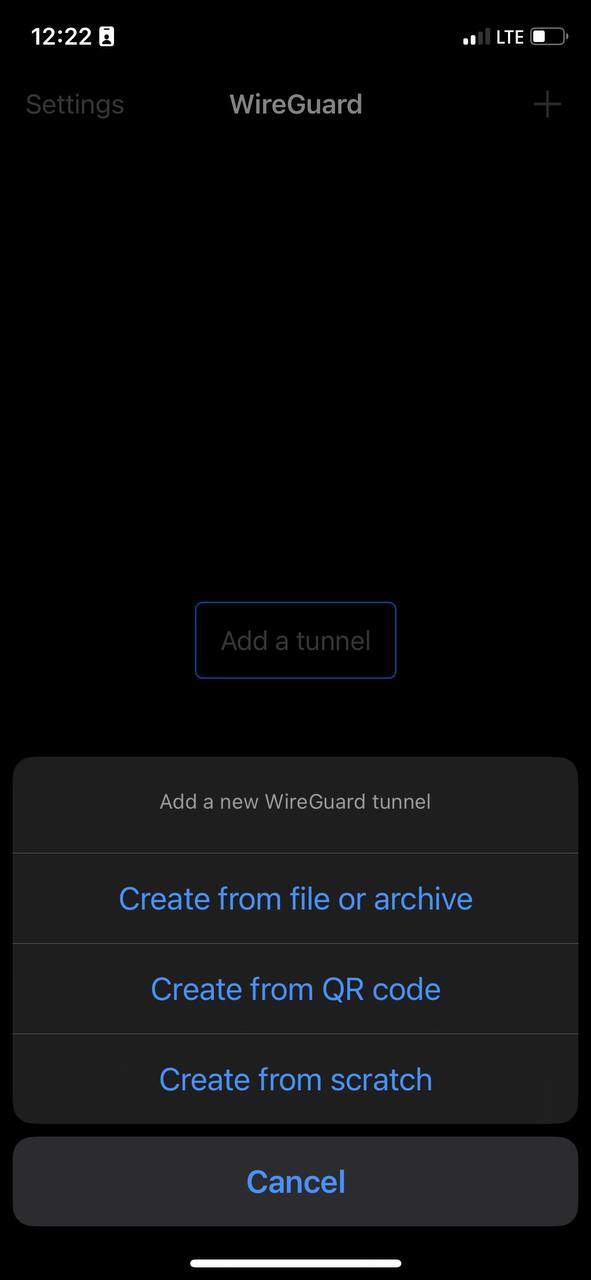
5. This is how the main window of the application looks like, which has no configured connections. To set up a new VPN connection, you must press the plus button or "Add a tunnel" button.
[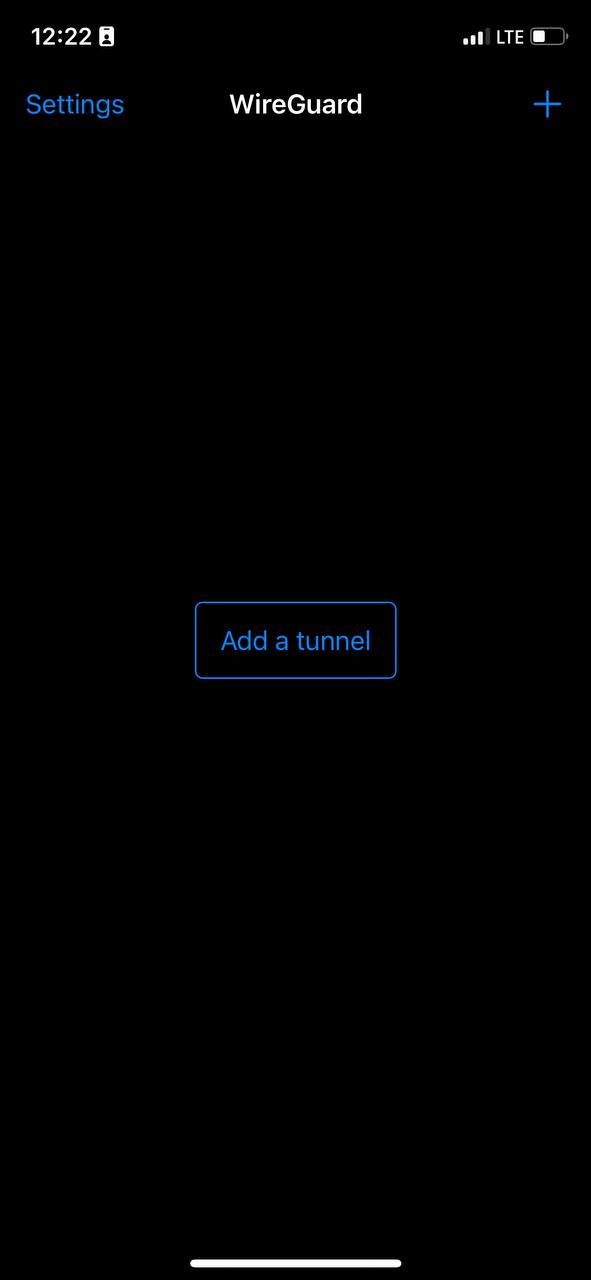](https://doc.puq.info/uploads/images/gallery/2023-07/5.jpg)
6. After you click on the button that allows you to create a new connection, you will be presented with several options. Now we will use the QR code scanning method. Click on the "SCAN FROM QR CODE" button to start scanning.
Later in this manual, **in point number 10**, we will look at creating a connection using a configuration file.
[](https://doc.puq.info/uploads/images/gallery/2023-07/6.jpg)
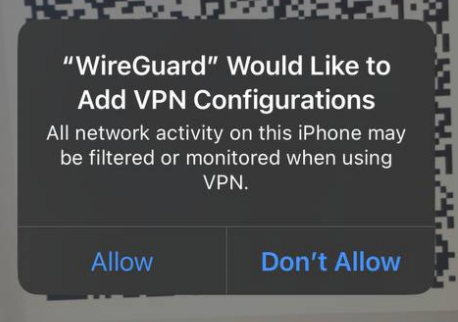
It is worth noting that if you are using the application for the first time, your device will ask you if you can allow access to the camera. You need to allow access to the camera, otherwise scanning will not be possible.
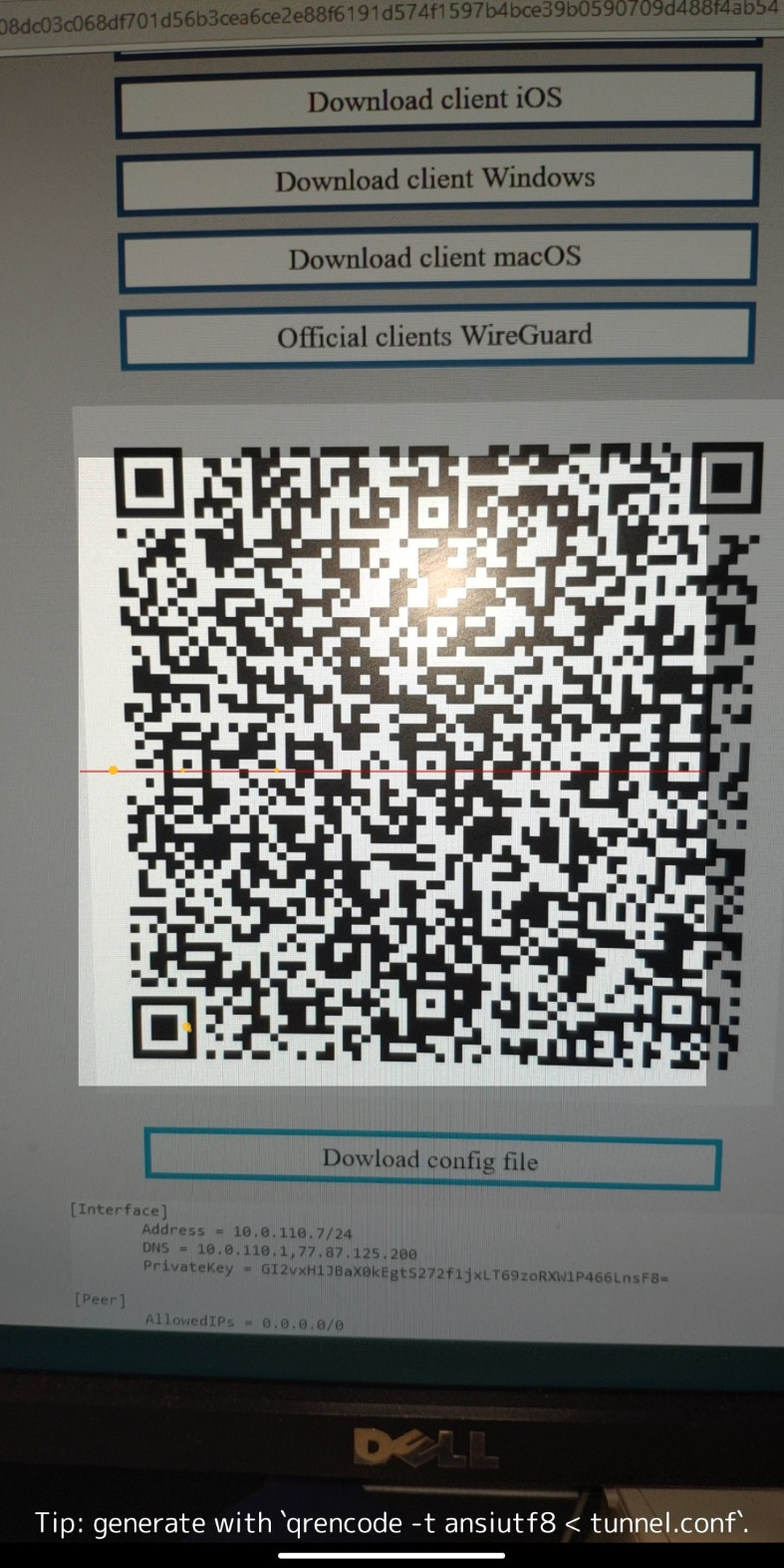
7. After you can already start scanning and see that your device is ready, point your camera at the QR code you received.
It is worth noting the system will ask your password
[](https://doc.puq.info/uploads/images/gallery/2023-07/11.jpg)
[](https://doc.puq.info/uploads/images/gallery/2023-07/6Cc8.png)
[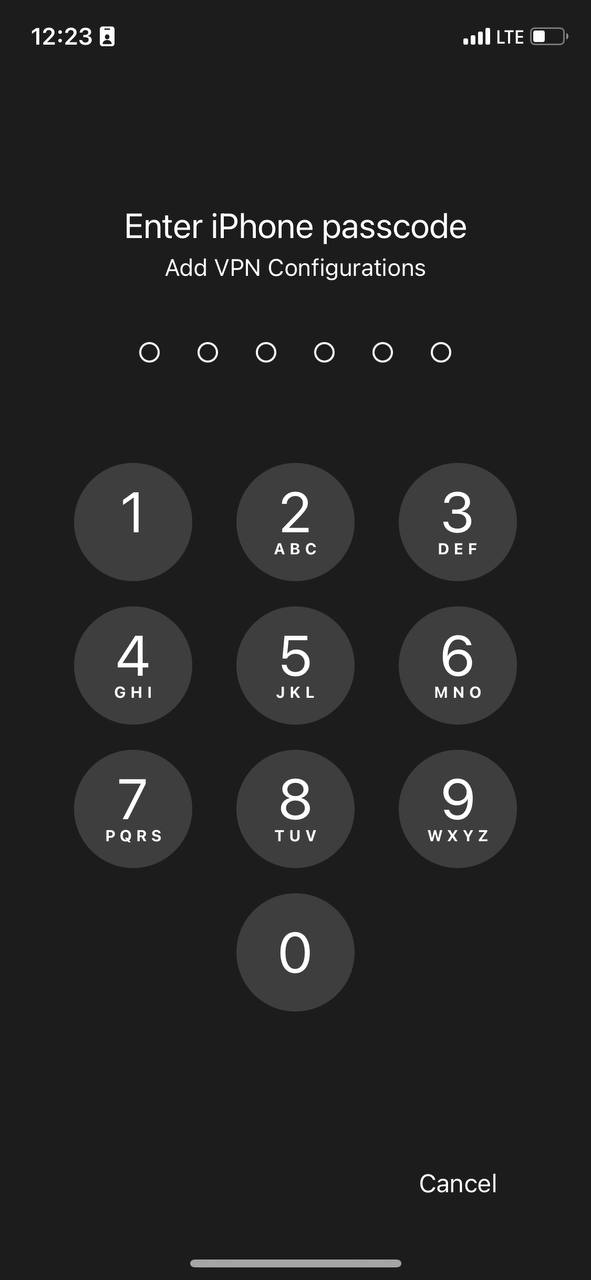](https://doc.puq.info/uploads/images/gallery/2023-07/image-1690801574494.jpg)
8. After scanning the code, when the scan was successful, the application will prompt you to enter a name for the new connection. Enter a name and save the new configuration by clicking on the "Save" button.
[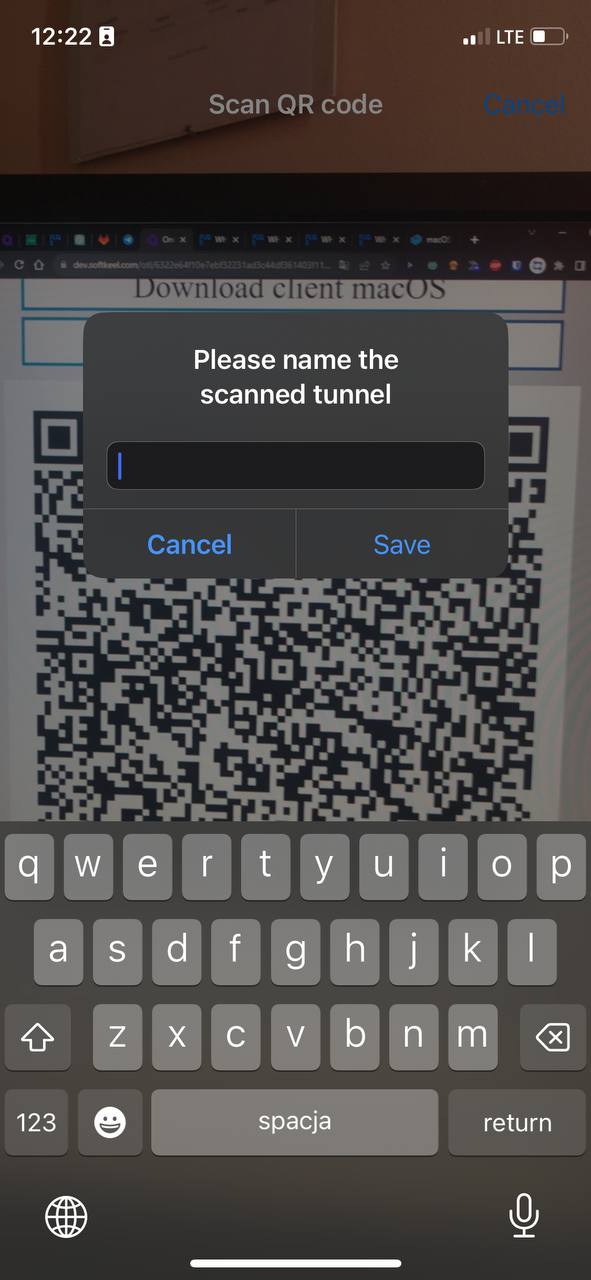](https://doc.puq.info/uploads/images/gallery/2023-07/image-1690801637924.jpg)
9. After you save your new connection, you will see a list of your VPN connections. Find the required connection to activate it and switch the slider to activation mode. [](https://doc.puq.info/uploads/images/gallery/2023-07/10.jpg)
10. **To create a connection using a configuration file:** You need to download the configuration file to your mobile device. To download this file, click on the "Dowload config file" button.
[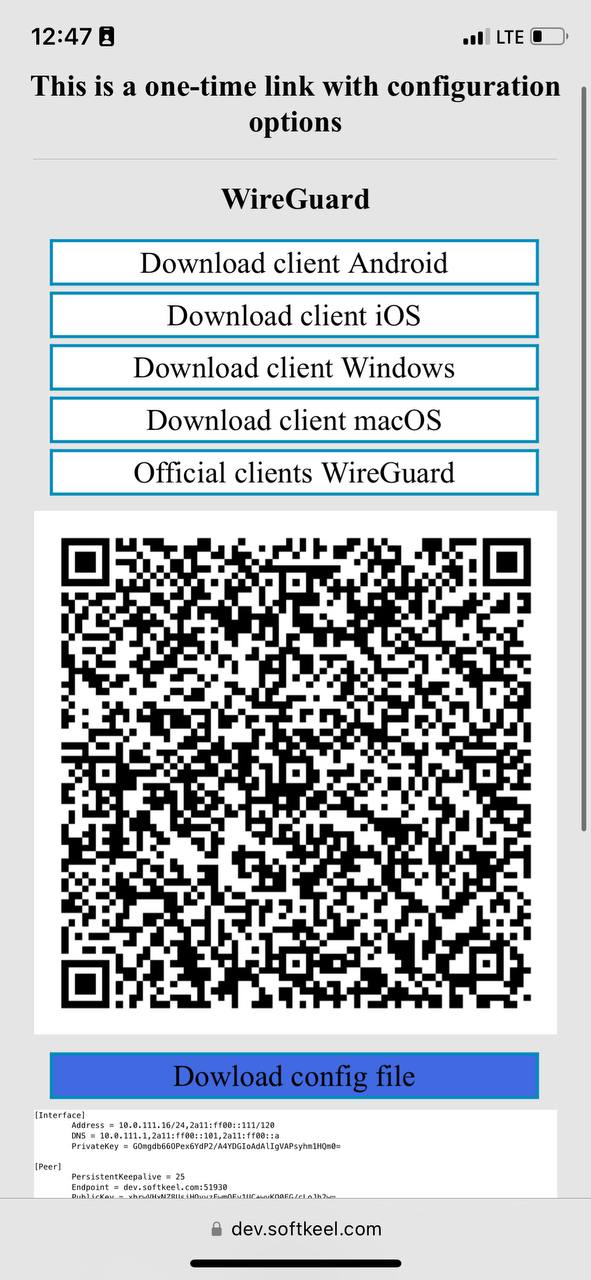](https://doc.puq.info/uploads/images/gallery/2023-07/photo-5348218480027095645-y.jpg)
11. Once your configuration file has been downloaded to your device, you need to proceed. You need to return to the "WireGuard" application to import your configuration file. Click "Create fron file or archive" to start importing the configuration file.
[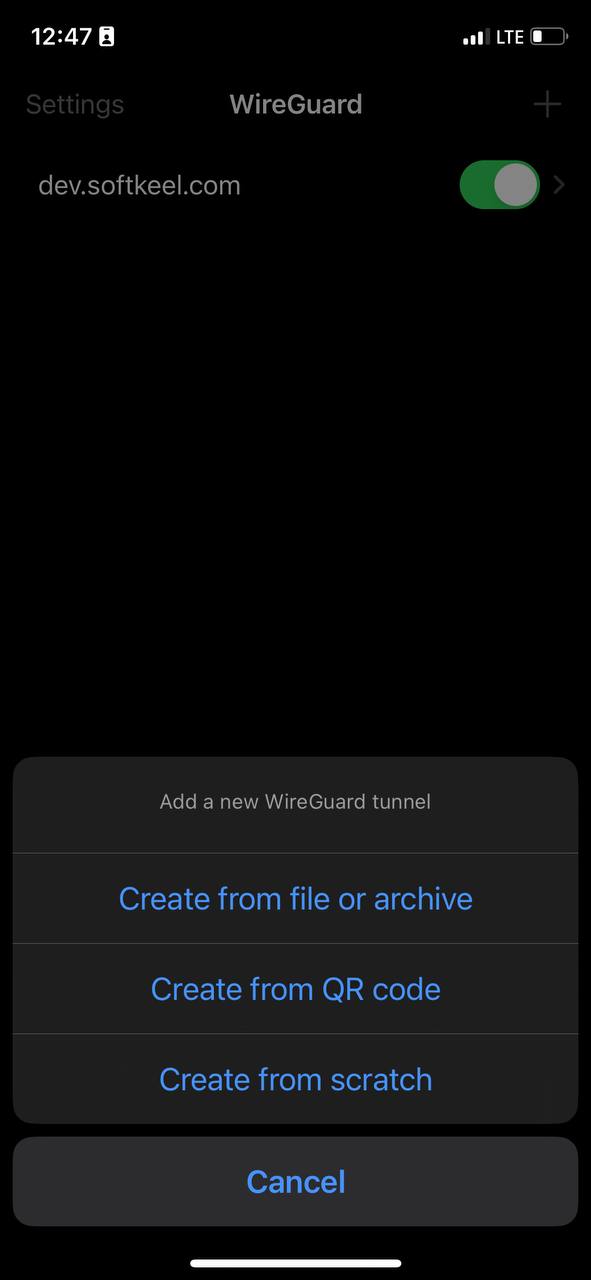](https://doc.puq.info/uploads/images/gallery/2023-07/photo-5348218480027095646-y.jpg)
12. Next, you will be prompted to find your configuration file. You need to find the configuration file and select it.
[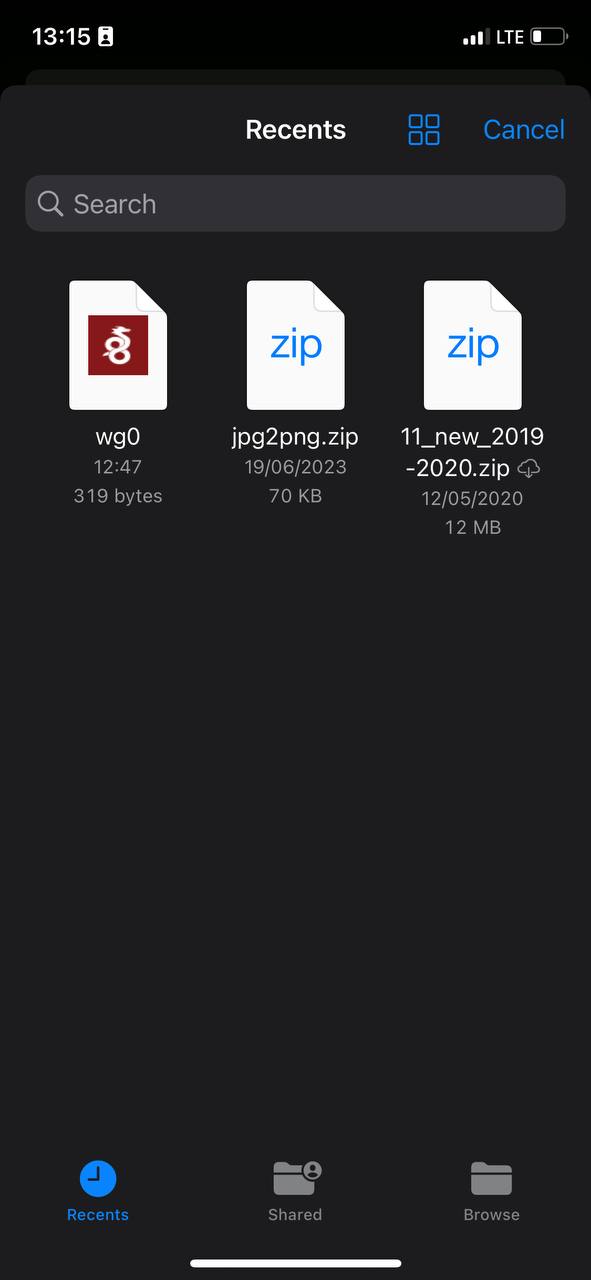](https://doc.puq.info/uploads/images/gallery/2023-07/photo-5348218480027095672-y.jpg)
13. After you select your configuration file, the connection will be created.
14. To connect to a new VPN connection, you need to activate the slider opposite to the activate position.
[](https://doc.puq.info/uploads/images/gallery/2023-07/photo-5348218480027095647-y.jpg)
# IKEv2 clients configuring
# IKEv2 Official clients
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
Our solution works great with official client programs. We strongly invite you to use them.
You can download from the [https://www.strongswan.org/download.html](https://www.strongswan.org/download.html)
Please always download latest versions. The following list is intended as a general direction only.
# [strongSwan Downloads](https://download.strongswan.org/)
## NetworkManager Plugin
strongSwan's NetworkManager plugin is available as **binary package** for several distributions (e.g. `network-manager-strongswan` on Debian/Ubuntu).
#### Current Release
Version: **1.6.0**
- [NetworkManager-strongswan-1.6.0.tar.bz2](https://download.strongswan.org/NetworkManager/NetworkManager-strongswan-1.6.0.tar.bz2)
- This version supports GTK 4 (in addition to GTK 3), but doesn't support compiling against libnm-glib anymore.
## Android App
The strongSwan Android app can be installed from App stores, or manually by downloading the APK from our download server.
#### Current Release
Version: **2.3.3**
[https://play.google.com/store/apps/details?id=org.strongswan.android](https://play.google.com/store/apps/details?id=org.strongswan.android)
[https://f-droid.org/en/packages/org.strongswan.android/](https://f-droid.org/en/packages/org.strongswan.android/)
# Android IKEv2 client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to connect to a VPN, follow these steps:
1. Open the link you received in a browser to get instructions and configuration for your new VPN connection. And you will see the following page in the browser window
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928539397.png)
2. To continue, you need to install a connection client for your Android device. To download and install your IKEv2 connection client, go to the IKEv2 section and click on the "Download client Android" button.
[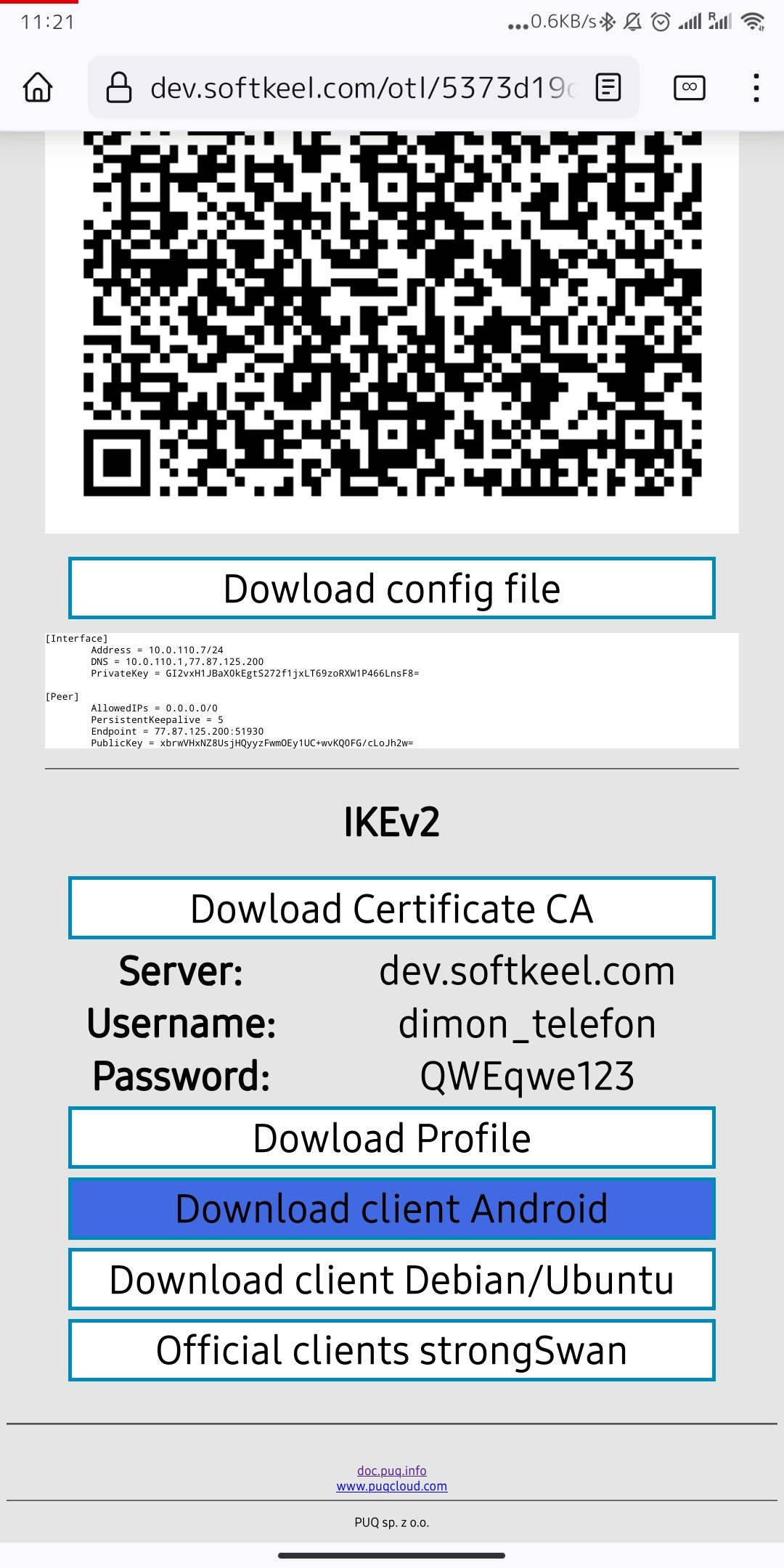](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671014636238-mozilla-firefox.jpg)
3. Install the app from your app store. [](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671020017652-android-vending.jpg)
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671014756387-android-vending.jpg)
4. After the app is installed. Download your connection profile in the IKEv2 section. To download the connection profile, click "Dowload Profile"
[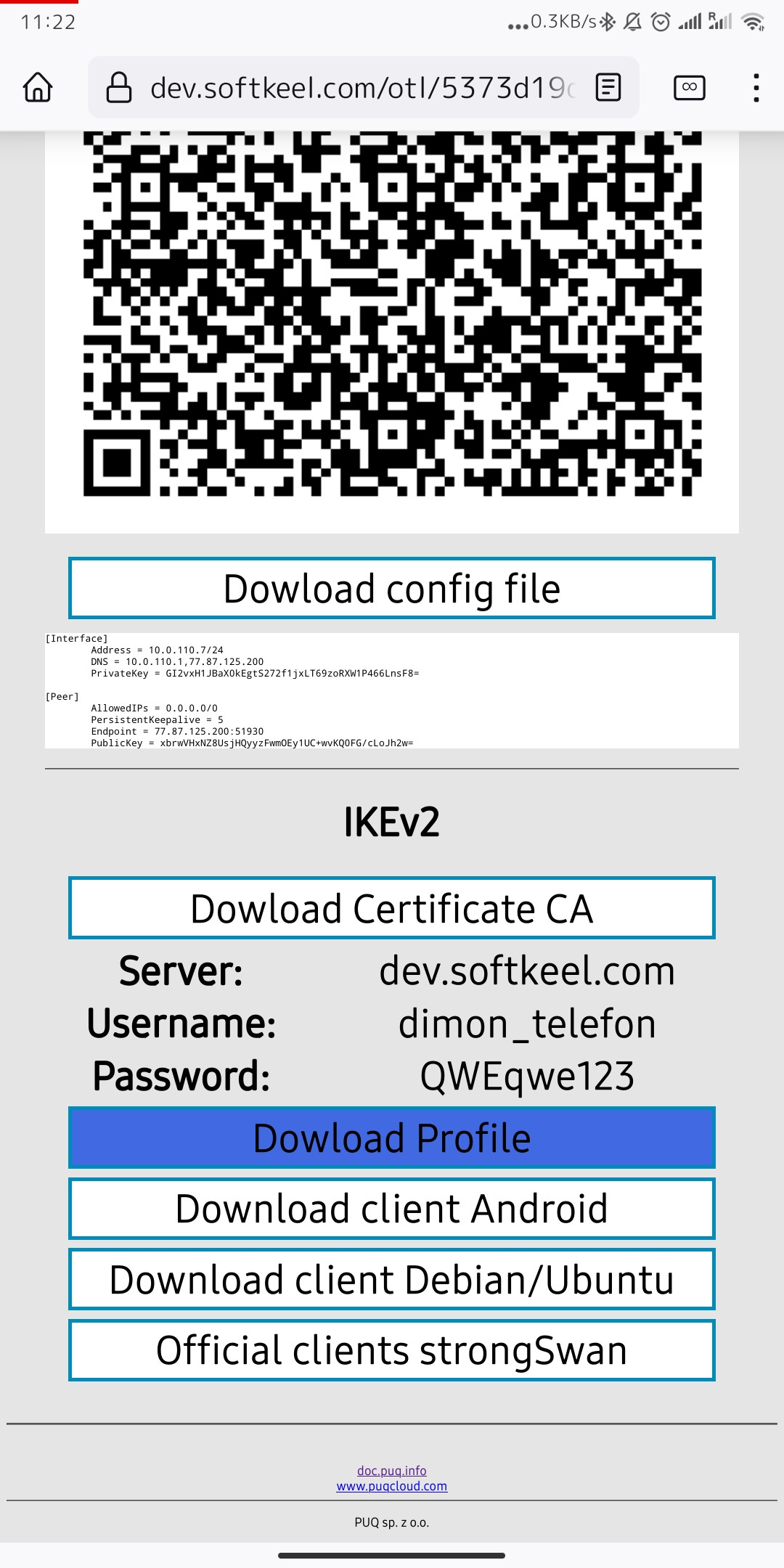](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671018841192-mozilla-firefox.jpg)
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671018952589-mozilla-firefox.jpg)
5. After you have downloaded the connection profile, you need to import this profile into your application. Open the app and click "Import VPN Profile" on the menu.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671019112680-strongswan-android.jpg)
6. You need to enter your password, which will be available to you in the information provided to you. We cannot pass the password as it is not secure in terms of the IKEv2 protocol.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671019246935-strongswan-android.jpg)
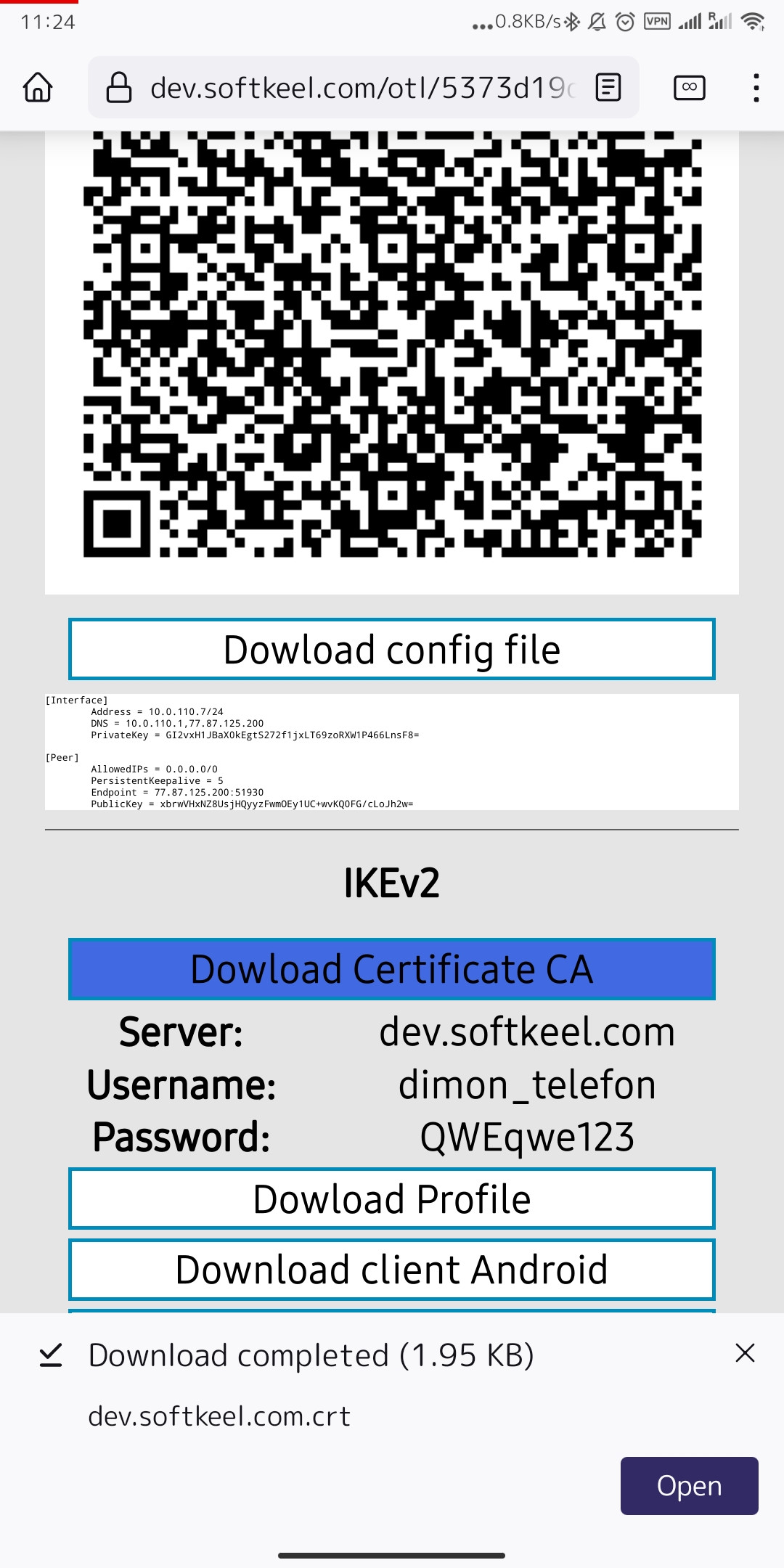
7. Almost done. But that's not all. We need to import keys for our connection. This is necessary to ensure that the connection is encrypted. To download the key, you need to click on the "Dowload Certificate CA" button. And save the certificate for further integration. To start importing a certificate, simply open it and select an application to open the file.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671019859852-mozilla-firefox.jpg)
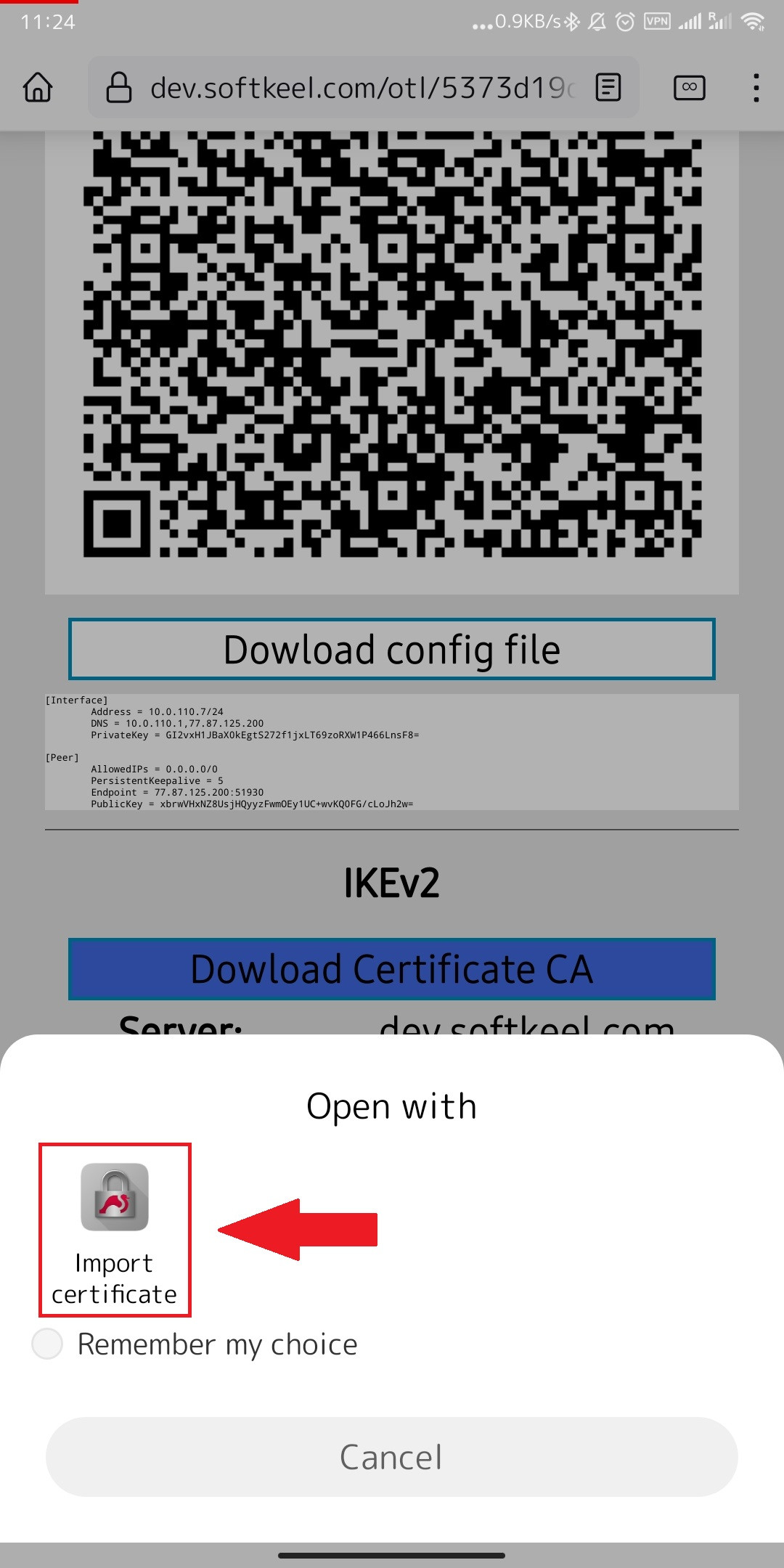
8. Next click open.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671019944656-mozilla-firefox.jpg)
9. After you click open, select an application from those offered. And click on the "Import Certificate" button.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671020143782.jpg)
[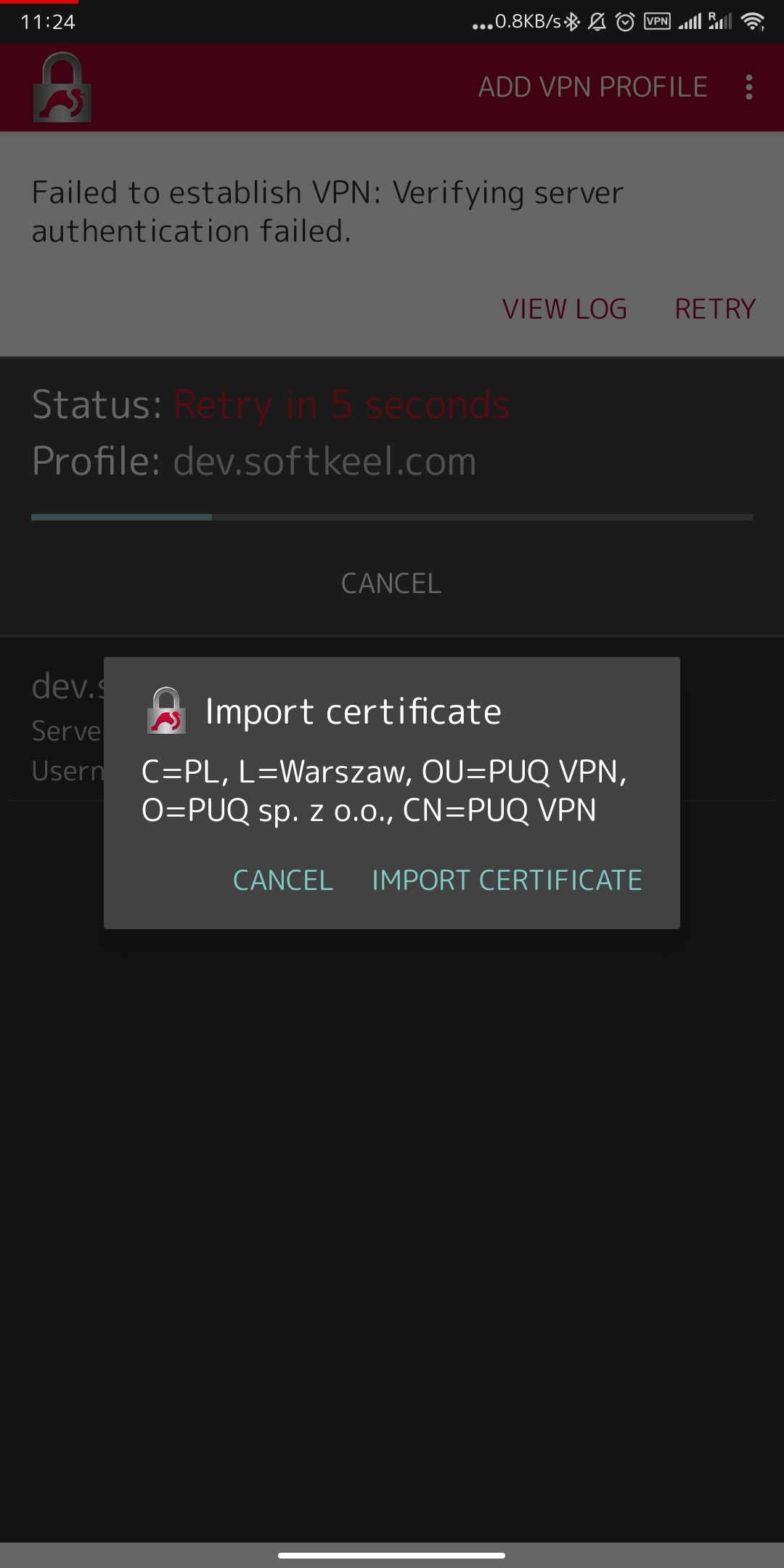](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671020212035-strongswan-android.jpg)
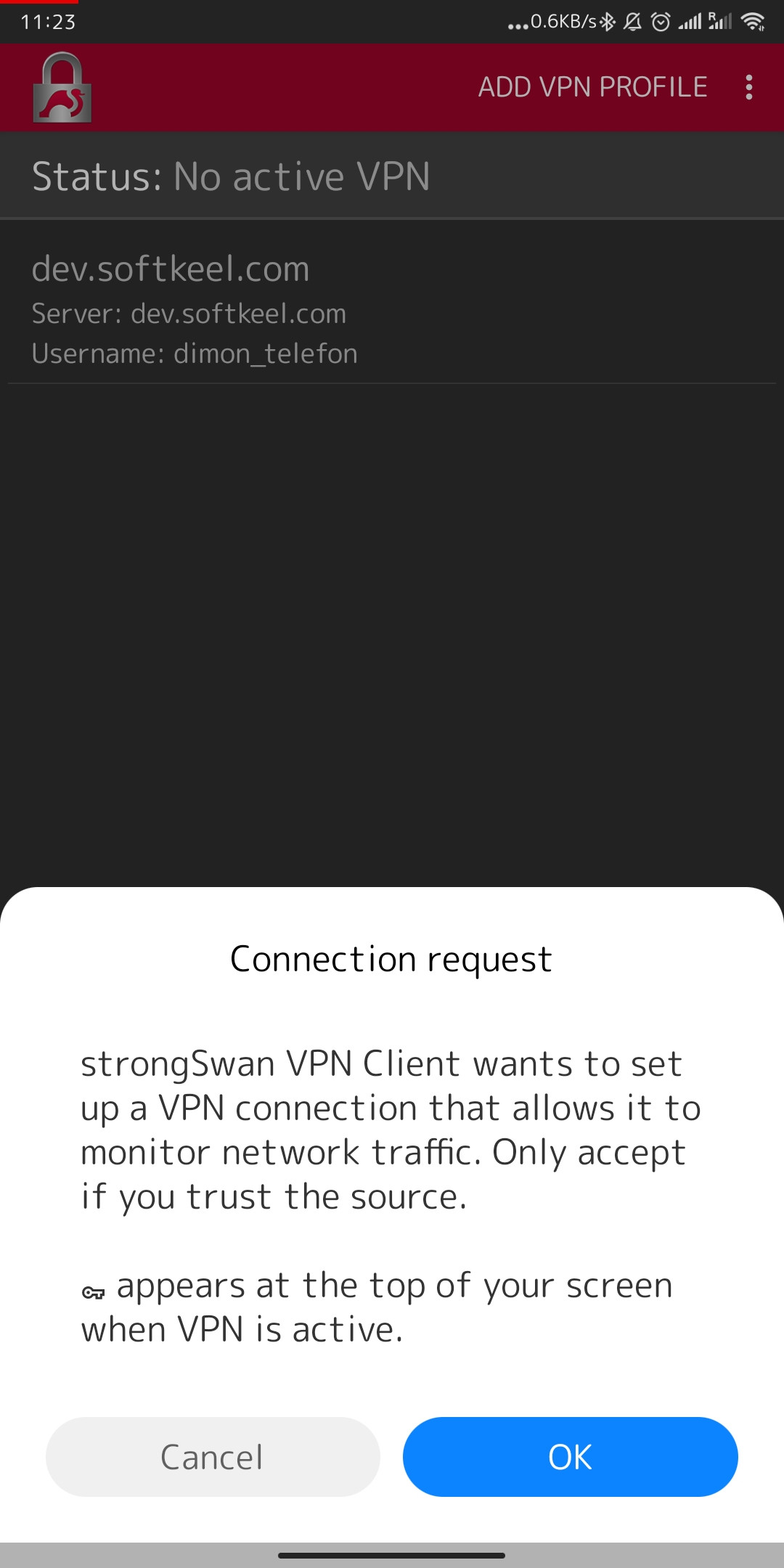
10. After importing the certificate, you can share it with a secure VPN network. Agree to the system warnings if you want to activate the connection.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671020424018-android-vpndialogs.jpg)
[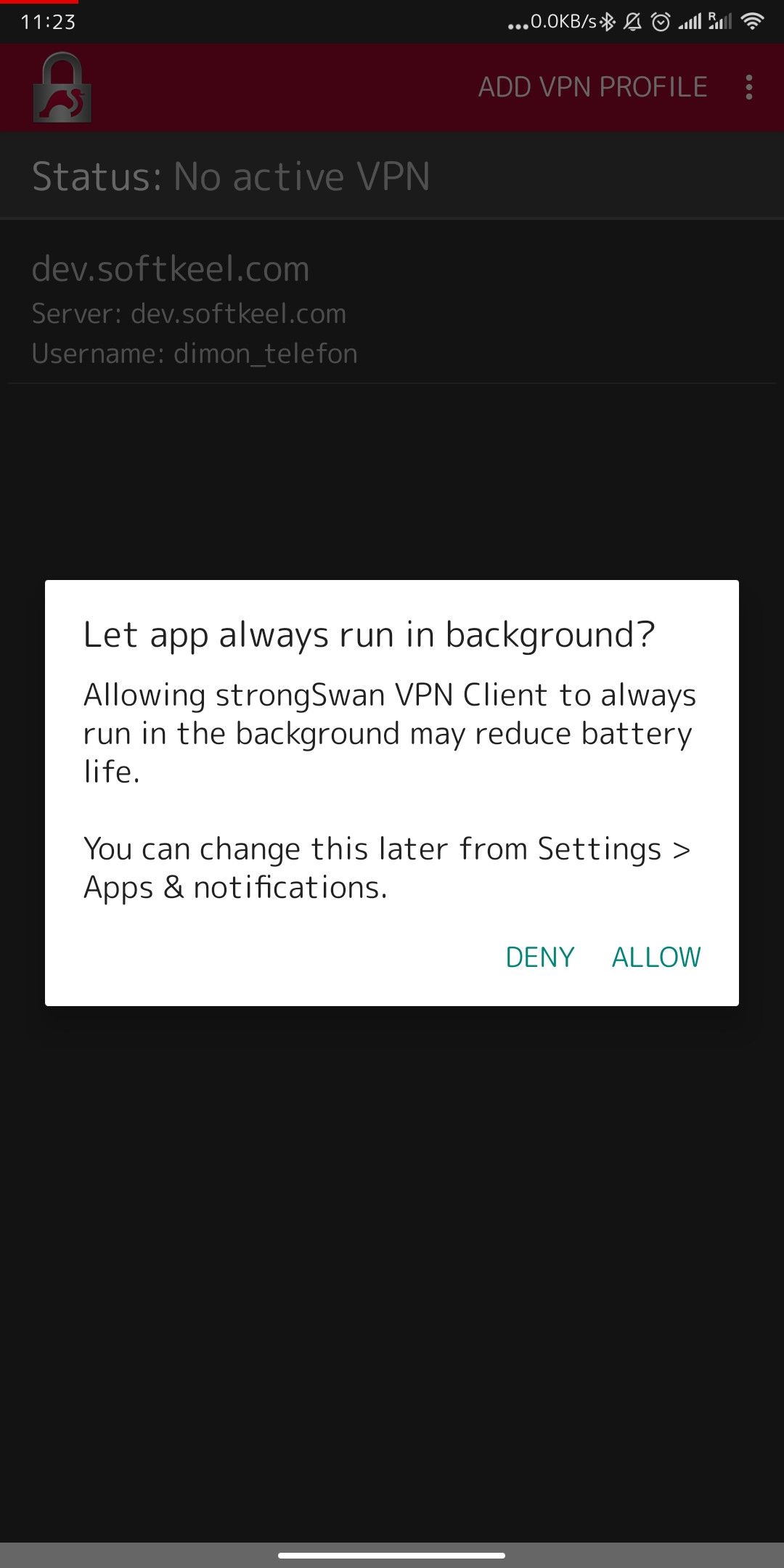](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671020445898-android-settings.jpg)
11. Congratulations, your connection is set up!
[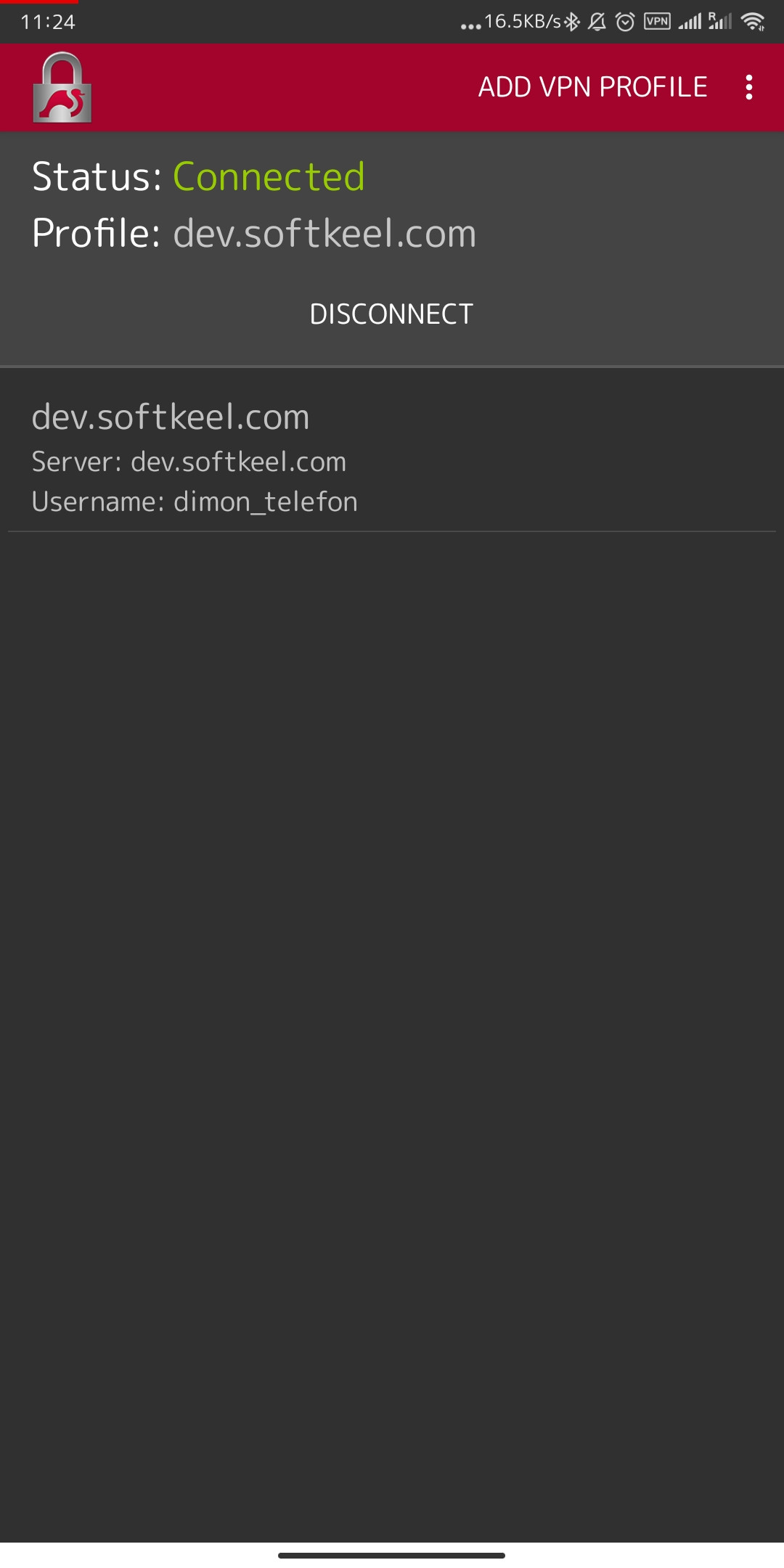](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671020540840-strongswan-android.jpg)
# macOS IKEv2 client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to connect to a VPN, follow these steps:
1. Open the link you received in a browser to get instructions and configuration for your new VPN connection. And you will see the following page in the browser window
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928539397.png)
2. In order to start the configuration you need to download the Certificate CA file. To download the Certificate CA file, click the "Dowload Certificate CA" button.
[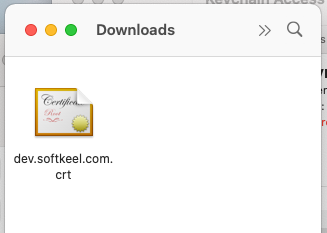](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671025030636-15-49.png)
3. Later, when you download the certificate, go to the folder where you downloaded the certificate. Next, double-click on the certificate file, or open the context menu of the file and click open.
[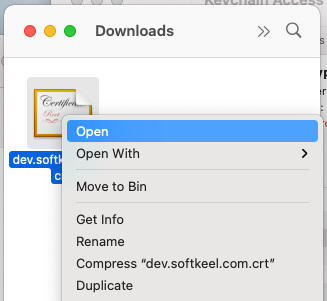](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671025042839-16-08.png)
4. After you open this certificate file, you will be taken to "Keychain Access". Find the certificate you just integrated there. This will be a root certificate, and the certificate will not be trusted.
[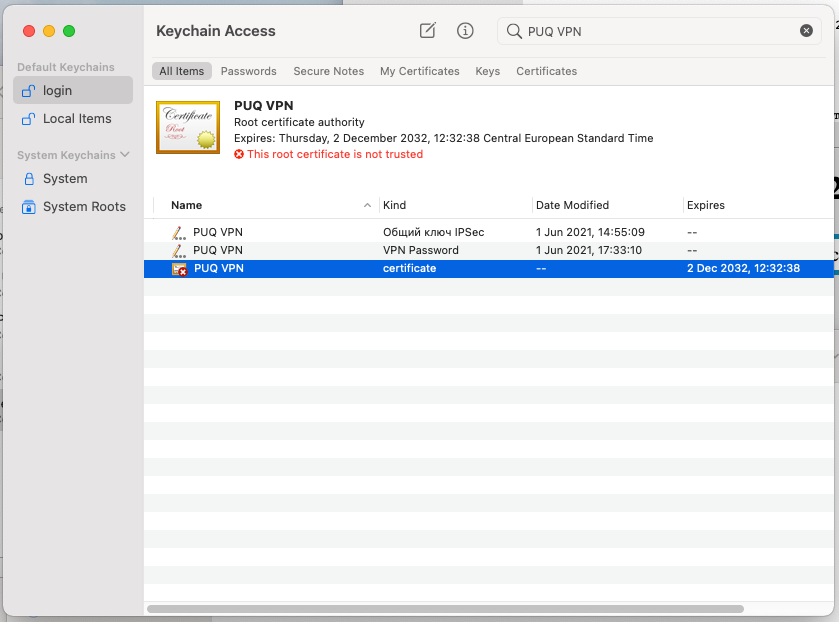](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671025229939-15-26.png)
5. Next, double-click on it and make the certificate trusted.
[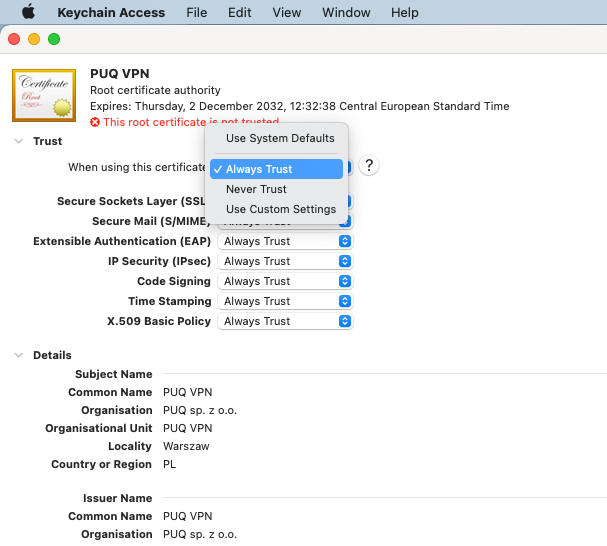](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671025295739-07-16.png)
6. After you close the previous window, you will be prompted to enter your system password in order to store the settings. Note that the certificate is now trusted.
[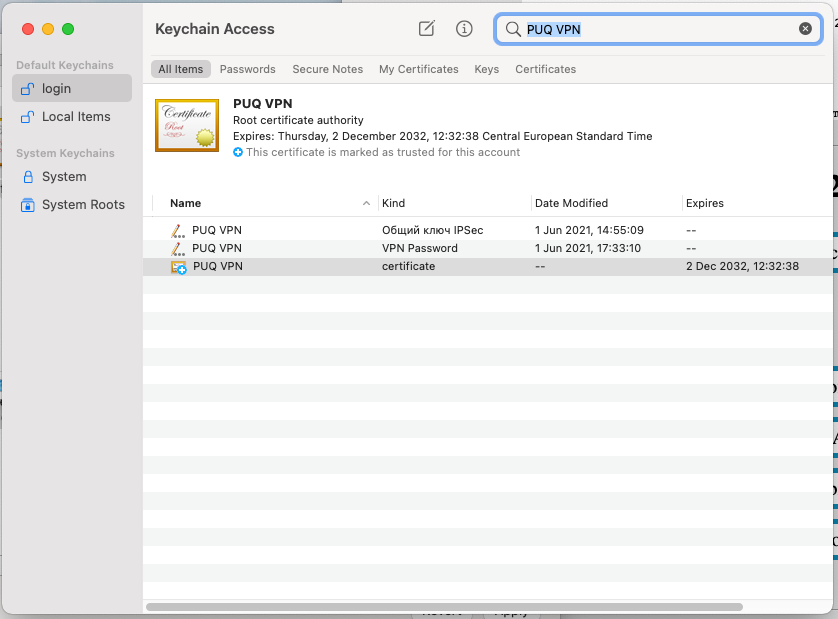](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671025411216-16-40.png)
7. After installing the certificate, we can proceed to the connection configuration. Open connection settings. Click on the plus button to add a new connection.
[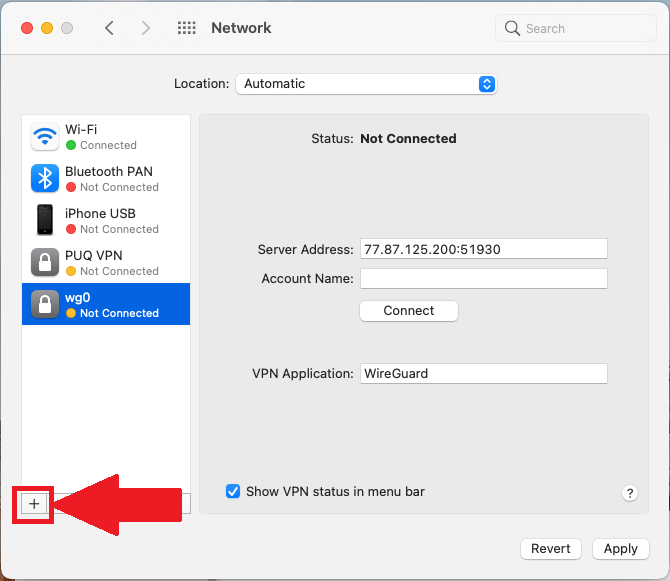](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671025828943-10-09.png)
8. Create a new IKEv2 connection.
[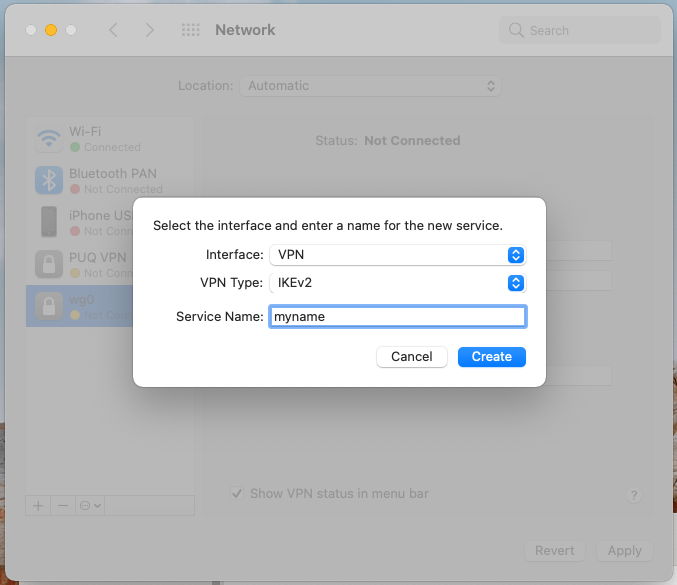](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671025909106-10-41.png)
9. Enter the data as required. Server address and remote ID.
[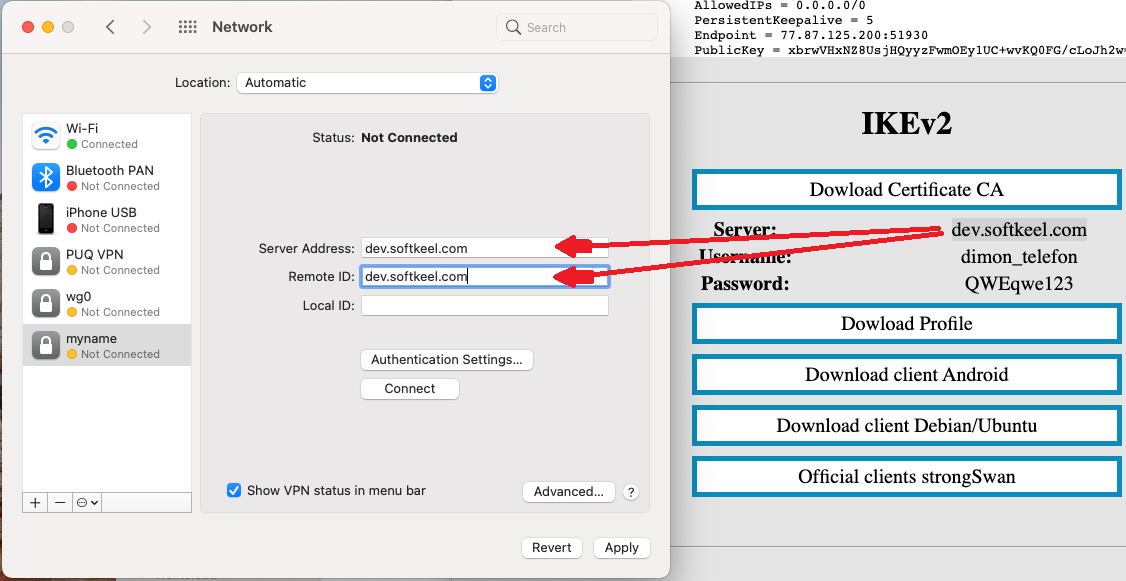](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671026134939-12-23.png)
10. Next, click on the Authentication Settings button to enter the Authentication details.
[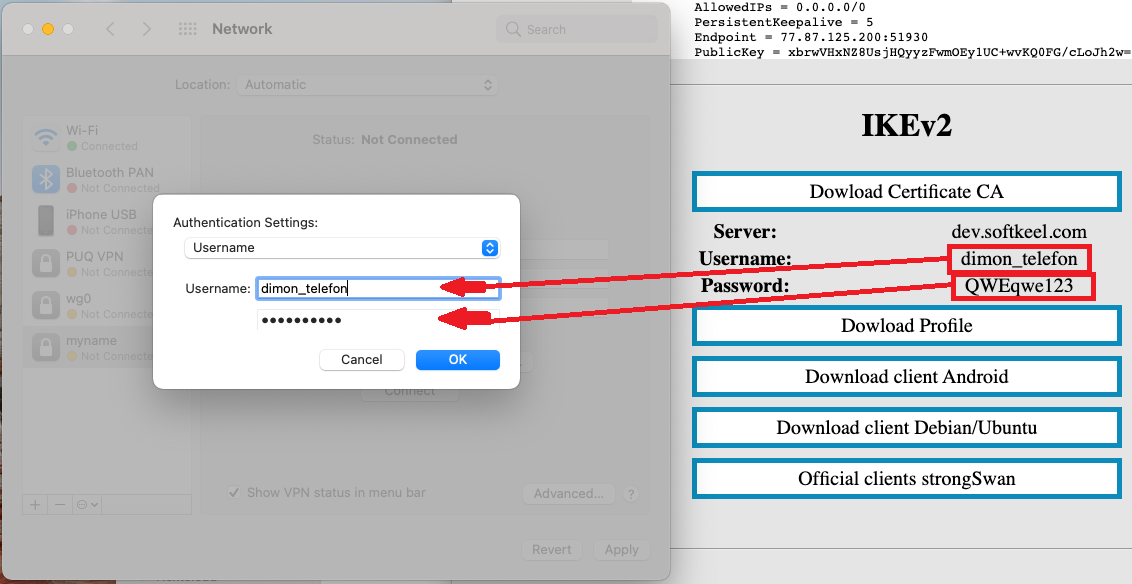](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671026339624-13-33.png)
11. Save your connection and connect to a new VPN connection. Congratulations, your connection is set up!
[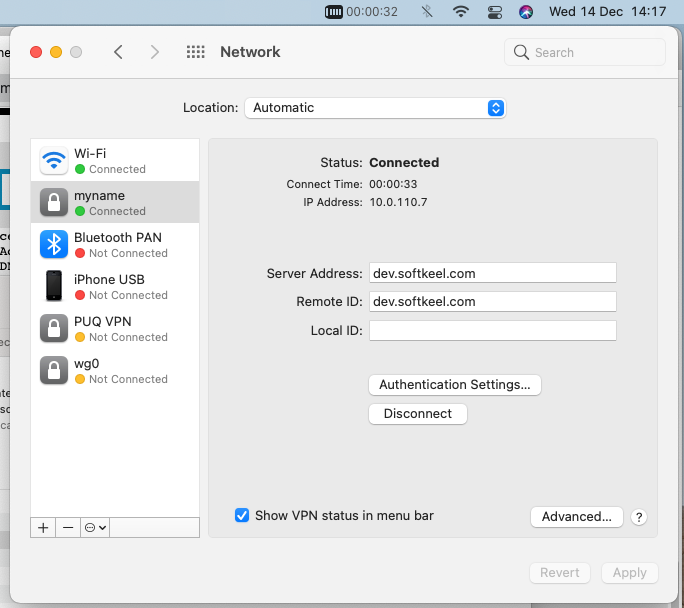](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671026616649-17-45.png)
# Windows IKEv2 client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to connect to a VPN, follow these steps:
1. Open the link you received in a browser to get instructions and configuration for your new VPN connection. And you will see the following page in the browser window
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928539397.png)
2. In order to configure the VPN connection on Windows. You need to install a certificate. First, download the certificate from the IKEv2 section and save it on your device, for example, in the Downloads folder.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671029595087.png)
3. Go to the download folder, then double-click or in the context menu of the downloaded certificate file, click Open
[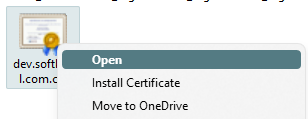](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671029771637.png)
4. You will see a warning window, click open.
[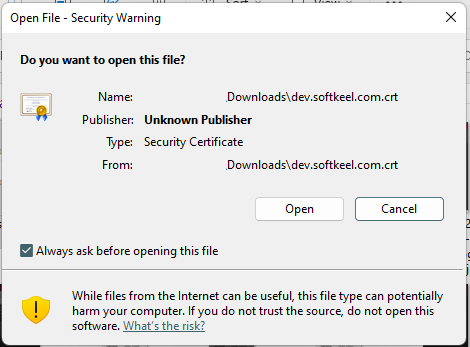](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671029891599.png)
5. After that, a window will open in which information about the certificate will be described. Click the "Install Certificate" button.
[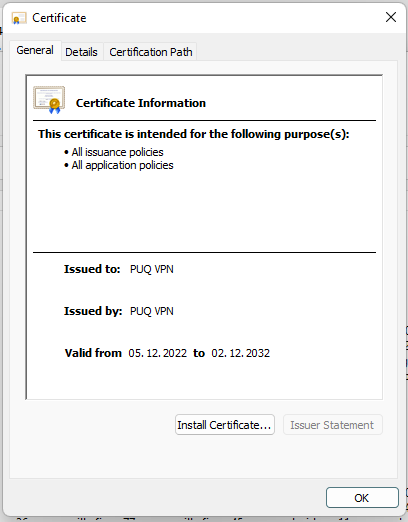](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671029979876.png)
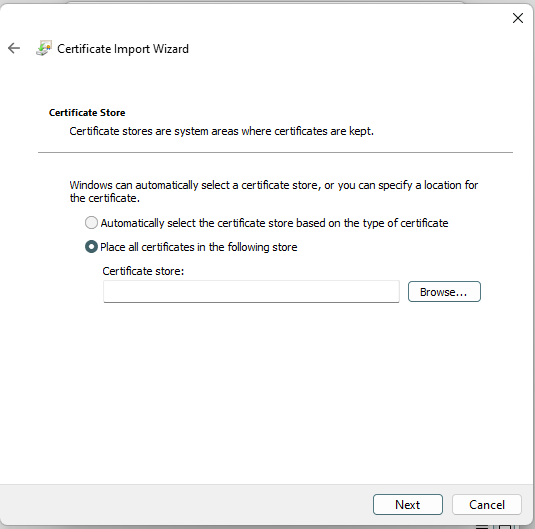
6. The Certificate Installation Wizard opens. Follow hints and logic. For example, select "For Local Machine" to have the certificate trusted by all users on your system. Next.
[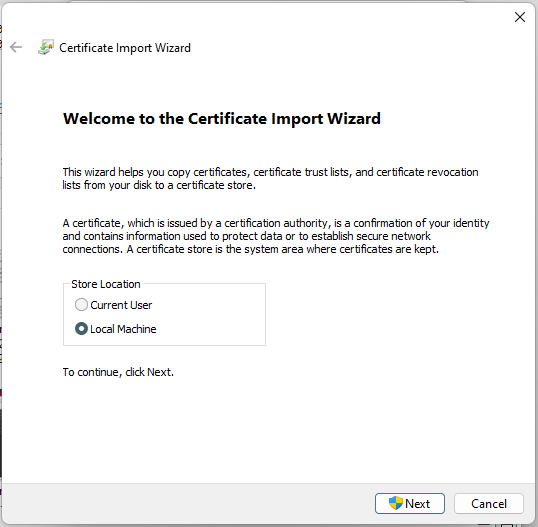](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671030116341.png)
7. Select a location to save the certificate. This is the root certificate, so we will save it to the root certificates.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671030210780.png)
[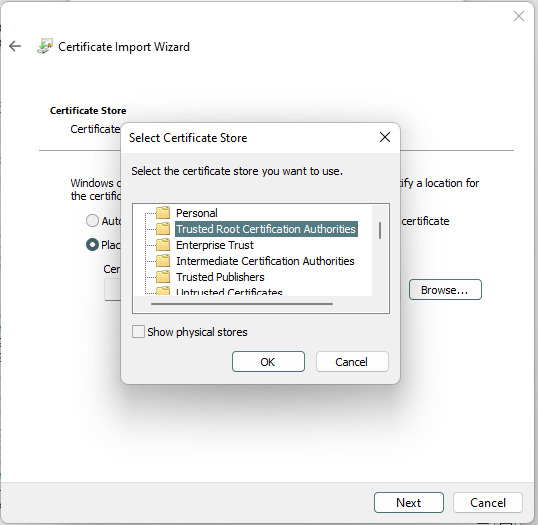](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671030221428.png)
[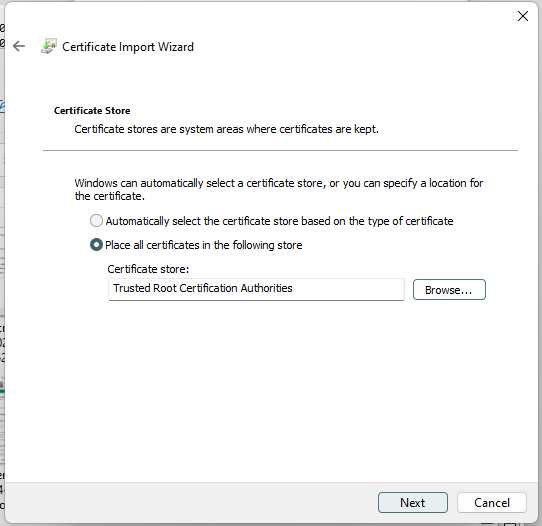](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671030231214.png)
8. Check and save settings.
[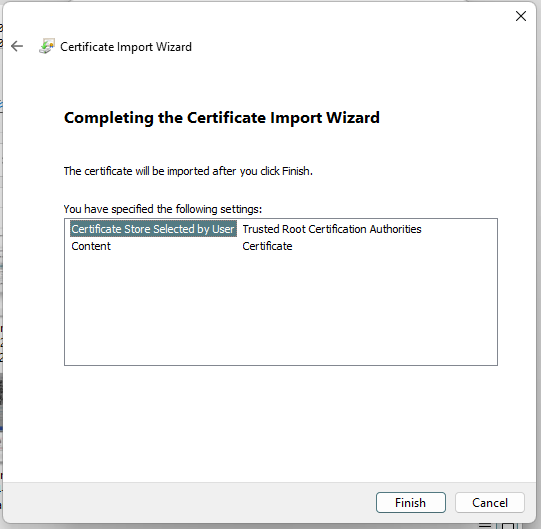](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671030300460.png)
9. The system will see us that the certificate was imported successfully.
[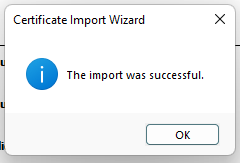](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671030340310.png)
10. Let's move on to connection settings. We go to the network connection settings in the system parameters and create a new VPN connection.
[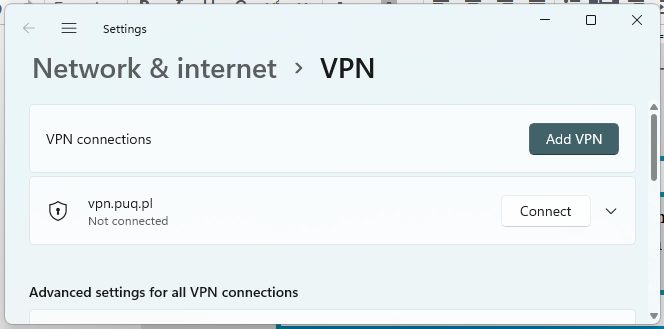](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671030399968.png)
11. Be sure to select IKEv2 and enter the correct data.
[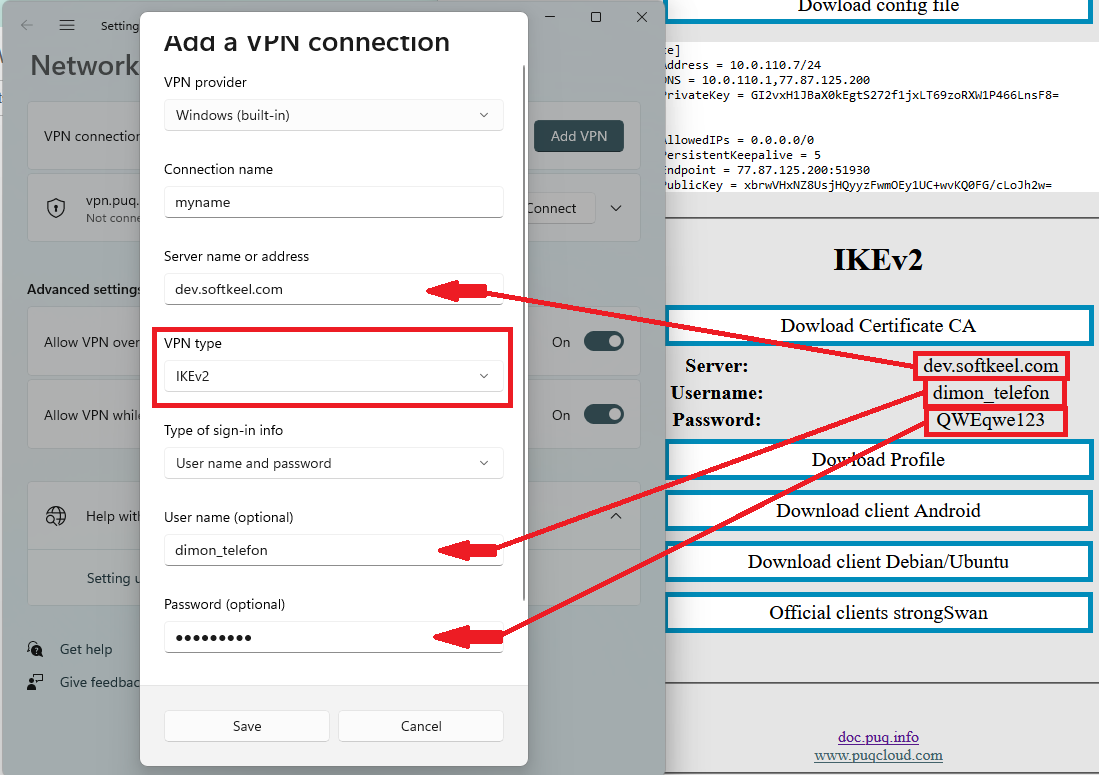](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671030604387.png)
12. Congratulations! Your connection has been successfully set up!
[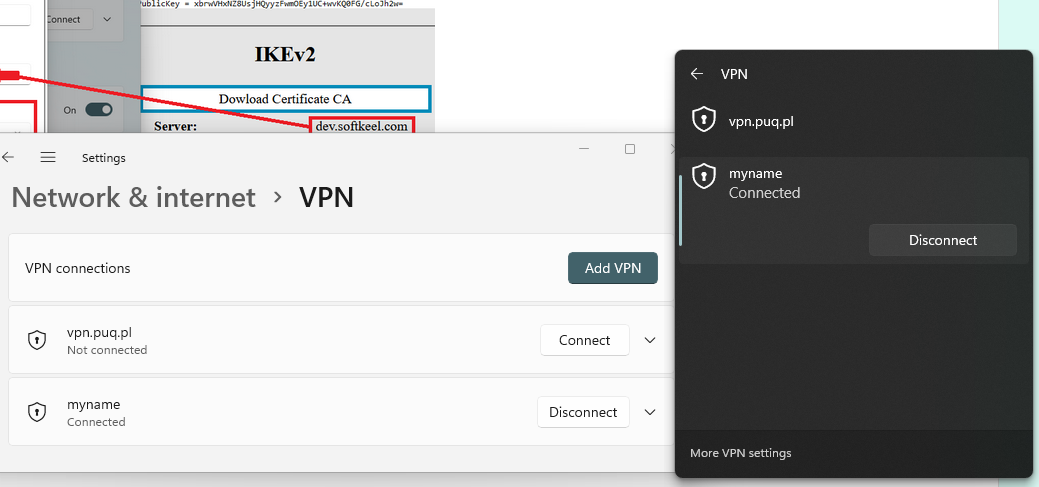](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671030744850.png)
# Linux IKEv2 client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to connect to a VPN, follow these steps:
1. Open the link you received in a browser to get instructions and configuration for your new VPN connection. And you will see the following page in the browser window
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1670928539397.png)
2. In order to start the configuration you need install some software, before installing the software, do not forget to update the package list using the command `sudo apt update`. After the package list is updated, install additional software:
`sudo apt install strongswan libcharon-extra-plugins`
3. Next, prepare a certificate to encrypt the connection. You can download the certificate, open the certificate file as text and create a new file at `nano /etc/ipsec.d/cacerts/ca-cert.pem`
4. To prevent automatic connection, use systemctl to disable StrongSwan from starting automatically
`sudo systemctl disable --now strongswan-starter`
5. Next, you need to edit or create a file with authentication data
`sudo nano /etc/ipsec.secrets`
In this file, you need to enter your login and password data from the IKEv2 section
```
your_username : EAP "your_password"
```
6. The next step is to edit the configuration file
`nano /etc/ipsec.conf`
The contents of the configuration file should be the following
```
config setup
conn ikev2-rw
right=adres_server
# This should match the `leftid` value on your server's configuration
rightid=adres_server
rightsubnet=0.0.0.0/0
rightauth=pubkey
leftsourceip=%cfg
leftauth=eap-mschapv2
leftid=your_username
eap_identity=%identity
auto=start
```
**Attention!** Please note that you need to enter your data in the configuration file and the authentication file.
7. To activate the connection, enter the command `sudo ipsec start` and to disable run the command `sudo ipsec stop`
# Mikrotik IKEv2 client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## Configuring Mikrotik as an IKEv2 Client.
##### Make sure you have an up to date routerOS system.
Version must be at least: 6.49.7
```shell
[admin@VPN-CLIENT] > system package print
Flags: X - disabled
# NAME VERSION SCHEDULED
0 ntp 6.49.7
1 ppp 6.49.7
2 dhcp 6.49.7
3 mpls 6.49.7
4 security 6.49.7
5 advanced-tools 6.49.7
6 system 6.49.7
7 openflow 6.49.7
8 multicast 6.49.7
9 routing 6.49.7
```
##### Open a one-time link to obtain authorization data and a root certificate.
[](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671037736670.png)
Download the certificate and place it on the Mikrotik router using the Winbox program
[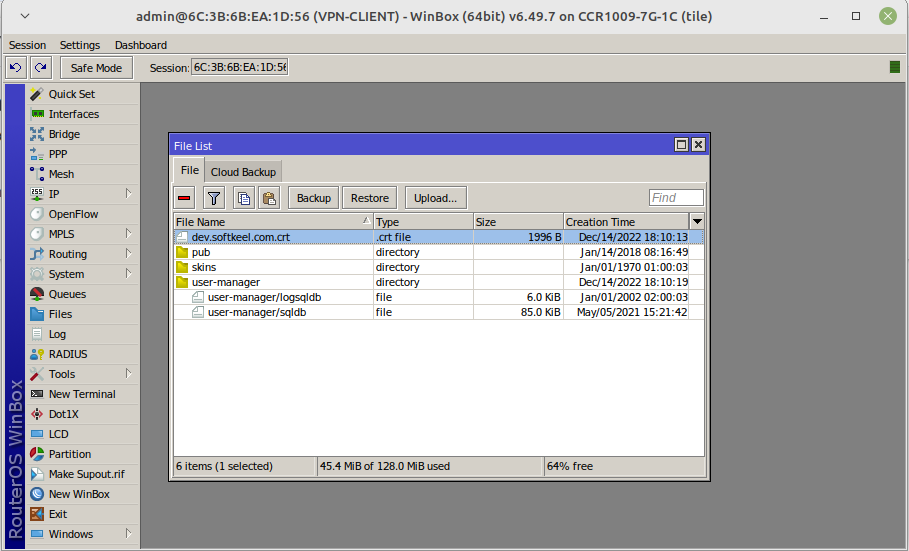](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671037851417.png)
Import the certificate into the system
[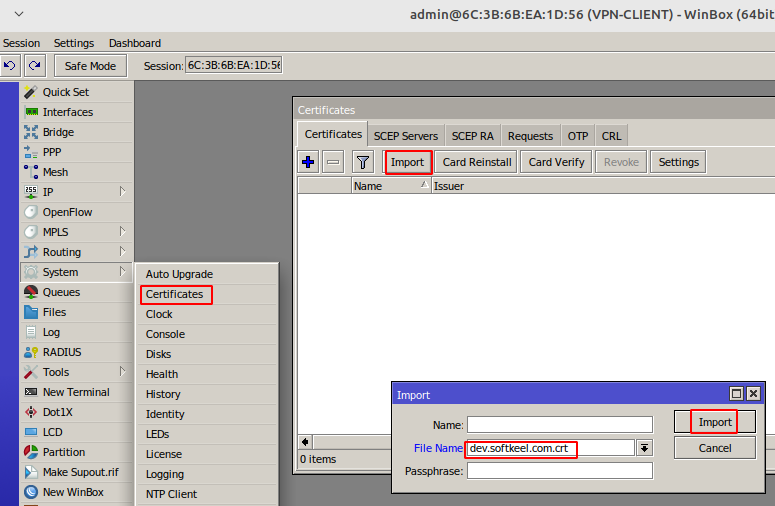](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671038008488.png)
[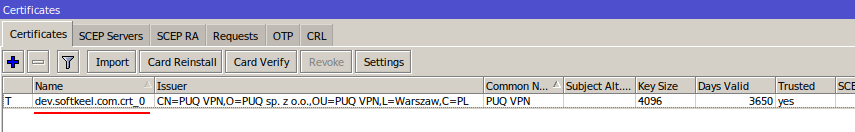](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671038098059.png)
To create an IKEv2 connection, we will use the console
Open a terminal and enter the following commands
Replace the authorization data with the data that is in the one-time link
the example contains the following data. You need to replace them with your own.
| **Server:** | **dev.softkeel.com** | address=**dev.softkeel.com** |
| **Username:** | **mikrotik** | my-id=user-fqdn:**mikrotik** AND username=**mikrotik** |
| **Password:** | **NX9%B3&3YG** | password=**NX9%B3&3YG** |
| **certificate** | **dev.softkeel.com.crt\_0** | certificate=**dev.softkeel.com.crt\_0** |
- - - - - -
It is a strong recommendation to use only the terminal command line in setup.
We encountered cases when, during the configuration of Mikrotik through *winbox*, some parameters were not correctly entered into the configuration. Commands entered through the terminal are always correctly processed.
```
/ip ipsec settings
set accounting=no
/ip ipsec mode-config
add name=MY_VPN responder=no
/ip ipsec policy group
add name=MY_VPN
/ip ipsec profile
add dh-group=modp1024 enc-algorithm=aes-256 name=MY_VPN
/ip ipsec peer
add address=dev.softkeel.com exchange-mode=ike2 name=MY_VPN profile=MY_VPN
/ip ipsec proposal
add name=MY_VPN pfs-group=none
/ip ipsec policy
add dst-address=0.0.0.0/0 group=MY_VPN proposal=MY_VPN src-address=0.0.0.0/0 template=yes
/ip ipsec identity
add auth-method=eap \
eap-methods=eap-mschapv2 generate-policy=port-strict \
mode-config=MY_VPN \
peer=MY_VPN policy-template-group=MY_VPN \
certificate=dev.softkeel.com.crt_0 \
my-id=user-fqdn:mikrotik \
username=mikrotik \
password=NX9%B3&3YG
```
##### After the work done, you can see the connection status in the IP->IPsec configuration
[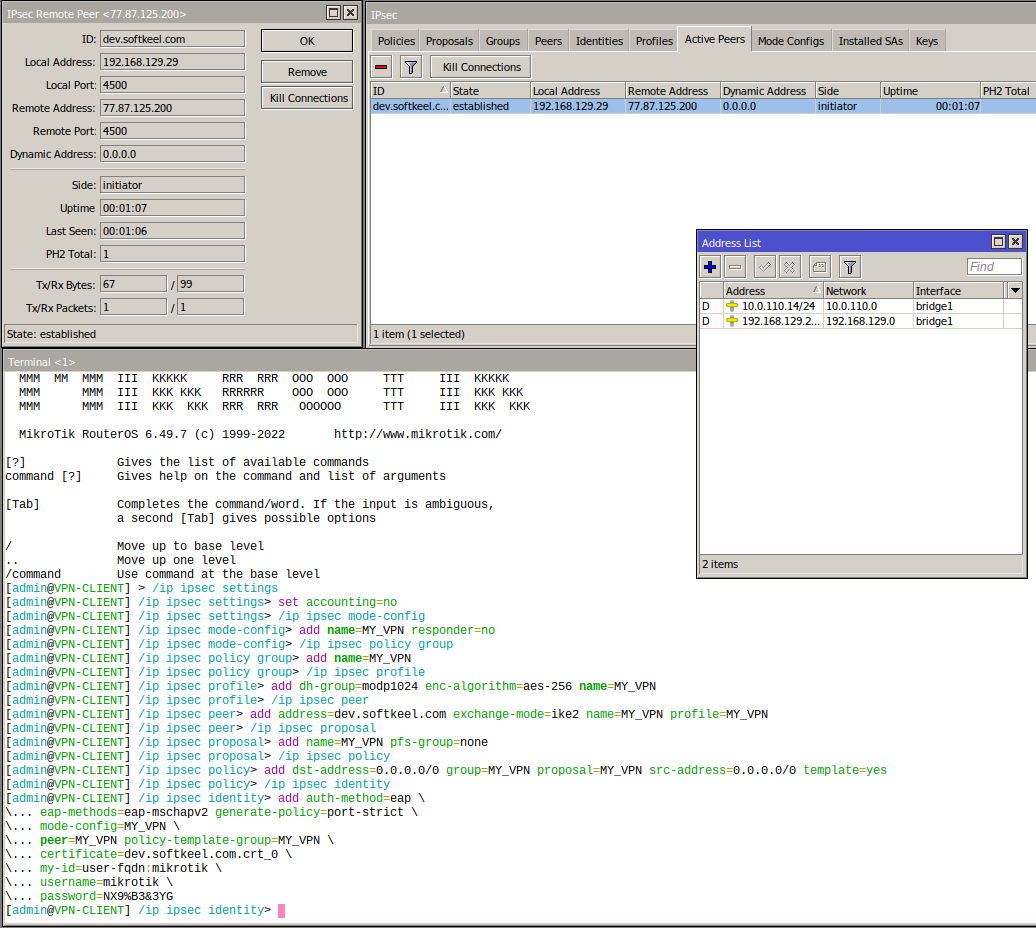](https://doc.puq.info/uploads/images/gallery/2022-12/image-1671039196036.png)
You also need to configure the traffic routes you need at your discretion.
# iOS IKEv2 client configuration
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
To connect to the VPN, follow these steps:
1. Open the provided link in your browser to get instructions and settings for your new VPN connection. You will see the following page in your browser window.
[](https://doc.puq.info/uploads/images/gallery/2023-07/1.png)
2. To proceed, you need to install the Certificate CA. Click the "Download Certificate CA" button and allow the download of the file.
[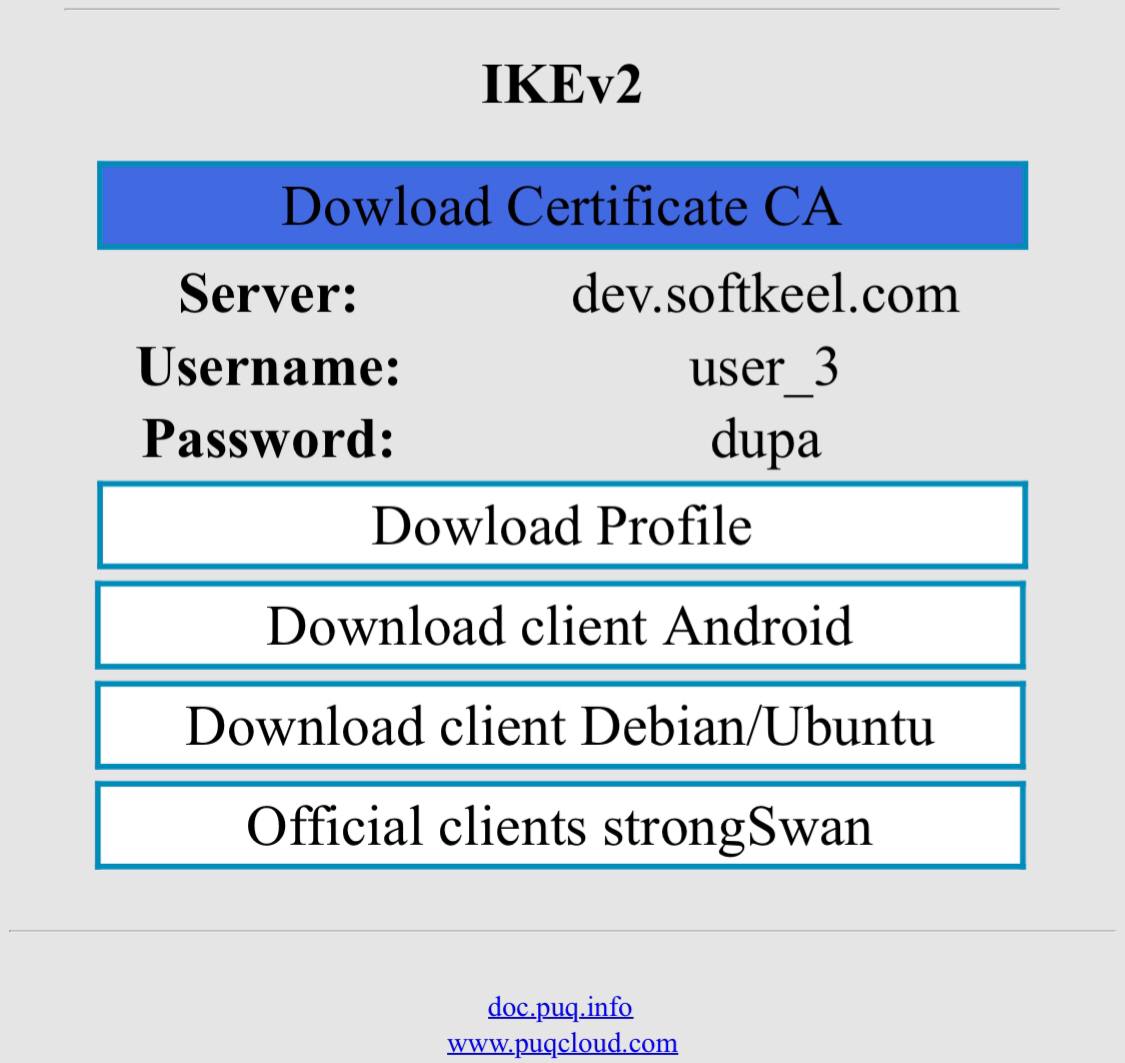](https://doc.puq.info/uploads/images/gallery/2023-07/1.jpg)
3. Next, navigate to the following path: Settings -> General -> VPN & Device Management, and wait for the profile to download and appear in this window.
[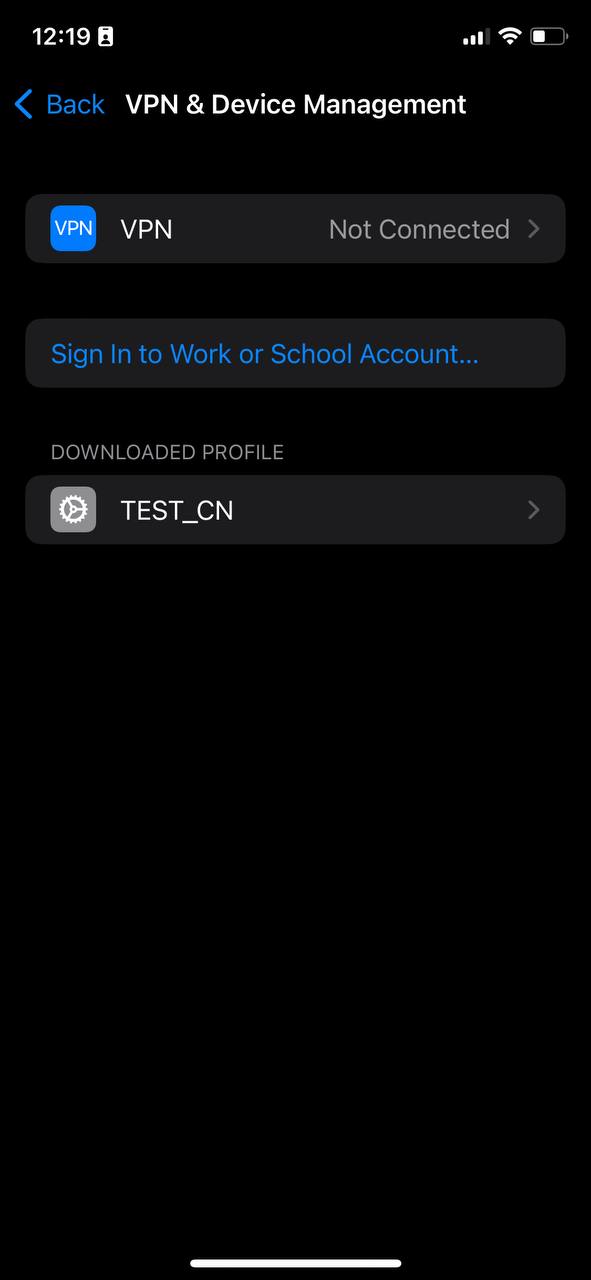](https://doc.puq.info/uploads/images/gallery/2023-07/dhk2.jpg)
4. Tap on the downloaded profile and, click the "Install" button.
[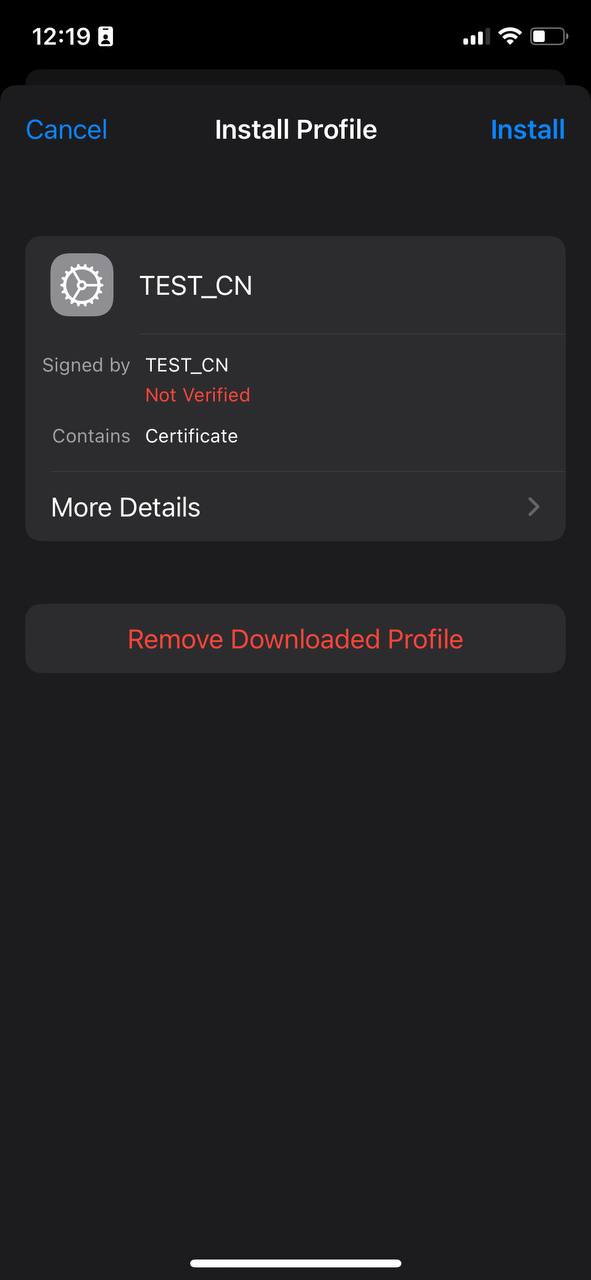](https://doc.puq.info/uploads/images/gallery/2023-07/Mm13.jpg)
5. Enter your password.
[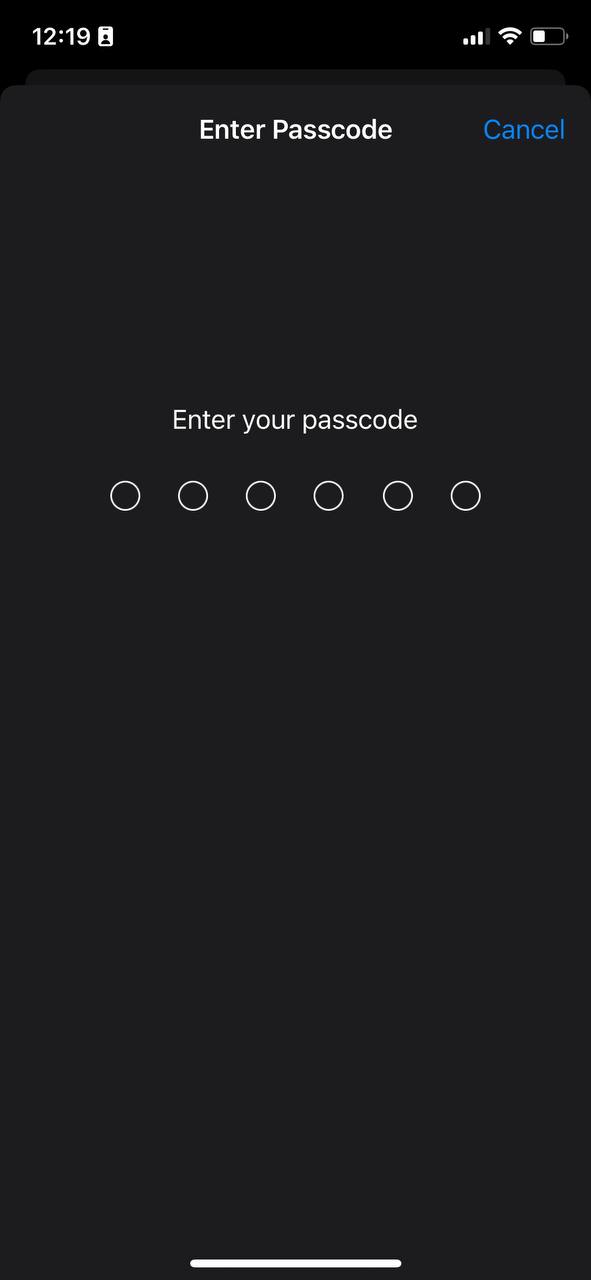](https://doc.puq.info/uploads/images/gallery/2023-07/Wkc4.jpg)
6. Read the warning and press the "Install" button
[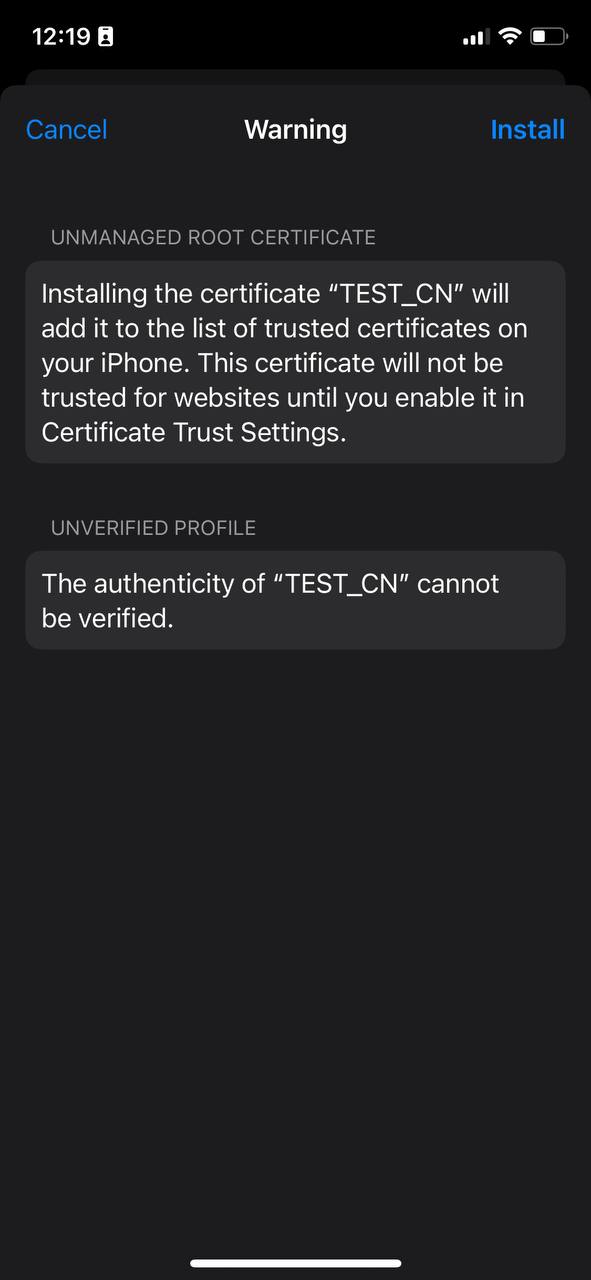](https://doc.puq.info/uploads/images/gallery/2023-07/Sg15.jpg)
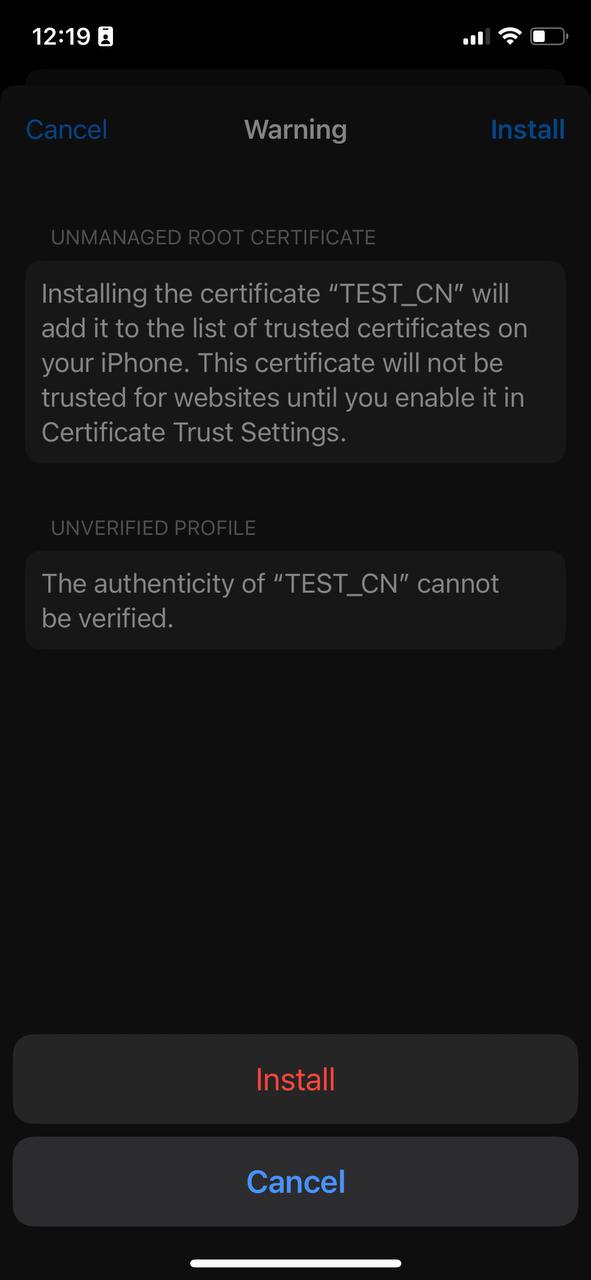
7. Press "Install" again to confirm.
[](https://doc.puq.info/uploads/images/gallery/2023-07/2zN6.jpg)
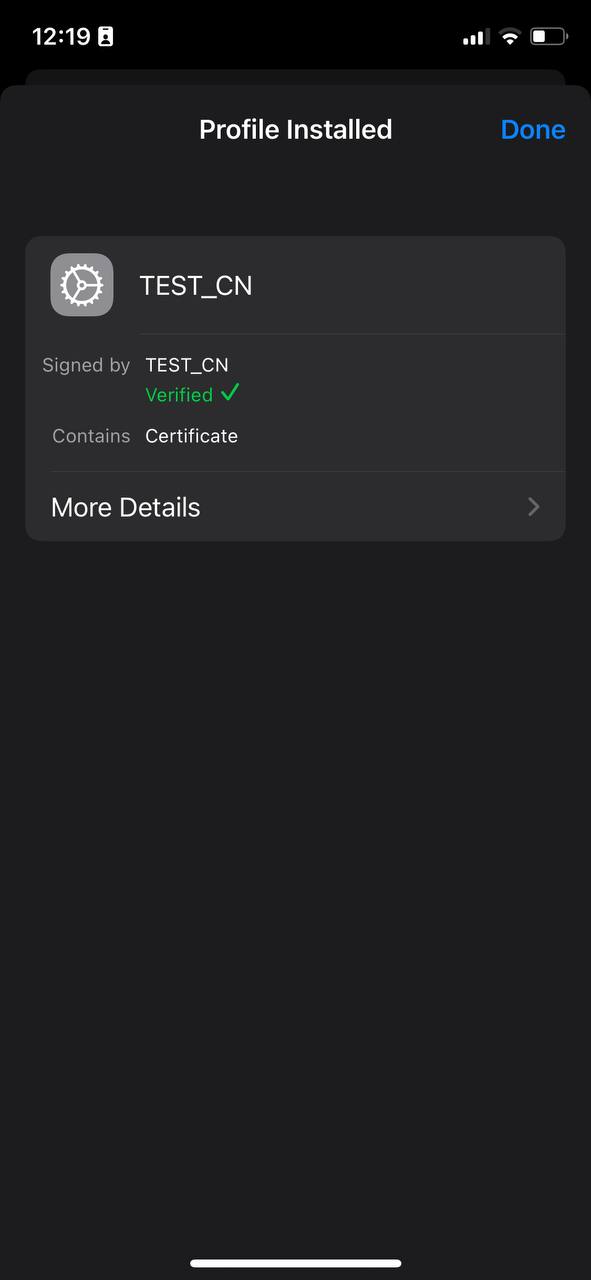
8. A window will appear, showing that the profile has been downloaded and verified.
[](https://doc.puq.info/uploads/images/gallery/2023-07/prC7.jpg)
**Next, you need to configure the VPN.**
1. To do this, go to Settings -> General -> VPN & Device Management -> VPN and tap on "Add VPN Configuration..."
[](https://doc.puq.info/uploads/images/gallery/2023-07/8.jpg)
2. Enter the required details and click "Done."
1. Description: \[Enter a description for this VPN connection\]
2. Server: \[Enter the server address\]
3. Remote ID: \[Enter the remote ID\]
4. Username: \[Enter your VPN username\]
5. Password: \[Enter your VPN password\]
6. Type: IKEv2
7. Proxy: Off
[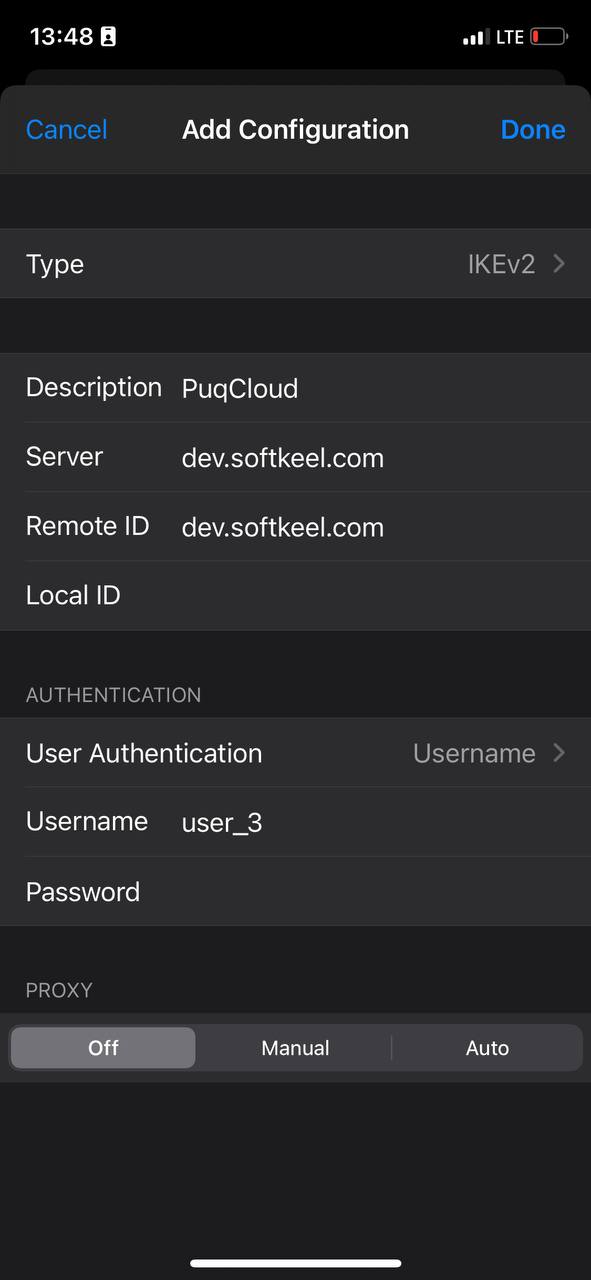](https://doc.puq.info/uploads/images/gallery/2023-07/p2H9.jpg)
3. Finally, select the VPN you added and don't forget to toggle the switch to enable it.
[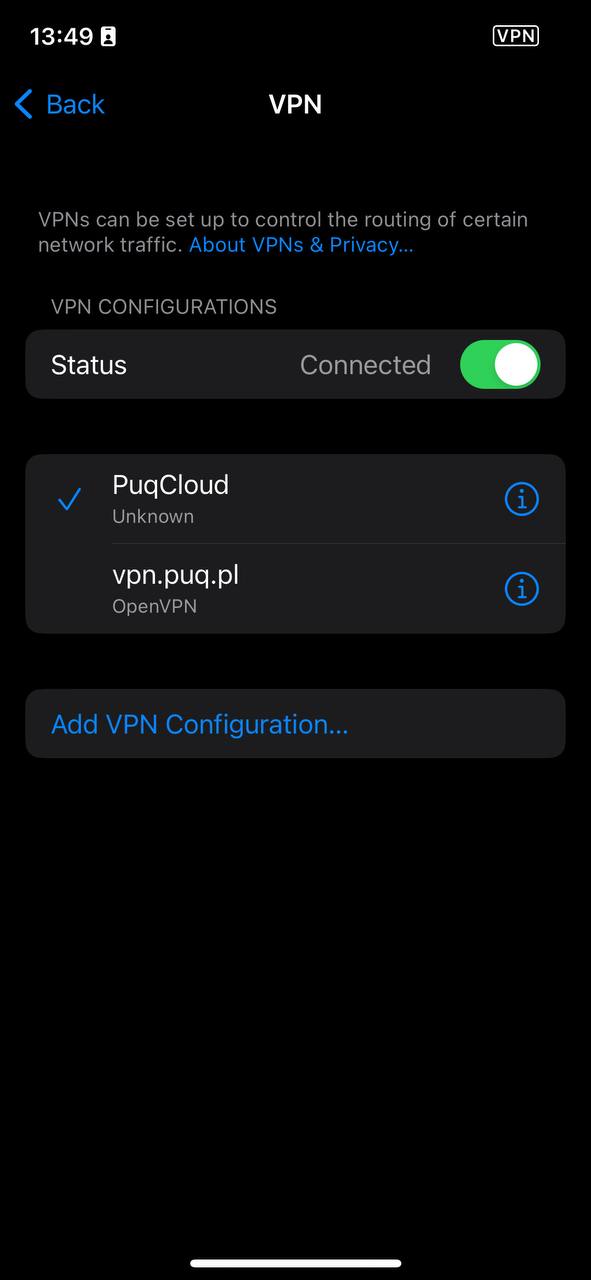](https://doc.puq.info/uploads/images/gallery/2023-07/UkP10.jpg)
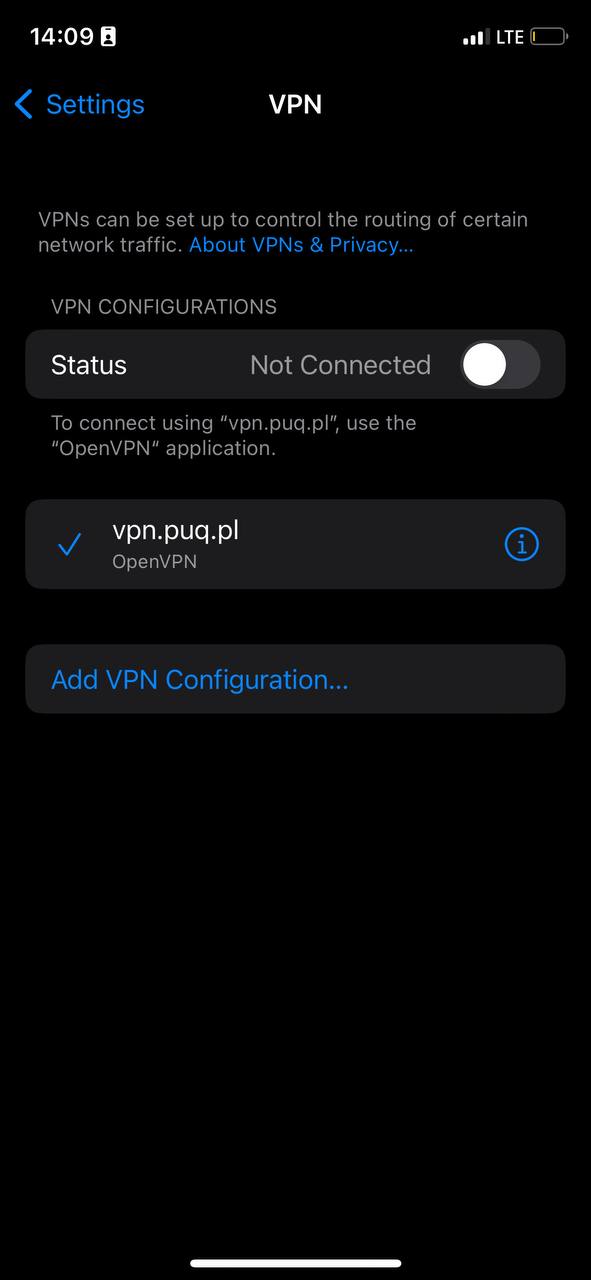
4. By tapping on the (i) icon, you can check the information for this VPN or make any necessary changes
[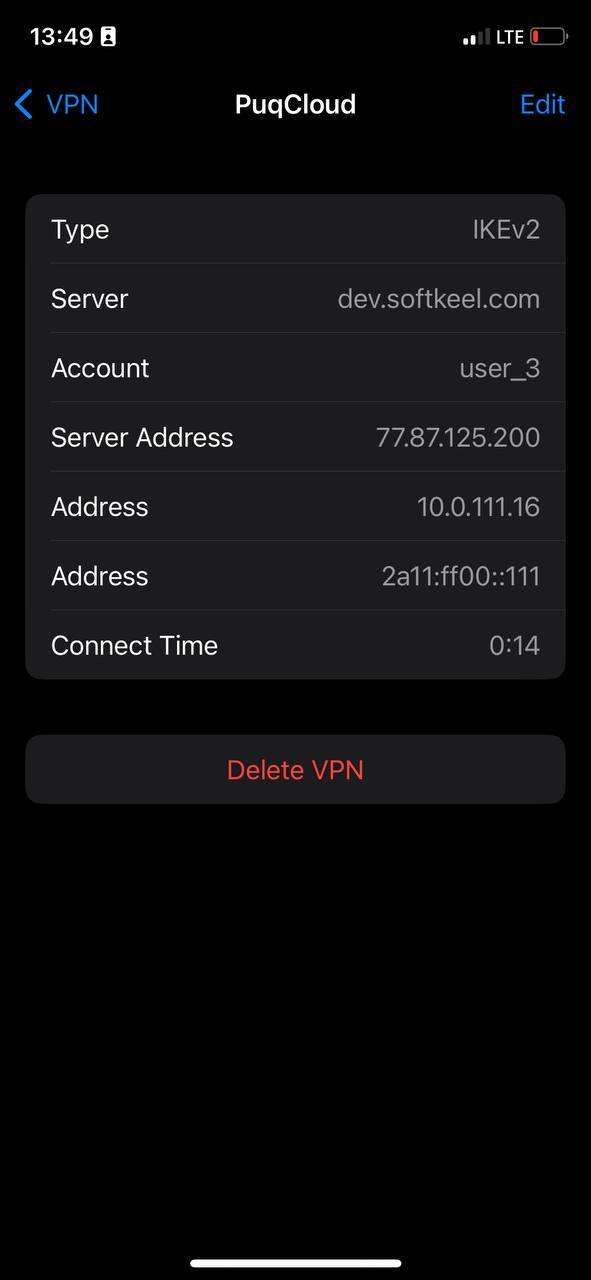](https://doc.puq.info/uploads/images/gallery/2023-07/9Zz11.jpg)
# Traffic Logging
# Traffic Logging Config
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
##### To enable and configure traffic logging go to **Settings->Traffic logging**
Logging all traffic passing through a server can be very resource intensive and can have a significant impact on the performance of the server. This is because logging requires the server to process and store a large amount of data, which can consume a significant amount of CPU, memory, and disk resources. In addition, logging all traffic can generate a large number of log messages, which can further strain the server's resources.
As a result, it is important to carefully consider the need for logging all traffic and to balance this need with the potential impact on the performance of the server. In some cases, it may be more appropriate to only log a subset of traffic or to use sampling or filtering techniques to reduce the volume of logs generated. It is also important to consider the hardware resources of the server and to ensure that the server has sufficient capacity to handle the load of logging all traffic.
In summary, while logging all traffic can be useful for certain purposes, it is important to be aware of the potential impact on the server's performance and to carefully evaluate the need for this level of logging.
[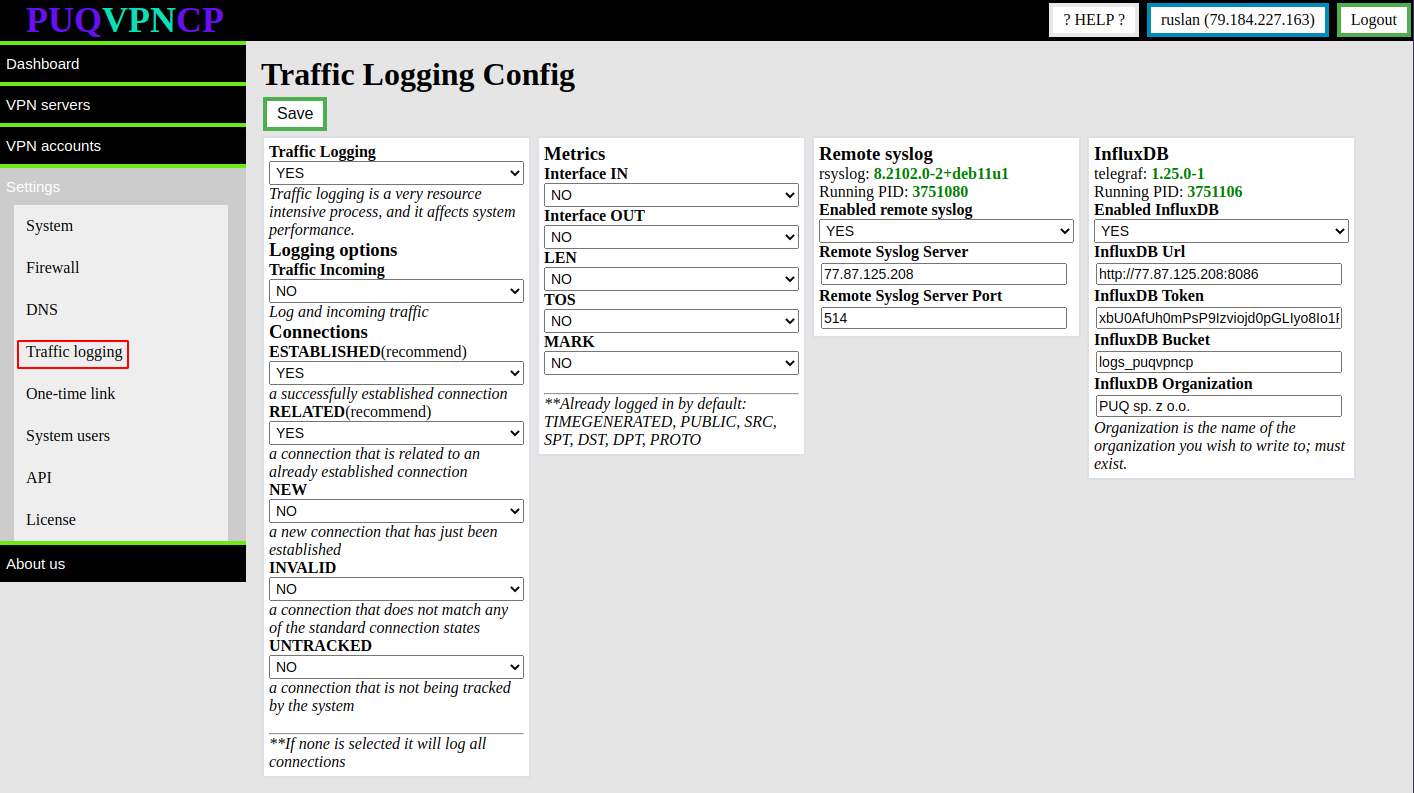](https://doc.puq.info/uploads/images/gallery/2022-12/image-1672237369542.png)
#### Remote syslogTraffic logging section
you can enable logging of client traffic passing through the server
##### Logging options
You can choose the following logging options:
1. Traffic Incoming - Log also incoming traffic. By default, only outgoing traffic is logged.
2. Connections - What connection types to log (ESTABLISHED and RELATED are recommended)
- **ESTABLISHED -** a successfully established connection
- **RELATED -** a connection that is related to an already established connection
- **NEW -** a new connection that has just been established
- **INVALID -** a connection that does not match any of the standard connection states
- **UNTRACKED -** a connection that is not being tracked by the system
**If none is selected it will log all connections**
##### Metrics
What data will be collected and transmitted to a remote server
**Already logged in by default: TIMEGENERATED, PUBLIC, SRC, SPT, DST, DPT, PROTO**
##### Remote syslog
Remote syslog server configuration options
##### InfluxDB
Remote InfluxDB server configuration options
To use logging to the InfluxDB server, you need to install telegraf
[https://docs.influxdata.com/telegraf/v1.21/introduction/installation/](https://docs.influxdata.com/telegraf/v1.21/introduction/installation/)
# rsyslog server settings for receiving logs
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
Here are the steps you can follow to configure rsyslog to receive logs from remote servers:
1. Install rsyslog on the machine that you want to use as the central log server. On a Debian-based system, you can install rsyslog with the following command:
```shell
sudo apt-get install rsyslog
```
2. Open the rsyslog configuration file in a text editor. On a Debian-based system, this file is typically located at /etc/rsyslog.conf.
```shell
sudo nano /etc/rsyslog.conf
```
3. In the configuration file, uncomment the line that reads "module(load="imudp")" and "input(type="imudp" port="514")". This will configure rsyslog to listen for incoming log messages on UDP port 514. If you want to use a different port, you can specify it here.
4. Save and close the configuration file.
5. Restart the rsyslog service to apply the new configuration. On a Debian-based system, you can do this with the following command:
```shell
sudo service rsyslog restart
```
To view the logo, use the command
```shell
sudo less /var/log/syslog
```
You should get something like this
```
Dec 28 15:42:50 dev.softkeel.com [2265632.987952] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=44680 DST=20.190.159.4 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265632.988013] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=44680 DST=20.190.159.4 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.020799] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=44680 DST=20.190.159.4 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.071709] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=44680 DST=20.190.159.4 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.081883] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=44680 DST=20.190.159.4 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.081972] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=44680 DST=20.190.159.4 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.239150] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=44680 DST=20.190.159.4 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.245651] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=37918 DST=40.126.32.160 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.245738] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=37918 DST=40.126.32.160 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.336217] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=37918 DST=40.126.32.160 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.339190] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=37918 DST=40.126.32.160 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.345274] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=37918 DST=40.126.32.160 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.345456] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=37918 DST=40.126.32.160 DPT=443 PROTO=TCP
Dec 28 15:42:50 dev.softkeel.com [2265633.430714] TIMEGENERATED=2022-12-28 15:42:50 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=37918 DST=40.126.32.160 DPT=443 PROTO=TCP
Dec 28 15:43:19 dev.softkeel.com [2265661.777196] TIMEGENERATED=2022-12-28 15:43:19 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=48566 DST=172.217.16.37 DPT=443 PROTO=TCP
Dec 28 15:43:19 dev.softkeel.com [2265661.784642] TIMEGENERATED=2022-12-28 15:43:19 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=48566 DST=172.217.16.37 DPT=443 PROTO=TCP
Dec 28 15:43:20 dev.softkeel.com [2265662.835952] TIMEGENERATED=2022-12-28 15:43:20 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=45142 DST=216.58.215.74 DPT=443 PROTO=TCP
Dec 28 15:43:40 dev.softkeel.com [2265682.853984] TIMEGENERATED=2022-12-28 15:43:40 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=41048 DST=142.251.1.188 DPT=5228 PROTO=TCP
Dec 28 15:43:40 dev.softkeel.com [2265682.893813] TIMEGENERATED=2022-12-28 15:43:40 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=41048 DST=142.251.1.188 DPT=5228 PROTO=TCP
Dec 28 15:43:40 dev.softkeel.com [2265682.921793] TIMEGENERATED=2022-12-28 15:43:40 PUBLIC=77.87.125.200 SRC=10.0.110.7 SPT=41048 DST=142.251.1.188 DPT=5228 PROTO=TCP
```
# Backup settings
# The concept of backups
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## The concept of backups
Backups are designed to create a backup copy of the server settings and then restore it on a new server or on the same server.
##### What settings are not included in the backup:
- System users
- Panel Web Interface SSL Certificates
- License
- Backup settings
- Optionally, you can exclude traffic statistics for VPN users
##### Backup options
- It is possible to manually create backups (with statistics of VPN users and without statistics)
- The ability to install an automatic backup scheduler
- Ability to send a backup to a remote FTP server
- Limiting the number of backups
- Ability to upload a backup to the system and recover
[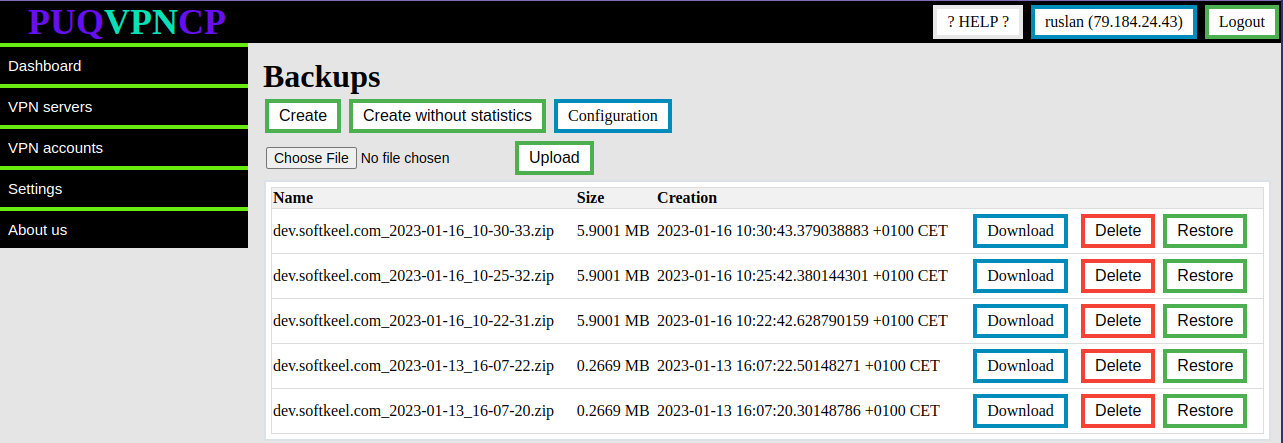](https://doc.puq.info/uploads/images/gallery/2023-01/image-1673863366875.png)
# Backup list
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
Backup settings are available in the **Settings->Backups** menu item
[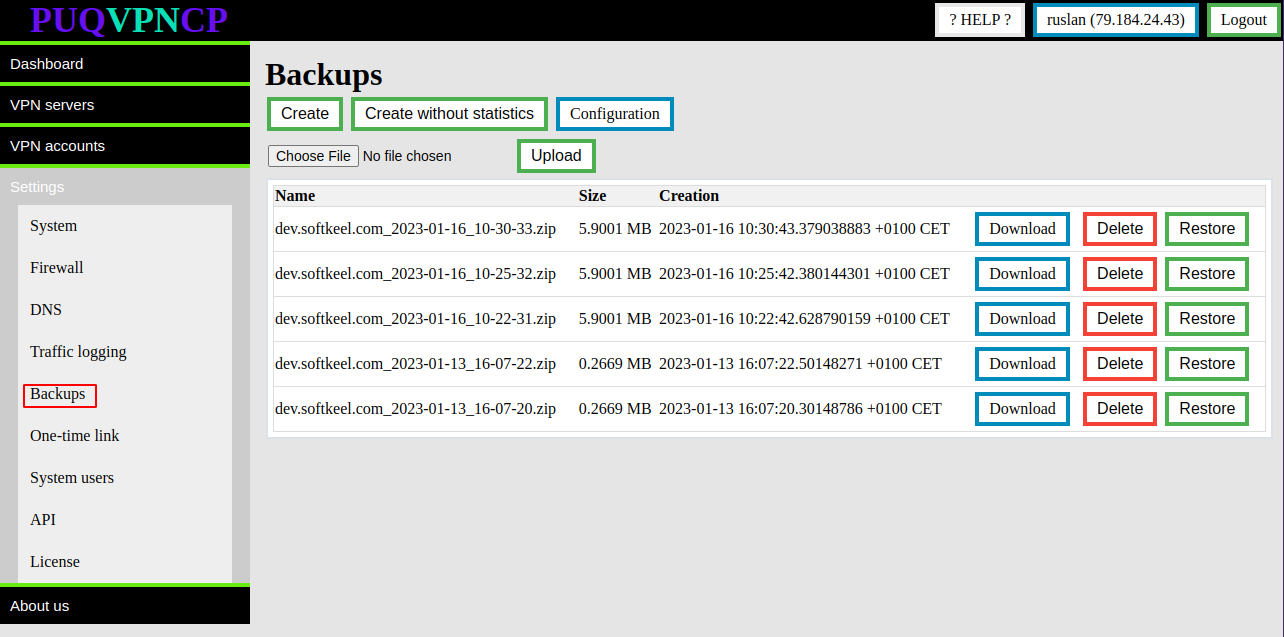](https://doc.puq.info/uploads/images/gallery/2023-01/image-1673863571698.png)
On this page you get a list of available backups.
##### There are function buttons:
- **Download** - To download a backup to a local computer
- **Delete** - In order to delete the backup on the server (does not delete the backup on the FTP server)
- **Restore** - In order to restore the entire configuration of the PUQVPNCP panel from a backup.
##### On this page there are buttons for creating backups:
- **Create -** Creates a full backup
- **Create without statistics -** Create a full backup and exclude traffic usage statistics for VPN users
##### There is also an **Upload** button with which you can upload a backup to the server
# Automatic backup scheduler
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
In order to go to the automation settings of the backup scheduler
Go to **Settings->Backups->Configuration**
[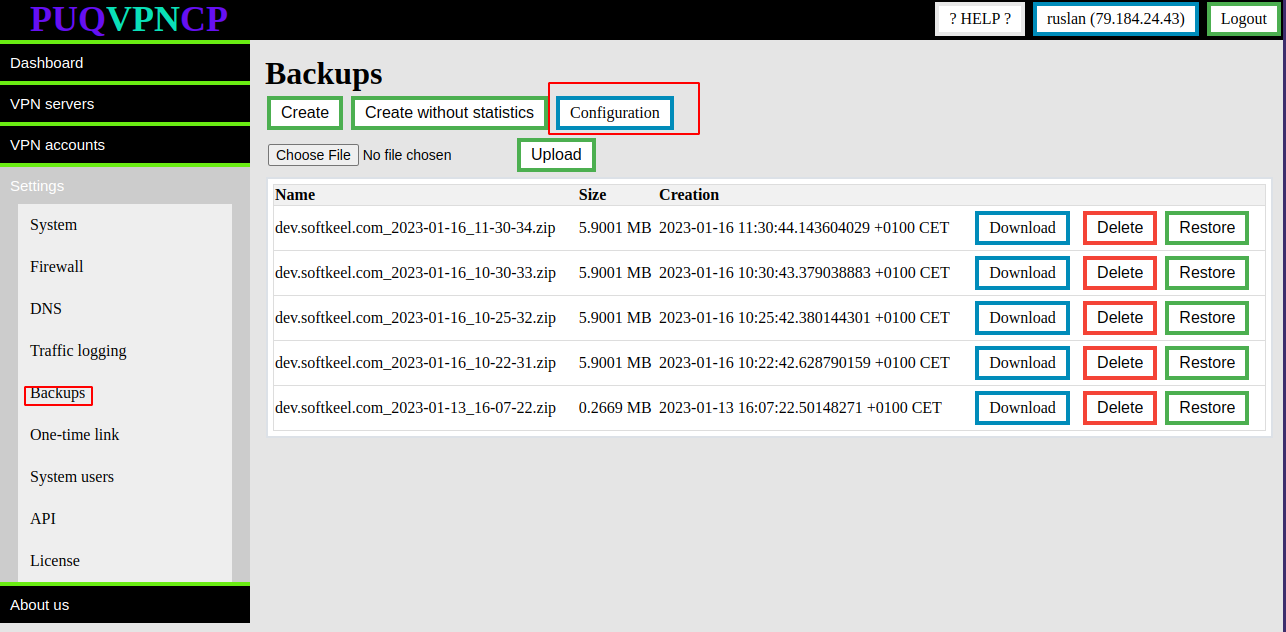](https://doc.puq.info/uploads/images/gallery/2023-01/image-1673865397778.png)
The automatic backup settings page opens.
[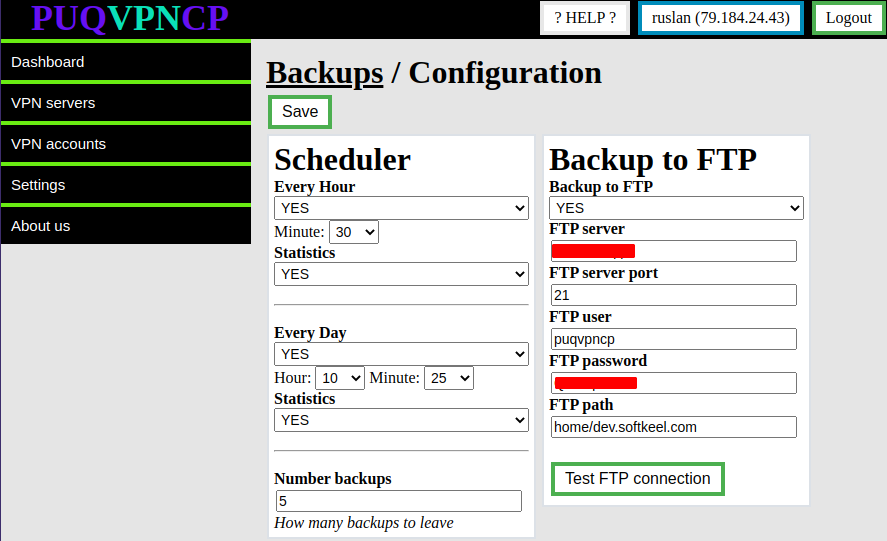](https://doc.puq.info/uploads/images/gallery/2023-01/image-1673865441113.png)
**Scheduler Every Hour** - In this section you can enable hourly automatic backup. It is necessary to enter the minute of the hour in which the automatic backup will be made
**Scheduler Every Day** - In this section, you can enable daily automatic backup. You must enter the hour and minute of the hour in which the automatic backup will be performed
**Backup to FTP** - In this section, you configure the FTP server parameters so that each copy of the backup is automatically sent to the FTP server
# FAQ
# How to recover password
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
**Problem:** Username or password were lost
**Solution:**
In order to restore the default account, you must
\- delete directory with accounts(**All system access accounts will be deleted**)
```shell
rm -R /usr/local/puqvpncp/users
```
\- Restart the **puqvpncp** service
```shell
service puqvpncp restart
```
after these steps, the system creates a default user
**Username:** admin
**Password:** admin
# API
# API Access Hashs
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
##### To manage API Access Hashs, go to the section Settings->API
[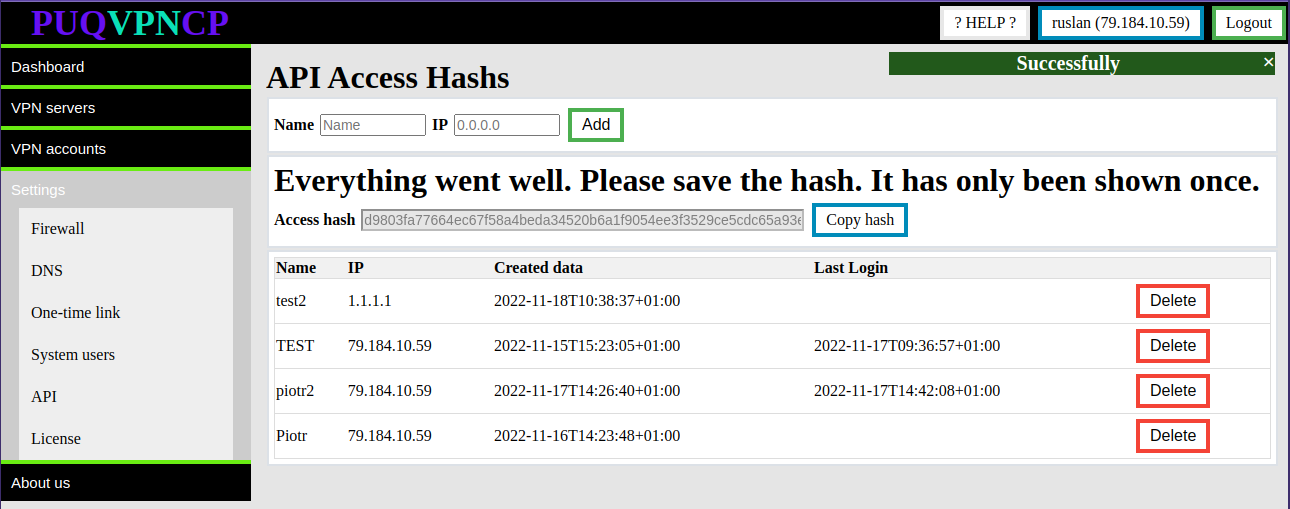](https://doc.puq.info/uploads/images/gallery/2022-11/image-1668764483617.png)
You can view/create/delete API Access Hashs.
Accept the fact that once the Access Hashs API is created, it will only be shown once.
Each API Access Hash only works from a specific IP address.
To authorize the API, API Access Hashs must be passed in the http header as the value of the "access\_hash" parameter in Cookies.
**API Root Link:** https://<Your\_server>/api/v1/
Application methods:
- **GET** - To get information about an object
- **POST** - Creating a new object
- **PUT** - Edit an existing object
- **DELETE** - Delete an existing object
**The data is sent to the server using the POST method.**
**Response from the server in json format**
**Each response from the server will have the same structure.**
```
{
"error" : "",
"msg" : "",
"status" : ""
}
```
- **STATUS:** if the result is successful then it will be "**SUCCESS"**, If the result is not successful it will be "**ERROR**"
- **MSG:** Here are the results of a successful request
- **ERROR:** In case of an error, the error text will appear here.
##### Here is an example using curl
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X GET https://dev.softkeel.com/api/v1/system/status
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"count_accounts" : 550,
"count_accounts_available" : 550,
"count_wireguard" : 100,
"license" : "2023-11-13T18:38:43+01:00",
"license_valid" : true,
"status" : "Loading (Wireguard delete old interfaces)",
"version" : "1.0"
},
"status" : "success"
}
```
# System
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## System status
**Request Structure:** `https:///api/v1/system/status`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X GET https://dev.softkeel.com/api/v1/system/status
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"count_accounts" : 550,
"count_accounts_available" : 550,
"count_wireguard" : 100,
"license" : "2023-11-13T18:38:43+01:00",
"license_valid" : true,
"status" : "Loading (Wireguard delete old interfaces)",
"version" : "1.0"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## System info
**Request Structure:** `https:///api/v1/system/info`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X GET https://dev.softkeel.com/api/v1/system/info
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"cpu_model" : "Common KVM processor",
"cpu_threads" : "4",
"cpu_used_load1" : "0.69",
"cpu_used_load15" : "0.20",
"cpu_used_load5" : "0.28",
"hostname" : "dev.softkeel.com",
"memory_free" : "218",
"memory_total" : "7956",
"memory_used" : "7737",
"memory_used_percent" : "97",
"os_architecture" : "amd64",
"os_name" : "Debian GNU/Linux 11 (bullseye)",
"timezone" : "Europe/Warsaw"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## System reload
**Request Structure:** `https:///api/v1/system/reload`
**Method:** `PUT`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X PUT https://dev.softkeel.com/api/v1/system/reload
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "success",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-PUQVPNCP status not OK
```
##
# WireGuard
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## WireGuard info
**Request Structure:** `https:///api/v1/wireguard/info`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=ae748cb82d024edffdc4cdc14251c1ef5a3bbe6fba7a670f465638b517eef49ca1c19e1e4c025aab" \
-X GET https://dev.softkeel.com/api/v1/wireguard/info
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"wireguard" : "1.0.20210223-1",
"wireguard-dkms" : "1.0.20210219-1",
"wireguard-tools" : "1.0.20210223-1"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## WireGuards servers list
**Request Structure:** `https:///api/v1/wireguard`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=ae748cb82d024edffdc4cdc14251c1ef5a3bbe6fba7a670f465638b517eef49ca1c19e1e4c025aab" \
-X GET https://dev.softkeel.com/api/v1/wireguard
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"Default_87" : {
"address" : "10.0.86.1/24",
"b_download" : "11",
"b_upload" : "22",
"dns_1" : "8.8.8.8",
"dns_2" : "1.1.1.1",
"external_ip" : "77.87.125.200",
"ikev2" : false,
"interface_name" : "wg87",
"internal_traffic" : false,
"keep_alive" : 0,
"listen_port" : "51907",
"name" : "Default_87",
"private_key" : "mPzPaGF2nltQEJ+FAptKJLKG+oG3lYQKrvrn1GOZrXU=",
"public_key" : "u2ACzhkKxlZfI52gcAsZuNdryum5ZgCeNY9ezqEI9kU="
},
"Default_97" : {
"address" : "10.0.96.1/24",
"b_download" : "1",
"b_upload" : "1",
"dns_1" : "8.8.8.8",
"dns_2" : "1.1.1.1",
"external_ip" : "77.87.125.200",
"ikev2" : true,
"interface_name" : "wg97",
"internal_traffic" : false,
"keep_alive" : 1,
"listen_port" : "51917",
"name" : "Default_97",
"private_key" : "4IbFB7rnE6QYdOhd2dssVrNrbhhIb/MV/VyJgB/QkWk=",
"public_key" : "9aLp9bEq+CI+yYM/lMBKEuwIG0NW1fO3IcBjFioI7XQ="
}
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## WireGuard server ADD
**Request Structure:** `https:///api/v1/wireguard`
**Cookie: `access_hash=`**
**Method: `POST`**
**POST data:**
**Options not required:**
```JSON
"name" = "NAME"
"private_key" = "private_key"
"public_key" = "public_key"
"interface_name" = "wgX"
"listen_port" = "51820-65535"
"mtu" = "0-9100"
"keep_alive" = "0-2147483647"
"allowed_ips" = "CIDR format,CIDR format,CIDR format,...."
"endpoint" = "IP|domain"
"address" = "CIDR format"
"internal_traffic" = "1|0"
"external_ip" = "CIDR format"
"dns_1" = "CIDR format"
"dns_2" = "CIDR format"
"ipv6" = "1|0"
"address_ipv6" = "CIDR format"
"dns_1_ipv6" = "CIDR format"
"dns_2_ipv6" = "CIDR format"
"b_download" = "0-10000"
"b_upload" = "0-10000"
"ikev2"= "1|0"
```
**If any parameter is not specified during creation, the system will create, if possible, with a unique parameter.**
**Example:**
```shell
curl \
-b "access_hash=ae748cb82d024edffdc4cdc14251c1ef5a3bbe6fba7a670f465638b517eef49ca1c19e1e4c025aab" \
-d "address=10.0.26.1/24&\
b_download=0&\
b_upload=0&\
dns_1=10.0.26.1&\
dns_2=77.87.125.200&\
external_ip=77.87.125.200&\
interface_name=wg28&\
internal_traffic=1&\
listen_port=51848&\
name=Default_28&\
keep_alive=25&\
ikev2=1&\
mtu=1320&\
allowed_ips=0.0.0.0/1,0.0.0.129/1&\
private_key=2DJdzjmOtT1IfAg25V3PuuTM1biFCcvOk7wI5D4SIUk=&\
public_key=qO2nrUkvxcWJ6xuMbZB1DMiCZ9OLUl918bQS8PnkDTE=" \
-X POST https://dev.softkeel.com/api/v1/wireguard
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"address" : "10.0.26.1/24",
"b_download" : "0",
"b_upload" : "0",
"dns_1" : "10.0.26.1",
"dns_2" : "77.87.125.200",
"external_ip" : "77.87.125.200",
"ikev2" : true,
"interface_name" : "wg28",
"internal_traffic" : true,
"keep_alive" : 25,
"listen_port" : "51848",
"name" : "Default_28",
"private_key" : "2DJdzjmOtT1IfAg25V3PuuTM1biFCcvOk7wI5D4SIUk=",
"public_key" : "qO2nrUkvxcWJ6xuMbZB1DMiCZ9OLUl918bQS8PnkDTE="
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
-The name is already in use
-Wrong network interface name (wgXXX)
-Wrong name (only letters, numbers and '_', '-')
-Keys are invalid
-Interface already in use
-Port already in use
-Wrong external IP format
-Wrong Port format
-IP address or subnet already in use
-Wrong DNS1 IP format
-Wrong DNS2 IP format
```
- - - - - -
## WireGuard server EDIT
**Request Structure:** `https:///api/v1/wireguard/`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Options not required:**
```JSON
"mtu" = "0-9100"
"keep_alive" = "0-2147483647"
"allowed_ips" = "CIDR format,CIDR format,CIDR format,...."
"endpoint" = "IP|domain"
"address" = "CIDR format"
"internal_traffic" = "1|0"
"external_ip" = "CIDR format"
"dns_1" = "CIDR format"
"dns_2" = "CIDR format"
"ipv6" = "1|0"
"address_ipv6" = "CIDR format"
"dns_1_ipv6" = "CIDR format"
"dns_2_ipv6" = "CIDR format"
"b_download" = "0-10000"
"b_upload" = "0-10000"
"ikev2"= "1|0"
```
**Example:**
```shell
curl \
-b "access_hash=ae748cb82d024edffdc4cdc14251c1ef5a3bbe6fba7a670f465638b517eef49ca1c19e1e4c025aab" \
-d "internal_traffic=false&\
listen_port=51333&\
keep_alive=50&\
mtu=1320&\
allowed_ips=0.0.0.0/1,0.0.0.129/1&\
ikev2=0" \
-X PUT https://dev.softkeel.com/api/v1/wireguard/Default_128
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"address" : "10.0.127.1/24",
"b_download" : "6",
"b_upload" : "7",
"dns_1" : "8.8.8.8",
"dns_2" : "1.1.1.1",
"external_ip" : "77.87.125.200",
"ikev2" : false,
"interface_name" : "wg128",
"internal_traffic" : false,
"keep_alive" : 50,
"listen_port" : "51333",
"name" : "Default_128",
"private_key" : "cAnS3fQbdvHUS+9eV05Uf+cP+gn8i4LpzXsdE7mUZ2E=",
"public_key" : "RVNBbsEIjEkgsyXzmd5vMBIcOzzcTSC/fPscdDwzlQo="
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
-Keys are invalid
-Interface already in use
-Port already in use
-Wrong external IP format
-Wrong Port format
-IP address or subnet already in use
-Wrong DNS1 IP format
-Wrong DNS2 IP format
```
- - - - - -
## WireGuard server DELETE
**Request Structure:** `https:///api/v1/wireguard/`
**Cookie: `access_hash=`**
**Method: `DELETE`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X DELETE https://dev.softkeel.com/api/v1/wireguard/Default_90
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "success",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
-Cannot be deleted. There are active peers.
```
- - - - - -
## WireGuard server DETAIl
**Request Structure:** `https:///api/v1/wireguard/`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=ae748cb82d024edffdc4cdc14251c1ef5a3bbe6fba7a670f465638b517eef49ca1c19e1e4c025aab" \
-X GET https://dev.softkeel.com/api/v1/wireguard/Default_95
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"address" : "10.0.127.1/24",
"b_download" : "6",
"b_upload" : "7",
"dns_1" : "8.8.8.8",
"dns_2" : "1.1.1.1",
"external_ip" : "77.87.125.200",
"ikev2" : false,
"interface_name" : "wg128",
"internal_traffic" : false,
"keep_alive" : 50,
"listen_port" : "51333",
"name" : "Default_128",
"private_key" : "cAnS3fQbdvHUS+9eV05Uf+cP+gn8i4LpzXsdE7mUZ2E=",
"public_key" : "RVNBbsEIjEkgsyXzmd5vMBIcOzzcTSC/fPscdDwzlQo="
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
```
- - - - - -
## WireGuard server PEERS
**Request Structure:** `https:///api/v1/wireguard//peers`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/wireguard/Default_125/peers
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"peer_126" : {
"allowed_IPs" : "10.0.124.2",
"b_download" : "8",
"b_upload" : "6",
"mangle" : "232",
"name" : "peer_126",
"password" : "K@6#2XR9$3",
"private_key" : "AG9dc2NLVVBGT3bxg7YT0QJHTplWHcHJmzAPUOOx22g=",
"public_key" : "PasJjAGnzTxV4meACiGtx3QvJ6jzvPugs4nBdzKUcSU=",
"status" : "enable",
"username" : "user_127",
"wg_name" : "Default_125"
},
"peer_132" : {
"allowed_IPs" : "10.0.124.3",
"b_download" : "8",
"b_upload" : "6",
"mangle" : "238",
"name" : "peer_132",
"password" : "6K2W3@W4$7",
"private_key" : "QJhk78F9ZyLmudqTlJAr4eVCSSmMgVblNEzWFyALbW4=",
"public_key" : "6jyITtbPNZNzRXexxIEnVBrN7hriRep3nlKhLeyqSFk=",
"status" : "enable",
"username" : "user_133",
"wg_name" : "Default_125"
}
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
```
- - - - - -
## WireGuard server port forward
**Request Structure:** `https:///api/v1/wireguard//port_forward`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=ee34183e198f9ba40a97a475579f8561bfcbe8c6f08337362b2f9e3cf1092e2d75f18179a80a14d8" \
-X GET https://dev.softkeel.com/api/v1/wireguard/Default_125/port_forward
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"123_tcp" : {
"dst_port" : 123,
"protocol" : "tcp",
"to_peer" : "peer_126",
"to_port" : 444
},
"123_udp" : {
"dst_port" : 123,
"protocol" : "udp",
"to_peer" : "peer_132",
"to_port" : 2223
},
"2222_tcp" : {
"dst_port" : 2222,
"protocol" : "tcp",
"to_peer" : "peer_126",
"to_port" : 22
},
"53_udp" : {
"dst_port" : 53,
"protocol" : "udp",
"to_peer" : "peer_126",
"to_port" : 53
}
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
```
- - - - - -
## WireGuard port worward ADD
**Request Structure:** `https:///api/v1/port_forward`
**Cookie: `access_hash=`**
**Method: `POST`**
**POST data:**
**Required:**
```JSON
"dst_port" = 1-65535
"protocol" ="tcp|udp"
"to_peer" = "name_of_peer"
"to_port" = 1-65535
```
**Example:**
```shell
curl \
-b "access_hash=ee34183e198f9ba40a97a475579f8561bfcbe8c6f08337362b2f9e3cf1092e2d75f18179a80a14d8" \
-d "dst_port=23&\
protocol=udp&\
to_peer=peer_126&\
to_port=325" \
-X POST https://dev.softkeel.com/api/v1/wireguard/Default_125/port_forwarding
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"dst_port" : 23,
"protocol" : "udp",
"to_peer" : "peer_126",
"to_port" : 325
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
-Protocol must be tcp or udp
-DST port must be within 1-65535
-DST port and protocol are already enabled
-ListenPort processing error
-DstPort cannot be ListenPort
-To port must be within 1-65535
-Entered incorrect peer
```
- - - - - -
## WireGuard port worward DELETE
**Request Structure:** `https:///api/v1/port_forward//`
**Cookie: `access_hash=`**
**Method: `DELETE`**
**Example:**
```shell
curl \
-b "access_hash=ee34183e198f9ba40a97a475579f8561bfcbe8c6f08337362b2f9e3cf1092e2d75f18179a80a14d8" \
-X DELETE https://dev.softkeel.com/api/v1/wireguard/Default_125/port_forwarding/23/udp
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "success",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
-There is no such port forwarding
-Incorrect protocol parameter (tcp|udp)
-Incorrect dst_port parameter
```
- - - - - -
## WireGuard server Firewall Nat Rules
**Request Structure:** `https:///api/v1/wireguard//firewall_nat_rules`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/wireguard/Default_125/firewall_nat_rules
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "10.0.124.0/24 -> 0.0.0.0/0 SNAT to:77.87.125.200 Pkt:0 Bytes:0\n",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
```
- - - - - -
## WireGuard server Firewall Filter Rules
**Request Structure:** `https:///api/v1/wireguard//firewall_filter_rules`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/wireguard/Default_125/firewall_filter_rules
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "10.0.124.0/24 -> 10.0.124.0/24 ACCEPT Pkt:0 Bytes:0\n",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
```
- - - - - -
## WireGuard server Traffic Control
**Request Structure:** `https:///api/v1/wireguard//traffic_control`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/wireguard/Default_125/traffic_control
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "qdisc htb 1: root refcnt 2 r2q 10 default 0 direct_packets_stat 0 direct_qlen 1000\n Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0) \n backlog 0b 0p requeues 0\n",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
```
- - - - - -
## WireGuard server Dump
**Request Structure:** `https:///api/v1/wireguard//dump`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/wireguard/Default_125/dump
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"port" : "51945",
"public_key" : "Ok2/cmy13UkcrXZOCsiXwj82uRhsX1ev+6BF8Z+8alc="
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
```
- - - - - -
## WireGuard Get Available IPs
**Request Structure:** `https:///api/v1/wireguard//available_ips`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/wireguard/Default_125/available_ips
```
**Response example:**
```JSON
{
"error" : "",
"msg" : [
"10.0.124.4",
"10.0.124.5",
"10.0.124.6",
"10.0.124.7",
"10.0.124.8",
"10.0.124.9",
"10.0.124.10",
"10.0.124.254"
],
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
```
- - - - - -
## WireGuard Set bandwidth fo all peers
**Request Structure:** `https:///api/v1/wireguard//set_bandwidth`
**Method:** `PUT`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/wireguard/Default_125/set_bandwidth
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Wireguard server not found
```
# Accounts
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## Accounts LIST
**Request Structure:** `https:///api/v1/account`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/account
```
**Response example:**
```JSON
{
"error" : "",
"msg" : [
{
"allowed_IPs" : "10.0.110.4",
"b_download" : "12",
"b_upload" : "12",
"mangle" : "322",
"name" : "ruslan_dom_pc",
"password" : "FE*37#L2WC",
"private_key" : "UN75r5fizeA5jaCAzF7/nOTTynu67ngsm4jxfiHaHGI=",
"public_key" : "sdxzHEBOdgm9ZzRn2tw2bzdnU1v7mUp1plpAU+craSo=",
"status" : "enable",
"username" : "user_217",
"wg_name" : "77_87_125_209"
},
{
"allowed_IPs" : "10.0.110.3",
"b_download" : "12",
"b_upload" : "12",
"mangle" : "286",
"name" : "ruslan_pc",
"password" : "78gYA%!!9X",
"private_key" : "GOLitV1C3WT6Pn2rNS8QtgOLRMiJ385DYoDcfnrRbXY=",
"public_key" : "VeQE3cIzmo58otUUzpfkEDWqk1jscoO9KRAKNtIW1QY=",
"status" : "enable",
"username" : "user_181",
"wg_name" : "77_87_125_209"
},
{
"allowed_IPs" : "10.0.110.17",
"b_download" : "12",
"b_upload" : "12",
"mangle" : "131",
"name" : "ruslan_telefon",
"password" : "jvPdmqqTmRV9",
"private_key" : "MEZAzrlpzqNJCT8k9JWLkBL2+TPe/LZQp3RAWEqffko=",
"public_key" : "GA2IQFgC+SVYwoIetUNQPSR1ytiet4xxXXAJ+P+IlUY=",
"status" : "enable",
"username" : "user_32",
"wg_name" : "77_87_125_209"
}
],
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Account DETAIL
**Request Structure:** `https:///api/v1/account/`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/account/peer_10
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"allowed_IPs" : "10.0.105.18",
"b_download" : "20",
"b_upload" : "20",
"mangle" : "109",
"name" : "peer_10",
"password" : "dH4%%2M2%B",
"private_key" : "GNuP0siryMimPSuF7Hnmw0D7gY7FXzoY6IgUmt1uuXc=",
"public_key" : "7C5u5vZk051iA5W2zfbxjlZDgAdm7HdRFRgarI8nBw4=",
"status" : "enable",
"username" : "user_10",
"wg_name" : "Default_106"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
```
- - - - - -
## Account ADD
**Request Structure:** `https:///api/v1/account`
**Cookie: `access_hash=`**
**Method: `POST`**
**POST data:**
**Required:**
```JSON
"wg_name" = "WG_NAME"
"allowed_IPs" = "CIDR format"
```
**Not required:**
```JSON
"name" = "NAME"
"status" = "enable|disable"
"username" = "USERNAME"
"password" = "PASSWORD"
"allowed_IPs" = "CIDR format"
"allowed_IPs_ipv6" = "CIDR format"
"private_key" = "private_key"
"public_key" = "public_key"
"b_download" = "0-10000"
"b_upload" = "0-10000"
"wg_name" = Name of WireGuard
```
**If any parameter is not specified during creation, the system will create, if possible, with a unique parameter.**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-d "wg_name=77_87_125_209&\
allowed_IPs=10.0.110.52&\
b_download=100&\
b_upload=100&\
name=NAME111&\
password=PASSWORD&\
status=disable&\
username=USERNAME111" \
-X POST https://dev.softkeel.com/api/v1/account
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"allowed_IPs" : "10.0.110.52",
"b_download" : "12",
"b_upload" : "12",
"mangle" : "100",
"name" : "NAME111",
"password" : "PASSWORD",
"private_key" : "kC8n0NGFxwqvwIfI8xJg2ZzRtp950ltC4ugPHlPxsm0=",
"public_key" : "p3i2VHZRHwVk3uk+Yo4oKoeQ6gLF+jF33P+pnKai3iE=",
"status" : "disable",
"username" : "USERNAME111",
"wg_name" : "77_87_125_209"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
-VPN account limit exceeded
-Wireguard server not valid
-Wrong name (only letters, numbers and '_', '-')
-The name is already in use
-The username is already in use
-Wrong Username (only letters, numbers and '_', '-')
-Wireguard server not valid
-Wrong IP format
-IP address already in use
-The IP address is not within the range of the wireguard server
-Keys are invalid
```
- - - - - -
## Account EDIT
**Request Structure:** `https:///api/v1/account/`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Not required:**
```JSON
"status" = "enable|disable"
"password" = "PASSWORD"
"allowed_IPs" = "CIDR format"
"allowed_IPs_ipv6" = "CIDR format"
"b_download" = "0-10000"
"b_upload" = "0-10000"
```
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-d "allowed_IPs=10.0.110.60&\
b_download=11&\
b_upload=11&\
password=PASSWORD111122223333&\
status=enable" \
-X PUT https://dev.softkeel.com/api/v1/account/NAME111
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"allowed_IPs" : "10.0.110.60",
"b_download" : "11",
"b_upload" : "11",
"mangle" : "100",
"name" : "NAME111",
"password" : "PASSWORD111122223333",
"private_key" : "kC8n0NGFxwqvwIfI8xJg2ZzRtp950ltC4ugPHlPxsm0=",
"public_key" : "p3i2VHZRHwVk3uk+Yo4oKoeQ6gLF+jF33P+pnKai3iE=",
"status" : "enable",
"username" : "USERNAME111",
"wg_name" : "77_87_125_209"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
-Wireguard server not valid
-Wrong external IP format
-IP address already in use
-The IP address is not within the range of the wireguard server
```
- - - - - -
## Account DELETE
**Request Structure:** `https:///api/v1/account/`
**Cookie: `access_hash=`**
**Method: `DELETE`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X DELETE https://dev.softkeel.com/api/v1/account/NAME111
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "success",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
```
- - - - - -
## Account Config Text
**Request Structure:** `https:///api/v1/account//config_text`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/account/peer_10/config_text
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "[Interface]\tAddress = 10.0.105.18/24\n\tDNS = 8.8.8.8,1.1.1.1\n\tPrivateKey = GNuP0siryMimPSuF7Hnmw0D7gY7FXzoY6IgUmt1uuXc=\n\t\n[Peer]\n\tAllowedIPs = 0.0.0.0/0\n\tEndpoint = 77.87.125.200:51926\n\tPublicKey = Hkldth2Pdu/jnJ0NH4cjSlsun2pFdIUZXt0h5qaNzmA=",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
```
- - - - - -
## Account Config QR
**Request Structure:** `https:///api/v1/account//config_qr`
**Method:** `GET`
**Cookie: `access_hash=`**
**Output:** data:image/png;base64
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/account/peer_10/config_qr
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "iVBORw0KGgoAAAANSUhEUgAAAfQAAAH0AQMAAADxGE3JAAAABlBMVEX///8AAABVwtN+AAAGTUlEQVR42uydP9arMA7F5UNBmSWwFC/NXhpLYQmUFBw0R/fKJuR900wDycjFO3kJPxrbsv5c65MYMWLEiBEjxv80RsVIh3+q/Hqai8igutp/9Bi2ly65lqS7A8H/CL/Zv/aDyGuRovbBeftxUq3J+HWaRYznK4N/Cv9SnYukfVxfS1aVYbcX2ayLyMsXh41c7e3jaq8M/lk8NuYqUuphvNpKSLYSJp3LITKu9ib7Mfgn8oJHMO2gFhGY2VWyYiFgTRTdJfgf42G/RcxE28dk2CLZHoH9nuVI6mczVtJf9j/4u/jmP/GILb7Fl1w17eP2WvJcrj/+F/8r+Ft4H5jhddIKt3edzH5jcy9Zqx6DrnCuzLj/OYK/iTf7O2c9EvzfrO7/Cu0vf+R3k1ZJZn/NOdbgf4WXac5Vkm4W9YgI/a+stv97/GofMna9nb84r4N/Ai+jHbZqj/CITR6/iiaf/6p9wH4vOK+DfwZvgeksicHqLOIvgtXeEP8InCvzkjXtMO5Zg38KP6rOUg7bvzxisUUXKfamzXZt5Y/0mobttWCbB/8rPIKdg7kmpn/5yDFsI8y22QTkfxHcciUF/xDetriardYVyV7/amYmAimJ5OdvLWk3myC5SvDP4EddzX8iL5hiPGLYzoO4eJiLTwOyE+/5h+Dv5JnPg9WlsysMUfGmEc/K0ZJLhSHNkjX4H+E9RZg8RSHFU4SZwarSf95bcXXQ7XXxn4O/l/esg8WvnGLO/6QW9Wzc9sxO6Vzw3WuR9/UT/K38iBILXVyZ5tKn+C25pAfqb3NpmaT3/FHwt/IMYLuLa88OmOKqyeYf/lNTLaBM84//FfxX8y9scfuwdokDnj3aE4fAuJMaP/Mfwd/Kj7pkSBxgyavwsOXDo/vUZtxPQ75c5j/4m3nYb+3OLrymxfV/G0syB6ou6uIkf3nwT+BZf4H9Rf4P569M1B+5c0yrCyUgn/qIX4L/Xt7z/wxRJ63lGFBIh4vF5IaLe11/5MWd4B/CI8QplDgwazjY/PsRS3HhQTe7npkoCf4hPDemF9sQ4tgRO9mbUHWZPX+E+Xdx0rV+GvztvMLrfaky//s6K95mbA8oGaZZCourl/xv8F/Nw1eeBVoHPAJPrOs/oX84miFQXLO4rJ/g7+WbiVbknyDRHehIu/6zJycUySnq7y/5x+Bv5Ec4S5h/odjTSyyYfyyOdqcpa0VyePqs3wV/J98GEnue/1PtJ7Hkmpj/1dq+yyrB/wYvrvoUlzjA2TL/uXJNNf0nywTQn9mBHfxT+M/84TXEafr7jeIkOlfLh340+Ht5llgEV1xw6xDBDjUNlO0yE1Gq7tKdq+CfwDPF58IilLh3+k9FdB+p3+TmpswM5++7/Q7+6/mZxRq/P6peP2+rJjdxUq6FkdDysX6Cv49v+Qfvn1GFV9ROiTXnf+vFOXkt0/X+YfD38j2Q9RQvd7JAv9C7ZrTeKIMvjuCfwZ/37zGQInL9H+4/sLgGcVn7CnqV4H+GR/6QZTekCBn1nLFqTW7Jm7jwY/0EfyfvKfousXb/OZuzxJRUz98XVcavF/1h8HfyHqwy/hHoF3bxrO95bfTM36t+1N+Cv5Xv/YvYf+H9/tLB5FJm/wWBuMHvvxQN/jf4rj/zYnkPcdTzhxkOGM5f1bQPXdwd/CN46I/6xaQqrn9Q9L/h+dvu/6J/kb88+GfwLJHWs0SqniKq/fzt9Rdcn4AStAb/GB7xyJGoXyi9fw308+f9JVzkZnLwqj8J/qv5VqJpKYpC/2uipBD2G8091e/vD4yJgn8O7x4y6zfVux67JWdIRHGEf0L+UIJ/Bu/6sVYi9V9Q/5bB75/ppTnrn/qz4O/j1VV/a2v75ld8GdK0/gtYCV2/GfyP8K3/49Ek2mdLnPP47c1xUnfOgn8G/9Z/FSU2GmtIBNPe5Q/enKzIv/2vg7+X978fcLhq5aq/1tas8f3+/mf/x+Bv5dvfD2h71PvP9/6pOH99/ltK+K+/PxD8F/OJV4SxxZnil1N/dPi171LTPmyf+pfgH8H7D7w/cbb4QyPA9/zvR//O4O/mW2MTZYqht5jvnVibEHQuvMm0/JM/DP4+/u3vBzB/1FrCtV41Wo/2J7HYP/Xa/y34r+ZjxIgRI0aM/7fxnwAAAP//JkrrMBYUTS4AAAAASUVORK5CYII=",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
```
- - - - - -
## Account IKEv2 Profile
**Request Structure:** `https:///api/v1/account//ikev2_profile`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=4a1eaf3a9f086baa452bac3c4e92eb60e34755d23f36190f44720b9b43700c23543aabb2794eda15" \
-X GET https://dev.softkeel.com/api/v1/account/peer_10/ikev2_profile
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "{\n\t\t\"uuid\": \"da7782cd-d00c-4114-9250-6c798585a441\",\n\t\t\"name\": \"dev.softkeel.com\",\n\t\t\"type\": \"ikev2-eap\",\n\t\t\"remote\": {\n\t\t \"addr\": \"dev.softkeel.com\",\n\t\t \"id\": \"dev.softkeel.com\",\n\t\t \"cert\": \"-----BEGIN CERTIFICATE-----\rMIIFfDCCA2SgAwIBAgIIMYZL3xAvgfwwDQYJKoZIhvcNAQEMBQAwXDEQMA4GA1UE\rAxMHUFVRIFZQTjEXMBUGA1UEChMOUFVRIHNwLiB6IG8uby4xEDAOBgNVBAsTB1BV\rUSBWUE4xEDAOBgNVBAcTB1dhcnN6YXcxCzAJBgNVBAYTAlBMMB4XDTIyMTIwNTEx\rMzIzOFoXDTMyMTIwMjExMzIzOFowXDEQMA4GA1UEAxMHUFVRIFZQTjEXMBUGA1UE\rChMOUFVRIHNwLiB6IG8uby4xEDAOBgNVBAsTB1BVUSBWUE4xEDAOBgNVBAcTB1dh\rcnN6YXcxCzAJBgNVBAYTAlBMMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKC\rAgEA1nYVzVwZxckXMsCeR3AnoPgvRHubvIslIPvp4lCFnSXZJhTXC5mmicZauPm1\rL0mpclc9umNOM1LxSHV4pcFYP+M1bDUYMef3iaufeQO3cU4R4UrJLsCC/WGwvw1o\rIqYDCxUtB0ePxZHNsBXDxu2/F0eVjX5SiPnCDxyY/tKsouJnX+bTGB5r0byeon6h\rA7V9mVrKJfKrIXhzKPtle28nFa9c6aRu+ROq3KotcradPSdzzzzFhCSCXChbI7+y\rdfnSiJ3rARREHljMpv0rWM/9NyCPHUIJaR+XJ8JQMDdQxMP8oN0fKB8y66foLiFD\roXWLvtGIFPkEnHbX2T7N//ly5xkA97upoQvo7wxtWV4xOIe1nfLesSZVCl/UL50d\r+LVf6NbguDda2HE15AuX6MjnOtX18Yn6VQNUo8R5rr+3dpuZnUYVzfdbnaVmmSuc\rISsQEUTZMzwTzCffpUwPzp8MMWB2K1pSOMTtC7o7cEjnv2BV8IuKhgK1V66lRapx\rcCWF/L1bHRasaqr5JCebGIVZNsd2qYJyuD6p0xP+VVo3PoboqusASKvbQ9PcoMdx\rm8GJHzNnJsuUQhapP2PpDpdht58p0xstWyPnANDsfbqooFWpwAJWhHlkl7JhQWuY\repEWKs78B3C2LYT6UeU4nJmRYNmsuclOUj9HpSJEMZ/nPnECAwEAAaNCMEAwDwYD\rVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8EBAMCAQYwHQYDVR0OBBYEFFbCzI+j1Md8\rNjG1pCPq+ksO0MhgMA0GCSqGSIb3DQEBDAUAA4ICAQBpmyQRfUF/BiuF76vEcwci\rOuuiBaoPcEOwQIueje84KtaEwA0a+QKX4sPGHE4Eoxv7JHEJhBfoeKABTgpIv+qF\rnWdEO+sMTowLhrcoB1VPTw50w3mOYDLG+aqcC3e7UrXoMx+MWmPM3u3/zUkp5j/f\rAsIZL4YdXBtwqmmoj13zg6URslhXhlPeqw+OiqevfpPZE1a1IgXTEY0Xnba1B5o6\reRUCLcUO4dYjv3Eg55WKKN4uPkmm0u1JiWZp8g13FBK1hss/g1qkh3ZW5nMVDjTP\rGFGrY+eHLzEgM8RRieJpU+Jq9mmezp/r0pC0EqoDILxOUz05qm/c892D8ZZVqvKP\rTQnuHppAyYATGcPBIOHURi4ufCfiEzbaOjK6KLLJMRtGZEuMgTTz77HSvfuGP0/C\r+OVNxvSWcXf26AUhQHXS5wjFo6eLTWsfyi4ZegT9rTOUfwJ/x3hYCnxfGFsofgdh\rbL6jLJkygi+tjQAiJzNmmgRddDpun195Emc9yPYWQT5gz6qwy6ExhAmyfZ6fnIIr\rzWIYcS+oUh+mffeqjBHSUAPfFSlOiWfeshx+XN1oun0SiPaeA9YAb/eiKF+l/0Fl\rwX59Ea2Mr559mRB0Dg9OHMRMqG5K52gYy3V3tXg2/ZZNKeXML0OVbctf+hSkdsT4\rCZwL60LmJPQCBkNr6XOfBA==\r-----END CERTIFICATE-----\r\"\n\t\t},\n\t\t\"local\": {\n\t\t \"eap_id\": \"user_104\"\n\t\t}\n\t }",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
```
- - - - - -
## Account One-time link
**Request Structure:** `https:///api/v1/account//otl`
**Method:** `GET`
**Cookie: `access_hash=`**
**Output:** url
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/account/peer_10/otl
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "https://dev.softkeel.com/otl/941baf43c2fd01e87e98db922c7d4aeb81ed27e1e88d6f3204c99dfae2f622b2433651f031cb461a",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
```
- - - - - -
## Account Firewall mangle rules
**Request Structure:** `https:///api/v1/account//firewall_mangle_rules`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/account/peer_10/firewall_mangle_rules
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "0.0.0.0/0 -> 10.0.105.18 MARK 0x6d Pkt:0 Bytes:0\n10.0.105.18 -> 0.0.0.0/0 MARK 0x6d Pkt:0 Bytes:0\n",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
```
- - - - - -
## Account Traffic Control
**Request Structure:** `https:///api/v1/account//traffic_control`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/account/peer_10/traffic_control
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "ens18 --> class htb 1:109 root leaf cb97: prio 0 rate 20Mbit ceil 20Mbit burst 1600b cburst 1600b \n Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0) \n backlog 0b 0p requeues 0\n\nwg106 --> class htb 1:109 root leaf cb98: prio 0 rate 20Mbit ceil 20Mbit burst 1600b cburst 1600b \n Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0) \n backlog 0b 0p requeues 0\n\n",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
```
- - - - - -
## Account Dump
**Request Structure:** `https:///api/v1/account//dump`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/account/peer_10/dump
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"allowed_ips" : "10.0.105.18/32",
"endpoint" : "(none)",
"keepalive" : "off",
"latest_handshake" : "0",
"transfer_rx" : "0",
"transfer_tx" : "0"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
```
- - - - - -
## Account Traffic statistics
**Request Structure:** `https:///api/v1/account//traffic_statistics//`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/account/ruslan_telefon/traffic_statistics/2022/11
```
**Response example:**
```JSON
{
"error" : "",
"msg" : [
{
"account" : "ruslan_telefon",
"date" : "2022-11-01",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-02",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-03",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-04",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-05",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-06",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-07",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-08",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-09",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-10",
"traffic_download" : 1209108969,
"traffic_upload" : 375698174
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-11",
"traffic_download" : 1588256401,
"traffic_upload" : 406223360
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-12",
"traffic_download" : 1963382022,
"traffic_upload" : 49067202
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-13",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-14",
"traffic_download" : 178929,
"traffic_upload" : 127102
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-15",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-16",
"traffic_download" : 168658637,
"traffic_upload" : 15390640
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-17",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-18",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-19",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-20",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-21",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-22",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-23",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-24",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-25",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-26",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-27",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-28",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-29",
"traffic_download" : 0,
"traffic_upload" : 0
},
{
"account" : "ruslan_telefon",
"date" : "2022-11-30",
"traffic_download" : 0,
"traffic_upload" : 0
}
],
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Account not found
-Wrong month setting
-Wrong year setting
```
- - - - - -
# Firewall
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## Firewall info
**Request Structure:** `https:///api/v1/firewall/info`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X GET https://dev.softkeel.com/api/v1/firewall/info
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"ip_forward" : "yes",
"iproute2" : "5.10.0-4",
"iptables" : "1.8.7-1"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Firewall conf
**Request Structure:** `https:///api/v1/firewall/conf`
**Cookie: `access_hash=`**
**Method:** `GET`
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X GET https://dev.softkeel.com/api/v1/firewall/conf
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"internal_traffic" : false,
"ip_forward" : false,
"policy_forward" : "ACCEPT",
"policy_input" : "ACCEPT",
"policy_output" : "ACCEPT"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Firewall change conf
**Request Structure:** `https:///api/v1/firewall/conf`
**Cookie: `access_hash=`**
**Method:** `PUT`
**PUT data:**
```JSON
"internal_traffic" = false|true
"ip_forward" = false|true
"policy_forward" = "ACCEPT"|"DROP"
"policy_input" = "ACCEPT"|"DROP"
"policy_output" = "ACCEPT"|"DROP"
```
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-d "ip_forward=1&internal_traffic=1&policy_forward=ACCEPT&policy_input=ACCEPT&policy_output=ACCEPT" \
-X PUT https://dev.softkeel.com/api/v1/firewall/conf
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "success",
"status" : "success"
}
```
**Errors:**
```
-Wrong parameter: INPUT policy, should be: ACCEPT or DROP
-Wrong parameter: FORWARD policy, should be: ACCEPT or DROP
-Wrong parameter: OUTPUT policy, should be: ACCEPT or DROP
```
- - - - - -
## Firewall rules FILTER
**Request Structure:** `https:///api/v1/firewall/rules/filter`
**Cookie: `access_hash=`**
**Method:** `GET`
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X GET https://dev.softkeel.com/api/v1/firewall/rules/filter
```
**Response example:**
```JSON
{
"error" : "",
"msg" : [
{
"action" : "ACCEPT",
"chain" : "INPUT",
"d_ip" : "0.0.0.0/0",
"d_port" : "8098",
"name" : "system_PUQVPNCP",
"protocol" : "TCP",
"s_ip" : "0.0.0.0/0",
"s_port" : "0"
},
{
"action" : "DROP",
"chain" : "INPUT",
"d_ip" : "0.0.0.0/0",
"d_port" : "23",
"name" : "TEST",
"protocol" : "TCP",
"s_ip" : "0.0.0.0/0",
"s_port" : "0"
}
],
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Firewall FILTER add rule
**If add at the top of the list**
**Request Structure:** `https:///api/v1/firewall/rules/filter/top`
**If added at the end of the list**
**Request Structure:** `https:///api/v1/firewall/rules/filter/end`
**Cookie: `access_hash=`**
**Method:** `POST`
**POST data:**
```JSON
"name" = "NAME"
"action" = "ACCEPT"|"DROP"
"chain" = "INPUT"|
"d_ip" = "CIDR format"
"d_port" = "0-65535"
"protocol" = "TCP"|"UDP"|"ICMP"|"ANY"
"s_ip" = "CIDR format"
"s_port" = "0-65535"
```
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-d "action=ACCEPT&\
chain=INPUT&\
d_ip=0.0.0.0/0&\
d_port=22&\
name=TEST_SSH_OPEN&\
protocol=TCP&\
s_ip=0.0.0.0/0&\
s_port=0"\
-X POST https://dev.softkeel.com/api/v1/firewall/rules/filter/top
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "success",
"status" : "success"
}
```
**Errors:**
```
-Wrong rule name. Must be letters and numbers only
-A rule with the same name already exists
-Not correct Chain
-Destination IP must be in CIDR format
-Source IP must be in CIDR format
```
- - - - - -
## Firewall FILTER delete rule
**If add at the top of the list**
**Request Structure:** `https:///api/v1/firewall/rules/filter/`
**Cookie: `access_hash=`**
**Method:** `DELETE`
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X DELETE https://dev.softkeel.com/api/v1/firewall/rules/filter/TEST_SSH_OPEN
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "success",
"status" : "success"
}
```
**Errors:**
```
-No rule found with given name
-You cannot delete this rule. ONLY name=system_PUQVPNCP
```
- - - - - -
## Firewall rules NAT
**Request Structure:** `https:///api/v1/firewall/rules/nat`
**Cookie: `access_hash=`**
**Method:** `GET`
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X GET https://dev.softkeel.com/api/v1/firewall/rules/nat
```
**Response example:**
```JSON
{
"error" : "",
"msg" : [
{
"action" : "SNAT",
"chain" : "POSTROUTING",
"d_ip" : "0.0.0.0/0",
"name" : "Default_144_wg144",
"s_ip" : "10.0.143.0/24",
"to-source" : "77.87.125.200"
},
{
"action" : "SNAT",
"chain" : "POSTROUTING",
"d_ip" : "0.0.0.0/0",
"name" : "Default_153_wg153",
"s_ip" : "10.0.152.0/24",
"to-source" : "77.87.125.200"
},
{
"action" : "SNAT",
"chain" : "POSTROUTING",
"d_ip" : "0.0.0.0/0",
"name" : "Default_44_wg44",
"s_ip" : "10.0.43.0/24",
"to-source" : "77.87.125.200"
},
{
"action" : "SNAT",
"chain" : "POSTROUTING",
"d_ip" : "0.0.0.0/0",
"name" : "Default_53_wg53",
"s_ip" : "10.0.52.0/24",
"to-source" : "77.87.125.200"
}
],
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Firewall rules MANGLE
**Request Structure:** `https:///api/v1/firewall/rules/mangle`
**Cookie: `access_hash=`**
**Method:** `GET`
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X GET https://dev.softkeel.com/api/v1/firewall/rules/mangle
```
**Response example:**
```JSON
{
"error" : "",
"msg" : [
{
"action" : "MARK",
"chain" : "FORWARD",
"d_ip" : "0.0.0.0/0",
"name" : "src_peer_121_user_122",
"s_ip" : "10.0.118.3",
"set-mark" : "227"
},
{
"action" : "MARK",
"chain" : "FORWARD",
"d_ip" : "10.0.118.4",
"name" : "dst_peer_122_user_123",
"s_ip" : "0.0.0.0/0",
"set-mark" : "228"
},
{
"action" : "MARK",
"chain" : "FORWARD",
"d_ip" : "0.0.0.0/0",
"name" : "src_peer_122_user_123",
"s_ip" : "10.0.118.4",
"set-mark" : "228"
}
],
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
# License
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## License status
**Request Structure:** `https:///api/v1/license`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/license
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"accounts" : 500,
"expiration_date" : "2023-11-13T18:38:43+01:00",
"key" : "I77REA-CJ5CCX-DK33DO-USODFR-H9IR8Y",
"last_check" : "2022-11-16T11:11:36+01:00",
"valid" : true
},
"status" : "success"
}
```
**Errors:**
```
-The license is not active
-Not authorized
```
# DNS
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## DNS status
**Request Structure:** `https:///api/v1/dns`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-X GET https://dev.softkeel.com/api/v1/dns
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"acl" : [
"127.0.0.1",
"10.0.110.0/24",
"10.0.107.0/24",
"10.0.176.0/24",
"10.0.44.0/24",
"10.0.68.0/24",
"10.0.111.0/24",
"10.0.15.0/24",
"10.0.1.0/24",
"10.0.52.0/24",
"10.0.85.0/24"
],
"bind9" : "1:9.16.33-1~deb11u1",
"enabled" : true,
"forwarders_1" : "77.87.125.10",
"forwarders_2" : "77.87.125.20",
"max_cache_ttl" : "3600",
"pid" : "2649459"
},
"status" : "success"
}
```
**Errors:**
```
-The license is not active
-Not authorized
```
- - - - - -
## DNS EDIT
**Request Structure:** `https:///api/v1/dns`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Options not required:**
```JSON
"enabled" = false|true
"forwarders_1" = "CIDR format"
"forwarders_2" = "CIDR format"
"max_cache_ttl" = "30-3600"
```
**Example:**
```shell
curl \
-b "access_hash=eda121857897bcf0e4cdf5a3eaf957f35ccb62d39d5bc0bfbfb6d31644eee3cd7f8365e71ad94a60" \
-d "enabled=false&\
forwarders_1=1.1.1.1&\
forwarders_2=8.8.8.8&\
max_cache_ttl=300" \
-X PUT https://dev.softkeel.com/api/v1/dns
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"address" : "10.0.127.1/24",
"b_download" : "6",
"b_upload" : "7",
"dns_1" : "8.8.8.8",
"dns_2" : "1.1.1.1",
"external_ip" : "77.87.125.200",
"interface_name" : "wg128",
"internal_traffic" : false,
"listen_port" : "51333",
"name" : "Default_128",
"private_key" : "cAnS3fQbdvHUS+9eV05Uf+cP+gn8i4LpzXsdE7mUZ2E=",
"public_key" : "RVNBbsEIjEkgsyXzmd5vMBIcOzzcTSC/fPscdDwzlQo="
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Incorrect data in Forwarder1 parameters
-Incorrect data in Forwarder2 parameters
```
# System Config
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## System Config
**Request Structure:** `https:///api/v1/system/config`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/system/config
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"traffic_statistics_frequency" : 1,
"traffic_statistics_history" : 1,
"wireguard_handshake_uptime" : 180
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## System Config EDIT
**Request Structure:** `https:///api/v1/system/config`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Options not required:**
```JSON
"traffic_statistics_frequency" = "1-1440"
"traffic_statistics_history" = "0-2147483647"
"wireguard_handshake_uptime" = "1-300"
```
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-d "traffic_statistics_frequency=10&\
traffic_statistics_history=5&\
wireguard_handshake_uptime=300" \
-X PUT https://dev.softkeel.com/api/v1/system/config
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"traffic_statistics_frequency" : 10,
"traffic_statistics_history" : 5,
"wireguard_handshake_uptime" : 300
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Incorrect value Traffic Statistics Frequency (should be 1 to 2147483647)
-Incorrect value Traffic Statistics History (should be 0 to 2147483647)
-Incorrect value Wireguard Handshake Uptime (should be 1 to 300)
```
- - - - - -
## System Config Set Default
**Request Structure:** `https:///api/v1/system/config/default`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Options not required:**
```JSON
```
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X PUT https://dev.softkeel.com/api/v1/system/config/default
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"traffic_statistics_frequency" : 5,
"traffic_statistics_history" : 2,
"wireguard_handshake_uptime" : 180
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
# IKEv2
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## IKEv2 info
**Request Structure:** `https:///api/v1/ikev2/info`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/ikev2/info
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"pid_charon" : "1473837",
"pid_starter" : "1473836",
"strongswan" : "5.9.1-1+deb11u3"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## IKEv2 Config
**Request Structure:** `https:///api/v1/ikev2/config`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/ikev2/config
```
**Response example{Server configuration example}:**
```JSON
{
"error" : "",
"msg" : {
"ca_cert" : "-----BEGIN CERTIFICATE-----\nMIIFfDCCA2SgAwIBAgIIMYZL3xAvgfwwDQYJKoZIhvcNAQEMBQAwXDEQMA4GA1UE\nAxMHUFVRIFZQTjEXMBUGA1UEChMOUFVRIHNwLiB6IG8uby4xEDAOBgNVBAsTB1BV\nUSBWUE4xEDAOBgNVBAcTB1dhcnN6YXcxCzAJBgNVBAYTAlBMMB4XDTIyMTIwNTEx\nMzIzOFoXDTMyMTIwMjExMzIzOFowXDEQMA4GA1UEAxMHUFVRIFZQTjEXMBUGA1UE\nChMOUFVRIHNwLiB6IG8uby4xEDAOBgNVBAsTB1BVUSBWUE4xEDAOBgNVBAcTB1dh\ncnN6YXcxCzAJBgNVBAYTAlBMMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKC\nAgEA1nYVzVwZxckXMsCeR3AnoPgvRHubvIslIPvp4lCFnSXZJhTXC5mmicZauPm1\nL0mpclc9umNOM1LxSHV4pcFYP+M1bDUYMef3iaufeQO3cU4R4UrJLsCC/WGwvw1o\nIqYDCxUtB0ePxZHNsBXDxu2/F0eVjX5SiPnCDxyY/tKsouJnX+bTGB5r0byeon6h\nA7V9mVrKJfKrIXhzKPtle28nFa9c6aRu+ROq3KotcradPSdzzzzFhCSCXChbI7+y\ndfnSiJ3rARREHljMpv0rWM/9NyCPHUIJaR+XJ8JQMDdQxMP8oN0fKB8y66foLiFD\noXWLvtGIFPkEnHbX2T7N//ly5xkA97upoQvo7wxtWV4xOIe1nfLesSZVCl/UL50d\n+LVf6NbguDda2HE15AuX6MjnOtX18Yn6VQNUo8R5rr+3dpuZnUYVzfdbnaVmmSuc\nISsQEUTZMzwTzCffpUwPzp8MMWB2K1pSOMTtC7o7cEjnv2BV8IuKhgK1V66lRapx\ncCWF/L1bHRasaqr5JCebGIVZNsd2qYJyuD6p0xP+VVo3PoboqusASKvbQ9PcoMdx\nm8GJHzNnJsuUQhapP2PpDpdht58p0xstWyPnANDsfbqooFWpwAJWhHlkl7JhQWuY\nepEWKs78B3C2LYT6UeU4nJmRYNmsuclOUj9HpSJEMZ/nPnECAwEAAaNCMEAwDwYD\nVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8EBAMCAQYwHQYDVR0OBBYEFFbCzI+j1Md8\nNjG1pCPq+ksO0MhgMA0GCSqGSIb3DQEBDAUAA4ICAQBpmyQRfUF/BiuF76vEcwci\nOuuiBaoPcEOwQIueje84KtaEwA0a+QKX4sPGHE4Eoxv7JHEJhBfoeKABTgpIv+qF\nnWdEO+sMTowLhrcoB1VPTw50w3mOYDLG+aqcC3e7UrXoMx+MWmPM3u3/zUkp5j/f\nAsIZL4YdXBtwqmmoj13zg6URslhXhlPeqw+OiqevfpPZE1a1IgXTEY0Xnba1B5o6\neRUCLcUO4dYjv3Eg55WKKN4uPkmm0u1JiWZp8g13FBK1hss/g1qkh3ZW5nMVDjTP\nGFGrY+eHLzEgM8RRieJpU+Jq9mmezp/r0pC0EqoDILxOUz05qm/c892D8ZZVqvKP\nTQnuHppAyYATGcPBIOHURi4ufCfiEzbaOjK6KLLJMRtGZEuMgTTz77HSvfuGP0/C\n+OVNxvSWcXf26AUhQHXS5wjFo6eLTWsfyi4ZegT9rTOUfwJ/x3hYCnxfGFsofgdh\nbL6jLJkygi+tjQAiJzNmmgRddDpun195Emc9yPYWQT5gz6qwy6ExhAmyfZ6fnIIr\nzWIYcS+oUh+mffeqjBHSUAPfFSlOiWfeshx+XN1oun0SiPaeA9YAb/eiKF+l/0Fl\nwX59Ea2Mr559mRB0Dg9OHMRMqG5K52gYy3V3tXg2/ZZNKeXML0OVbctf+hSkdsT4\nCZwL60LmJPQCBkNr6XOfBA==\n-----END CERTIFICATE-----\n",
"ca_common_name" : "dev.softkeel.com",
"ca_country_name" : "",
"ca_key" : "-----BEGIN RSA PRIVATE KEY-----\nMIIJJwIBAAKCAgEA1nYVzVwZxckXMsCeR3AnoPgvRHubvIslIPvp4lCFnSXZJhTX\nC5mmicZauPm1L0mpclc9umNOM1LxSHV4pcFYP+M1bDUYMef3iaufeQO3cU4R4UrJ\nLsCC/WGwvw1oIqYDCxUtB0ePxZHNsBXDxu2/F0eVjX5SiPnCDxyY/tKsouJnX+bT\nGB5r0byeon6hA7V9mVrKJfKrIXhzKPtle28nFa9c6aRu+ROq3KotcradPSdzzzzF\nhCSCXChbI7+ydfnSiJ3rARREHljMpv0rWM/9NyCPHUIJaR+XJ8JQMDdQxMP8oN0f\nKB8y66foLiFDoXWLvtGIFPkEnHbX2T7N//ly5xkA97upoQvo7wxtWV4xOIe1nfLe\nsSZVCl/UL50d+LVf6NbguDda2HE15AuX6MjnOtX18Yn6VQNUo8R5rr+3dpuZnUYV\nzfdbnaVmmSucISsQEUTZMzwTzCffpUwPzp8MMWB2K1pSOMTtC7o7cEjnv2BV8IuK\nhgK1V66lRapxcCWF/L1bHRasaqr5JCebGIVZNsd2qYJyuD6p0xP+VVo3PoboqusA\nSKvbQ9PcoMdxm8GJHzNnJsuUQhapP2PpDpdht58p0xstWyPnANDsfbqooFWpwAJW\nhHlkl7JhQWuYepEWKs78B3C2LYT6UeU4nJmRYNmsuclOUj9HpSJEMZ/nPnECAwEA\nAQKCAgA806lDYcf9jReDUZaS9ICI61uctOJrC5wwSsL/aY88DywT3P1RUPcnRJce\nt9Rn4SCqSYw8fUYE0JWW05qwiLIbDLpuQnDmVsCiz4afsCorfNUdbTS6ieedLkQP\nLCJJEYTzc8IdunJQuxX3x3SLy4rTc347b4TBTPV5i8bpH5/PYx+m17UvthEmn7Tu\nqbPJdYR2JoYHVVisWZlwGj2iUNhpEh/sNLM0+hsQE0RosNrQKYxzTu1GmYRP1zJi\nZVCcnYrVLNUmrTTU1qLVCiFtQzCyng15Yu2AX3Fj2X0c79N8u4m/pnfbzV2H8Uut\nKcog1VIZgRxztl1Uc3CtMV8EJyArXrVEJwXdgMo19H4LvZxK0/rlxyz8Y/zggUSy\n/PsO5YIHDR1VsRe/Q+Gd4+ttJKMZ/E+ghIQ6mTjamZwGOiH4rji5jg21pFSBZqwm\nLp7wpeTCYkFGAXbiNYVJw4PNoWOoPGlCdaNGiP2NEk4EPI6ieo+sFFZYBaPzrGw/\nStOYlKMrkGTcH7kGhYxFsIYtPp9t5La34msoqbCqPaxNP5rT3jeLcIkKulE0/Xao\nehAhXYVm+iDn1Y2iIzVyOouEd9i1XYTEJpO/aA7QdEqyR7003Y6jHMdjekEfH9AA\nWFOGKedHfzML6uQQMuDzhVGTEMtJAEKXXOaIT+G7UZh88rrvAQKCAQEA8bKB/jL3\no451NTJj+U/YZNRrfKysuDkBPnYIHuCWhWhmjJCOcF0txHhMhv6+KAGI4PU1Of0Q\niPQSaczP2LKgN6Dz8aJDqDonJ67sUzP+y+tNGpabOvydp8PH7KWpixAVt7bqI8K4\nCOymbR1hW6HHyujUlHM9s04zE1HI6ABTcsPbpTVh1lcl91TD42t2bSVfncdZqDKp\nO0iaFSuk6gpIvYMesSpsUCJrAF4mO5uPTwSRVQxg4tBj8OLsdWIuVlow0ZNXgcGd\n76XMzMmHit0FNN8zsDfoEg/GgLkoyY+2kmU5yahyvo2lBMLs/lpWQ5xp10PpnU4d\n3KWEynuNBxjQ+QKCAQEA4yb6AWp60hLgi4mfdaCHhXc8dZs+bP2CaE5lK4XFx/IM\nIrLYNjJFpWbNQ5Mlq2p6tedF3lRuU2/GXwvY0BlY1t5G2NdPqn6KOXDDcuq0u4JN\n2MmrTYrRjye4AtfP1qcVNnilU1kus+b4nK3Ob9m629sWEg0kHeDDF/Bw0WLoQAK/\nCpbuzo7OR4S1zx+F0p2MvDbErmmNtPgrFKiPjRixysgwnH5jnIIK667gHvinD23Z\nu6ZiOAS2Tm+0KhwELlaCCOPAB32dpAAUoKgv8RxbytvWQjgrOkKQSTEZ5T64BVZM\n4ClIz6+8IlQQCHUouF59w5z86VEPHJYu1zU+eNsvOQKCAQA91BlW6rjYuS+YjSxv\n8ZH8sS5R9WY1tjdwQAdxxqgatotNOAmICv4TPWbuPaptV38pdPDJxcf+ENnJAODG\noWNE98KPtJ+0IDQ1/ZRs8GckySuvOom5PDgkW3wAOJy3e0Ti+0LIJR6pAcjNLu/h\n3e/bI1aGJzjIbp+4OHq5hqPSPvIoQBCoISEQNTnrKmlgIGhmV0HDOjp6dOcdtU15\npWnYOPuX/K86jKNss6j6JKAzaYq4A/Og8ggu7g3pNVV/N5E3e4auJdZ+IJ7UYFVx\nG3sifFqfoJ2YSTrRYQxjC4V7y7NNt+6qeleVcTvpETjyEMgujivr1rji4eCnX5XD\nFAEZAoIBAAO1aTOIt4SihkQA9TeIbW4CalxJMpW49d4aGZDCWF5RV11hqiIIZBa1\nPPizeFP6IxLBOeTNYBfApW571QhgwZCQhHuZ2FUiR8N0UdyYdGbzU64MbN2RPKan\nsVtqhpwski4XfiuEMz0AsmJsfAhbd6+LPisBR+us9cJ4TH8+rCgPY2sa179LmZaV\nVhqRmy+7Hscb5c4rLwMbYiiuL9nP42c6KYEElz/A58i9TC91Q9T+qCVmLAhaG1fg\nfwKI/pB7HRhkD4iPxnkc/zk4RcAcBGuldzQRkrMazxxCzvdtNLfxlsO6KNQrPFkb\nIj/hGc8Yy9jbwU1V43dGBHHDDsgOXBECggEAN5TJ4PFR8PRE4/YlwDRWwXlEnFFr\nTRfkfvWyeDRnaQsSB9NqgF+IG0ymiGYrcmu4Ej2Ix3U0VuL+yjI4j+jxBdW+hs2H\n9z9AwVJVdPuz9XlLC/odQTEbdLtynQCrqxm3QtJKLMBQ3hyRdY95+Yd1VnJnTCnT\nSDM5UJiDEc+Xxx0/Z7Akn8s0U30RUdA989Pmb25p5CKcrF9/Juk/5bgf0z6cDz8G\nbGKG2DwJ/O9RVdOBLJWKli66LexRjMpBhksf6aAb5bImfGFJ0ki9amX3gN+TSotS\n0BRSu+9CGRwt+SPONcxcXqs6OTYu+WkAv3V23+ON8aiNli7qKJVyYvNzQQ==\n-----END RSA PRIVATE KEY-----\n",
"ca_locality" : "",
"ca_organization" : "dev.softkeel.com",
"ca_organizational_unit" : "",
"ca_state_or_province_name" : "",
"enabled" : true,
"server_cert" : "-----BEGIN CERTIFICATE-----\nMIIFnTCCA4WgAwIBAgIIZqs60I6InzAwDQYJKoZIhvcNAQEMBQAwXDEQMA4GA1UE\nAxMHUFVRIFZQTjEXMBUGA1UEChMOUFVRIHNwLiB6IG8uby4xEDAOBgNVBAsTB1BV\nUSBWUE4xEDAOBgNVBAcTB1dhcnN6YXcxCzAJBgNVBAYTAlBMMB4XDTIyMTIxMTEw\nMzQyM1oXDTI3MTIxMDEwMzQyM1owUTEZMBcGA1UEAxMQZGV2LnNvZnRrZWVsLmNv\nbTEZMBcGA1UEChMQZGV2LnNvZnRrZWVsLmNvbTEZMBcGA1UECxMQZGV2LnNvZnRr\nZWVsLmNvbTCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBANt/3Wdzsk88\ntLzJ4cw7plofxOgtXKkF01/j41MVtUNjysq4QhxvwXO96336npPYisPzZan7pIaq\nGN8EDcQ3tiQvCTOPu/JeoNTtEgUdy5/MXSGfl6981MxG0+njtE9+4WEg7D0wTgs2\nKuyVv1G/hpbz+XnkyPEYAXLVJXcwdFODZZkAuDk84olNr0QT/AeLKHf0QThTQipZ\nnDIn0OQs1zKULaw/kVs3owhAConAi8Vra5In63K0UBHetdL8eB/YgiGx/ZIcmQtf\nAWLEaUv0kRpv5iWoqqmtpODNVrZRxS/HN3lZWJZwO3DZfFtViADFS8xQ+jwPq2/R\nh6cs+OD3J7lSViJuKXEDyfvSzSf7dNrQQsjtAlkMqQVi134mEabhd6pZ2wNjPqvf\njOZge/ssYqmB+esIJsO3CmcVxop7aUzLx9HaAFNj1dyc2mFeIBovUqSaQLN103fY\n5axEJutRRFbRUNf55w71gPEKcSdkYfDAkG6pZn4+TD/Q28piMj+N8iLwsKWm3kgl\nzh9dhEPhaPhZL6nPy1p7t4YEr+07XumMzp6v5KcACSj7a8Jb+X+I9RjJ9NttvWo8\nPaR8of5dJ1d2AaQAPfqtXP3uq01cwpxwuAjVLkEAURFMIoznOTxleMucvV7FSgIn\nCbx5DbLGNGbPzGPPKGwpKWGbWw5qwErzAgMBAAGjbjBsMB8GA1UdIwQYMBaAFFbC\nzI+j1Md8NjG1pCPq+ksO0MhgMCoGA1UdEQQjMCGCEGRldi5zb2Z0a2VlbC5jb22C\nDTc3Ljg3LjEyNS4yMDAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFCAICMA0G\nCSqGSIb3DQEBDAUAA4ICAQDOKUmPnSZcW0oj49WstpGzumNxQz25k6qqyPK3tuAm\n8DCVm+6vjVuApEdeVu+JlHOwJu1TdMiIUcHWRpF/gmgRewc27ZD86zWAVTjGOCuV\ne8aHP3CYIQzs5SHvfE389xKpsGV+5CPB93fxJ5jxGthbJ7wI1XZXTTmC66s0fE5F\nDVIi0e/d3vc5IWP9BLPOlWWUmDgmZi0Zosk1Lr3+1WQ4w+EIcSZ1jRc4/LmwoEXk\nr/Do/pP6oKkZ/zcuYFWGWzupUTc1nfU4pWOK2gxeleMO6YRL3EtM1LvMIdXgvZaO\nQ+HZ89P/4Ttt3r2XpgRcyddjv1iUbjyTuhmkX6xrF7n3p4740VwvdJ1bIaJOdVhc\n10Ii5vBaoLbQt7T3722UoMdKGTTpbC+fSA5hH1NrSwePgSG0f0stdKTVmQ4MXIK4\nYld92SMscQ4c/w/3s8+M3wGMOg2oXvjS7Z+FKvL+C51lQLIPDutEI3EQx/C4Zwtm\n6QvWYd2Cq7CsQ/E7ahr6NI8r9i08nSMZUqCQEj7glnTuPuwnl4wAgZ8X2Msdgv3F\n3tLhxVQLBgubtYK89/WskPEKKFZk/vhjz6yuFGwXW23NeRsFTRc446F4V08OZSEl\nA+mdfigBVsM1L8kdpuvIWH0rA52mhSou2odtcL2xlhLsYVhHl6mNMjo31J5uobHr\nPQ==\n-----END CERTIFICATE-----\n",
"server_key" : "-----BEGIN RSA PRIVATE KEY-----\nMIIJJwIBAAKCAgEA23/dZ3OyTzy0vMnhzDumWh/E6C1cqQXTX+PjUxW1Q2PKyrhC\nHG/Bc73rffqek9iKw/NlqfukhqoY3wQNxDe2JC8JM4+78l6g1O0SBR3Ln8xdIZ+X\nr3zUzEbT6eO0T37hYSDsPTBOCzYq7JW/Ub+GlvP5eeTI8RgBctUldzB0U4NlmQC4\nOTziiU2vRBP8B4sod/RBOFNCKlmcMifQ5CzXMpQtrD+RWzejCEAKicCLxWtrkifr\ncrRQEd610vx4H9iCIbH9khyZC18BYsRpS/SRGm/mJaiqqa2k4M1WtlHFL8c3eVlY\nlnA7cNl8W1WIAMVLzFD6PA+rb9GHpyz44PcnuVJWIm4pcQPJ+9LNJ/t02tBCyO0C\nWQypBWLXfiYRpuF3qlnbA2M+q9+M5mB7+yxiqYH56wgmw7cKZxXGintpTMvH0doA\nU2PV3JzaYV4gGi9SpJpAs3XTd9jlrEQm61FEVtFQ1/nnDvWA8QpxJ2Rh8MCQbqlm\nfj5MP9DbymIyP43yIvCwpabeSCXOH12EQ+Fo+Fkvqc/LWnu3hgSv7Tte6YzOnq/k\npwAJKPtrwlv5f4j1GMn02229ajw9pHyh/l0nV3YBpAA9+q1c/e6rTVzCnHC4CNUu\nQQBREUwijOc5PGV4y5y9XsVKAicJvHkNssY0Zs/MY88obCkpYZtbDmrASvMCAwEA\nAQKCAgBLMMf1Ukq4ngED0txIi/52TP+00SU2uUopRPVwVrVbOmoTe38aIqZQMbTj\n2OBNoRYX/d7LlepMPyR58PeOSc9ZIcuzH/+wDP5nMjbEDerc+LLGe9cIRGjY+UJK\nkrgHq10lWpPSeiOh75JQrRN2u3ctarIBMYAsJp8IaT+GTtDqcs5w1TBGWzb29eee\nGIJzSxY30TIuS0cVHtFE1SLXpwyoxN3IbZYreymb/+QcQBshK6UT0hzzlBUBqhr7\nBYVY01/wjvpf/O/oV0kwPjwbytGSDtb1+4tKyLL8VxrnJae4sDOunA6eqh+Sjs3s\ns6X9LZjDitHNlUiS62HewKcY2VF/pby+IhOQCqQf55uDDpCyfWmy2OZ979gb6rcf\nhm/T/nt44v0mh2UHOe4RoDZQwXeOPCCGb2009Kb7q8YZfiEf+h6xPXL2sBxcqMet\n8P39GxeJgDRy7+e0024UYNsNMC5IeW/mT9H6dkaY7EeM/Da4mTl31r6Rfgp3CGi9\nN1o8jU6Uwk9Z0jqRlnHaVS2Gb3lojggwxOm4qN2eBBTAnHrqVFAlj0IlbU1gtZjm\nwrTuqDs4K5F8jjeOiU78iCwPTVCk6b8JWspjXAoVlTzb7WYajbRjVWWjBCJQIxp4\nFBQWJy0hgNaSj5g99fAc/evIsX/8ssla4d5+5zcE42rHVRPhsQKCAQEA+PlPEsPr\nYnQY5vkGoz/chc8PmMYZ4VrOjxM2Yl9x/4UQUMM56GPxGVFexgQdxl9wzD4hKdyA\nGkVLgfPiz5Qnj/vVqOZfZuP1U6joAeboKCg/0KoOnC+URI0Zs3gnv63jarGkf8AG\nCURHxIq3RUFtO7jvY5F8lfept/lEI0fJaTO11tqGMTeCLo5vz165SPUW8GO0GQ7s\nbGjgFzN9wEPOLqEcsghgngXs7olJcKRZfL7Xl5e9dBE5i8PGr+4LXewcG8SAmYbf\nuPdA2vMpIz3fGxZ3oz69bqwH8Exrn7yP5ZFytJgS63pDATxS+TiqDr6npP8eZm7Q\nrhI8N+ITVtBZtwKCAQEA4bGe5LGOf+B5Q1Hr//j0jSKlEf2iU6wKsBAnaEvNOYea\nHxm7JsAEMxJqRXhVLefbgSI6Tbm2vWgII0ytO7ufwd32t3kwu0vvBuoa6XaWtIgB\nrKu0Mdjtjj8TzCUgt9b8JnazN9Qhhx/1EiuScpnm7pIbxEm54R5Rauvm65xll2aT\nZ73Dq1U4ZV0Y0S0A4UwsrSN1TVfEoCV+4wg0/dwEABLk9GYzAPxY0hg4+ZzhqU19\nWcEHoOjSyUWYqSQpcU8MQM95LW3N6QvXOIAvPLYGP4tANmrYaSYAsvMI6ns2Kp3V\nxXTfxSmnZ4GdyyzUv9hKTJmeaGmvfDV0UOOo6J1IpQKCAQBdEEunVwZ4Qa9BPtpl\nUSyr867/yyTHYLsPLf5JHSYufd2QYrkVja4Eaa8EU2uRyAEQxzR8Qki8CSTlSXWB\nY/65ykeeH6aPfiwofl1iwJ4MzKa156sYZIyGZzuxIvuwoV39drNncS6Qbi5pX/SL\ndZ5QEZuh2zL3l6Cf/ROkIGQ/561Tx1EbuoT1xBY1LFIT3FEbwBkEuNhU2YrSAVRC\n9tVuBpkETy9WQh7DNxv1d+lfQLKznmuZpAqfnKl6/37ON8B1/KiZOpoLuJhMf1Hk\nM29e37IOmhgS80jwYJBmIASlqg13RdTkoknDf3oAYFbotglSGm6RmWB1gKlzthTG\ngZDXAoIBAGK3JvGOe+6Qx1lbpqbiREzK/3pb/rksQcx6dFIY/Z2RIydBQOuVBwEz\np8nU9STMCeV0jB3dAgHcU9rkucyrpxfLtxLO7jKt5tGWacj9trMl3d2hiIJZCKa0\nDju3bZUbclR8jKz5muSYZL/a0QZRLIHi5EQ5nxTJBwGGRw187a6IDidNCB2Te8RS\nMP2k+oKQp+Xe4Xq/zd/iJpq0x0DWD+XcXcpMPTjMJylVsO304XsEyrQMSwLlcvTX\n/QrWJ05JLenXFYB6S5sIM82hu4eJcjgu9xoWJ6vuFFYxGRA+bhW7zXm9Qfbh3jfW\nqKbqZ++1ceIJOxEeUMQ6OTL8MK/1w4UCggEAUVYosvgQYko61OoBWRG/5bEmCvk8\nH1gN15CKa9cnoO8IQ0Bs5nmgo6sVj8z+gDa05Qfrj8hisp11t7K7ysWWVWI57h7H\nCuUefF8ojw7lRAuXnIhofx4gTuq/cqjJfwoScNKpjOjZPnnfGB20vKHnQ9+l1KTw\ndj3RQVtbaBEd8z1K+xzDHXV8C2UJRaOEE9lVWDHNB/+adg6s0VUJGIlsi2CzglwS\nc86vSnay1J/XJDEI+e0kf86Kub5yybsVjpQUJYJPA7q825utfJVcl0HG5LNdiYeX\n5VhMA0neypCR0Ojfil7Zx5AcPKVfdrMvqa7CGHL1UKOR7sCV/lrcsPtLtg==\n-----END RSA PRIVATE KEY-----\n",
"server_common_name" : "dev.softkeel.com",
"server_country_name" : "",
"server_domain" : "dev.softkeel.com",
"server_ip" : "77.87.125.200",
"server_locality" : "",
"server_organization" : "dev.softkeel.com",
"server_organizational_unit" : "",
"server_state_or_province_name" : ""
},
"status" : "success"
}
```
**Response example{Example of not configuring server}:**
```JSON
{
"error" : "",
"msg" : {
"ca_cert" : "",
"ca_common_name" : "dev.softkeel.com",
"ca_country_name" : "",
"ca_key" : "",
"ca_locality" : "",
"ca_organization" : "dev.softkeel.com",
"ca_organizational_unit" : "",
"ca_state_or_province_name" : "",
"enabled" : false,
"server_cert" : "",
"server_common_name" : "dev.softkeel.com",
"server_country_name" : "",
"server_domain" : "dev.softkeel.com",
"server_ip" : "77.87.125.200",
"server_key" : "",
"server_locality" : "",
"server_organization" : "dev.softkeel.com",
"server_organizational_unit" : "",
"server_state_or_province_name" : ""
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## IKEv2 Import CA certificate and key
**Request Structure:** `https:///api/v1/ikev2/import_ca_rsa`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Options required:**
```JSON
"ca_cert" = ""
"ca_key" = ""
```
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-d "ca_cert=$(sed 's,+,%2B,g' </api/v1/ikev2/generate_ca_rsa`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Options required:**
```JSON
"ca_common_name" = ""
"ca_organization" = ""
```
**Options not required:**
```JSON
"ca_country_name" = ""
"ca_locality" = ""
"ca_organization" = ""
"ca_organizational_unit" = ""
"ca_state_or_province_name" = ""
```
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-d "ca_common_name=TEST_CN&\
ca_country_name=TEST_C&\
ca_locality=TEST_L&\
ca_organization=TEST_O&\
ca_organizational_unit=TEST_OU&\
ca_state_or_province_name=TEST_S&\
" \
-X PUT https://dev.softkeel.com/api/v1/ikev2/generate_ca_rsa
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"ca_cert" : "-----BEGIN CERTIFICATE-----\nMIIFlDCCA3ygAwIBAgIIP9dfvYShrW8wDQYJKoZIhvcNAQEMBQAwaDEQMA4GA1UE\nAwwHVEVTVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8w\nDQYDVQQHDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9D\nMB4XDTIyMTIxMTE1MzgwM1oXDTMyMTIwODE1MzgwM1owaDEQMA4GA1UEAwwHVEVT\nVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8wDQYDVQQH\nDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9DMIICIjAN\nBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA4dJvCvJ+4CDpYMVzEtWLyOpKLeeg\ns3yCWjKwHQubGXiTl9KsQLlrWTXYyFO3FhqygEZ3V0LUgBm4fWE+668dFa2b3qpp\nxmPJdw1TmnIwadQBZfJh9/Ve/fsnk6ktZKS03lgW0qKvwjCi02hTwNwzrrGUrueY\nO0dK1sKzGJdSD4hZQUQ7/8OnfQy7gsyVZbipXs9OOWQBdpbMhTDH/5xGVH0UmZyW\n0hYyb5pQVsayQQYC8FixltHwACohqoGDfNQVEYu8sg0bnHUf8n/+lH8Kuw01xZie\nIvpF0RoGWJIlwOCX4BHbYkHs/yygzbQFQ/F31ONHLGgrx282AemDaGKNlJKlghQi\nmBwW6Qwp3NJAgBXcV1iViyyagRmsFKP3Raya+KaG0RVjFQWoLJ71Bxv6LoVWIAfH\nMnAWRLuFrXcGA3zJrKKpDwEi3zBfFkiRNdj97BHKHcLKmkcmGwn9w4RaJtFoAuhO\nQAAjcEwSAjyhhQTGW/VjW0FqctmnHMFT1jldDlqy4i92QUrvmrdH+Lk8LE1MaZhh\nYWwwH6eDGHYBpE2056Yxn1if6/wvgcii3yC5kA/vg56BNkBwnTR3in74oYdXGbLO\nkOOqXI0/mSAWYN+bk3PQ7Gb5IlpMK6s0gyj3fixepzAtzm5+FttFib5pNoK1QILR\nLn54cO7TPprNg48CAwEAAaNCMEAwDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8E\nBAMCAQYwHQYDVR0OBBYEFCGwbrB4NeaArXVbUE5B83SF1G8ZMA0GCSqGSIb3DQEB\nDAUAA4ICAQDE0kq0gV0Bj4w6JkjgYGnQrNSWRL1PuC4sI2DYWykP6ALYD+lxEv0X\nOV+zhIqrnDUzBXvqHLFwmyiwH+qIHpv0j0q8DdgPCf7WcjlRWvS5rjc0bjFbcwnJ\n1zLnMyrEdsC+acaQocaLzgg9yXuqh5KNImbgMG8oy+raosf4fAimHSUh3s5rxhjE\nV/S+QlGjDufw/RfgUzBM7C3DpXudA9CEQySyc2Kttcoe+2H3pU6TLuquqFIayIjv\nDb65o6mEJ2whF8HJzK8FjH+0MxvT7Bmm/E7Yg1WJWS/OLRdjeXzI8BmrnrUR5nb2\naek+AXq3QNDdLNM6a+hDX7hpgHA+0X8N72yu/vwmB8VJ7P36YYG0/a+VQLz6x9wY\njiqM7jPXAmyffRhxzkCfXIlScz4SHvKBcLHxExdIP3kWhuRw9l1fkgpIgBdz/0FS\nw0e0IXRC9b3EkidxpQZlgq5JkwwC1Juy0jrDUs/hMuqy+2cmc2oYeJ86jmGIBjb4\nyugjQvLJk8jQfuWU2OTxt5DKNFENdVTVZmRT176eT4/vzVIq9J4HzPJbYTQHGpK2\nIiCJjyf81wkGNckbz7nLlpnN67AsMO7hNrGpPMF96ipZZOw5YqG9TmNmLcOBvTYH\nzjMtZdeD605y+wMgUkiCYK1yZ+MnXD9odD6q7dj1HWpPsOGhTIeK9A==\n-----END CERTIFICATE-----\n",
"ca_common_name" : "TEST_CN",
"ca_country_name" : "TEST_C",
"ca_key" : "-----BEGIN RSA PRIVATE KEY-----\nMIIJKgIBAAKCAgEA4dJvCvJ+4CDpYMVzEtWLyOpKLeegs3yCWjKwHQubGXiTl9Ks\nQLlrWTXYyFO3FhqygEZ3V0LUgBm4fWE+668dFa2b3qppxmPJdw1TmnIwadQBZfJh\n9/Ve/fsnk6ktZKS03lgW0qKvwjCi02hTwNwzrrGUrueYO0dK1sKzGJdSD4hZQUQ7\n/8OnfQy7gsyVZbipXs9OOWQBdpbMhTDH/5xGVH0UmZyW0hYyb5pQVsayQQYC8Fix\nltHwACohqoGDfNQVEYu8sg0bnHUf8n/+lH8Kuw01xZieIvpF0RoGWJIlwOCX4BHb\nYkHs/yygzbQFQ/F31ONHLGgrx282AemDaGKNlJKlghQimBwW6Qwp3NJAgBXcV1iV\niyyagRmsFKP3Raya+KaG0RVjFQWoLJ71Bxv6LoVWIAfHMnAWRLuFrXcGA3zJrKKp\nDwEi3zBfFkiRNdj97BHKHcLKmkcmGwn9w4RaJtFoAuhOQAAjcEwSAjyhhQTGW/Vj\nW0FqctmnHMFT1jldDlqy4i92QUrvmrdH+Lk8LE1MaZhhYWwwH6eDGHYBpE2056Yx\nn1if6/wvgcii3yC5kA/vg56BNkBwnTR3in74oYdXGbLOkOOqXI0/mSAWYN+bk3PQ\n7Gb5IlpMK6s0gyj3fixepzAtzm5+FttFib5pNoK1QILRLn54cO7TPprNg48CAwEA\nAQKCAgEAkpIMItXcRcr2zym5E+to7EItXXgu1PCmhrbJmkCTLcgWO/+wb94pb+DE\nUNoNRpqTazDReuDUnkSTe0WoGj8xqIVjWvXO68aO1+fdcKxXAglp0uqsbc1kF4Nx\nX6T54o4JGxufzJ1taKQ6uu7HFbGXFfcK4y9MnoUabSQ4LGjjCVPdYsBQFSS/zCl8\nd1wkR77Ap9n0Esn3LSqZmoVb+mtLNsFsonuBZOClYcyOApS60/t74tYehh7DIMg3\ny7x+RII/HoFNO1/IoRdgYfxzl5yRsXDUiukREvDQafTzU3+gY30i9nuAoljZ45Hq\n2TjUBhJvTc0qwAbpC2wCaOFQumrlKuaVWMl1UAass9Mg5XZBQ//Gco1/Di7CHiF3\nA5hczVGDkCTZfZJBLEXxi4zqey311c9pzEBOXy82E5FxnhB3G/oRWCKfjI3YAXb0\nIUgvFbXH/S/LOmzYFXEVounVq8OwXg7anUtp45sGXIh7X/+OOuWt93dFN10+c3XH\nLeSJBfRdhHU7GyuWIYfaDsBvjkk1vgh4TO3TCkIIF3lq9Izre7NKc2g+NqRddIO5\neGPC6GCpckbgNs3TWLFCKoi71pLFKEq6cUYw4Fl/WYbDNbTZioiEmn8xr/sh2bVw\nKlkWMUZk2DgqrXpYxd7jg0RJhG20Ii0Z5Xyz2nfqB3+tBnMVfrECggEBAPLk+wK9\nW6fT0C5eyFDKnkzIJ69wNaYCKZo1fWbzDHC8Yi6jTKTaAC7D9mnnWmcdOUluKFea\njaBCWbVP0BqkVpQ1bbQiUxru38M7B48/Y3ba984N1/f/aFURsEe0rMWr0Sdc4BiP\nN6payJBQFhgp/9Upbk3ncUx2SMvMmRiWvyYwbmkd9iXGq8+cH5Q6WtmDzA27cn09\nRdbO98y18TZD8FE+Np7JKvxOD/oct3oCGtxhO+vnxoNVGubK0wrxj4xqZuy80CgK\nkOS9DFLzBSaELqCZAkWB3BbVK6UFfeRhY53O3jyF8nzxl/XgoQgu0o017n1BhVpd\nZY5rnuVwVroUv8kCggEBAO4BoyNwDFBdWI2Nl/yDFzEHs8fUVfpu7jwIkGSuP4oE\nh3TKoRH0HQ9IryLP0W1tCYUpwWcPeejyUuQLIDGHwB+0ZnvwoXh2VeQvYGJaZgTR\nmV8lcOBtKeLY1HekpcLmJldRbDXdC7ATj77W5K4gu9nE2MZ9/5iJu4t+WiiiQfV6\nK+gTUNP2/X72r/fxPHH5/e6nhPfpAGqhJrCqLNpO/i5Xogh/5wkg2/V4oAPlqD4N\nC9dRclWs2NOOERzHyEs8mLHOBsiK3wHfK5Zz6SbBQcqASgKDPDex+OQZYWQY8HDg\nR/3W815SVzmHcDqP/3VfQ4MemtebRqGOedvDui4nRJcCggEANWFzdNeuxAR99SLp\nfS/6eD9o0Vqkv7Yr9HMa+zwhGMmd/kfvOS+b6KsyhXXN3WmDxIqMHSyfQYAzfPBs\neN5zFKFlWbhNcVbcIGjhsW6p6l4XJdbPBva/tCpuBmRDsDGhhrgXm+4luq+28lhX\ncroQOoWfc0mREc/REdEGOGww2DC+oyVtikHOUpMqMYZdnv4jI0V11OZZaesUdI3r\n1BQ8RW6ZzG3Dn618P2h+PjcmNha8d4z5iLV0cxJSLU6HUMG1mwOn75Ta4RpXEgfM\nsvlL0gmugR4YA4CX1e2ODFoG7ZCgMMbzUtg5oFTcrxKzPUuD/U0gBIsQHauzQRNe\nTAjxWQKCAQEAo6JYiUrGDJLBCUFqV1/BmCIVhrQEENQn0vqIW9A5Oyj2AGQ37WIK\ngLGWR7bd4//tZbJZmAPZ60B/oO3NSoBspN+g/mFogqvJTcMM31ILhhCdA/935bTn\n8WDmYwO+O4uEnNAMN9Qr7vjkAW85dkZnIMfnykBidHtth/BtCDbWZnGCsmJlVfYg\nPyRXw34F8s7PuT9Peiql8KmvMhMuF0HsG+yAKJvXOj1vPQub6FIDI/ZQR89lbmYS\nBRFNzp3EpYWZ7dUacNKZlG3dR+mVSOHh29nsCGI2Coy/9ANHJEzJMrHgjTM1y4mN\nEq59iKXsGsROZF2sU8QcAYM1YNTmskipLQKCAQEA41tpWPB9uVecozXFX87gPkUu\neX1zl799NLq3gtm7T6H2WgI30lS2Gr2HEr8wjJc/pTKYBi8iFdBumeF6GjE/zj8q\nCXVGKcPlDoB7B6gX84jmSC9iPmjHgABs/QdWSlbYFqTDr934/exKUKN6BxmNQBco\nMB3qqHSZJ46nMpp3KurL81NMIaeGgHGszVyqjKAGESWgxZ2c1Uk6X21xm1NiADfJ\np/Xm6wq8igq6sUznmIHWsk/r3mJ1WkvE/VgKBaQuFjCIN9io9BHIO/LnUCHgQdK/\nJxzObRWt+gmxcD5xkgJyUeb2vugThVHAPYi8c/1K+n9Q9PUODa/bq8i9NabBOA==\n-----END RSA PRIVATE KEY-----\n",
"ca_locality" : "TEST_L",
"ca_organization" : "TEST_O",
"ca_organizational_unit" : "TEST_OU",
"ca_state_or_province_name" : "TEST_S",
"enabled" : false,
"server_cert" : "",
"server_common_name" : "dev.softkeel.com",
"server_country_name" : "",
"server_domain" : "dev.softkeel.com",
"server_ip" : "77.87.125.200",
"server_key" : "",
"server_locality" : "",
"server_organization" : "dev.softkeel.com",
"server_organizational_unit" : "",
"server_state_or_province_name" : ""
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-The root certificate is already in the system
-Common Name must be filled
-Organization must be filled
```
- - - - - -
## IKEv2 Delete CA certificate and key
**Request Structure:** `https:///api/v1/ikev2/delete_ca_rsa`
**Cookie: `access_hash=`**
**Method: `DELETE`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X DELETE https://dev.softkeel.com/api/v1/ikev2/delete_ca_rsa
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"ca_cert" : "",
"ca_common_name" : "TEST_CN",
"ca_country_name" : "TEST_C",
"ca_key" : "",
"ca_locality" : "TEST_L",
"ca_organization" : "TEST_O",
"ca_organizational_unit" : "TEST_OU",
"ca_state_or_province_name" : "TEST_S",
"enabled" : false,
"server_cert" : "",
"server_common_name" : "dev.softkeel.com",
"server_country_name" : "",
"server_domain" : "dev.softkeel.com",
"server_ip" : "77.87.125.200",
"server_key" : "",
"server_locality" : "",
"server_organization" : "dev.softkeel.com",
"server_organizational_unit" : "",
"server_state_or_province_name" : ""
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-The ROOT certificate is not present in the system
```
- - - - - -
## IKEv2 Generate SERVER certificate and key
**Request Structure:** `https:///api/v1/ikev2/generate_server_rsa`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Options required:**
```JSON
"server_domain" = ""
"server_ip" = ""
"server_common_name" = ""
"server_organization" = ""
```
**Options not required:**
```JSON
"server_organizational_unit" = ""
"server_organization" = ""
"server_locality" = ""
"server_state_or_province_name" = ""
"server_country_name" = ""
"server_ipv6" = ""
```
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-d "server_domain=vpn.test.test&\
server_ip=172.16.0.1&\
server_common_name=TEST_CN&\
server_organizational_unit=TEST_OU&\
server_organization=TEST_O&\
server_locality=TEST_L&\
server_state_or_province_name=TEST_S&\
server_country_name=TEST_S&\
" \
-X PUT https://dev.softkeel.com/api/v1/ikev2/generate_server_rsa
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"ca_cert" : "-----BEGIN CERTIFICATE-----\nMIIFlDCCA3ygAwIBAgIIaQxQOCqyX0MwDQYJKoZIhvcNAQEMBQAwaDEQMA4GA1UE\nAwwHVEVTVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8w\nDQYDVQQHDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9D\nMB4XDTIyMTIxMTE2MjAyN1oXDTMyMTIwODE2MjAyN1owaDEQMA4GA1UEAwwHVEVT\nVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8wDQYDVQQH\nDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9DMIICIjAN\nBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA2mAubwuBj55hq/Ukk7U916waAKUG\nb08RdUqzDqC+HP7wpwrg7q8JFKyCDCLQDbDQNZxRPwEIOphRrwY7ZJ8Rmdn2Mu9M\noQOIwOvcJ5vBj/8ge7ypaOvBtp3kezp+WR2k3WE1DVPLoPn+sdMFQawnsKo7U/8O\naUPEMRpMAYMDLR3FeckET0BfJIRWL1WTx4ho6URfIp0F1jntI4i+vcHZPPzRCorG\n86WdmvOoHzKPOH9aHTMBEtG6kHUS67EKgPyLSZDYVjSi1GO4HbOiymV36EMIbaQS\ntQrkj+P9ODsErbBj3SkjDQ8J6a1DlE07gruasR9kVKyGwZfTGRJBcjLzMEzOk7KS\nMj0Z5v3clq3TficJ9HuYjAND9nk0UNzTp0FfwJVJyA/bdu7ev340ZJcH6rhIP6/t\najNDRJPRzJsP+TeAeba41AjhYU6LJjEYyng8g1osui/Lqjlj/n059SO21nobPaCX\norIAYigVlfoS+Jp+vaoFfM0S742q/wa/WGvrsm8ikd8MoKbBJLl9mJJi64REpzkb\nwUxs+7efFF8neMNtDKpx83Ub0nqPM/UCdfTmi2iwLD4i5Bv+Xd0U/q1I51Kbna8l\nimQ1N26JGE2+1NVH5PQ/SO++q7NE4oYsgJqlJHt0nm6+k46mUXjVQojtuSVaDp30\n8q+LubCtTdGjwF0CAwEAAaNCMEAwDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8E\nBAMCAQYwHQYDVR0OBBYEFN9i/vdCTH3z/zc693rCsHS1PtqNMA0GCSqGSIb3DQEB\nDAUAA4ICAQAcz/UIJa8VQqj0e9gSekZq9+EnpaGxSmf7pb6WDcX9dVDmRbiWMgHE\nJwWovePd6Jdb7XOhY3IrYGSQK9mEeRh4ac1guUEgQNRpbj+dEKpvvoYt8UQhuc7U\nrpyNggHfpzmYoMDJ/Z7EYbh5qnIkmqsTjnr4ZXEUxKC8iwxA41j5mRTrlGE5GGiC\nfrfLNI0NdTgnmvEXVTFj6wvGbw5qzerkRk22vwj/C2wBZBkd6CYrmAJk/5G4oWik\nTWrwTLqM+pxVI4YXO84dRysEf90cHy+T1y4YvNtowLJ4SkQYNhR5+xW8PWQM9JRG\n65xDrFBGm2cnhvGDpZGApy4mtg8n2stuK4C/QB+puNs6EoV1aMs2SPmxf5PJHSjQ\nuK32L+ZPw+9wPZnlUURLTIryyIwcY70Wjx4+kgzjANyxgEk8y77RuWdya8RocT8G\nQvglhyKZxpojXt5VUFIM2d8fnKTugeNeds9zgh5CjrVcBkh+q85Im3+t4a8tUqlq\nxvH5C0d4wxnHsNh/dQAlGxC5ppNKxYmR259KqGmGvW24vSO6BSnTmDrWGKiGlixW\nV4CfC9Cpnghqu6jEThUw1QY7E6YOfKn7kpx+t3QbQJa3MYSrumZRFEgVYXvg8tdY\nyehwxBWIhVZVCZFbKasBPeatv1hwH8IzWAJFLctcM6Kp4xdRQUrkxQ==\n-----END CERTIFICATE-----\n",
"ca_common_name" : "TEST_CN",
"ca_country_name" : "TEST_C",
"ca_key" : "-----BEGIN RSA PRIVATE KEY-----\nMIIJKQIBAAKCAgEA2mAubwuBj55hq/Ukk7U916waAKUGb08RdUqzDqC+HP7wpwrg\n7q8JFKyCDCLQDbDQNZxRPwEIOphRrwY7ZJ8Rmdn2Mu9MoQOIwOvcJ5vBj/8ge7yp\naOvBtp3kezp+WR2k3WE1DVPLoPn+sdMFQawnsKo7U/8OaUPEMRpMAYMDLR3FeckE\nT0BfJIRWL1WTx4ho6URfIp0F1jntI4i+vcHZPPzRCorG86WdmvOoHzKPOH9aHTMB\nEtG6kHUS67EKgPyLSZDYVjSi1GO4HbOiymV36EMIbaQStQrkj+P9ODsErbBj3Skj\nDQ8J6a1DlE07gruasR9kVKyGwZfTGRJBcjLzMEzOk7KSMj0Z5v3clq3TficJ9HuY\njAND9nk0UNzTp0FfwJVJyA/bdu7ev340ZJcH6rhIP6/tajNDRJPRzJsP+TeAeba4\n1AjhYU6LJjEYyng8g1osui/Lqjlj/n059SO21nobPaCXorIAYigVlfoS+Jp+vaoF\nfM0S742q/wa/WGvrsm8ikd8MoKbBJLl9mJJi64REpzkbwUxs+7efFF8neMNtDKpx\n83Ub0nqPM/UCdfTmi2iwLD4i5Bv+Xd0U/q1I51Kbna8limQ1N26JGE2+1NVH5PQ/\nSO++q7NE4oYsgJqlJHt0nm6+k46mUXjVQojtuSVaDp308q+LubCtTdGjwF0CAwEA\nAQKCAgAHaRwqSImtBgLqgvcqzAu9Nenr+62sOVKuWEqbRHkvIren84aOkwIL4Y7I\nOqY00LtAFn3rVW2iD2k2N0/sqjk+r1bbg6NmE2igo2BlN7Pp3w6LJGvbU6TPPaxz\nQhjnjUn6+UGDokRWwiUSg8a54821ARHiV9V1XQdbYzkRFBEXhtsctuWeiuCvrI4A\nLTdGnipxQBC6a/m2u2CAxDM03U8x8qJlaTA3NHeUupAJ/v09PZUhSInQya07Gb36\noZdpqShQ5slwo3ijHH8zAtWTaL4Y861lixvXaPc4qtP9BIO0IThCWRMHbms3stmI\nPta2KQem2xnchb5M84oGX8g4x+HYwa/hrRZAsQNvNqPXaHHAav6+QKALiaGVY9Hr\nITmKgoimPuPxMEPfqHAs9kI9DpDwV+58i+jJsb04wsC/INeO35G4dxBZqoHrA61k\nPGsxyDHTKn4f5PguN+JUmU+Y0NV9uehFJD+lAA3UBYoR+MYXyrQBTXh6OYGgniZO\n+EJljgfwWnCXj27uFm6dOI8S+sBim64MVPD9G+FRG48sV+RAYZKy9QP6nOgUmQVM\nePjGCz4TfXIXXpbdkXdNHSzPIGMFpPKBeK/uF8mxKDKxg9Di0t/Q6CYz+xiid+Vj\nIkh2dSrwzkyYghVDW97Rivbx3mEdLPsbMbfY0stuiDhaBXlNQQKCAQEA+hVmqnpD\nUqQMkf6tmQCurZm4GQTRqklWnQ+ta4OhKinnSKGBGct0GgX1ip5ImAus8drcTz5W\n9bc1rDaXuFKnKVqal6FzbsyfvKWTzdNqKw2dFgisqwLzJ7xg6htuBi2AOyBrpNtm\nDmXP2cWEcdk93E99nwhTyaP5mnftx0SBlyKAn7Qt5iUg6ePfXmjL1ce4ZLHNAQC4\nwQWLQ2TVlGINpJPK0ZXW2dHbGdLvbnSdEg8stSRGOLXKoBT06kQCkEaBZzt5/cJl\n6Hlw9hYRofKR1pVqwG6XkN/x4Px1nc2HyDGSsVIxIM5Yv/d9pa3OcXvRuS+5FaXf\nd0qUUxeZqZlUrwKCAQEA34q+4IEq20BqwhOLlLCjpbyGIHiLMMraLFZ8Z5D5poBZ\nWjfsO3coFysLg1VEa+C9rMceCYI6i/H8fYiSoYJrBN72DYBFkWF5GTeJ5EHmW4B4\nL7u4cW/x/yyf6woGJRkoRagNUb7bD/Cp3Fhpm45iP5bYvIK4cJKhQZixpJ4VZpIg\n9f+oHP3ikuJgJ/B6kdv2zJ7SghVFrpP8yOokMdbiKYtiHDSOsRRiEj5l4DHfymyy\nGDLw/kMuoC+PHAipjvL4VxlqO1r+wqorjEPdZ2CtYdi353xrPERNGTS9D43ZyRT0\nLeMGUeDely40T2oewmHXEPeqng8+Mj1PTg7/6uGWswKCAQAfBva04fRmVWol1uYs\n3HPPoAnCOOHWccDoPaCzfSJKu+YxEbCVxbNC40hiiV7SVmh/nTrGLiLV24QyOJe8\nS6znqZESjPpoXcTXv+dFmxxJ+SdrK2pY0UXfwTR49yxAYfbN3yjbzEiuMp2GFEZp\nZZ2SLt6UE5FprAl0y7pZhbtaR/KTXeRv8F1UB2yYJwJbJKtQ+upHXJKPiCOOGf2R\nqlSs/ZUlSaTdY3b+jjgciSVPr0hJtRVtRci88bytMADta4H0j+GDxVGldSO5tGU9\npX3IlMMo2s+9LruwwUHKcUyOXvAnRd5IhrFmJ8uT+atqUwVjJ3OcJvdBsqQSZxQu\ngZKLAoIBAQCvNYlsX/FeTfwfR8CEd3qcwcoDE1hNkwEz9UmmxyvVxA3Et8ZRyZBD\nsHpioudxAoLINH0niMoovC9hmTUMoDMPa05BwMNGMrb++9f5b2mFWIlbKHBlgQ+V\nKL3jNEUiuLgm+JQP+V6r/L62NRn5Ub1SCAKypma33UXFK1A5LaqqbWimR47Vwmzf\nIc2qIEOBpX2oXeezC8dFETr1owdhhQJY+6WXY95fjxFbKUsiURUODOn+K5dWQwP9\ni6lImMWFhIz/f60S/rxliYl+dAbKKy1aXsmuB4fpgcNIOVziHxWPFPxaJvHiJTVy\nG0Xm5M9dHeC6rNQu9NWT/Rf2n60YxV4fAoIBAQC9qXbBxy2kd+4+I9gVt348qRbd\nZlxJi3q/N22wZ1BOIGCAWWsw33YyNghq6xlsu6jt7C/XFYRKTaS5Z9F8/InXbP4j\n/gejdT22TikruWpPrU3+8fifJZsmEfsUGZ6ulk9174hbGbz/TH/JRtpCxFLxw92e\nG+JuKpz0GP/MvtpkkH8MXCmP3dXVchO7pFQXfCjmVaSRA7oii8M4a9m2U4+zM76F\nEfOkFehwYi+LSUBFbFrNKM0+Gw6q8pS0GjdKnljuyhhzN43k0iyLGXcpK5I2xuT7\n8iypj2n4VHccj7flM1QbY2mNuerlfs6s0/Z0t6oF/ZdC6GEMT8LA9czGinLY\n-----END RSA PRIVATE KEY-----\n",
"ca_locality" : "TEST_L",
"ca_organization" : "TEST_O",
"ca_organizational_unit" : "TEST_OU",
"ca_state_or_province_name" : "TEST_S",
"enabled" : false,
"server_cert" : "-----BEGIN CERTIFICATE-----\nMIIFujCCA6KgAwIBAgIIbvUBrU6ZBQUwDQYJKoZIhvcNAQEMBQAwaDEQMA4GA1UE\nAwwHVEVTVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8w\nDQYDVQQHDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9D\nMB4XDTIyMTIxMTE2MjE1NloXDTI3MTIxMDE2MjE1NlowaDEQMA4GA1UEAwwHVEVT\nVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8wDQYDVQQH\nDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9TMIICIjAN\nBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA1Fw/nJ9q3W3avtdBIJP6RNOUwsk8\n0Km4ezzVw/ikoaLVMDwJCOJr1R7zxYh9GGYZUj06cFtQ7Q0JPSyYmEXozLEBDIsi\na6N34kX4q7n2cb2lzIOUblVFer2SjSqHDr2hlNtOr7lh83TsSTiVxzkIQ/fUR3Vj\nOxT4vz+Oh/VDOCuQY6QblGL2hoonuusGXY6FMQhErktCmfUkLJKVXmN3/EUg1J/c\nHe5TZ6XQ2YYBBAXxEwP//DWFa/4eWou1D2PlvSs4nq+PSNupM/ZeOkVmtyX/0vGL\n76BMoy3ZD7E8CIXaXsX65ez6/PL9S96l0D0z7b/UKmCESCFLly5gU3HzW6GQyykE\nw5X3g/Cocg+oUK6gSonwtzvqTmvsEvb3RokzjceZzvV52HRl9JfgqbCBJiKLMVge\nlggBCxrCr4qZVjA1m6K0Z8rG3nTPGxYGDU/flS8sUfcL9BfbO83JEy4sBExmD2VQ\nKSJdsQnqQ+NxnFNyl4y1xY8rQ+oqr49xsu1rrC60GOWQ3jp7tbgGIvErVaCRuk64\nM7tmdrVT5pdS1XqHMI5f3vAigGsPjcNrFXSQLDttQdLmGq9SOcLqKeao0UINr0Vs\nM3Mejmb92ns8cFvWmq+SWNJyplYRUiLskJKS2hnigdqYiLI9VWaQ8uIlLQbV6tRZ\nxSw+0ZdTy+58rHMCAwEAAaNoMGYwHwYDVR0jBBgwFoAU32L+90JMffP/Nzr3esKw\ndLU+2o0wJAYDVR0RBB0wG4INdnBuLnRlc3QudGVzdIIKMTcyLjE2LjAuMTAdBgNV\nHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUIAgIwDQYJKoZIhvcNAQEMBQADggIBAFh4\np8q0mviEk/E+s/OUXLDwd498r7WV+Wt+fMvLT2k+Pnalc5wAfmRxJb4RgjoyzK05\nKxxTACuZw6+0kTl7SWrH9W8ljXK7ecNnHE9YGwpCwXQRO+bWu8wPkXho847stA2D\n4tVJyqW74Q1S40ETaoHf8EJyiljHsHshNq31BWin69OHM5686VksAXXcv9fMgthd\nhVZhwWCNMWQRCY74/r7ewZjFFBc5OUYqyfURC4DflID6qEcEC2eClOjKezqZj/qp\nWajmscUcCWCxy5qQep64XP9P7lxfh/6bFbme3rd8W1twMLg8C2edCjKpGX+/Jgf9\nMpsq0CfowwRDh3Gl2IkwnwBJnSdKzJbNRbukyYCqdSP/1Xics3qXkCYIO7D1xpz1\nFDce9xv04rpykjA4+jrS1Uj7VYacvKwiczZ4zu5QUiaUsBFfoV8iinpyt3Rkvvq/\n3dAHw0HJh+5+VmQ+PYXDfk/UtXVr+w/i/j+ZHZBskGkh3+dUvvWtb6z5jFXhaSYH\nt0C2+UrjmPrfuvIFBm7fLC7qVkvF+CaRw4CKVSH2frOn+Di1ODOjwlcVY+D9WKF2\n1v90oZW77NT7N6fS2nv7VLDbD0JhjWXOLR+gjD5FMzbFApaQROl2G7SeXhAAINZo\nLFlPsN8gOUd8+EnkifXKNa1qpZ87vc8u+RZh2tdm\n-----END CERTIFICATE-----\n",
"server_common_name" : "TEST_CN",
"server_country_name" : "TEST_S",
"server_domain" : "vpn.test.test",
"server_ip" : "172.16.0.1",
"server_key" : "-----BEGIN RSA PRIVATE KEY-----\nMIIJKQIBAAKCAgEA1Fw/nJ9q3W3avtdBIJP6RNOUwsk80Km4ezzVw/ikoaLVMDwJ\nCOJr1R7zxYh9GGYZUj06cFtQ7Q0JPSyYmEXozLEBDIsia6N34kX4q7n2cb2lzIOU\nblVFer2SjSqHDr2hlNtOr7lh83TsSTiVxzkIQ/fUR3VjOxT4vz+Oh/VDOCuQY6Qb\nlGL2hoonuusGXY6FMQhErktCmfUkLJKVXmN3/EUg1J/cHe5TZ6XQ2YYBBAXxEwP/\n/DWFa/4eWou1D2PlvSs4nq+PSNupM/ZeOkVmtyX/0vGL76BMoy3ZD7E8CIXaXsX6\n5ez6/PL9S96l0D0z7b/UKmCESCFLly5gU3HzW6GQyykEw5X3g/Cocg+oUK6gSonw\ntzvqTmvsEvb3RokzjceZzvV52HRl9JfgqbCBJiKLMVgelggBCxrCr4qZVjA1m6K0\nZ8rG3nTPGxYGDU/flS8sUfcL9BfbO83JEy4sBExmD2VQKSJdsQnqQ+NxnFNyl4y1\nxY8rQ+oqr49xsu1rrC60GOWQ3jp7tbgGIvErVaCRuk64M7tmdrVT5pdS1XqHMI5f\n3vAigGsPjcNrFXSQLDttQdLmGq9SOcLqKeao0UINr0VsM3Mejmb92ns8cFvWmq+S\nWNJyplYRUiLskJKS2hnigdqYiLI9VWaQ8uIlLQbV6tRZxSw+0ZdTy+58rHMCAwEA\nAQKCAgAa/rsLYuyHx242MlDSHl2DIE5Z0JENiXWtHNejuNjcv0FQh2Eyou3IQs4E\nP0x/rILthGEIZWNNLwoMn72qJcDpPFsAyDMQ8c/MkM6CrfoZDV2lONjGicpyRuT5\nUv2mLw76SEKhbfR4qVVcHXhUwfg+A6QVjWOW4Bya2y54NAJegpMxR2xGGapzAd75\nEOVXQUXHLODmMyT9Qz9c9ylLvWNES1lYDhZCK8iodViuPi2k4Eh7/VcuLXOPfddH\n9ViH41ASEwt4iKKzRVEmDNx/ldDv2UHDA/eg94Smfa6JIyOZhcJzp8E0N0LUouL2\nIRB8/zq5r1f+JxTJwonEZx3Rnbusn95x+92aRXjMyhtzViwCIm9LODFZ0suKgELP\nd75FIksG5e4JJCP866ZqkxP50Hbu/02pZwPWsJn752PgiI/1CPvcVYbV8BcN6mAa\ngHGTr7lzbTbyJOaCEht6Y5q8Qckc7TysHfUwgDbohfa8Byra9ITR39JJ5hnuN73/\nABE6SDpYXaK5JCf0pv29fcrr76Kra+cJ49ZBNtBJIqM0neNDPcZrX+MbFt8KDo6l\nrClE0Xk7mfHmTxMsdM6zGhW2ktTCdc07irWwidGLVdeIhO6H+kMHul0yB3AwWqw2\ncqGWCabP21CtIO43wIMg9SskYZ3bUgLtE1STYZwQsOugNv3lEQKCAQEA+NwBolZd\nY1F7VOR5lUq7YQLIwdhnMkbF+HORpXuaNfwfw7t5ByMUSF0NQhF937/DsAX5QRm7\nXiwOPD/axedXzhozfCpQak/lCSvpkef9EgnxcsPl/etyHtI8wV1JhHHs5nsHG1DD\nsL766w/60Syk2zAU/S3r2I56VD2RzId1ouHmB/xuOe8UapEB+AnO3Dbwme5o++KQ\nSzCp9JlFxZmXlZ3h1nwh6dLhF62qP7RySIa+GHDph+Fl8/rVPyxU/qlumBEcRL39\nkqa2j5+RNRHWKvseylq0x2qWH1UrScW1WMd6ZoCczftYhANesFF5TvC0uttPufGN\no5wGeNBjyKpriwKCAQEA2nQjhUfKzQ6/qV7zugZN9+5FuRT2dZPCmH03B74U2LJW\nmesV+rf1gKaoS67Bex9egb3UigdaLHBGTI6SYYy7dUjv1g5VPFvfGoNsf4lVP6yN\nAc/3VQQlZjpM6YpONc6oXWso50m29FOuIpAbWafRG+WDXuHc9WVvd/1w6ToACPmL\n4/EDW12rPSUaNqWXBbmzhRpOIbHuIzBcx7mDn8sXVCDr8nlrCpvsd4c/Zh+jPcvg\n5wyvSVgeKYeEM9J2B8K/uUSnKZK7QQuseKqyeXtMZHNQdrg6WRNQ/nQW56eWsZRD\nBurG6qX0oweN6xE9/+pavWvea/DYXI6wDDhVK1F/uQKCAQBCxj3GAmiCis2OBNQ+\n49ONf0LBCMD/84+RT+lHvves/p7DVV1vNdFubVFuZeUhkYH/jErKVg45gZa8QeIA\n8kdULSGdcnkrXY62PEsq9FWqbnKT+c6PqIpxjLXyqIZefHc1jNNmV/B6T3RieGIz\nmEgP7EHlgVnkPK7ERdUGTV6aOwUPJYOqFeWjho9Br9gKrM84bolK9QsEseUYlbvr\n/n93DOsZMyuiYww030tsVo3HuiftxPZUmH1Tzv1DOzD/OBVNxmGQbG5K2GLp/MXo\nuIV/+OvVHiudypLHi4HXBK7ZSIUmVeI9PvEMUx8oLmRfcyT7cnddDFyWBvqRllD/\n+gJrAoIBAQCAPP09GE/s4GOSwbLB2UGb8bvsUmn7y6nIankLioIiU06TPHXCoIr1\n4t+YzhW2eUu5Tf6eqII+5AnglzFHIp5I03A3cGKI9EWcAtqGY9AveNOt5K+EsNJj\nmIXd8trGq3IapPV2EMfd1eG7WG01zFXs0ma0JFLZm5o8DgNiZjHvEs8UGD+oOuxz\nEHy656ooKkNAN5j2HsV00sckV7r06vve3xSjWrODntTJthN5l8j0VeLIv6GGpLvQ\nFUV+RmYTWDfEQpD+zqwuGvQ8QbhTqBXIQglSKAPYloZNWUi45KCJzkcqoFf1F0bt\nDVo6S/zhZmmuGMyRAOmCLCEci1U0ALvBAoIBAQCWFh8HAtiPaFtX3vJs/tpyaDMf\nCuudCtEVnjgk+jD4V+Qj7wFAVcyQ0qF+S2XaapyukN8Yz935DQ/54I8vhhZhs8z4\nd0Mjm5sD7DP/3fkafxBfg5znpDsVrRBk/vMV+kR9REiEnf6TaEcKWfjnihp2xWX3\nNwF+OL4ojiECh9WLPETNI2nQa3nQoB1+LztuQ+w27YLdDs2qIXLfnkj3aYj6UQ9i\n9OhiIY8ZjHq0EaGTxyAVCqlh07C3KwA0aHbvG84pDyDpMJIjVEMnVd2uH38qAw3b\nclvXzBF+s0KAPFI4qCQSyY0yKLA2e03EANAoqwBIsUDNUFo1EpHGbPtddeQD\n-----END RSA PRIVATE KEY-----\n",
"server_locality" : "TEST_L",
"server_organization" : "TEST_O",
"server_organizational_unit" : "TEST_OU",
"server_state_or_province_name" : "TEST_S"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-The root certificate is not present in the system
-Server Domain must be filled
-Server IP must be filled
-Common Name must be filled
-Organization must be filled
```
- - - - - -
## IKEv2 Delete SERVER certificate and key
**Request Structure:** `https:///api/v1/ikev2/delete_server_rsa`
**Cookie: `access_hash=`**
**Method: `DELETE`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X DELETE https://dev.softkeel.com/api/v1/ikev2/delete_server_rsa
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"ca_cert" : "-----BEGIN CERTIFICATE-----\nMIIFlDCCA3ygAwIBAgIIaQxQOCqyX0MwDQYJKoZIhvcNAQEMBQAwaDEQMA4GA1UE\nAwwHVEVTVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8w\nDQYDVQQHDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9D\nMB4XDTIyMTIxMTE2MjAyN1oXDTMyMTIwODE2MjAyN1owaDEQMA4GA1UEAwwHVEVT\nVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8wDQYDVQQH\nDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9DMIICIjAN\nBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA2mAubwuBj55hq/Ukk7U916waAKUG\nb08RdUqzDqC+HP7wpwrg7q8JFKyCDCLQDbDQNZxRPwEIOphRrwY7ZJ8Rmdn2Mu9M\noQOIwOvcJ5vBj/8ge7ypaOvBtp3kezp+WR2k3WE1DVPLoPn+sdMFQawnsKo7U/8O\naUPEMRpMAYMDLR3FeckET0BfJIRWL1WTx4ho6URfIp0F1jntI4i+vcHZPPzRCorG\n86WdmvOoHzKPOH9aHTMBEtG6kHUS67EKgPyLSZDYVjSi1GO4HbOiymV36EMIbaQS\ntQrkj+P9ODsErbBj3SkjDQ8J6a1DlE07gruasR9kVKyGwZfTGRJBcjLzMEzOk7KS\nMj0Z5v3clq3TficJ9HuYjAND9nk0UNzTp0FfwJVJyA/bdu7ev340ZJcH6rhIP6/t\najNDRJPRzJsP+TeAeba41AjhYU6LJjEYyng8g1osui/Lqjlj/n059SO21nobPaCX\norIAYigVlfoS+Jp+vaoFfM0S742q/wa/WGvrsm8ikd8MoKbBJLl9mJJi64REpzkb\nwUxs+7efFF8neMNtDKpx83Ub0nqPM/UCdfTmi2iwLD4i5Bv+Xd0U/q1I51Kbna8l\nimQ1N26JGE2+1NVH5PQ/SO++q7NE4oYsgJqlJHt0nm6+k46mUXjVQojtuSVaDp30\n8q+LubCtTdGjwF0CAwEAAaNCMEAwDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8E\nBAMCAQYwHQYDVR0OBBYEFN9i/vdCTH3z/zc693rCsHS1PtqNMA0GCSqGSIb3DQEB\nDAUAA4ICAQAcz/UIJa8VQqj0e9gSekZq9+EnpaGxSmf7pb6WDcX9dVDmRbiWMgHE\nJwWovePd6Jdb7XOhY3IrYGSQK9mEeRh4ac1guUEgQNRpbj+dEKpvvoYt8UQhuc7U\nrpyNggHfpzmYoMDJ/Z7EYbh5qnIkmqsTjnr4ZXEUxKC8iwxA41j5mRTrlGE5GGiC\nfrfLNI0NdTgnmvEXVTFj6wvGbw5qzerkRk22vwj/C2wBZBkd6CYrmAJk/5G4oWik\nTWrwTLqM+pxVI4YXO84dRysEf90cHy+T1y4YvNtowLJ4SkQYNhR5+xW8PWQM9JRG\n65xDrFBGm2cnhvGDpZGApy4mtg8n2stuK4C/QB+puNs6EoV1aMs2SPmxf5PJHSjQ\nuK32L+ZPw+9wPZnlUURLTIryyIwcY70Wjx4+kgzjANyxgEk8y77RuWdya8RocT8G\nQvglhyKZxpojXt5VUFIM2d8fnKTugeNeds9zgh5CjrVcBkh+q85Im3+t4a8tUqlq\nxvH5C0d4wxnHsNh/dQAlGxC5ppNKxYmR259KqGmGvW24vSO6BSnTmDrWGKiGlixW\nV4CfC9Cpnghqu6jEThUw1QY7E6YOfKn7kpx+t3QbQJa3MYSrumZRFEgVYXvg8tdY\nyehwxBWIhVZVCZFbKasBPeatv1hwH8IzWAJFLctcM6Kp4xdRQUrkxQ==\n-----END CERTIFICATE-----\n",
"ca_common_name" : "TEST_CN",
"ca_country_name" : "TEST_C",
"ca_key" : "-----BEGIN RSA PRIVATE KEY-----\nMIIJKQIBAAKCAgEA2mAubwuBj55hq/Ukk7U916waAKUGb08RdUqzDqC+HP7wpwrg\n7q8JFKyCDCLQDbDQNZxRPwEIOphRrwY7ZJ8Rmdn2Mu9MoQOIwOvcJ5vBj/8ge7yp\naOvBtp3kezp+WR2k3WE1DVPLoPn+sdMFQawnsKo7U/8OaUPEMRpMAYMDLR3FeckE\nT0BfJIRWL1WTx4ho6URfIp0F1jntI4i+vcHZPPzRCorG86WdmvOoHzKPOH9aHTMB\nEtG6kHUS67EKgPyLSZDYVjSi1GO4HbOiymV36EMIbaQStQrkj+P9ODsErbBj3Skj\nDQ8J6a1DlE07gruasR9kVKyGwZfTGRJBcjLzMEzOk7KSMj0Z5v3clq3TficJ9HuY\njAND9nk0UNzTp0FfwJVJyA/bdu7ev340ZJcH6rhIP6/tajNDRJPRzJsP+TeAeba4\n1AjhYU6LJjEYyng8g1osui/Lqjlj/n059SO21nobPaCXorIAYigVlfoS+Jp+vaoF\nfM0S742q/wa/WGvrsm8ikd8MoKbBJLl9mJJi64REpzkbwUxs+7efFF8neMNtDKpx\n83Ub0nqPM/UCdfTmi2iwLD4i5Bv+Xd0U/q1I51Kbna8limQ1N26JGE2+1NVH5PQ/\nSO++q7NE4oYsgJqlJHt0nm6+k46mUXjVQojtuSVaDp308q+LubCtTdGjwF0CAwEA\nAQKCAgAHaRwqSImtBgLqgvcqzAu9Nenr+62sOVKuWEqbRHkvIren84aOkwIL4Y7I\nOqY00LtAFn3rVW2iD2k2N0/sqjk+r1bbg6NmE2igo2BlN7Pp3w6LJGvbU6TPPaxz\nQhjnjUn6+UGDokRWwiUSg8a54821ARHiV9V1XQdbYzkRFBEXhtsctuWeiuCvrI4A\nLTdGnipxQBC6a/m2u2CAxDM03U8x8qJlaTA3NHeUupAJ/v09PZUhSInQya07Gb36\noZdpqShQ5slwo3ijHH8zAtWTaL4Y861lixvXaPc4qtP9BIO0IThCWRMHbms3stmI\nPta2KQem2xnchb5M84oGX8g4x+HYwa/hrRZAsQNvNqPXaHHAav6+QKALiaGVY9Hr\nITmKgoimPuPxMEPfqHAs9kI9DpDwV+58i+jJsb04wsC/INeO35G4dxBZqoHrA61k\nPGsxyDHTKn4f5PguN+JUmU+Y0NV9uehFJD+lAA3UBYoR+MYXyrQBTXh6OYGgniZO\n+EJljgfwWnCXj27uFm6dOI8S+sBim64MVPD9G+FRG48sV+RAYZKy9QP6nOgUmQVM\nePjGCz4TfXIXXpbdkXdNHSzPIGMFpPKBeK/uF8mxKDKxg9Di0t/Q6CYz+xiid+Vj\nIkh2dSrwzkyYghVDW97Rivbx3mEdLPsbMbfY0stuiDhaBXlNQQKCAQEA+hVmqnpD\nUqQMkf6tmQCurZm4GQTRqklWnQ+ta4OhKinnSKGBGct0GgX1ip5ImAus8drcTz5W\n9bc1rDaXuFKnKVqal6FzbsyfvKWTzdNqKw2dFgisqwLzJ7xg6htuBi2AOyBrpNtm\nDmXP2cWEcdk93E99nwhTyaP5mnftx0SBlyKAn7Qt5iUg6ePfXmjL1ce4ZLHNAQC4\nwQWLQ2TVlGINpJPK0ZXW2dHbGdLvbnSdEg8stSRGOLXKoBT06kQCkEaBZzt5/cJl\n6Hlw9hYRofKR1pVqwG6XkN/x4Px1nc2HyDGSsVIxIM5Yv/d9pa3OcXvRuS+5FaXf\nd0qUUxeZqZlUrwKCAQEA34q+4IEq20BqwhOLlLCjpbyGIHiLMMraLFZ8Z5D5poBZ\nWjfsO3coFysLg1VEa+C9rMceCYI6i/H8fYiSoYJrBN72DYBFkWF5GTeJ5EHmW4B4\nL7u4cW/x/yyf6woGJRkoRagNUb7bD/Cp3Fhpm45iP5bYvIK4cJKhQZixpJ4VZpIg\n9f+oHP3ikuJgJ/B6kdv2zJ7SghVFrpP8yOokMdbiKYtiHDSOsRRiEj5l4DHfymyy\nGDLw/kMuoC+PHAipjvL4VxlqO1r+wqorjEPdZ2CtYdi353xrPERNGTS9D43ZyRT0\nLeMGUeDely40T2oewmHXEPeqng8+Mj1PTg7/6uGWswKCAQAfBva04fRmVWol1uYs\n3HPPoAnCOOHWccDoPaCzfSJKu+YxEbCVxbNC40hiiV7SVmh/nTrGLiLV24QyOJe8\nS6znqZESjPpoXcTXv+dFmxxJ+SdrK2pY0UXfwTR49yxAYfbN3yjbzEiuMp2GFEZp\nZZ2SLt6UE5FprAl0y7pZhbtaR/KTXeRv8F1UB2yYJwJbJKtQ+upHXJKPiCOOGf2R\nqlSs/ZUlSaTdY3b+jjgciSVPr0hJtRVtRci88bytMADta4H0j+GDxVGldSO5tGU9\npX3IlMMo2s+9LruwwUHKcUyOXvAnRd5IhrFmJ8uT+atqUwVjJ3OcJvdBsqQSZxQu\ngZKLAoIBAQCvNYlsX/FeTfwfR8CEd3qcwcoDE1hNkwEz9UmmxyvVxA3Et8ZRyZBD\nsHpioudxAoLINH0niMoovC9hmTUMoDMPa05BwMNGMrb++9f5b2mFWIlbKHBlgQ+V\nKL3jNEUiuLgm+JQP+V6r/L62NRn5Ub1SCAKypma33UXFK1A5LaqqbWimR47Vwmzf\nIc2qIEOBpX2oXeezC8dFETr1owdhhQJY+6WXY95fjxFbKUsiURUODOn+K5dWQwP9\ni6lImMWFhIz/f60S/rxliYl+dAbKKy1aXsmuB4fpgcNIOVziHxWPFPxaJvHiJTVy\nG0Xm5M9dHeC6rNQu9NWT/Rf2n60YxV4fAoIBAQC9qXbBxy2kd+4+I9gVt348qRbd\nZlxJi3q/N22wZ1BOIGCAWWsw33YyNghq6xlsu6jt7C/XFYRKTaS5Z9F8/InXbP4j\n/gejdT22TikruWpPrU3+8fifJZsmEfsUGZ6ulk9174hbGbz/TH/JRtpCxFLxw92e\nG+JuKpz0GP/MvtpkkH8MXCmP3dXVchO7pFQXfCjmVaSRA7oii8M4a9m2U4+zM76F\nEfOkFehwYi+LSUBFbFrNKM0+Gw6q8pS0GjdKnljuyhhzN43k0iyLGXcpK5I2xuT7\n8iypj2n4VHccj7flM1QbY2mNuerlfs6s0/Z0t6oF/ZdC6GEMT8LA9czGinLY\n-----END RSA PRIVATE KEY-----\n",
"ca_locality" : "TEST_L",
"ca_organization" : "TEST_O",
"ca_organizational_unit" : "TEST_OU",
"ca_state_or_province_name" : "TEST_S",
"enabled" : false,
"server_cert" : "",
"server_common_name" : "TEST_CN",
"server_country_name" : "TEST_S",
"server_domain" : "vpn.test.test",
"server_ip" : "172.16.0.1",
"server_key" : "",
"server_locality" : "TEST_L",
"server_organization" : "TEST_O",
"server_organizational_unit" : "TEST_OU",
"server_state_or_province_name" : "TEST_S"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-The ROOT certificate is not present in the system
```
- - - - - -
## IKEv2 Enable/Disable
**Request Structure:** `https:///api/v1/ikev2/`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Options required:**
```JSON
"enabled" = "0|1"
```
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-d "enabled=1" \
-X PUT https://dev.softkeel.com/api/v1/ikev2
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"ca_cert" : "-----BEGIN CERTIFICATE-----\nMIIFlDCCA3ygAwIBAgIIaQxQOCqyX0MwDQYJKoZIhvcNAQEMBQAwaDEQMA4GA1UE\nAwwHVEVTVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8w\nDQYDVQQHDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9D\nMB4XDTIyMTIxMTE2MjAyN1oXDTMyMTIwODE2MjAyN1owaDEQMA4GA1UEAwwHVEVT\nVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8wDQYDVQQH\nDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9DMIICIjAN\nBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA2mAubwuBj55hq/Ukk7U916waAKUG\nb08RdUqzDqC+HP7wpwrg7q8JFKyCDCLQDbDQNZxRPwEIOphRrwY7ZJ8Rmdn2Mu9M\noQOIwOvcJ5vBj/8ge7ypaOvBtp3kezp+WR2k3WE1DVPLoPn+sdMFQawnsKo7U/8O\naUPEMRpMAYMDLR3FeckET0BfJIRWL1WTx4ho6URfIp0F1jntI4i+vcHZPPzRCorG\n86WdmvOoHzKPOH9aHTMBEtG6kHUS67EKgPyLSZDYVjSi1GO4HbOiymV36EMIbaQS\ntQrkj+P9ODsErbBj3SkjDQ8J6a1DlE07gruasR9kVKyGwZfTGRJBcjLzMEzOk7KS\nMj0Z5v3clq3TficJ9HuYjAND9nk0UNzTp0FfwJVJyA/bdu7ev340ZJcH6rhIP6/t\najNDRJPRzJsP+TeAeba41AjhYU6LJjEYyng8g1osui/Lqjlj/n059SO21nobPaCX\norIAYigVlfoS+Jp+vaoFfM0S742q/wa/WGvrsm8ikd8MoKbBJLl9mJJi64REpzkb\nwUxs+7efFF8neMNtDKpx83Ub0nqPM/UCdfTmi2iwLD4i5Bv+Xd0U/q1I51Kbna8l\nimQ1N26JGE2+1NVH5PQ/SO++q7NE4oYsgJqlJHt0nm6+k46mUXjVQojtuSVaDp30\n8q+LubCtTdGjwF0CAwEAAaNCMEAwDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8E\nBAMCAQYwHQYDVR0OBBYEFN9i/vdCTH3z/zc693rCsHS1PtqNMA0GCSqGSIb3DQEB\nDAUAA4ICAQAcz/UIJa8VQqj0e9gSekZq9+EnpaGxSmf7pb6WDcX9dVDmRbiWMgHE\nJwWovePd6Jdb7XOhY3IrYGSQK9mEeRh4ac1guUEgQNRpbj+dEKpvvoYt8UQhuc7U\nrpyNggHfpzmYoMDJ/Z7EYbh5qnIkmqsTjnr4ZXEUxKC8iwxA41j5mRTrlGE5GGiC\nfrfLNI0NdTgnmvEXVTFj6wvGbw5qzerkRk22vwj/C2wBZBkd6CYrmAJk/5G4oWik\nTWrwTLqM+pxVI4YXO84dRysEf90cHy+T1y4YvNtowLJ4SkQYNhR5+xW8PWQM9JRG\n65xDrFBGm2cnhvGDpZGApy4mtg8n2stuK4C/QB+puNs6EoV1aMs2SPmxf5PJHSjQ\nuK32L+ZPw+9wPZnlUURLTIryyIwcY70Wjx4+kgzjANyxgEk8y77RuWdya8RocT8G\nQvglhyKZxpojXt5VUFIM2d8fnKTugeNeds9zgh5CjrVcBkh+q85Im3+t4a8tUqlq\nxvH5C0d4wxnHsNh/dQAlGxC5ppNKxYmR259KqGmGvW24vSO6BSnTmDrWGKiGlixW\nV4CfC9Cpnghqu6jEThUw1QY7E6YOfKn7kpx+t3QbQJa3MYSrumZRFEgVYXvg8tdY\nyehwxBWIhVZVCZFbKasBPeatv1hwH8IzWAJFLctcM6Kp4xdRQUrkxQ==\n-----END CERTIFICATE-----\n",
"ca_common_name" : "TEST_CN",
"ca_country_name" : "TEST_C",
"ca_key" : "-----BEGIN RSA PRIVATE KEY-----\nMIIJKQIBAAKCAgEA2mAubwuBj55hq/Ukk7U916waAKUGb08RdUqzDqC+HP7wpwrg\n7q8JFKyCDCLQDbDQNZxRPwEIOphRrwY7ZJ8Rmdn2Mu9MoQOIwOvcJ5vBj/8ge7yp\naOvBtp3kezp+WR2k3WE1DVPLoPn+sdMFQawnsKo7U/8OaUPEMRpMAYMDLR3FeckE\nT0BfJIRWL1WTx4ho6URfIp0F1jntI4i+vcHZPPzRCorG86WdmvOoHzKPOH9aHTMB\nEtG6kHUS67EKgPyLSZDYVjSi1GO4HbOiymV36EMIbaQStQrkj+P9ODsErbBj3Skj\nDQ8J6a1DlE07gruasR9kVKyGwZfTGRJBcjLzMEzOk7KSMj0Z5v3clq3TficJ9HuY\njAND9nk0UNzTp0FfwJVJyA/bdu7ev340ZJcH6rhIP6/tajNDRJPRzJsP+TeAeba4\n1AjhYU6LJjEYyng8g1osui/Lqjlj/n059SO21nobPaCXorIAYigVlfoS+Jp+vaoF\nfM0S742q/wa/WGvrsm8ikd8MoKbBJLl9mJJi64REpzkbwUxs+7efFF8neMNtDKpx\n83Ub0nqPM/UCdfTmi2iwLD4i5Bv+Xd0U/q1I51Kbna8limQ1N26JGE2+1NVH5PQ/\nSO++q7NE4oYsgJqlJHt0nm6+k46mUXjVQojtuSVaDp308q+LubCtTdGjwF0CAwEA\nAQKCAgAHaRwqSImtBgLqgvcqzAu9Nenr+62sOVKuWEqbRHkvIren84aOkwIL4Y7I\nOqY00LtAFn3rVW2iD2k2N0/sqjk+r1bbg6NmE2igo2BlN7Pp3w6LJGvbU6TPPaxz\nQhjnjUn6+UGDokRWwiUSg8a54821ARHiV9V1XQdbYzkRFBEXhtsctuWeiuCvrI4A\nLTdGnipxQBC6a/m2u2CAxDM03U8x8qJlaTA3NHeUupAJ/v09PZUhSInQya07Gb36\noZdpqShQ5slwo3ijHH8zAtWTaL4Y861lixvXaPc4qtP9BIO0IThCWRMHbms3stmI\nPta2KQem2xnchb5M84oGX8g4x+HYwa/hrRZAsQNvNqPXaHHAav6+QKALiaGVY9Hr\nITmKgoimPuPxMEPfqHAs9kI9DpDwV+58i+jJsb04wsC/INeO35G4dxBZqoHrA61k\nPGsxyDHTKn4f5PguN+JUmU+Y0NV9uehFJD+lAA3UBYoR+MYXyrQBTXh6OYGgniZO\n+EJljgfwWnCXj27uFm6dOI8S+sBim64MVPD9G+FRG48sV+RAYZKy9QP6nOgUmQVM\nePjGCz4TfXIXXpbdkXdNHSzPIGMFpPKBeK/uF8mxKDKxg9Di0t/Q6CYz+xiid+Vj\nIkh2dSrwzkyYghVDW97Rivbx3mEdLPsbMbfY0stuiDhaBXlNQQKCAQEA+hVmqnpD\nUqQMkf6tmQCurZm4GQTRqklWnQ+ta4OhKinnSKGBGct0GgX1ip5ImAus8drcTz5W\n9bc1rDaXuFKnKVqal6FzbsyfvKWTzdNqKw2dFgisqwLzJ7xg6htuBi2AOyBrpNtm\nDmXP2cWEcdk93E99nwhTyaP5mnftx0SBlyKAn7Qt5iUg6ePfXmjL1ce4ZLHNAQC4\nwQWLQ2TVlGINpJPK0ZXW2dHbGdLvbnSdEg8stSRGOLXKoBT06kQCkEaBZzt5/cJl\n6Hlw9hYRofKR1pVqwG6XkN/x4Px1nc2HyDGSsVIxIM5Yv/d9pa3OcXvRuS+5FaXf\nd0qUUxeZqZlUrwKCAQEA34q+4IEq20BqwhOLlLCjpbyGIHiLMMraLFZ8Z5D5poBZ\nWjfsO3coFysLg1VEa+C9rMceCYI6i/H8fYiSoYJrBN72DYBFkWF5GTeJ5EHmW4B4\nL7u4cW/x/yyf6woGJRkoRagNUb7bD/Cp3Fhpm45iP5bYvIK4cJKhQZixpJ4VZpIg\n9f+oHP3ikuJgJ/B6kdv2zJ7SghVFrpP8yOokMdbiKYtiHDSOsRRiEj5l4DHfymyy\nGDLw/kMuoC+PHAipjvL4VxlqO1r+wqorjEPdZ2CtYdi353xrPERNGTS9D43ZyRT0\nLeMGUeDely40T2oewmHXEPeqng8+Mj1PTg7/6uGWswKCAQAfBva04fRmVWol1uYs\n3HPPoAnCOOHWccDoPaCzfSJKu+YxEbCVxbNC40hiiV7SVmh/nTrGLiLV24QyOJe8\nS6znqZESjPpoXcTXv+dFmxxJ+SdrK2pY0UXfwTR49yxAYfbN3yjbzEiuMp2GFEZp\nZZ2SLt6UE5FprAl0y7pZhbtaR/KTXeRv8F1UB2yYJwJbJKtQ+upHXJKPiCOOGf2R\nqlSs/ZUlSaTdY3b+jjgciSVPr0hJtRVtRci88bytMADta4H0j+GDxVGldSO5tGU9\npX3IlMMo2s+9LruwwUHKcUyOXvAnRd5IhrFmJ8uT+atqUwVjJ3OcJvdBsqQSZxQu\ngZKLAoIBAQCvNYlsX/FeTfwfR8CEd3qcwcoDE1hNkwEz9UmmxyvVxA3Et8ZRyZBD\nsHpioudxAoLINH0niMoovC9hmTUMoDMPa05BwMNGMrb++9f5b2mFWIlbKHBlgQ+V\nKL3jNEUiuLgm+JQP+V6r/L62NRn5Ub1SCAKypma33UXFK1A5LaqqbWimR47Vwmzf\nIc2qIEOBpX2oXeezC8dFETr1owdhhQJY+6WXY95fjxFbKUsiURUODOn+K5dWQwP9\ni6lImMWFhIz/f60S/rxliYl+dAbKKy1aXsmuB4fpgcNIOVziHxWPFPxaJvHiJTVy\nG0Xm5M9dHeC6rNQu9NWT/Rf2n60YxV4fAoIBAQC9qXbBxy2kd+4+I9gVt348qRbd\nZlxJi3q/N22wZ1BOIGCAWWsw33YyNghq6xlsu6jt7C/XFYRKTaS5Z9F8/InXbP4j\n/gejdT22TikruWpPrU3+8fifJZsmEfsUGZ6ulk9174hbGbz/TH/JRtpCxFLxw92e\nG+JuKpz0GP/MvtpkkH8MXCmP3dXVchO7pFQXfCjmVaSRA7oii8M4a9m2U4+zM76F\nEfOkFehwYi+LSUBFbFrNKM0+Gw6q8pS0GjdKnljuyhhzN43k0iyLGXcpK5I2xuT7\n8iypj2n4VHccj7flM1QbY2mNuerlfs6s0/Z0t6oF/ZdC6GEMT8LA9czGinLY\n-----END RSA PRIVATE KEY-----\n",
"ca_locality" : "TEST_L",
"ca_organization" : "TEST_O",
"ca_organizational_unit" : "TEST_OU",
"ca_state_or_province_name" : "TEST_S",
"enabled" : true,
"server_cert" : "-----BEGIN CERTIFICATE-----\nMIIFujCCA6KgAwIBAgIIEJgkV3yqf6gwDQYJKoZIhvcNAQEMBQAwaDEQMA4GA1UE\nAwwHVEVTVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8w\nDQYDVQQHDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9D\nMB4XDTIyMTIxMTE2MjcwN1oXDTI3MTIxMDE2MjcwN1owaDEQMA4GA1UEAwwHVEVT\nVF9DTjEPMA0GA1UECgwGVEVTVF9PMRAwDgYDVQQLDAdURVNUX09VMQ8wDQYDVQQH\nDAZURVNUX0wxDzANBgNVBAQMBlRFU1RfUzEPMA0GA1UEBgwGVEVTVF9TMIICIjAN\nBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAoFlmfQYPCKNSz4aihkB1URMYeC3d\n0+A08h+0lU1M7rr42YR/YLYa0DUnT0OGPSsr/bGdahdbq58E667Be7DcR13RBXj2\n6AWHAu4Mom829mhL9YtDdwxRbB177hvDCM4bnHStPaRyiBXy15U7WTUr+o77pAQd\ndQ7UP8BJWwYZVzUD17lainJwd5zTW9z6Hghzt4LM7ovIyFA8jkN1jecrUC4Mpl/i\n4oeC1KTNiTbYmOomrrwcW7jjF9N5bdOEBEkl6ubU8xXmZN3Wo1u2WiEjm9iPLMDf\nYXj20+jaxetphhVGYe9cxg9YRo4N/f6tCO7WA8lqjkmTcy5Aqgk8mfMuFJfbKaSn\nR0MIWIT4hPDFs89Mg7wdLTwq4pRDyuoQmGvEyx/L5FxD4kTi5DlcPlBKsqPIfIL9\nSJdb7Io2Dns82lwWJnfkcYegsQza9Qlb52s5s5oxTnCrp26lnC1Fu+8hRjT3NXRz\no3+Qfdxdt3bB7r7cIF+9KQELz3QrTUO1QtqGnoT2u6N5J5oqSfCnisknziKrlI4d\nazEZfw3amGFRcP9PhBhOTDmS3icA7p0hre337Z2S3qKMo+S50e0jYs52U8jFqooI\nzOR+C58SLDGK3MxpGOwqHCMBwZGKn8MX2tD/BMW6KWh7KVC4S5bnBATwLZr7pNsx\nozi86fLJdDmZw4MCAwEAAaNoMGYwHwYDVR0jBBgwFoAU32L+90JMffP/Nzr3esKw\ndLU+2o0wJAYDVR0RBB0wG4INdnBuLnRlc3QudGVzdIIKMTcyLjE2LjAuMTAdBgNV\nHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUIAgIwDQYJKoZIhvcNAQEMBQADggIBAAmR\naa1N9jlETp6tjC9hDVBzSKSZ/sTo7cZ4YKtYN3y2m8hIkYi9uWSR37Qv6pUnIeP+\nP3tuTAMkdAnGZ63TuTo0bvNwUsLlG+2i1OxyeFPMJKZcK4SYirXe7I4Xdoja3o6A\nEEZdW+aCP+YVhmdMHfv2JRKawrX2N75WDufZyQy+95Nus+cNQDNZ2OtUAr4JZSXj\n9UpfaXHl74RZBYLzDTCntTpRUM1D/Je1JjSiGNd0n6Wgs+P5alli/MhHiGuqJdpG\nJHQ7tqdX3Ytd9lGaEckk9FJjgX0MhuC13OZMN0WtnRe1uvMm2cbghjxQ/wYOgLQQ\nDGISLNa3kenTSCvcgH5Mo3VVGgx0wFD4Iq84LaENd5xnSDJhKvxAB4YZEWO7rZOU\nvrYXZF16yCJ3hebw8MZebTc26NroxfkIX50xtvDLFH+LyB2IwW3pIOgtzRC6OsLh\nlCEm2n7bbjGReAa0TmXa3Ss1zO6yUNvZ1XNAL2gv/yxNDntVtaI0c38bEO6XmMdu\n5c26xAlujRJf4udJbmwks6w4enDva4m05rDEbUikNsYpaUAxF0FBEzt8u0q58cHr\nwUR+ank6dixa0TjFFeugzHXqq3uFtkHsAvOX5xE5WTaVvgHKEO7uYmLRD0c0bJDc\n+RsnXU1f1ks5wUHajj6aeAknNKnoQQ/K0dhTI0Vb\n-----END CERTIFICATE-----\n",
"server_common_name" : "TEST_CN",
"server_country_name" : "TEST_S",
"server_domain" : "vpn.test.test",
"server_ip" : "172.16.0.1",
"server_key" : "-----BEGIN RSA PRIVATE KEY-----\nMIIJKAIBAAKCAgEAoFlmfQYPCKNSz4aihkB1URMYeC3d0+A08h+0lU1M7rr42YR/\nYLYa0DUnT0OGPSsr/bGdahdbq58E667Be7DcR13RBXj26AWHAu4Mom829mhL9YtD\ndwxRbB177hvDCM4bnHStPaRyiBXy15U7WTUr+o77pAQddQ7UP8BJWwYZVzUD17la\ninJwd5zTW9z6Hghzt4LM7ovIyFA8jkN1jecrUC4Mpl/i4oeC1KTNiTbYmOomrrwc\nW7jjF9N5bdOEBEkl6ubU8xXmZN3Wo1u2WiEjm9iPLMDfYXj20+jaxetphhVGYe9c\nxg9YRo4N/f6tCO7WA8lqjkmTcy5Aqgk8mfMuFJfbKaSnR0MIWIT4hPDFs89Mg7wd\nLTwq4pRDyuoQmGvEyx/L5FxD4kTi5DlcPlBKsqPIfIL9SJdb7Io2Dns82lwWJnfk\ncYegsQza9Qlb52s5s5oxTnCrp26lnC1Fu+8hRjT3NXRzo3+Qfdxdt3bB7r7cIF+9\nKQELz3QrTUO1QtqGnoT2u6N5J5oqSfCnisknziKrlI4dazEZfw3amGFRcP9PhBhO\nTDmS3icA7p0hre337Z2S3qKMo+S50e0jYs52U8jFqooIzOR+C58SLDGK3MxpGOwq\nHCMBwZGKn8MX2tD/BMW6KWh7KVC4S5bnBATwLZr7pNsxozi86fLJdDmZw4MCAwEA\nAQKCAgAM9m00mjLI7fsZz7Z/x+I0Bakqvfp60Fs3X5zHnRIlEnRfkTiC5vXP8xwU\nak8FzuGlhqBFHVJJ03cgXmZBy5BjLJBjMt4y7490iy32S6tTzCan2PRBQXurk86a\n9x+TLKZKxZvjqdGgcrXI+8VqdsPxY3GwVqzS87nw1WiYtSuDQ0PmQpOxMYMqCEGF\n4Z1OpDxGj4pllmNK3kGm9okgSZnUx4Q6RvIegfnvmssK1qY35mXuJkLcn1usZ2of\nmMPJXOh1zudUJ2cSrGRXnGhnbNpmFOGuKoFkbdT2WJKnAVrsfffMnv8O+9qVCZLT\n/6yZVkVy1OuKSSRkYU7U8B44C9KjsshuMCk9qtVmdTAdyeXgm+6nwJ9wkA5czu1y\nfbkXNX0hCxqPlHAqpD5eOQh67daWYydLyPXo7SIYoeKyX3+dSOWC938qF/AJ4WyN\nONFX3uinzIMHVPQREWqcihMKCzNAdHGJ3uKzUgBoqHcRQog3hdYIKD0oexUBT9pQ\ngoVZH7d2JftL2cpEfU8ez7xHe79PFlmWJYQqKRs0smgcMeVglTrE/J8V0A3g4E6G\nAxmw9uKYdcJMbAD6S2Myi3Ygvef0bFQ8Qx1/G7ggYEVyimWTcbwzCOUQ0LeEfMaH\noUUdfj+WwBOyfGjUTxbdNf39fKH0ADFjQw974DoioVtKhOSdkQKCAQEAzPvDPvZC\nCdevnHNHEHyMlvvkbu14GruXdoNfzEccnABkD/n44+PJYXA1YNpsmwUE5js63TBf\najyLbA94plG87vtheMIbeFSe0zG0ysUGqS/kycOsCHzuAXfrg3+/+lNrfOUoZF+2\nh8JaiFnIdZgNXis+rNrYGepEnZoW0vPzNPx0xVm6zQEKb3I+bSP5SvegIy3D+HQV\nyXAqxkhV/9ATzqNH8DGubhyGlY605gjkkLKcIJprPtVrlcwKnHi6a/+fNnU/eKQG\nxvhvJdzsI+98yad6PI62vZESBYBoyWJs4LzaW5Z7OnlmKmBrqsOe6CeHCy/KlQZ5\nSeQov2IP6OnqfwKCAQEAyEHUWGH6Gy4Vsl/LdBCYGuANN2J7p24Xi20LxcSbSc63\npgSfdnRvps5GgNIIS2C6H3axpCwbYPgO4LhOZ7cuaQHXyvEqhLVq94nPySTn5axS\nkzcKS8yiKUGA48cjX7jmbV4wOCfrlMMW0cHxDafMym/X1BCSadA/tQ0WgkD9c3On\nBWoU+6uDVghY4Za9p/7BlYqMHCttT29zg1pGiT7BeS8sDBUnc7pU8y2xLkTBN/0o\n4dOGgnnvhUPjZ9PpzvT/jPeTyOzVIehfeWjp24qp+U2EikyNOPg2u4mp4+273H3X\nUfUrUtwicOSRgXxtAcBn1csbGRkkuneW/loofGj8/QKCAQBi4XfX4XcNxGvELp+z\nRkGTe8M/93Geg6uW0dzeb9dPMakTQ+RaGkHErRoytGr7hLpOTXghxvngB4DCCdyL\nbpaTOdRVKl2R+E/9VNb/kXebGa1l3uwX1BwDvVNwxalYGfGZ9/k6Iims54ZAi/71\nKvoX2QiM3aytI6Mh23jzHhbOEpJJuPUxezULebK/d0EEdtta3PLR4T25RFB+Adrq\nYfeMEJvdNDoOh9gsQQDmjpejbWV/HL5rOwyA4EKmJF7ZRiAJZxnNGmLijGkhfKa0\n1wv9Qrrmh3mDjH2DBeSGcOJQrwkucTLUjEdKXeTSJTd8icTNEqrIpKzRhixZ1fYS\nxvQFAoIBACZZJNa//GsUCiecXJOfUeFjomRGwbMwS+XxPd3jZnFd2qE6JWdDqNXi\njnHAxsHYhgvcaOwtXhjVp9O0t5743zRQnAhK4n+DVjaM93NnU9kRhMaYNaqKR0tr\nNcloqwd7mvS6orU+P8i/CzGj2AtrZLYncMc1XTRSIsEC/pp245ImRYet5tLC52Wk\nN5ELksoG6P9ABtCmKEqb5xzyPqutjtMsC11M978boYTn7RQVKoMUQa3tGccGnq2A\ncJ3DYPS2yfEuv+gsIixaGV5gjtfx19bb11O8kRalwaVsGVKChgUVPBR/xIobiaTg\nwFRxhVZeiAPS3x+RRw1GNW4Dydj5KekCggEBAKD4a0sl7HjeygohDM1DFiLNkaJ5\nVlh0imvP9B0DmYog+itmNrfADuqWju0fgSTYD3MeePDYr5EuHrfOR1TjgipOuQmv\n4WuO99zYR+4v0m4bECElQFyXNPIdz/WpdhYiFnFMxR7K3M2ozIOoiQbqOLfGdO7Z\nhzSSXa1CLA/h9g0dd0ZeoQ1NFz+rJG2slrcx7VhnON+ISiQhc4dgtG9VSJbddKzI\nJZ940kIw4ImL02EDWKr71k5uPsxB3GyR0ObBi31TTD9HWx/1V6Y0hLTP80ql8GAN\nbijDRGsUo9jzoT2CeJPoH45yiVyzMN5g4CkCNf/ZU9ZEF5C+/lgsEWtyekY=\n-----END RSA PRIVATE KEY-----\n",
"server_locality" : "TEST_L",
"server_organization" : "TEST_O",
"server_organizational_unit" : "TEST_OU",
"server_state_or_province_name" : "TEST_S"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-The ROOT certificate is not present in the system
-The SERVER certificate is not present in the system
```
- - - - - -
## IKEv2 Advanced settings show
**Request Structure:** `https:///api/v1/ikev2/advanced_settings`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/ikev2/advanced_settings
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"authby" : "pubkey",
"charondebug_asn" : 0,
"charondebug_cfg" : 0,
"charondebug_chd" : 0,
"charondebug_dmn" : 0,
"charondebug_enc" : 0,
"charondebug_esp" : 0,
"charondebug_ike" : 0,
"charondebug_imc" : 0,
"charondebug_imv" : 0,
"charondebug_job" : 0,
"charondebug_knl" : 0,
"charondebug_lib" : 0,
"charondebug_mgr" : 0,
"charondebug_net" : 0,
"charondebug_pts" : 0,
"charondebug_tls" : 0,
"charondebug_tnc" : 0,
"closeaction" : "none",
"compress" : "no",
"dpdaction" : "clear",
"dpddelay" : 300,
"dpdtimeout" : 150,
"esp" : "aes256-sha256,chacha20poly1305-sha512,aes256-sha1,aes256gcm16-ecp384,3des-sha1!",
"forceencaps" : "yes",
"fragmentation" : "yes",
"ike" : "aes256-sha1-modp1024,aes128-sha1-modp1024,chacha20poly1305-sha512-curve25519-prfsha512,aes256gcm16-sha384-prfsha384-ecp384,3des-sha1-modp1024!",
"ikelifetime" : 86400,
"inactivity" : 86400,
"installpolicy" : "yes",
"keyingtries" : 5,
"lifetime" : 3600,
"margintime" : 600,
"mobike" : "yes",
"modeconfig" : "pull",
"reauth" : "yes",
"rekey" : "no",
"rekeyfuzz" : 100,
"strictcrlpolicy" : "no",
"type" : "tunnel",
"uniqueids" : "no"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## IKEv2 Advanced settings set
**Request Structure:** `https:///api/v1/ikev2/advanced_settings`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Options required:**
```JSON
"charondebug_dmn" = "-1|0|1|2|3|4"
"charondebug_mgr" = "1|0|1|2|3|4"
"charondebug_ike" = "1|0|1|2|3|4"
"charondebug_chd" = "1|0|1|2|3|4"
"charondebug_job" = "1|0|1|2|3|4"
"charondebug_cfg" = "1|0|1|2|3|4"
"charondebug_knl" = "1|0|1|2|3|4"
"charondebug_net" = "1|0|1|2|3|4"
"charondebug_asn" = "1|0|1|2|3|4"
"charondebug_enc" = "1|0|1|2|3|4"
"charondebug_lib" = "1|0|1|2|3|4"
"charondebug_esp" = "1|0|1|2|3|4"
"charondebug_tls" = "1|0|1|2|3|4"
"charondebug_tnc" = "1|0|1|2|3|4"
"charondebug_imc" = "1|0|1|2|3|4"
"charondebug_imv" = "1|0|1|2|3|4"
"charondebug_pts" = "1|0|1|2|3|4"
"uniqueids" = "yes|no|never|replace|keep"
"strictcrlpolicy" = "yes|no|ifuri"
"authby" = "pubkey|rsasig|ecdsasig|psk|secret|xauthrsasig|xauthpsk|never"
"closeaction" = "none|clear|hold|restart"
"compress" = "yes|no"
"dpdaction" = "none|clear|hold|restart"
"dpddelay" = "0-2147483647"
"dpdtimeout" = "0-2147483647"
"inactivity" = "0-2147483647"
"esp" = ""
"forceencaps" = "yes|no"
"fragmentation" = "yes|accept|force|no"
"ike" = ""
"ikelifetime" = "0-2147483647"
"installpolicy" = "yes|no"
"keyingtries" = "1-2147483647"
"lifetime" = "1-86400"
"margintime" = "1-2147483647"
"mobike" = "yes|no"
"modeconfig" = "push|pull"
"reauth" = "yes|no"
"rekey" = "yes|no"
"rekeyfuzz" = "0-2147483647"
"type" = "tunnel|transport|transport_proxy|passthrough|drop"
```
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-d "authby=pubkey&\
charondebug_asn=1&\
charondebug_cfg=1&\
charondebug_chd=1&\
charondebug_dmn=1&\
charondebug_enc=1&\
charondebug_esp=1&\
charondebug_ike=1&\
charondebug_imc=1&\
charondebug_imv=1&\
charondebug_job=1&\
charondebug_knl=1&\
charondebug_lib=1&\
charondebug_mgr=1&\
charondebug_net=1&\
charondebug_pts=1&\
charondebug_tls=1&\
charondebug_tnc=1&\
closeaction=none&\
compress=no&\
dpdaction=clear&\
dpddelay=300&\
dpdtimeout=150&\
esp=$(sed -e 's,!,%21,g' </api/v1/ikev2/advanced_settings/default`
**Cookie: `access_hash=`**
**Method: `PUT`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X PUT https://dev.softkeel.com/api/v1/ikev2/advanced_settings/default
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"authby" : "pubkey",
"charondebug_asn" : 0,
"charondebug_cfg" : 0,
"charondebug_chd" : 0,
"charondebug_dmn" : 0,
"charondebug_enc" : 0,
"charondebug_esp" : 0,
"charondebug_ike" : 0,
"charondebug_imc" : 0,
"charondebug_imv" : 0,
"charondebug_job" : 0,
"charondebug_knl" : 0,
"charondebug_lib" : 0,
"charondebug_mgr" : 0,
"charondebug_net" : 0,
"charondebug_pts" : 0,
"charondebug_tls" : 0,
"charondebug_tnc" : 0,
"closeaction" : "none",
"compress" : "no",
"dpdaction" : "clear",
"dpddelay" : 300,
"dpdtimeout" : 150,
"esp" : "aes256-sha256,chacha20poly1305-sha512,aes256-sha1,aes256gcm16-ecp384,3des-sha1!",
"forceencaps" : "yes",
"fragmentation" : "yes",
"ike" : "aes256-sha1-modp1024,aes128-sha1-modp1024,chacha20poly1305-sha512-curve25519-prfsha512,aes256gcm16-sha384-prfsha384-ecp384,3des-sha1-modp1024!",
"ikelifetime" : 86400,
"inactivity" : 86400,
"installpolicy" : "yes",
"keyingtries" : 5,
"lifetime" : 3600,
"margintime" : 600,
"mobike" : "yes",
"modeconfig" : "pull",
"reauth" : "yes",
"rekey" : "no",
"rekeyfuzz" : 100,
"strictcrlpolicy" : "no",
"type" : "tunnel",
"uniqueids" : "no"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
##
##
##
# Check online users
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## Check online users WireGuard protocol
**Request Structure:** `https:///api/v1/wireguard/online`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/wireguard/online
```
**Response example:**
```JSON
{
"error" : "",
"msg" : [
{
"allowed_IPs" : "10.0.110.17",
"b_download" : "10",
"b_upload" : "10",
"endpoint" : "79.184.218.180:47471",
"latest_handshake" : "2022-12-12 13:02:01",
"name" : "ruslan_telefon",
"status" : "enable",
"transfer_rx" : "3892",
"transfer_tx" : "2972",
"username" : "user_32",
"wg_name" : "77_87_125_209"
},
{
"allowed_IPs" : "10.0.110.12",
"b_download" : "30",
"b_upload" : "30",
"endpoint" : "77.87.125.204:59558",
"latest_handshake" : "2022-12-12 13:01:48",
"name" : "test_mac",
"status" : "enable",
"transfer_rx" : "2244",
"transfer_tx" : "3356",
"username" : "test_mac",
"wg_name" : "77_87_125_209"
}
],
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Check online users IKEv2 protocol
**Request Structure:** `https:///api/v1/ikev2/online`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/ikev2/online
```
**Response example:**
```JSON
{
"error" : "",
"msg" : [
{
"allowed_IPs" : "10.0.110.17",
"b_download" : "10",
"b_upload" : "10",
"endpoint" : "79.184.218.180",
"name" : "ruslan_telefon",
"status" : "enable",
"uptime" : " 11 seconds ago",
"username" : "user_32",
"wg_name" : "77_87_125_209"
},
{
"allowed_IPs" : "10.0.110.12",
"b_download" : "30",
"b_upload" : "30",
"endpoint" : "77.87.125.204",
"name" : "test_mac",
"status" : "enable",
"uptime" : " 4 seconds ago",
"username" : "test_mac",
"wg_name" : "77_87_125_209"
}
],
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Drop user connection IKEv2 protocol
**Request Structure:** `https:///api/v1/ikev2/online/`
**Cookie: `access_hash=`**
**Method: `DELETE`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X DELETE https://dev.softkeel.com/api/v1/ikev2/online/ruslan_telefon
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "success",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
##
# One-time link
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## One-time link Config
**Request Structure:** `https:///api/v1/otl/config`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/otl/config
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"after_body" : "\n
\n
\n
\n
\n
\n\nPUQ sp. z o.o.
\n\t",
"before_body" : "\nThis is a one-time link with configuration options
\n\t",
"css" : "\n* {\n\tbackground-color: #E5E5E5;\n\ttext-align: center;\n}\n\n.wireguard,.ikev2 {\n\tmargin: auto;\n\twidth: 550px;\n\ttext-align: center;\n}\n \n.qr-img{\n\ttext-align: center;\n}\n\n.config-text{\n\ttext-align: center;\n\tdisplay: inline-block;\n}\n\n.config-text pre {\n\twidth: 550px;\n\ttext-align: left;\n\toverflow-x: auto;\n\ttab-width: 1; \n\toverflow-x: auto;\n\twhite-space: pre-wrap;\n\twhite-space: -moz-pre-wrap !important;\n\twhite-space: -pre-wrap;\n\twhite-space: -o-pre-wrap;\n\tword-wrap: break-word;\n\tbackground: #fff;\n}\n\n.btn {\n\twidth: 400px;\n\tborder: none;\n\tcolor: white;\n\tpadding: 4px 10px;\n\ttext-align: center;\n\ttext-decoration: none;\n\tdisplay: inline-block;\n\tfont-size: 20px;\n\tmargin: 5px 5px;\n\ttransition-duration: 0.5s;\n\tcursor: pointer;\n\tbackground-color: white;\n\tcolor: black;\n\tborder: 5px solid #008CBA;\n}\n.btn:hover {\n\tbackground-color: RoyalBlue;\n}\n\n.authorization_data {\n\ttext-align: center;\n\tfont-size: 20px;\n}\n.authorization_data table {\n\twidth: 100%;\n}\n\n@media only screen and (orientation: portrait){\n\t* h1 {\n\t\tfont-size: 50px;\n\t}\n\t.wireguard,.ikev2 {\n\t\twidth: 90%;\n\t\tmargin: auto;\n\t}\n\t.btn {\n\t\twidth: 90%;\n\t\tfont-size: 50px;\n\t\tmargin: 5px 5px;\n\t}\n\t.qr-img img{\n\t\twidth: 100%;\n\t\theight: 100%;\n\t}\n\t.config-text{\n\t\twidth: 100%;\n\t}\n\t.config-text pre {\n\t\twidth: 100%;\n\t}\n\t.authorization_data {\n\t\ttext-align: center;\n\t\tfont-size: 50px;\n\t}\n}\n",
"lifetime" : "10",
"not_relevant" : "\nThis link is no longer relevant.
\nRequest a new link.
\n
\n\nPUQ sp. z o.o.
\n\t",
"title" : "One-time link"
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## One-time link list
**Request Structure:** `https:///api/v1/otl/list`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/otl/list
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"olts" : {
"05fcdebdbd5744aa4df6b72386cacc0bea2b452475d5d31ff25744695c7372a2a3adaed3988382b8" : {
"account" : "ruslan_windows",
"created_data" : "2022-12-09",
"key" : "05fcdebdbd5744aa4df6b72386cacc0bea2b452475d5d31ff25744695c7372a2a3adaed3988382b8",
"lifetime" : "2022-12-19"
},
"569a3095db4c2251491e0dc19c302b1a9d5f64a67f83d53040cde52a108ea970d940926ca0eb58dc" : {
"account" : "peer_101",
"created_data" : "2022-12-09",
"key" : "569a3095db4c2251491e0dc19c302b1a9d5f64a67f83d53040cde52a108ea970d940926ca0eb58dc",
"lifetime" : "2022-12-19"
},
"84cb3a75982f739f68458e72e361ee3eae6f419400ce28713f88a371ff254a3f3db4392cf405a00f" : {
"account" : "ruslan_windows",
"created_data" : "2022-12-09",
"key" : "84cb3a75982f739f68458e72e361ee3eae6f419400ce28713f88a371ff254a3f3db4392cf405a00f",
"lifetime" : "2022-12-19"
},
"8d0fa51763d06ebe7db4d82e6f5a521421087b4a13e6b7fb1f5c1f6939171926437d23c8d66402ef" : {
"account" : "ruslan_windows",
"created_data" : "2022-12-09",
"key" : "8d0fa51763d06ebe7db4d82e6f5a521421087b4a13e6b7fb1f5c1f6939171926437d23c8d66402ef",
"lifetime" : "2022-12-19"
},
"b91361407612aec12803ecac999bba70a3b4b1466caa50c61344e93acac86f8f1caa7cc1f8bcafdc" : {
"account" : "ruslan_windows",
"created_data" : "2022-12-09",
"key" : "b91361407612aec12803ecac999bba70a3b4b1466caa50c61344e93acac86f8f1caa7cc1f8bcafdc",
"lifetime" : "2022-12-19"
},
"dbfa0ab6ba04d3c186031cd6b276c7405d030d12c6524e52accc4cd32e2e68554cf6fecabfb56c1e" : {
"account" : "ruslan_dom_pc",
"created_data" : "2022-12-10",
"key" : "dbfa0ab6ba04d3c186031cd6b276c7405d030d12c6524e52accc4cd32e2e68554cf6fecabfb56c1e",
"lifetime" : "2022-12-20"
}
}
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## One-time link WireGuard Config section
**Request Structure:** `https:///api/v1/otl/config_wireguard`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/otl/config_wireguard
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"button1_label" : "Download client Android",
"button1_link" : "https://play.google.com/store/apps/details?id=com.wireguard.android",
"button2_label" : "Download client iOS",
"button2_link" : "https://apps.apple.com/us/app/wireguard/id1441195209",
"button3_label" : "Download client Windows",
"button3_link" : "https://download.wireguard.com/windows-client/wireguard-installer.exe",
"button4_label" : "Download client macOS",
"button4_link" : "https://itunes.apple.com/us/app/wireguard/id1451685025",
"button5_label" : "Official clients WireGuard",
"button5_link" : "https://www.wireguard.com/install/",
"button6_label" : "",
"button6_link" : "",
"download_config_button_label" : "Dowload config file",
"enable" : true,
"enable_config_qr" : true,
"enable_config_text" : true
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## One-time link IKEv2 Config section
**Request Structure:** `https:///api/v1/otl/config_ikev2`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=def77a57825907131fca3ba92fc22970ffe7429fd8b49535e178f59542c42cf2be854e296941de9f" \
-X GET https://dev.softkeel.com/api/v1/otl/config_ikev2
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"button1_label" : "Download client Android",
"button1_link" : "https://play.google.com/store/apps/details?id=org.strongswan.android",
"button2_label" : "Download client Debian/Ubuntu",
"button2_link" : "https://download.strongswan.org/NetworkManager/",
"button3_label" : "Official clients strongSwan",
"button3_link" : "https://download.strongswan.org/",
"button4_label" : "",
"button4_link" : "",
"button5_label" : "",
"button5_link" : "",
"button6_label" : "",
"button6_link" : "",
"download_certificate_button_label" : "Dowload Certificate CA",
"download_profile_button_label" : "Dowload Profile",
"enable" : true
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
# Traffic Logging Config
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## Traffic Logging Get Config
**Request Structure:** `https:///api/v1/traffic_logging`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=f3a4359ffc8c62629e1067c76df99cda7d64f4e82f8e24e6fa9569b9b48de5c58af8d53b4f444a70" \
-X GET https://dev.softkeel.com/api/v1/traffic_logging
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"enabled" : true,
"enabled_influxdb" : true,
"enabled_remote_syslog" : true,
"established" : true,
"incoming" : false,
"influxdb_bucket" : "logs_puqvpncp",
"influxdb_organization" : "PUQ sp. z o.o.",
"influxdb_token" : "xbU0AfUh0mPsP9Izviojd0TGLIyo8Io1PFW3DXK2VQDeoUEDDBXwEkJ36A6H2uDBIiW7DEVsG4TgGiUTq6rslg==",
"influxdb_url" : "http://77.87.125.208:8086",
"interface_in" : false,
"interface_out" : false,
"invalid" : false,
"len" : false,
"mark" : false,
"new" : false,
"related" : true,
"remote_syslog_server" : "77.87.125.208",
"remote_syslog_server_port" : 514,
"tos" : false,
"untracked" : false
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Traffic Logging Edit Config
**Request Structure:** `https:///api/v1/traffic_logging`
**Cookie: `access_hash=`**
**Method: `PUT`**
**PUT data:**
**Not required:**
```JSON
"enabled" = 1|0
"enabled_influxdb" = 1|0
"enabled_remote_syslog" = 1|0
"established" = 1|0
"incoming" = 1|0
"influxdb_bucket" = ""
"influxdb_organization" = ""
"influxdb_token" = ""
"influxdb_url" = "influxdb_url"
"interface_in" = 1|0
"interface_out" = 1|0
"invalid" = 1|0
"len" = 1|0
"mark" = 1|0
"new" = 1|0
"related" = 1|0
"remote_syslog_server" =
"remote_syslog_server_port" = 1-65536,
"tos" = 1|0
"untracked" = 1|0
```
**Example:**
```shell
curl \
-b "access_hash=f3a4359ffc8c62629e1067c76df99cda7d64f4e82f8e24e6fa9569b9b48de5c58af8d53b4f444a70" \
-d "enabled=1&\
enabled_influxdb=1&\
enabled_remote_syslog=1&\
established=1&\
incoming=0&\
influxdb_bucket=logs_puqvpncp&\
influxdb_organization=PUQ sp. z o.o.&\
influxdb_token=xbU0AfUh0mPsP9Izviojd0pGLIyo8Io1PFW8DXKHVQDeoUEDDBXwEkJ36A6H2uDBIiW7DEVsG4TgGiUTq6rslg==&\
influxdb_url=http://77.87.125.208:8086&\
interface_in=0&\
interface_out=0&\
invalid=0&\
len=0&\
mark=0&\
new=0&\
related=1&\
remote_syslog_server=77.87.125.208&\
remote_syslog_server_port=514&\
tos=0&\
untracked=0" \
-X PUT https://dev.softkeel.com/api/v1/traffic_logging
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"enabled" : true,
"enabled_influxdb" : true,
"enabled_remote_syslog" : true,
"established" : true,
"incoming" : false,
"influxdb_bucket" : "logs_puqvpncp",
"influxdb_organization" : "PUQ sp. z o.o.",
"influxdb_token" : "xbU0AfUh0mPsP9Izviojd0pGLIyo8Io1PFW8DXKHVQDeoUEDDBXwEkJ36A6H2uDBIiW7DEVsG4TgGiUTq6rslg==",
"influxdb_url" : "http://77.87.125.208:8086",
"interface_in" : false,
"interface_out" : false,
"invalid" : false,
"len" : false,
"mark" : false,
"new" : false,
"related" : true,
"remote_syslog_server" : "77.87.125.208",
"remote_syslog_server_port" : 514,
"tos" : false,
"untracked" : false
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Remote Syslog Server must be filled
-InfluxDB Telegraf not installed
-InfluxDB Url must be filled
-InfluxDB Token must be filled
-InfluxDB Bucket must be filled
-InfluxDB Organization must be filled
-At least one logging method must be enabled (Remote Syslog or/and InfluxDB)
```
- - - - - -
# Backups
##### [Order now](https://puqcloud.com/puqvpncp.php) | [Download](https://download.puqcloud.com/cp/puqvpncp/) | [FAQ](https://faq.puqcloud.com)
## Backups List
**Request Structure:** `https:///api/v1/backups`
**Method:** `GET`
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=7effe99173b87e9cdebdab66d6fb23c9b244af250cb09b5dd36d8f80d14a8510b2d00bcba7290252" \
-X GET https://dev.softkeel.com/api/v1/system/backups
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"backups" : [
{
"backup_name" : "dev.softkeel.com_2023-01-27_19-00-40.zip",
"creation_date" : "2023-01-27T19:00:57.159356394+01:00",
"size" : 7.462
},
{
"backup_name" : "dev.softkeel.com_2023-01-27_18-00-39.zip",
"creation_date" : "2023-01-27T18:00:55.902692143+01:00",
"size" : 7.462
},
{
"backup_name" : "dev.softkeel.com_2023-01-27_17-00-37.zip",
"creation_date" : "2023-01-27T17:00:54.501350728+01:00",
"size" : 7.462
}
]
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Backup Create
**Request Structure:** `https:///api/v1/backups`
**Method:** POST
**Cookie: `access_hash=`**
**Options not required:**
```
statistics=0|1
```
**Example:**
```shell
curl \
-b "access_hash=7b8125b94edbb5baf677286fb186942673afe317e0298601990d4cf3dd37991e399e764f9bc2fd20" \
-d "statistics=1" \
-X POST https://dev.softkeel.com/api/v1/backups
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"backup_name" : "dev.softkeel.com_2023-01-28_12-50-42.zip",
"creation_date" : "2023-01-28T12:50:59.772514276+01:00",
"size" : 7.6038
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-Error backup creation:
-FTP upload error:
```
- - - - - -
## Backup Restore
**Request Structure:** `https:///api/v1/backups/restore`
**Method:** PUT
**Cookie: `access_hash=`**
**Options required:**
```
backup_name="backup_name"
```
**Example:**
```shell
curl \
-b "access_hash=7b8125b94edbb5baf677286fb186942673afe317e0298601990d4cf3dd37991e399e764f9bc2fd20" \
-d "backup_name=dev.softkeel.com_2023-01-28_12-50-42.zip" \
-X PUT https://dev.softkeel.com/api/v1/backups/restore
```
**Response example:**
```JSON
{
"error" : "",
"msg" : "success",
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-PUQVPNCP status not OK
-There is no backup with this name
-Error backup reader:
-Empty list of files in file with file list
-Empty archive
-The number of files in the archive does not match the list of files in the file
-Mismatch between files in archive and list of files
-Unable to delete old configuration:
-Failed to open archive, ERROR:
-Failed to create folder:
-Failed to create file:
-Failed to unzip file:
```
- - - - - -
## Backup Download
**Request Structure:** `https:///api/v1/backups/filename`
**Method:** GET
**Cookie: `access_hash=`**
**Example:**
```shell
curl \
-b "access_hash=7b8125b94edbb5baf677286fb186942673afe317e0298601990d4cf3dd37991e399e764f9bc2fd20" \
-X GET https://dev.softkeel.com/api/v1/backups/dev.softkeel.com_2023-01-28_12-00-59.zip \
--output dev.softkeel.com_2023-01-28_12-00-59.zip
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Backups Get Configuration
**Request Structure:** `https:///api/v1/backups/config`
**Method:** GET
**Cookie: `access_hash=`**
**Options required:**
```
backup_name="backup_name"
```
**Example:**
```shell
curl \
-b "access_hash=7b8125b94edbb5baf677286fb186942673afe317e0298601990d4cf3dd37991e399e764f9bc2fd20" \
-X GET https://dev.softkeel.com/api/v1/backups/config
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"backup_to_ftp" : true,
"every_day" : true,
"every_day_hour" : 13,
"every_day_minute" : 5,
"every_day_statistics" : true,
"every_hour" : true,
"every_hour_minute" : 50,
"every_hour_statistics" : true,
"ftp_password" : "QWEqwe123",
"ftp_path" : "home/dev.softkeel.com",
"ftp_server" : "home.uuq.pl",
"ftp_server_port" : 21,
"ftp_user" : "puqvpncp",
"number_backups" : 10
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
```
- - - - - -
## Backups Set Configuration
**Request Structure:** `https:///api/v1/backups/config`
**Method:** PUT
**Cookie: `access_hash=`**
**Options required:**
```
backup_to_ftp=1|0
every_day=1|0
every_day_hour=0-23
every_day_minute=0-59
every_day_statistics=0|1
every_hour=1|0
every_hour_minute=0-59
every_hour_statistics= 1|0
ftp_password=
ftp_path=
ftp_server=
ftp_server_port=
ftp_user=
number_backups=
```
**Example:**
```shell
curl \
-b "access_hash=7b8125b94edbb5baf677286fb186942673afe317e0298601990d4cf3dd37991e399e764f9bc2fd20" \
-d "backup_to_ftp=1&\
every_day=1&\
every_day_hour=14&\
every_day_minute=45&\
every_day_statistics=1&\
every_hour=1&\
every_hour_minute=40&\
every_hour_statistics=1&\
ftp_password=QWEqwe123&\
ftp_path=home/dev.softkeel.com&\
ftp_server=home.uuq.pl&\
ftp_server_port=21&\
ftp_user=puqvpncp&\
number_backups=100" \
-X PUT https://dev.softkeel.com/api/v1/backups/config
```
**Response example:**
```JSON
{
"error" : "",
"msg" : {
"backup_to_ftp" : true,
"every_day" : true,
"every_day_hour" : 14,
"every_day_minute" : 45,
"every_day_statistics" : true,
"every_hour" : true,
"every_hour_minute" : 40,
"every_hour_statistics" : true,
"ftp_password" : "QWEqwe123",
"ftp_path" : "home/dev.softkeel.com",
"ftp_server" : "home.uuq.pl",
"ftp_server_port" : 21,
"ftp_user" : "puqvpncp",
"number_backups" : 100
},
"status" : "success"
}
```
**Errors:**
```
-Not authorized
-In every hour schedule, the minute parameter must be between 0 and 59
-In the daily schedule, the hour parameter must be between 0 and 23
-In a daily schedule, the minute parameter must be between 0 and 59
-Number backups parameter must be greater than 0
-FTP server must be filled
-FTP user must be filled
-FTP password must be filled
```
##